The Pro Bowl has definitely had its ups and downs. It's probably the most glorified exhibition game on earth. I mean, even the NFL Commissioner, Roger Goodell, wanted to cancel it this year.

A few weeks ago, Twitter announced that they would be creating an archive feature for its members, which they've been slowly rolling out to select users. After signing in today, I noticed the feature was finally available for my account, so I went to test it out.
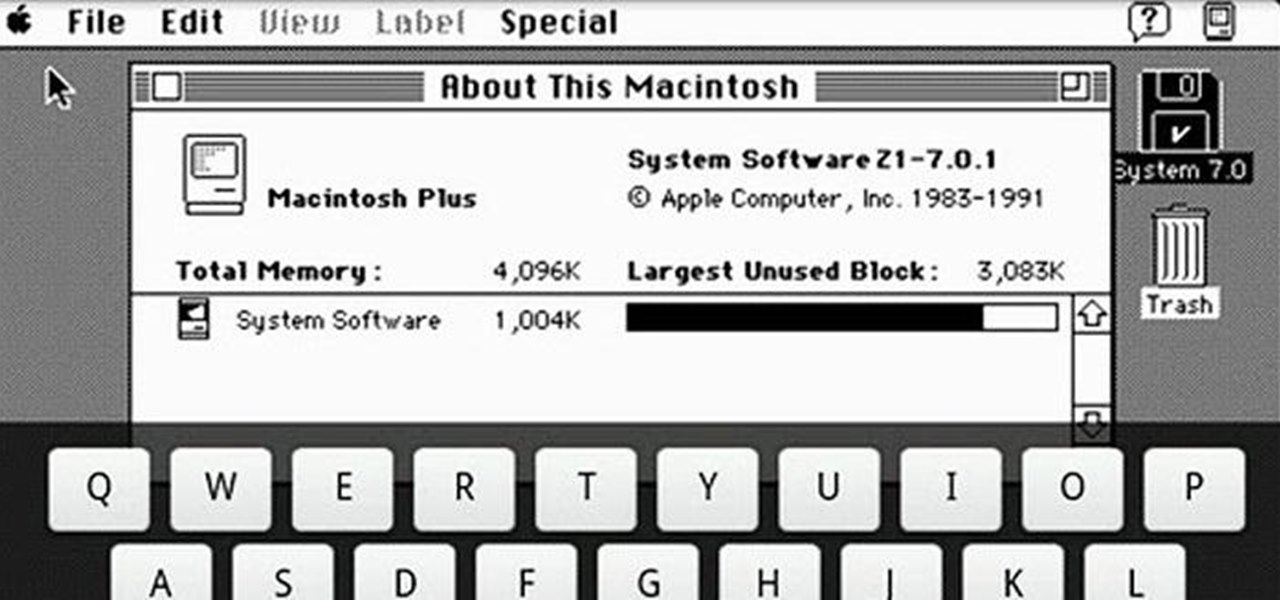
Remember these? Sadly, I don't, but I'm sure someone out there does. Anyone? This monstrosity, called the Macintosh Plus, was introduced in 1986 for the low-low price of $2,599. Wait...what? Almost three grand for that bulky baby?!? With a whopping 1MB of RAM standard?!? Whoa there...

Feeling nostalgic for Super Mario Kart, but don't want to fire up the old Super Nintendo? Never fear, with a free Flash-based emulator called SNESbox, you can relive the 90s and play all your favorite games right from your browser, without having to install anything. With 1,861 games, if there's something made for the Super Nintendo that you want to play, they almost certainly have it. Sure, there are tons of emulators you can use, but SNESbox is different in that it gives you the ability to ...

Christmas sweaters are one of those anomalies that everyone complains about, yet so many are sold every year that someone has to like them (kind of like fruitcake). Whether you're keeping tradition for tradition's sake, or secretly you actually enjoy ugly sweaters (we won't tell anyone), why not at least make this year one to remember?

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

Remember how the bad guys in Scooby Doo would always use cut-out portraits to spy on people through walls? Well, unless your landlord is super cool, you probably shouldn't start cutting holes in your wall just yet, but you can make a higher tech version, thanks to NASA employee Mark Rober. Mark used a cheap picture frame and a portrait with the eyes cut out to make the "Scoob Cam," which also doubles as a surveillance device. He used an iPhone and an iPad to start a FaceTime chat, then taped ...

At one time or another, we've all enjoyed the visualizations that came stock in Windows Media Player. I remember spending hours listening to my favorite album, putting the graphic equalizer on full screen, and getting lost in the flurry of colors that would dance across the screen. Well, now thanks to the imaginative mind of Instructables user yardleydobon, you can now recreate this rainbow-colored music visualizer right on top of your freaking head—with these trippy EL wire headphones, which...

Remember TwtRoulette? TwtRoulette was an online app that turned you into a so-called Twitter spy, letting you peruse someone's own timeline feed exactly how they saw it themselves. So, if you wanted to see what tweets Ashton Kutcher was seeing in his home timeline from the 700+ people he follows, you could.

Summer is over and autumn is here. Serotonin levels are dropping and people don't have the motivation to be outside as much anymore. So we play Minecraft instead. But walking is cumbersome, so we want minecarts. Remembering to carry one in your inventory or placing one on the tracks might be a bit much to ask for, and don't even get me started on bothering to press a button to make it go.

Keyless entry remotes are great, but they don't always work how you want them to. One of the most common complaints is that they just don't reach far enough, and there's nothing more annoying when you can't remember where you parked. After all, what's the point of having "remote" entry if you have to be right next to the car for it to work?

Sea otters are the largest members of the weasel family. When people started hunting sea otters for their fur, their population fell from roughly 225,000 to about 1,500, until the International Fur Seal Treaty took effect in 1911. Since the international ban on otter hunting, the population has rebounded back to roughly 107,000.

Need some creepy visual effects for your alien flick, but don't want to spend a bunch of money? With some pretty basic materials, you can turn an empty aquarium into a "cloud tank," which can be used to create several different atmospheric effects. Before Hollywood started using CGI, cloud tanks were used for scenes in a lot of famous movies. Remember this one? Besides Raiders of the Lost Ark, cloud tanks also helped make some wonderful non-CGI effects in Independence Day, Close Encounters of...

Remember going to the doctor when you were a kid? If the word 'traumatizing' comes to mind, you'll love the RoboDoc by MarkusB, a robotic doctor that makes checkups a little less scary (and a lot more fun) for kids. It all started when Markus took his 14-month-old daughter for a checkup. The finger clip that the doctor used to check her pulse terrified her, so Markus decided to build a heartbeat monitor just for kids that's much more likely to make them laugh than cry.

Hello! Today I would like to share the process of making your own natural marigold cream. The product does not contain any (artificial) chemical elements and therefore can be called natural. Step 1: Ingredients

Remember those Choose Your Own Adventure novels? If your school was anything like mine, they were so popular you were lucky to find one to check out at the library. But there's no worries now, thanks to this handy HTML5 app, which makes it easy to write and share your own 'choose your own adventure' novels. inklewriter is a free tool designed to make writing interactive stories simple. Basically, you start typing and inklewriter helps you organize your story, making it easy to add, remove and...

If you are like me and you have a old iPhone and you don't want to buy a new one, you can fake your ios version by fallowing this tutorial. Just to be safe i am not responsible for what you do with this or if you mess up and wreck your phone. Plus ios and iPhone all belong to their rightful owners.

A minigame we built with redstone! Video: .

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. This past Saturday we had a great turn out for the Weekly Workshop, and we even managed to get a few of you in TeamSpeak. Thanks to all who joined in, hope you learned some awesome new things!

Since the days of Archytas, rocket propulsion has been the Holy Grail of aeronautics. Thanks to Galileo's inertia, Newton's laws of motion, and the "father of modern rocketry," Goddard, space is not a complete mystery anymore. Rocket-powered aircrafts have evolved from the first liquid fuel rocket in 1926, to the Soviet R-7 which launched Sputnik, to NASA's Saturn V that propelled Apollo 11 to the moon. Today, even billionaire tourists can enjoy space, like Microsoft's Charles Simonyi and Cir...

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

Since iCloud's introduction in 2011, you get only 5 GB of complimentary cloud storage with your Apple account. With iPhone backups, app data, iCloud Drive files, and even emails (if you have a Mac, Me, or iCloud email address), you'll quickly run out of space to back up photos and videos. Fortunately, Google offers 15 GB of free storage, making it easy to upload your Camera Roll for safekeeping.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

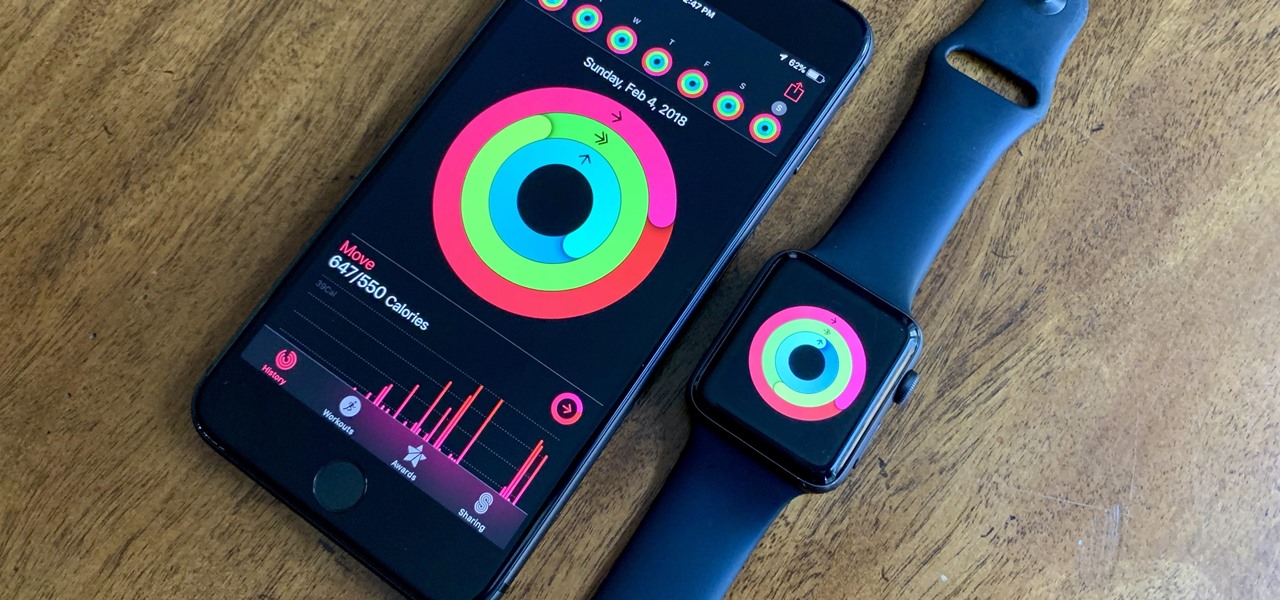
Apple Watch owners know the struggle — it's the end of the day, and those rings aren't met. Whether you forgot your watch before hitting the gym, let the battery run out, or just didn't move enough, you could feel the sting of fitness failure. But it doesn't have to be this way. You can actually close your Activity rings yourself; it just takes a little know-how.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

There's no denying that there are some seriously useful new features in iOS 11 for iPhone. But there's also no denying that Apple got a few things wrong with the latest iOS update, as well as left a few important features out.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Word games fit perfectly with the on-the-go nature of mobile gaming. They're easy to pick up whenever you feel like exercising your brain, but they're also fairly easy to put down when you need to get back to the real world.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

What if the code you are trying to reverse engineer is obfuscated or somehow corrupted? What if no way is left? Here comes what I like to call (wrongly and ironically) the "brute force of reverse engineering".

This time it's serious. Really. The largest web security vulnerability of all time went public on Monday, April 7th, 2014, resulting in widespread panic throughout the Internet as system administrators scrambled to secure their websites from the OpenSSL bug known as Heartbleed.

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

If you've been to a convention of any sort before, you know that there are good and bad panels, and that their inherent goodness or badness often has little to do with the actual content being discussed. That's because giving a panel is a skill that not everyone has. However, it is a skill that everyone could have! In this article, I'll tell you how to give a good panel on practically any subject. Image by Shannon Cottrell