While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

As we aim for a wireless world, technology's reliance on cloud computing services is becoming more apparent every day. As 5G begins rolling out later this year and network communications become even faster and more reliable, so grows our dependency on the services offered in the cloud.
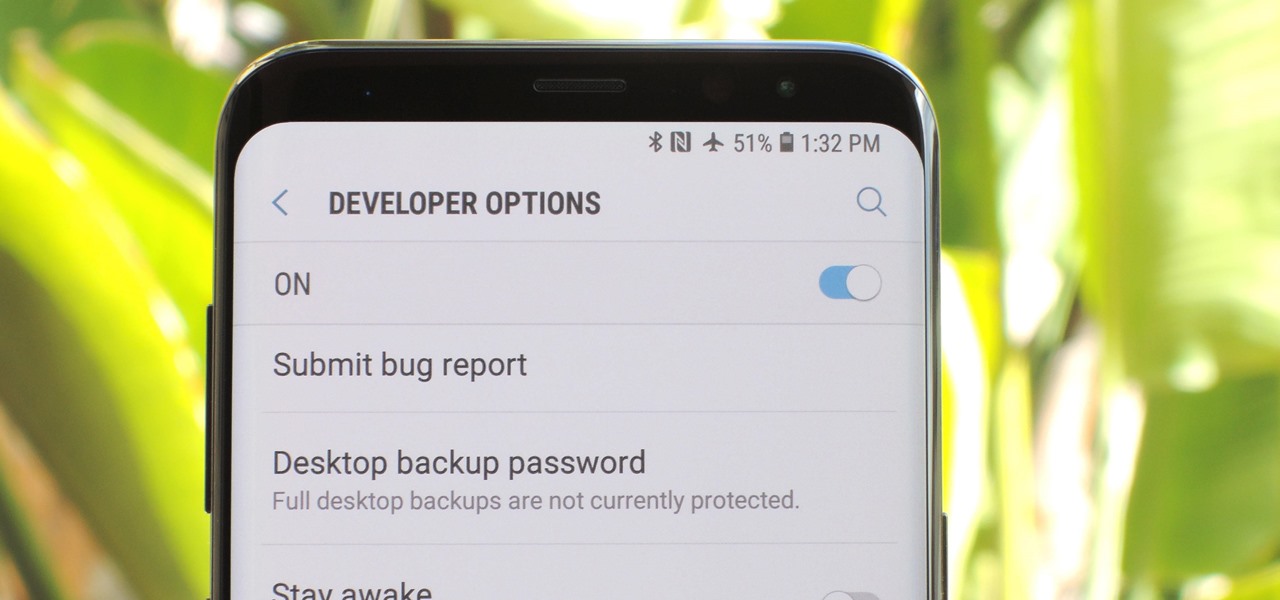
You don't need to have a fully modded and rooted Galaxy S9 to appreciate what developer options brings to the table. Besides the obvious USB debugging, which lets you use ADB, this hidden menu lets you tweak your phone's animations or change its DPI to better suit your needs — and that's just the tip of the iceberg.

Because augmented reality is still so new to so many people, there are a number of would-be experts opining online, often repeating basic facts anyone with a spare 15 minutes can find on their own. That's why it's important to point out when someone delivers what could be considered the ultimate cheat sheet for ramping up your AR IQ if you're unfamiliar with the finer points of the space.
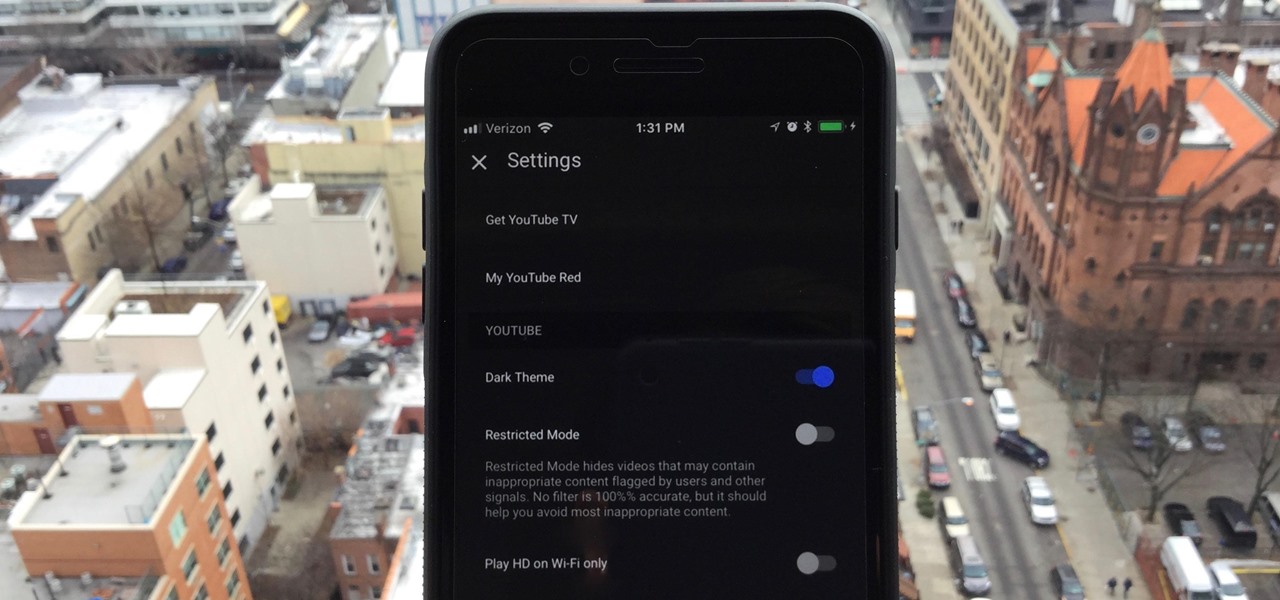
One of the downsides to iOS is the lack of a true dark mode. While Apple has offered a workaround, third-party developers have taken it upon themselves to implement dark themes in their apps. While big names like Twitter and Reddit have led the charge for some time, it appears YouTube is the next app to join the party.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

Not all remakes of video game classics turn out well, but a new augmented reality take on Super Mario is likely to draw in fans of the Nintendo hit.

If you know your internet history, then you fondly remember the Star Wars Kid and his epic lightsaber display on YouTube. Now, many years later, everyone is following in the footsteps of the Star Wars Kid thanks to the Lenovo Mirage and the new Star Wars: Jedi Challenges app.

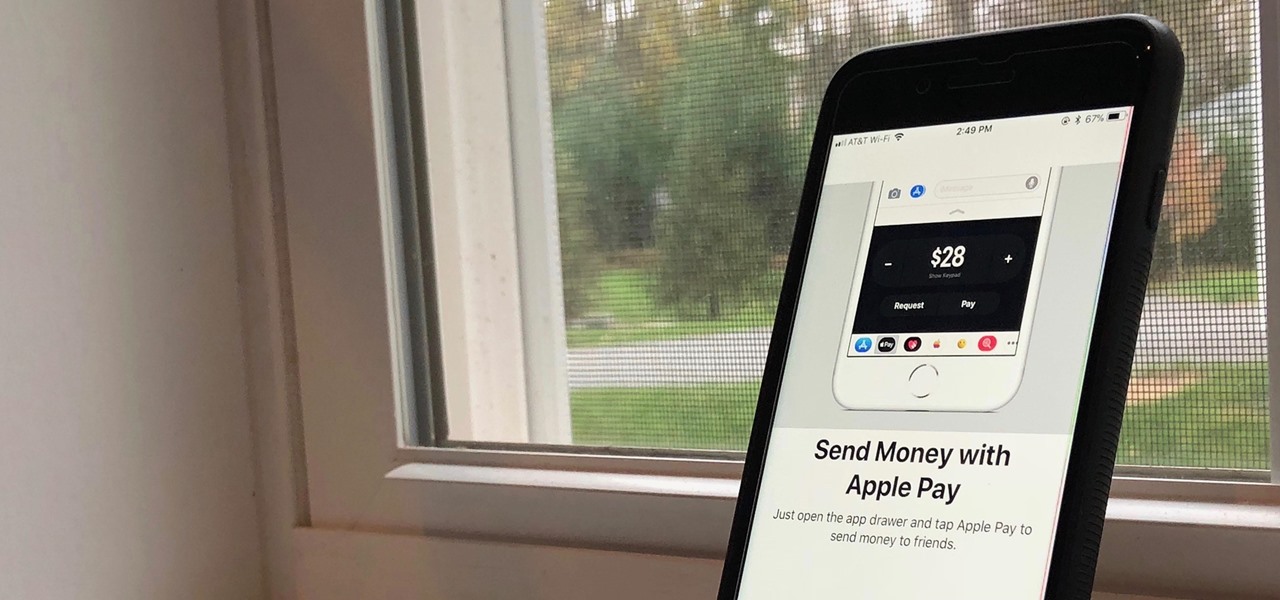
First showcased back in June at WWDC, Apple Pay Cash is Apple's answer to Venmo. Although iOS 11 has been out in the wild since September, this new iMessage feature has been mysteriously absent. That's finally changed with the second beta of iOS 11.2 — Apple Pay Cash is here.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Augmented reality dogs have been a big hit with developers using Apple's ARKit. RoVR hit YouTube a few days ago and people have been clamoring for it ever since. Not to mention the Good Dogs Game created by the people behind the famous We Rate Dogs Twitter.

Your Apple TV is just that — your Apple TV, which means you probably want to personalize it a bit, to make yours stand out from everybody else's. And the easiest way to do this is by renaming it. If you live in an apartment building, this will help differentiate your Apple TV from your neighbors' when trying to use AirPlay.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

You will soon be able to play an AR version of one of the most frustrating mobile games of all time, thanks to Apple's ARKit.

Following the most recent election, some argue that increasing political polarization is dividing Americans. A new app, called Read Across the Aisle, is aiming to combat this by encouraging users to read news from media outlets on both sides of the political spectrum.

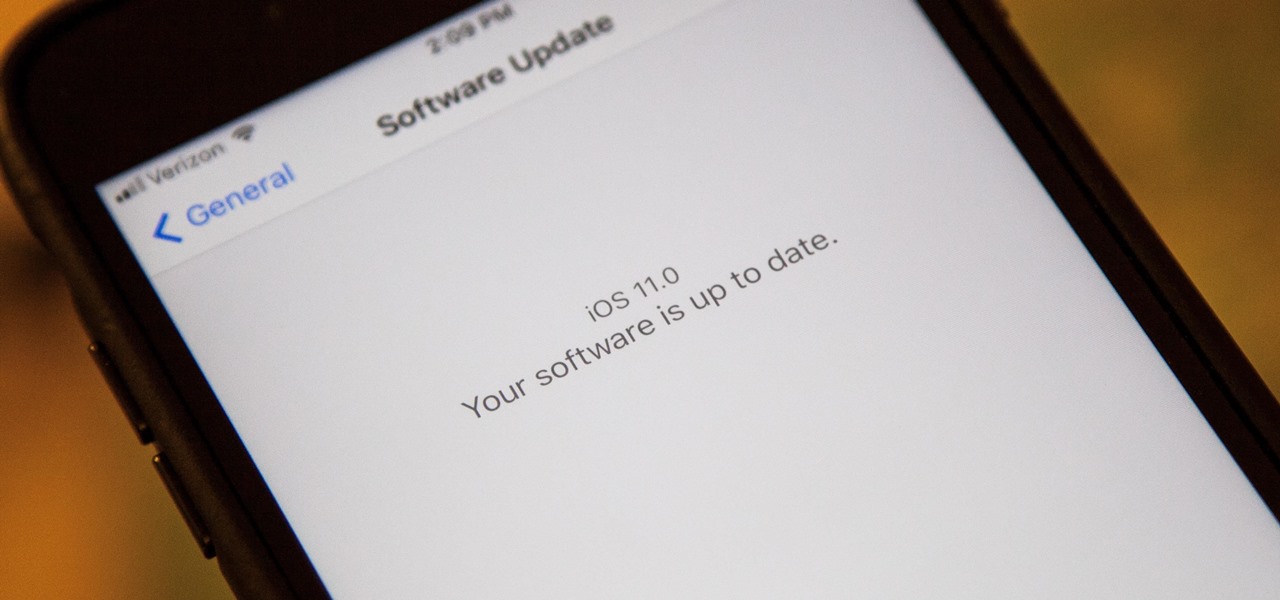
Apple promised at WWDC to release the iOS 11 public beta by the end of June, and they've just followed through on their promise.

Pokémon GO updates will have new deterrents for cheaters, and these seem to use shame more than just prevention. The changes were mentioned by a Pokémon GO support account on Reddit. (There are other updates coming soon to Pokémon GO as well.)

A new feature of Google's Gboard for Android lets users doodle an emoji in order to find it. The change was part of a few updates introduced earlier today.

Super Mario Run has been one of the most insidiously addicting iOS games to come out in recent years for iPhone. And now, as of March 22, Android users can get in on the fun, too.

Just over a month ago, the Rubik's Cube world record was smashed by Mats Valk, a Dutch speedcuber, during the Jawa Timur Open 2016. Valk was able to shave 0.16 seconds off the previous record of 4.90 seconds, which was a pretty impressive feat.

We've all been there... admit it. You sent a couple messages, but your friend had the "Read Receipts" option turned off in WhatsApp, so after a few minutes, you start wondering if they're away from their phone right now or just flat-out ignoring you.

We started with a static page and evolved to dynamic screens, and making that 2D surface interactive was a relatively straightforward transition in design. But when you can put holographic objects literally anywhere in the room, the way you design apps, games, and experiences requires a different mode of thought entirely.

If we go by the timeline set forth in Back to the Future Part II, Nike's new HyperAdapt 1.0 with adaptable lacing is at least a year late. But HyperAdapt will do more than just automatically tighten your laces—sensors in the sole of the shoe will provide a "tailored-to-the-moment" custom fit to maximize comfort and function while you jog, play sports, or navigate through hordes of aloof morons clogging the lanes at your local Trader Joe's.

This Video is about my Trying a New Braid pattern for a Crochet Weave.

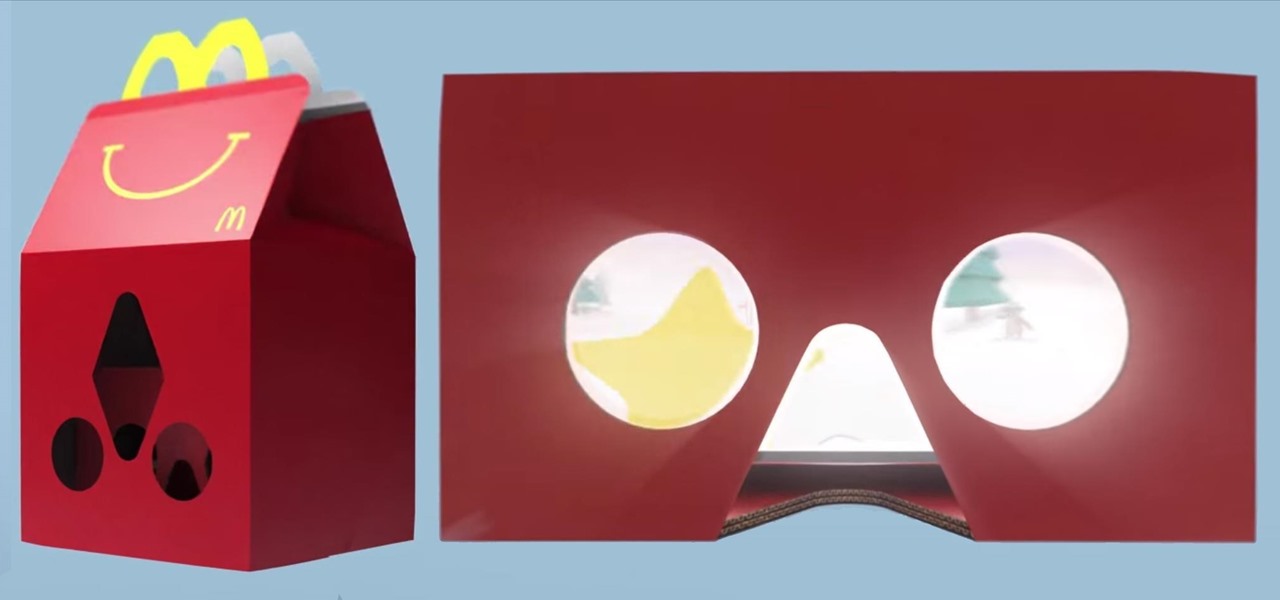
Another day, another company hopping on the virtual reality bandwagon. Today, it's fast food behemoth McDonald's, which is testing limited edition Happy Meal boxes that you can turn into a VR headset by punching out a couple holes and tearing along a few perforated seams. The resulting headset is a lot like Google Cardboard, with the lingering scent of fry grease.

The first White Hat Award for Technical Excellence tutorial contest ended last night at midnight! We had many excellent articles submitted, once again re-affirming what an incredible community we have here at Null Byte! We had quite a flurry of great articles in the last few days. Thanks to all of you who submitted such high quality material to our community. Your efforts are appreciated and you have the undying gratitude of our community. We will not forget your efforts. I'll be reading and ...

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Welcome back my friends !! Today we'll go through the second part of this C# series

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

I will Show you in this Video How I dust my Ends... PLEASE NOTE:

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Greetings my fellow hackers.

This Video will show you How to Do Two Strand Twist. I had been practicing looking at different YouTube Videos

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.