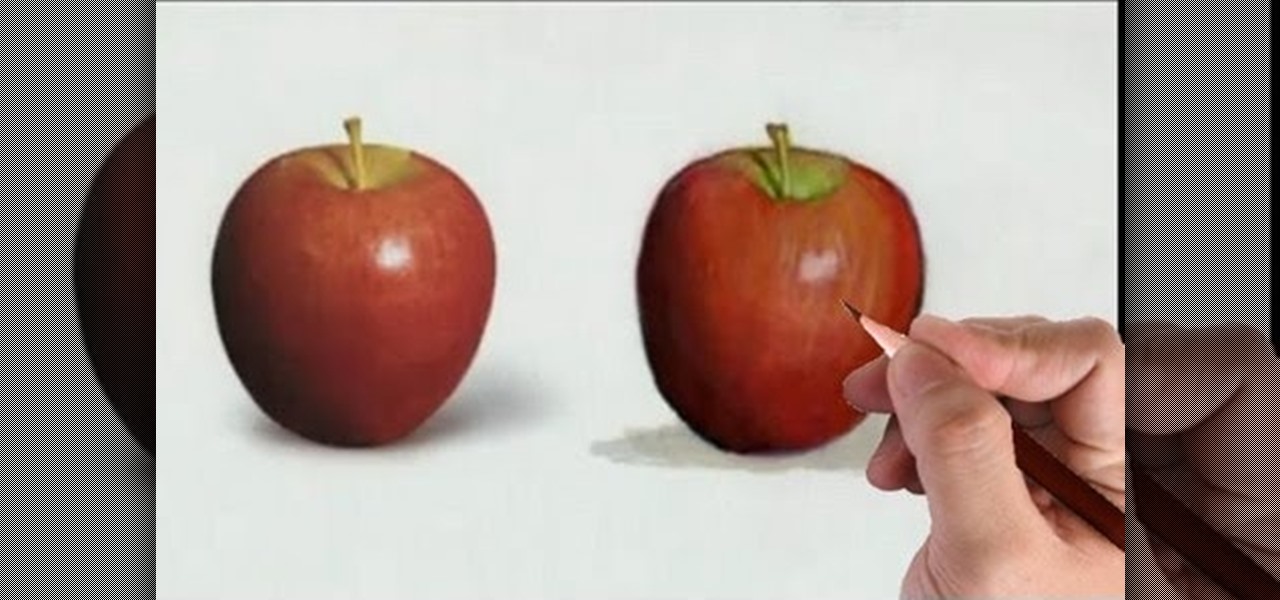
Watch this fine art video tutorial to learn how to illustrate with markers and colored pencils. "This video shows my process for making an illustration (non tradigital). I use illustration markers (usually prismacolor) and color pencils (usually prisma once again) and a wax blending stick. I make my illustrations in two steps:

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

Power Armor that isn't faction based, mostly around the Brotherhood of Steel, is very hard to come by in Fallout New Vegas. Wearing faction based armor can have negative effects if you're traveling in the territory of a faction that doesn't like that faction, regardless of your standing with that faction. Now THAT's a mouthful! But, there is a suit of Enclave Remnant Power Armor laying at the crashed Enclave Vertibird. Check out this video for the location of the Power Armor!

There are zillions of fun and cool things you can do with guitars, including riffs, hammer down, and so on. But in order to unleash the rock star that we know is hidden deep within you, you have to start with the basics first.
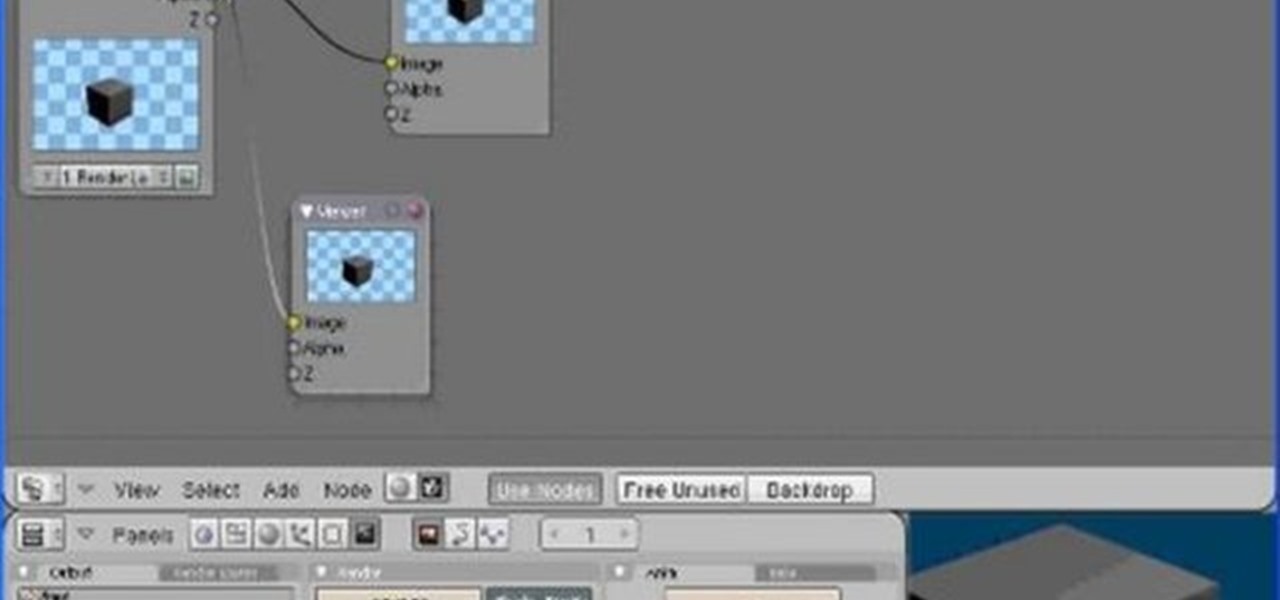
Conceptually, what is node-based compositing and what do nodes do? This clip uses the factory analogy to convey the concept. Blender can process video, images, sequences, and families of images in a directory. Then you'll fire up Blender and talk about threading nodes and how images are duplicated and routed through the compositing network ("noodle"), how threads are created between sockets. Creating threads, cut threads. The clip also points out common threading errors and misrouting threads...

A major Hollywood player since she was a preteen, Vanessa Hudgens knows what looks on the red carpet and what doesn't. And, like most girls, she's found that the smokey eye never fails to make your eyes pop and to the make the eyes of nearby cartoon wolves pop out.

In this tutorial, from Zappos, learn how to make a simple stop motion video. This process is a lot easier than you would expect and this video is here to give you a step by step.

This is a video that explains to a person how to write their name in Japanese. The woman shows two ways as to how to translate your name in Japanese. The first is how the name is pronounced, and the second way is to translate your name based on the meaning. Usually the name is translated based on pronunciation in the native language. The name is pronounced similarly but not exactly the same. For example Rachel is pronounced "Reicheru". She also shows a website where more information can be fo...

This video describes how to make a "no calorie" birthday cake centerpiece with carnations in soft and sweet hues of pink, yellow, white and cantaloupe. first a flower foam was taken. Then the toothpicks were used to join the flower foam together. Then trace out a circle from the foam using a kitchen knife. Add some water to the base of the cake. With equal size flowers decorate the base of the cake. Then the cake is beautifully covered with different types of flowers. decorate with as many fl...

In this video tutorial, viewers learn how to make a Midori based "Green Iguana" cocktail. The video lists all the required ingredients to make a "Green Iguana" cocktail. The ingredients include: an ounce of Midori, half an ounce of tequila and 2 ounces of homemade sweet sour mix. To make the "Green Iguana" cocktail, follow these steps: mix all three ingredients in a cup, mix ingredients by shaking and add ice. This video will benefit those adult viewers who enjoy alcoholic beverages and are w...

This video teaches the secrets of applying flawless false lashes. An excellent summary is given below. First hold the lashes with tweezers to your eyelash to check the size of it. Cut it off a bit if the false lashes are big compared to your eyelashes. Now apply some glue carefully to the base of the false eyelash. Close your eyes and stick the false lashes to the base of your eyelash and hold it for a few seconds to let it dry. After the glue gets dried blend the false lashes to match with y...

In this video tutorial, Chris Pels will show several aspects of defining and using master pages in an ASP.NET web site. First, see how to create master pages declaratively using the ASP.NET master page model and learn what information is best suited to a master page compared to an individual content page. Next, see how to programmatically assign master pages on-the-fly in an individual content page. Also learn how to create a base page class which assigns a master page programmatically for al...

While Google Stadia currently needs to be sideloaded on Chromecast with Google TV, there are a handful of games that are compatible with the streaming device and require a gamepad. But you don't need to buy a specific controller just for your Chromecast, you can use one you already have lying around.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

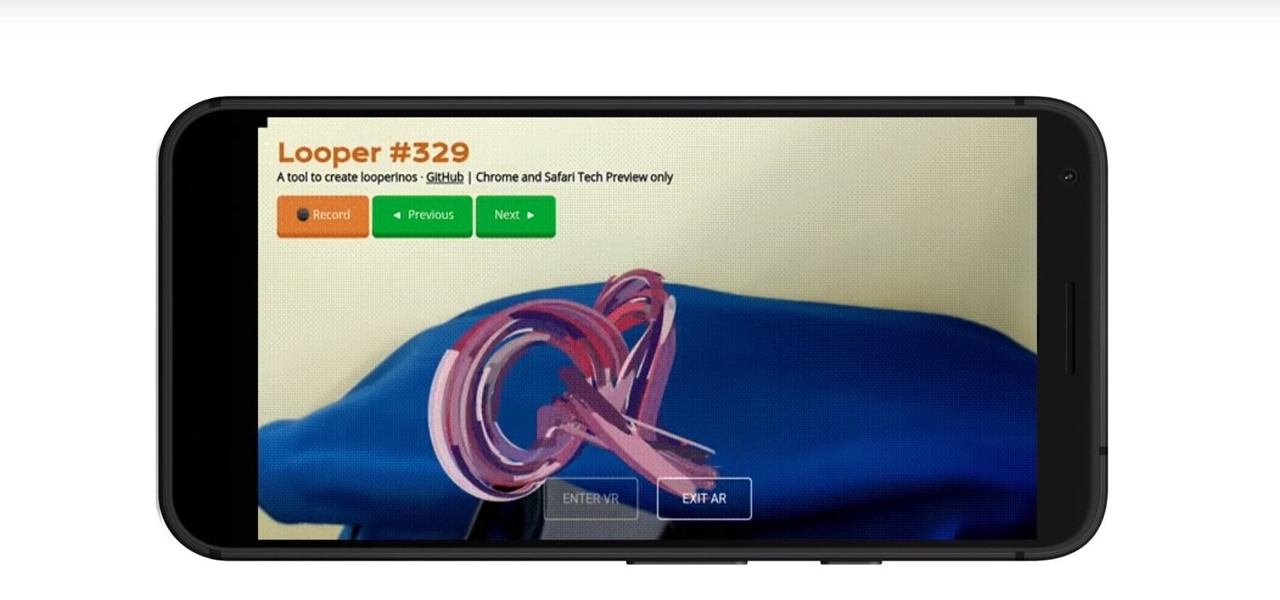
Web-based mobile augmented reality technology continues to gain momentum as Google is set to expand the standard for immersive web content to AR.

In iOS 13, Apple added an important new feature to its HomeKit smart home ecosystem called HomeKit Secure Video. With it, you have a secure, private way to store and access recordings from your smart home IoT cameras.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Apple released iOS 12.3, the latest version iOS 12 for iPhone, on May 13. Great features to know about include Apple TV Channels such as HBO and Showtime that you can subscribe to in the TV app, support for audio, image, and video streaming to AirPlay 2-enabled TVs, and the ability to use Apple Pay to pay for content and subscriptions inside Apple's own apps.

Every year, fans of Irish culture, as well as those looking to celebrate their own culture, come together on St. Patrick's Day, March 17.

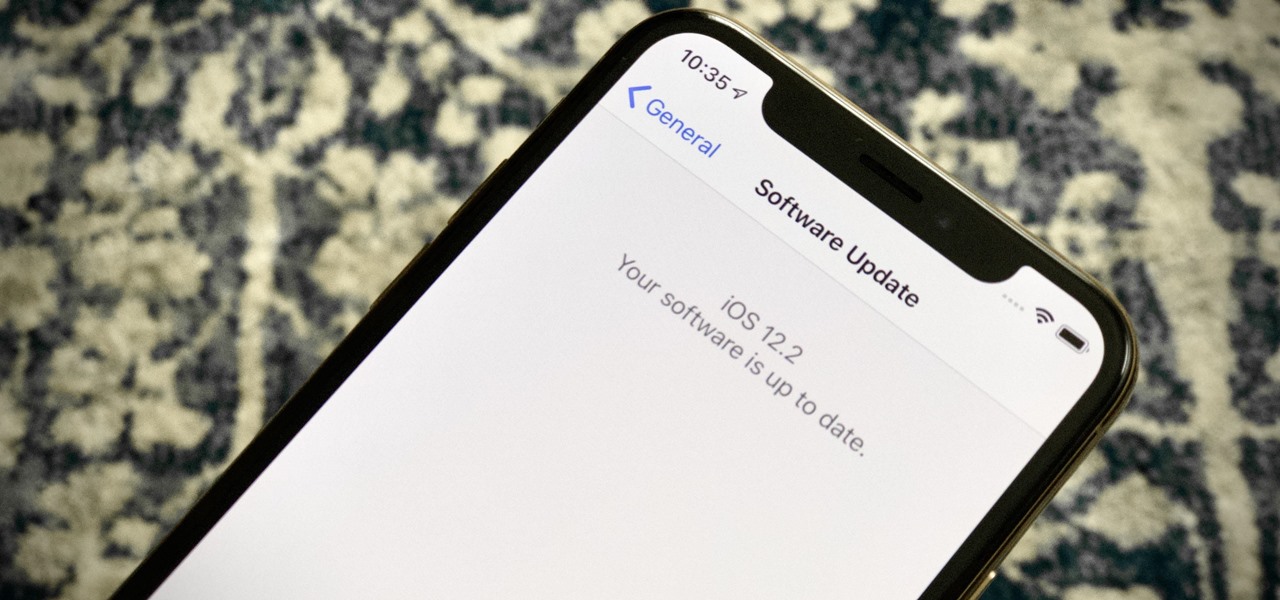
If you're an iOS app developer, your Monday just got better; Apple just released iOS 12.2 developer beta 5 to your Software Updates today, March 11. This fifth beta includes a number of small UI changes and tweaks, and likely some degree of under-the-hood improvements and bug fixes.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Zenko Games makes no apologies for its influences. In fact, they cite them explicitly in their own promotional materials for Diamonst AR.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

Rooting a phone lets us install custom operating systems, known as ROMs, which replace the device's preinstalled OS. Most custom ROMs are based on code from the Android Open Source Project (AOSP), which gives them a look and feel similar to Google's version of stock Android. But every now and then, you'll see a ROM that isn't based on Android, though these are few and far between — at least, until now.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Returning your device to stock, whether it is because you need to sell it or just want to receive OTAs again, is not always a simple process. Since HTC has released countless variations of both the M7 and M8 HTC One, it can be a pain in the ass finding the right files and tools to get your phone back to stock settings.

For the most part, transferring files from your computer to your Nexus 7 (and vice versa) is a simple process. Just hook up your tablet to your computer with the USB cable and transfer. However, most of the time you'll need additional software on your computer to do this, and then, of course, you need the USB cable.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

First of all, you must get in to the screen and start to made a base for your ice rocket. Then you chose your pen size and start to draw the ignition rocket body and the base for the ignition metal for your rocket.

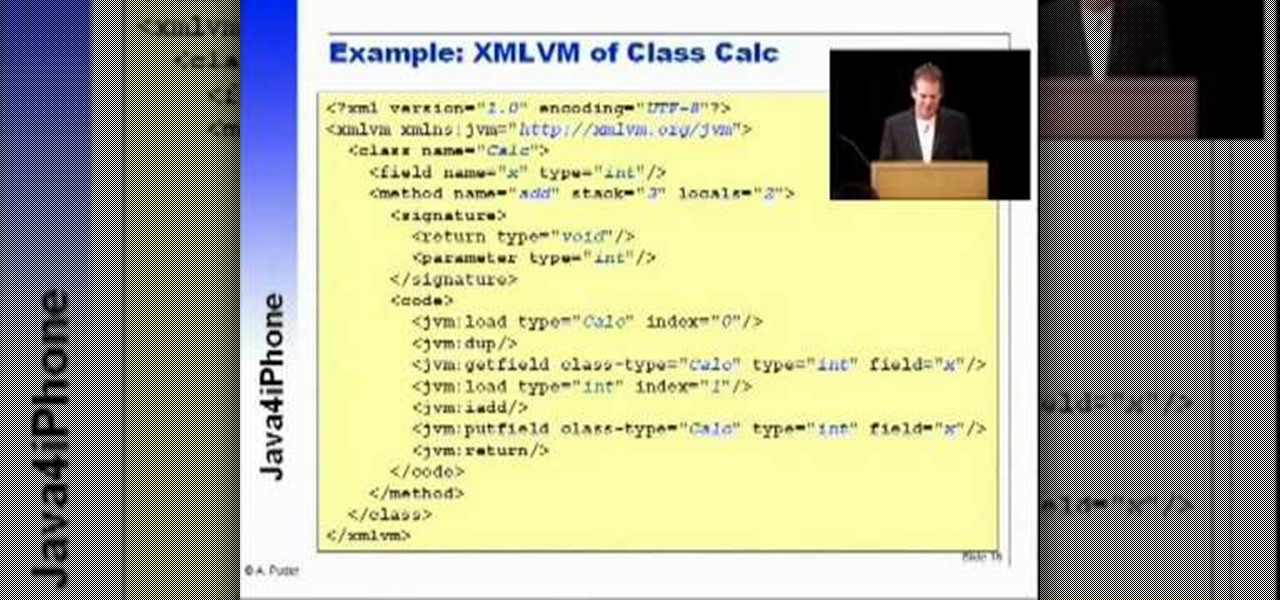
Arno Puder, a master of the XML coding field, gives a great rundown of Apple's new proprietary Java coding. This is especially helpful for Cocoa implementation

This video shows you how to use couplers for cake decoration using these steps: 1. Couplers usually come in two plastic pieces, a base and a ring. This system fits inside cake decorating bags or cones and allows you to use the same icing with different tips.

Before you whip out your iPhone and call your neighborhood plumber for a job that's sure to cost you a pretty penny, check out this video to learn how to do some impressive plumbing yourself. Using a few tools you probably already have lying around your house, you'll learn how to install a shower base in your shower unit and then connect it with the drain - effectively, you'll be setting up a plumbing system.

Watch this video for instructions on making the Yukki Cross Artemis scythe from the anime / manga Vampire Knight.

Many people think that once they start a business of their own they'll be cruisin' through life. No set hours, no boss to insult you, and no getting up at 6 AM to commute to work. But being your own boss comes with a lot of responsibility. If you're ready to take the good with the bad, check out this video to learn how to begin a home-based business.