We've all played with LEGOs at some point in our childhood, but when video games took over the world, we all converted to PlayStations and Xboxes in lieu of building blocks. But soon enough, the satisfaction of childhood construction was integrated into video game format, so we could once again love LEGOs. With LEGO video games like LEGO Harry Potter, LEGO Indiana Jones, LEGO Star Wars, what could go wrong? Nothing. But before those games, there was another, based not off of popular movies, b...

The first thing you need to do in this mission on Battlefield Bad Company 2 is to hop out of the copter and get in the sand buggy and head to your marked location. You'll need to locate and head to each station on the map: Bravo Base Station, Charlie Base Station, and Alpha Base Station. After that, complete the Triangulation Point. Watch this video walkthrough to learn how to complete the Sangre Del Toro mission in Bad Company 2 on the PS3.

First of all cut of the top and the bottom of the cylinder to get two circles. Now take a scissors and cut of the cylinder into two halves from the top to the bottom as shown. Now you get a rectangle shape. You can easily measure the length of the cylinder but to measure the base is a problem. So mark a point on the table with tape and also make a mark on the can or the object you want to measure. Now place the two points over each other. Now use a ruler as a guide and move the can so that th...

Sue McMahon, Cookery Editor of Womens Weekly, shows how to decorate your Christmas cake, in this video. She begins by turning over a rich plum cake to have a smooth surface for the decoration. Next, she pours some brandy over the cake to moisten it. She uses apricot glaze and spreads it evenly over the surface and sides of the cake. She kneads ready-made marzipan to make it smooth. Next, she dusts some icing sugar on the work top and rolls over the marzipan into a circle, large enough to cove...

This video will show you how to have an androgynous high fashion look. Use dark blue eyeshadow as base extending to your lower lids. Use dark plumage (Mac) or any dark shade (purple or blue) over the base color. Use an eyeliner for the lids and lower lash line and put some matte black eyeshadow on top of it. Apply an eyeshadow, same color as your face, for the highlights. Use an eye brow pencil for the brows and black carbon eyeshadow on the base of your brows. Use brush to blend and apply cl...
Stand with feet shoulder width apart. Shifting your weight to one leg, bend your knee while slightly lifting your other leg off the ground.

Changing a toilet is really not the dirty and difficult job that you would imagine. Start by turning the water off using the valve that is located on the wall. Empty the tank by flushing the toilet and holding up the drain valve. Soak up the excess water with a sponge. Disconnect the water line and loosen the bolts that hold the toilet down. Cut through the caulk seal at the bottom of the toilet. Remove the toilet and the wax ring that is around the opening of the drain. Remove the wax ring a...

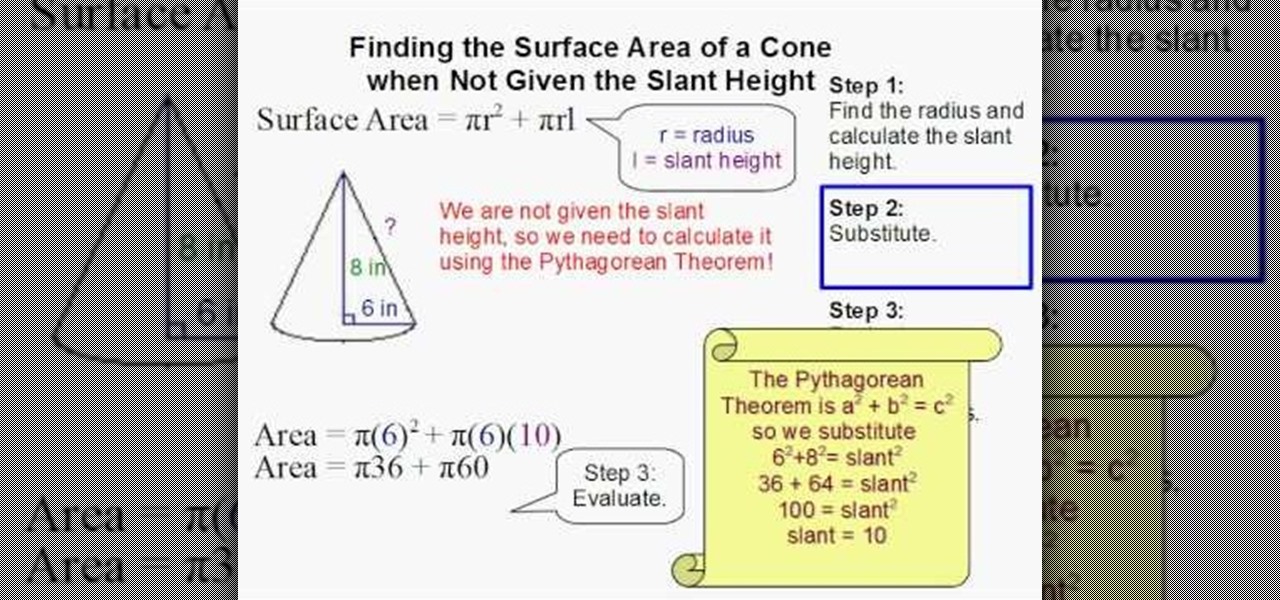
Math always seems hardest until someone shows you how to do the problem and then it all seems just so simple. This video will walk you through the process of finding the surface area of a cone when you also have to derive the slant height. Use this example to help with your other cone problems.

Before you start a paint job you will need to prime the surface of the wall. Priming is necessary if the wall is a dark color or stained or bumpy at all. Once you've decided to prime and paint, check out this tutorial for advice on how to go about it.

As businesses flocked to Zoom, Microsoft Teams, Google Meet, and other video conferencing platforms to bridge the gap, we wondered aloud -- why aren't more companies leaning even more heavily on augmented reality?

If you've ever needed to prove you have remote access to a device, or simply want a way to convince someone their computer is haunted, SSH can be used to make a device begin to show signs of being possessed.

Silicon Valley-based startup 8th Wall has spent much of the last few years building a reputation for enabling AR experiences that are platform agnostic via web browsers and mobile apps. Now, 8th Wall is promising to give developers the freedom to build and host AR experiences from anywhere via a simple web browser.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

A few months ago, iOS 12.1 came out with a handful of useful new features, and iOS 12.2 goes even further. While some of iOS 12.2's new features for iPhone are much welcomed, there are some that we'd be better without.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals with their products, as both now appear to be interested in making AR headsets for the military.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Christmas came early for Apple, as the company was awarded more than 40 patents by the US Patent and Trademark Office on Tuesday, including one covering a system for compositing an augmented reality construct based on image recognition.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Surveillance is always a useful tool in a hacker's arsenal, whether deployed offensively or defensively. Watching targets yourself isn't always practical, and traditional surveillance camera systems can be costly, lacking in capabilities, or both. Today, we will use motionEyeOS running on a Raspberry Pi Zero to create a small, concealable Wi-Fi connected spy camera that is both affordable and easily concealed.

The world of gaming has never been cooler thanks to Apple's ARKit. From AR arcade games to giant god battles to Pac-Man, we've seen our fair share of awesome and innovative games.

We admit it: we are ranch dressing fanatics. We like to put it on our simple salads, spread it across our chicken wings, and dip homemade sweet potato fries in it. Plus, since childhood, neither of us can eat pizza without ranch dressing to accompany it.

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

I've been involved in the Android scene for a very long time and have grown to develop a love/hate relationship with CyanogenMod. While I do like the stability they offer in their custom ROMs, they don't always include the flashy features on top of their vanilla Android base.

Instant ramen and just-add-water noodles are lifesavers because they are convenient and fast, but they are also usually chock-full of processed ingredients and unrecognizable pieces of dehydrated meat and vegetables.

Apple's keyboard has a set of media controls to navigate the music playing on iTunes, allowing you to play, pause, skip, and replay songs and videos. Unfortunately, these controls are exclusive to iTunes; if you're playing music from Spotify, Pandora, or the myriad of other online web-based services (Amazon, Rdio, SoundCloud, etc.), you're out of luck.

This article is for anyone wanting to learn how to do gel nails at home. Although it is easy. It is time consuming, so be prepared to have at least 30 minutes to do all the steps. We chose to do gel nails with a french press tip.

Hey guys, I was building my floating island earlier today (and having a quick look at the competition) and I came up with a couple of hints and tips that will really improve your islands.

Yes! soon I will be able to log in more as I untie the shackles this map has placed on me in the time leading up to its eventual release and log in once in a while!

Leah for May Arts Ribbon shows how to make a flower loop bow. The following items are needed for it: Needle and thread, scissors, May Art Ribbons and a ruler. Buttons or flowers may also be needed to put on top of your bow as per your selection.

In order to make a Silicone Ring Mold you should first get a small plastic container. This will be your mold box. First, you should cut the bottom out of the container. Next, use double sided tape to stick the ring down to the base of this. Next, secure the mold walls to the base. Now, mix the silicone mix in a separate mixing cup. Make sure you mix this thoroughly until the color is uniform. Now pour the silicone into the mold in a fine stream on the side of the ring, this will help prevent ...

Demons sure are scary but a ‘Cartoon Demon’ does appeal to anyone for sure. Learn how to draw one, by watching this video. Begin the skeletal outline, by tracing an oval shape. Then draw an oval, overlapping the first one horizontally, at the base. Draw two elf like ears, on either sides of the top oval. Draw a small neck from the base of the fist oval and a line beneath it. Join the edges of the line with a deep curve for the body. Draw two curves away from each other, near the base of the b...