Spotify is how I listen to almost all of my music; I use it on my way to work, while I workout, and even while I'm in the shower. And more often than not, I use my Spotify account on various devices including my MacBook, iPhone, and LG G3. In order to make listening to music across multiple devices even more convenient, Spotify released “Spotify Connect” earlier this month.

Sometimes, ceiling fans just don't cut it. They spin meekly, barely generating any air flow to cool down your sweltering room. Or, when turned up high, they can wobble wildly, shaking and vibrating as if the ceiling is about to come crashing down. If this sounds like your ceiling fan, chances are the solution is a simple as flipping a switch.

Whether you're trying to get an unconventional angle or just want to include yourself in the picture, there are plenty of times when a remote trigger can come in really handy. Of course, if you want to buy one, you have tons of options. But if you already have an Xbox 360 headset, all you have to do is plug it in. YouTube user Gurnarok accidentally found that by plugging his Xbox headset into his camera's remote port, the on/off toggle triggered the shutter release and flash.

Yesterday, we pointed out that hackers could remote-wipe certain Android-based Samsung smartphones like the Galaxy S III using a USSD exploit. All they have to do is hide a small code into any webpage or text—even barcodes—then once you click on it, the phone resets to factory settings in a matter of seconds. The video below shows just how easy it is.

Go to web browser, click on tools- under tools click on 'Fire ftp.' Add an account to get into recall server. Under 'MANAGE ACCOUNTS' - click 'Add new one.' In host type 'Recall.(yourserver.)' then click on 'anonymous.' Click 'okay.' Now hit 'Connect.' the ftp server is then going to connect to your remote server. On right side you can see the remote server and it's file structure. Clicking on plus button (+) will expand the file tree structure. At this point you can see all the folders but y...

This tutorial shows you how to set up the high voltage wiring for your RC kit. Although this is not a basic step for putting together your RC vehicle, it can be used to help make things easier. Be careful though, this can mess up your ability to use a remote control. So pay attention and enjoy!

So you want to control the flashes on your camera using a remote, and you know that you need to get to Master mode on your Canon 580EX II to be able to do that. But Canon made Master mode for this particular model of camera very difficult to locate and enable. However, this video shows you every single step you need to take with your camera in order to be able to set up this particular functionality for your next shoot!

These days, with so many digital distractions clogging the cloud - Twitter, Facebook, Blackberries, and iPads just to name a few - very few of us spend quality time just talking and cooking and eating with those we love. Take some time out to remember what it felt like to move without a Wii remote by learning how to pick blackberries and preserve jam.

Few Bluetooth users realize that Bluetooth headsets can be hacked or otherwise exploited to a remote attacker the ability to record and inject audio through the headset while the device is not in an active call. SANS Institute author and senior instructor Joshua Wright demonstrates, and explains, the security vulnerability in this how-to. For more information, including step-by-step instructions on how you can replicate this hack yourself, take a look.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

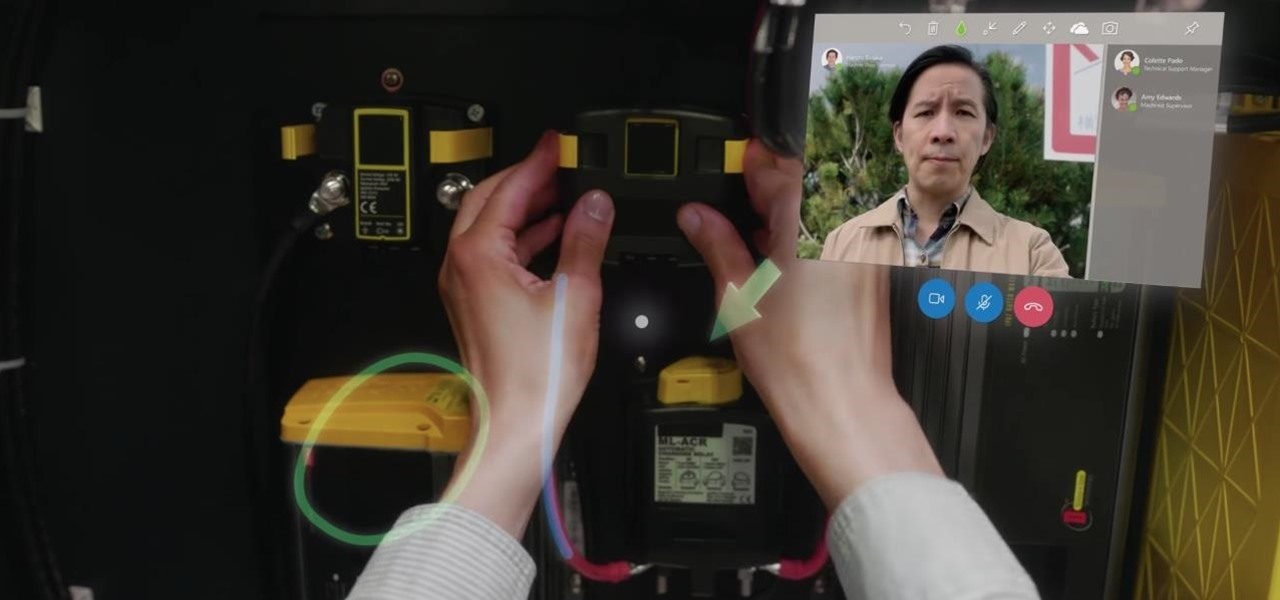
Mixed reality developer Arvizio has updated its MR Studio software suite to integrate processing of 3D light detection and ranging (LiDAR) point clouds.

While you can do a lot of things on your smartphone that were once only done on a computer, having a laptop is still necessary and critical for many tasks. Often times, the two devices work very well together.

While the Play Store has a plethora of apps available for finding lost Android phones, Google came out with its own web-based application, Google Device Manager, earlier this year to help you keep track of all your Android devices and remote lock, erase, ring, and track if need be.

Normally a remote control car only comes with four body clips. Body clips tend to get misplaced, or they fall off of the remote control car quite easily. For quick maneuvering, attach extra body clips directly to the body of the car.

If you're a fan of remote control vehicles or plan on taking up the hobby, you'll need to know some tricks and tips. From putting together the tires for your vehicle to properly painting certain parts of the car.

Squirrelod shows you how to put together a shock assembly or a shock absorber on a Factory Team remote control car kit. He takes us through building the piston - shaft, dampener, nuts and over rings step by step. Practical tips and tricks involved in building up the shaft and the recommended oil used are presented. This is not something that should be done in a hurry since time is needed to let the oil settle thus removing any air bubbles in the piston. Although the instructions for different...

It's simple: if you've got a brushed motor, you'll want to break it in under controlled circumstances before taking it out into the world. Why break in your engine? The main idea of breaking in your engine is to wear down your engine's brush so as to maximize surface contact with the commutator, reducing resistance (and therefore waste energy) and thereby increasing power. For detailed instructions on breaking in your remote control vehicle's engine, watch this RC hobbyest how-to.

Check out this five-part video tutorial on how to use fiberglass finish over balsa wood for RC airplanes. If you like building engines and bodies for remote-controlled vehicles (airplanes), then this will definitely help you out, just by learning how to apply simple fiberglass to the balsa wood parts of the RC airplane body. You will learn all of the tricks needed for fiberglassing.

In this tutorial, we learn how to make your home safe and secure with tips from Lowe's. You should do a safety check on your house at least once a year. Start with the entryway, making sure you have an insulated wood door in the doorway. Make sure there is a lock and a deadbolt lock on the door as well. Once inside, make sure you have timers to control your lighting, so it can come on even when you're not at home to detract any robbers. In the garage, make sure you have an electronic door ope...

Kip Kay, from Make Magazine, shows you how to take your radio controlled vehicle and turn it into a spy car, by mounting a camera onto it. Follow Kip, as he shows you how to remove the body from your radio controlled car, mount the camera inside the chassis using the triPod mounting screw hole on your video camera, and put it all back together. In just few short steps you, too, can have your very own radio controlled spy car.

iPod and iPhone home automation remote control using Girder is only an install away. Run the lights, heat, security system among other things in your space age home for the 21st century. Make your home a modern marvel with this app for iPhone.

If you call yourself a hobbyist or a kid at heart, you know that remote-controlled vehicles are more than just fun. If you're a serious R/C man, you'll know all about doing everything to your model truck or car, like fixing wheels, vamping the pinion gears, waterproofing, troubleshooting, electronic diagnostics, setting up, programming, and finally... racing. As much as you know about these remote-controlled vehicles, it will never be enough; you'll always be looking for more...

The COVID-19 pandemic forced many businesses into remote work models, whether they were ready or not, making Zoom a household (or home office) name for its video conferencing service.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

After three rounds of beta testing, Apple finally released iOS 13.3.1 today, Jan. 28. It's the latest update to iOS 13, coming exactly seven weeks after the release of iOS 13.3. So, what's new?

Norway-based production tools company Vizrt is putting the real into augmented reality with its broadcast AR solution that's designed to keep sports fans (and other audiences) watching.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

On Monday, at its annual Build developer conference, Microsoft revealed two new apps for the HoloLens apps.

A recent TED Talk makes a strong case for the healthcare industry to adopt augmented reality as a means to expanding access to surgical care across the globe.

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

The Samsung Galaxy S4 is a great smartphone, but do you know all the tips and tricks within the handset?

Most folks mistakingly think that slime - or green silly putty - simply can't be whipped up without borax. But the buffer solution can easily be replaced by another ingredient that you already have lying around in your house: laundry detergent.

Were you aware that you can use your Nokia N900 mobile phone as a remote controller for your Sony PS3? It's easy! So easy, in fact, that this N900 owner's guide can present a complete overview of the complete process in just under three minutes. For all of the details, including step-by-step instructions, take a look.

Want to know how to pair your Wiimote controller with your Nintendo Wii video game console? It's easy! So easy, in fact, that this Wii owners' guide from the folks at Butterscotch can present a complete overview of the process in about two minutes. For more information and detailed instructions, take a look.

In this video tutorial, we learn how to set up an Apple iPad as a remote control for PreSonus StudioLive 24. Whether you're new to PreSonus' DAW or new to digital recording more generally, you're sure to find much to take away from this free video software tutorial. Take a look.

In this clip, you'll learn how to use your Apple iPod Touch or iPhone to remotely control iTunes. For more information, including detailed, step-by-step instructions, and to get started using your iPhone or iPod Touch as a remote control for you iTunes library, take a look.

VPN's are an invaluable set up for small business', and larger business', when it comes to keeping your information secure with remote employee's. This video details all of the info that you need to know about setting up and maintaining a great VPN!

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to make a Starship Troopers (film, not book) style map where a group of Terrans have to defend a remote...

Learn how to configure the features in F5's FirePass v7 SSL VPN Endpoint Security. Peter Silva shows some of the new Endpoint Security features in the recent FirePass v7 release. Watch how to create policies, enforce host checks and other protective measures for your Remote Access deployments. For more information, and to get started configuring your own installation of FirePass v7, take a look.

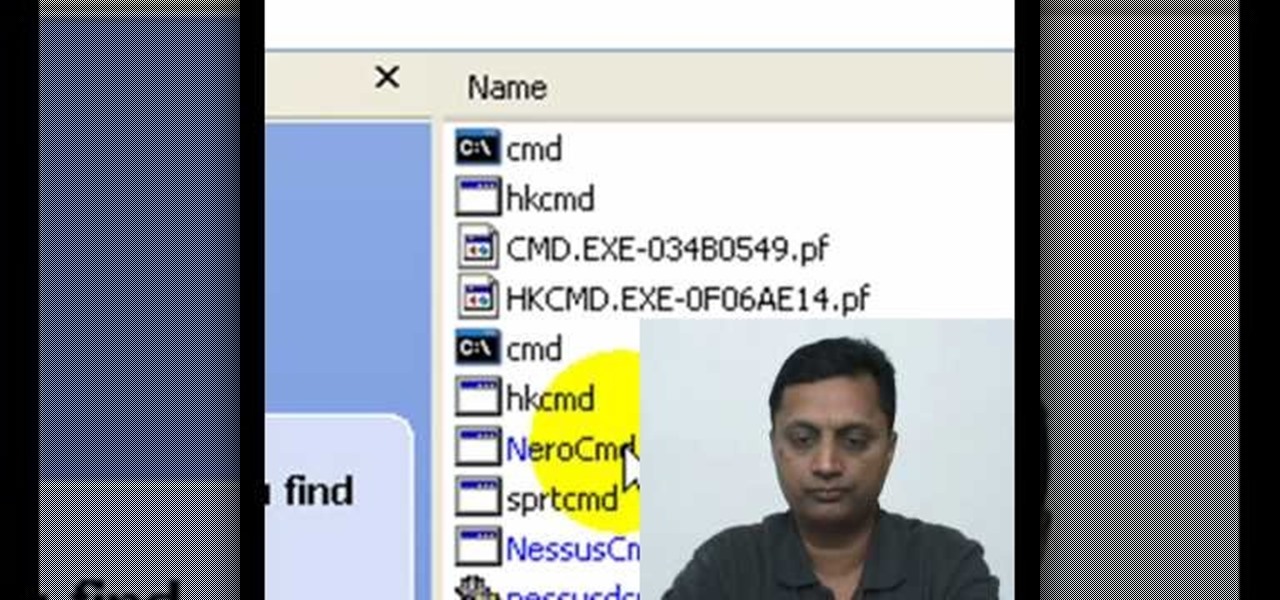
Here is a basic walk-through of how to remove the harmful file known as the cmdd.exe. The cmdd.exe file is a backdoor trojan virus that can allow a hacker remote access to a computer infected with it. Your computer can be infected with this threatening virus at any time and it must be removed immediately. This video provides several techniques that can be used to completely get rid of the file from your computer.