All Kohl's wants for Christmas is Snapchat augmented reality. In conjunction with a holiday pop-up hosted in New York City from Nov. 7 through Nov. 10, Snapchat ran a sponsored portal lens available to targeted Snapchat users in the AR carousel. The experience gave users the ability to virtually transport themselves to the pop-up.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

All the cash Magic Leap is amassing is probably going a long way toward hardware development and manufacturing, but it's also becoming increasingly clear that a large portion of that cash will be devoted to content. The latest proof is a new partnership between Magic Leap and the UK's Royal Shakespeare Company (RSC).

In just a few days, all the Galaxy S9 and S9+ leaks will come to an end, as Samsung will officially unveil its latest top-tier smartphone. But before that happens, we're all getting another leaked image of the handset thanks to a bit of snooping and the magic of augmented reality.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

While it might be a little past its prime now, the running gag about Nokia phones never breaking was one of the internet's favorite jokes. "If you buy one," they would say, "you'll never need another phone again." I think if those users could see into the future, they'd change their tune, as the Nokia 6 is now available to preorder — and I'm guessing it would give any of Nokia's old bricks a run for their money.

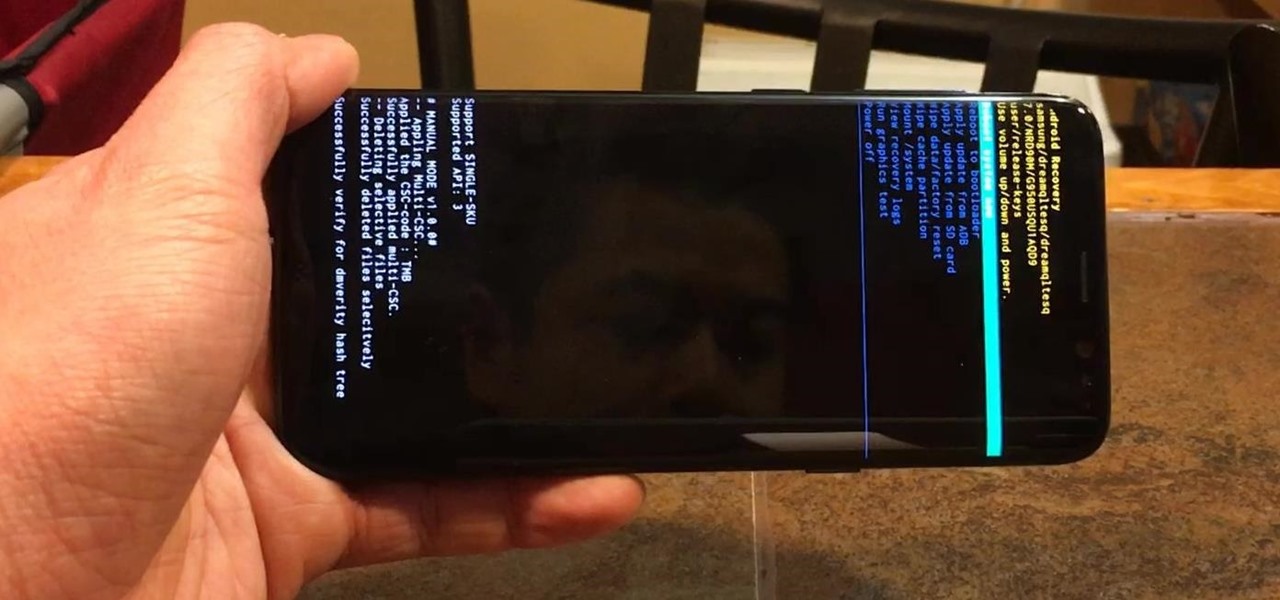
Samsung devices have two pre-boot menus that every Galaxy owner should know about: recovery mode and download mode. The recovery screen allows users to wipe cache files or perform a factory reset, which can help save the phone from a soft brick. Download mode, on the other hand, allows you to flash firmware files using utilities like Odin and Smart Switch, which can truly be a lifesaver.

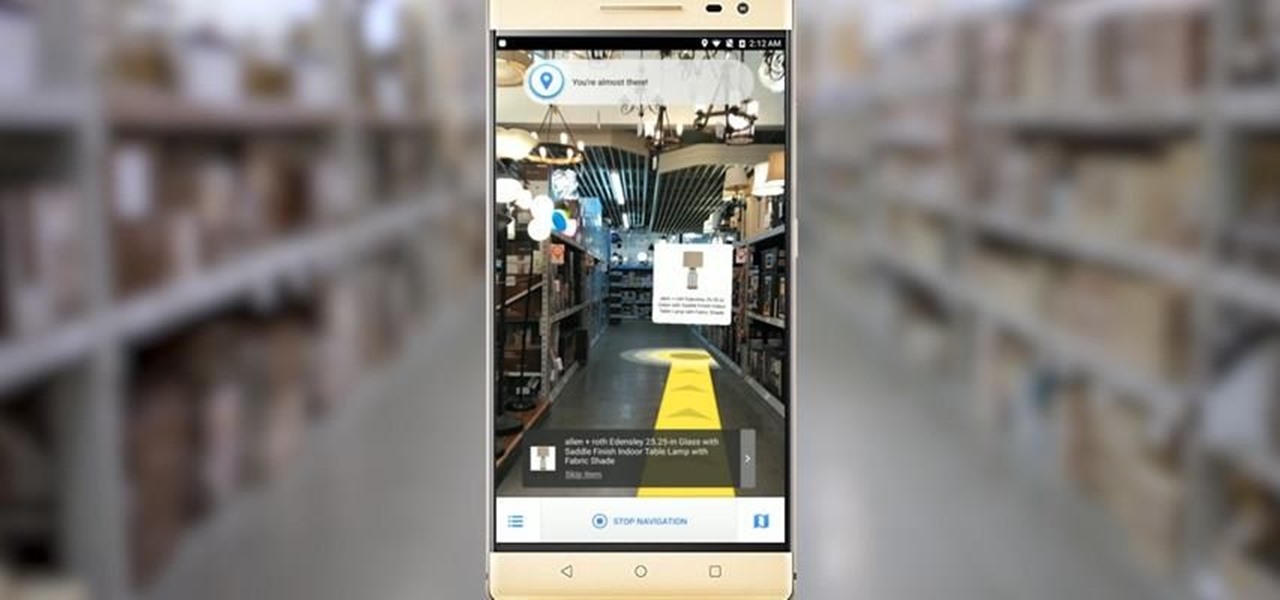
Lowe's Home Improvement laid another brick in their augmented reality foundation with today's announcement of a new app for Tango-enabled smartphones.

Pong, one of the simplest video games ever created, has managed to evolve in some crazy ways over time, from the original basic 2D version and colorful Breakout sequel, to the PlayStation game with power-ups and 3D graphics, and now Cyberpong VR—a virtual reality game on the HTC Vive—where you act as the paddle instead of just moving it into place with a controller.

The HoloLens can do some pretty crazy things such as create a robot invasion in your walls, but it can also help you do simple stuff, like hanging frames, paintings, or anything else on those walls—after you repair them from the robot attack, of course.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

Google announced today that it's offering rewards to Android Pay users, and taking advantage of these deals could land you a free 2nd Generation Chromecast, among other prizes. The Tap 10 promotion is pretty self-explanatory: Tap to use Android Pay 10 times before February 29, 2016, and Google will give you a code to redeem a free Chromecast, free music, or both. You'll also be rewarded for Taps 1 through 9 as well. You'll receive a code for one music track from the Google Play Store for ever...

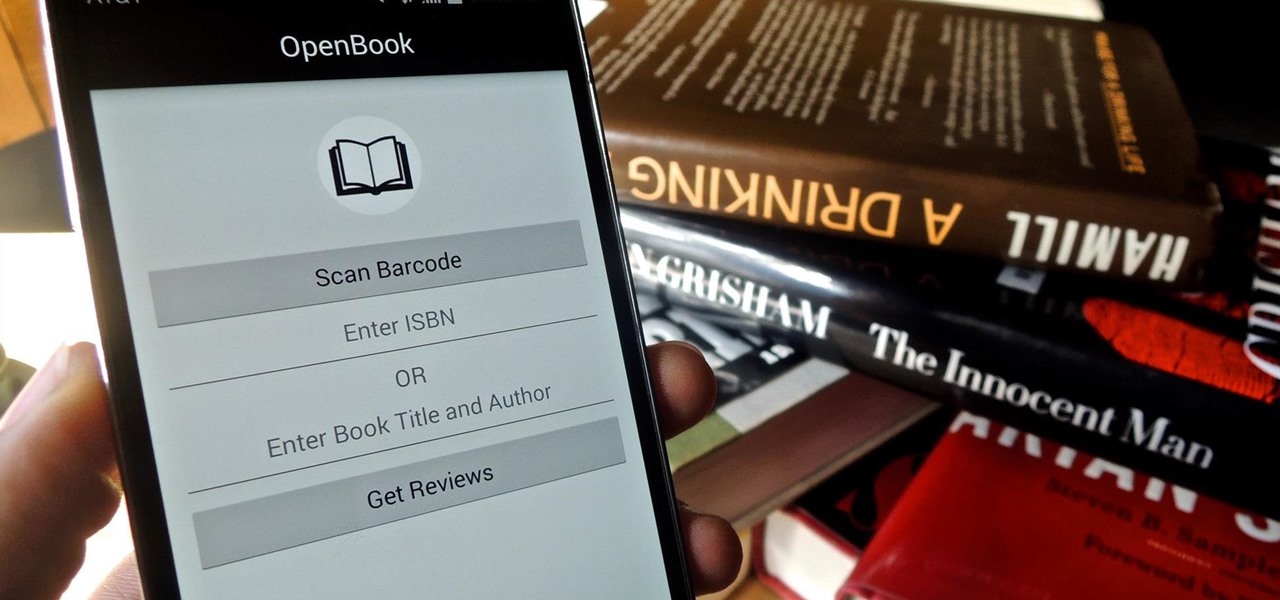
Purchasing an actual book from a brick-and-mortar store is becoming increasingly less common for people to do, but it hasn't completely gone out of style just yet. There's something about entering a bookstore and viewing all the potential great stories and epic tales just sitting on the shelves, waiting to be discovered.

Who doesn't love The Lego Movie? With a theme song that shouts the film's awesomeness, becoming one of its brick-bodied, eternally happy characters is everyone's dream.

My OnePlus One easily gets over a day of battery life without a problem, but when I try to charge it, it seems to take just as long. For some reason, no matter what charger you plug your OPO into, it never gets more than USB-level power, meaning that charging times are more than double when compared to traditional AC-charging.

Rooting your phone is one thing, but to truly be in control of your device, you need to be S-Off. S-Off allows you to flash, mod, and tweak just about any aspect of your phone, including the ability to run custom recoveries and flash kernels, which are vital tools for power-users. Up until now, there have been many ways to S-Off your device, but some newer HTC models have become un-exploitable.

Just short of a week after its release, the new HTC One has been rooted thanks to Android devs beaups and jcase, the same guys that brought us S-OFF for the original HTC One (M7).

How to make a Lego key holder with note board. Tired of loosing your keys? Well keep them safe and in one place with this fun Lego key holder.

If you pre-ordered your Samsung Galaxy S4, it might very well be possible that you're reading this on your brand spanking new Android device. As is commonplace with the release of popular smartphones, rooting instructions are usually released simultaneously. I mean, what's the point of paying so much for an expensive phone if you can't have a little fun? Android developer Dan Rosenberg (aka djrbliss) recently announced that you can root your Samsung Galaxy S4 using the root exploit he origina...

Online shopping is way more convenient than brick-and-mortar stores in a number of ways, not the least of which are the discounts. But with so many online stores and sites like Amazon which feature thousands of retailers, how can you know you're getting the best deal?

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

In this tutorial, from Zappos, learn how to make a simple stop motion video. This process is a lot easier than you would expect and this video is here to give you a step by step.

Installing clutch shoes is very simple. What you need are the clutch shoes, clutch shoe installation/removal tool which costs about $5 or a flat tip screwdriver. First, line up the clutch shoe. Plastic shoes wear out faster. Aluminum last longer. With the screwdriver method you bend the spring out. Take the bent out spring and push it down. Push it straight down. This is not the authors favorite method. Using the clutch shoe installation tool, simply push the spring out and push straight down...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to broadcast live online.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Watch this how to video to learn how to make your own Lego race car. This tutorial will teach you how to make the Lego race car brick by brick.

The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.

Throughout the COVID-19 pandemic, Facebook enjoyed a boost in sales of Portal, its smart video cameras with AR effects, as social distancing became the norm.

While Google Stadia currently needs to be sideloaded on Chromecast with Google TV, there are a handful of games that are compatible with the streaming device and require a gamepad. But you don't need to buy a specific controller just for your Chromecast, you can use one you already have lying around.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

With many office workers in the US being asked to work from home if their job allows, Magic Leap's customary updates for the Lumin OS and Lumin SDK brings some help to keep distributed workforces connected.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.

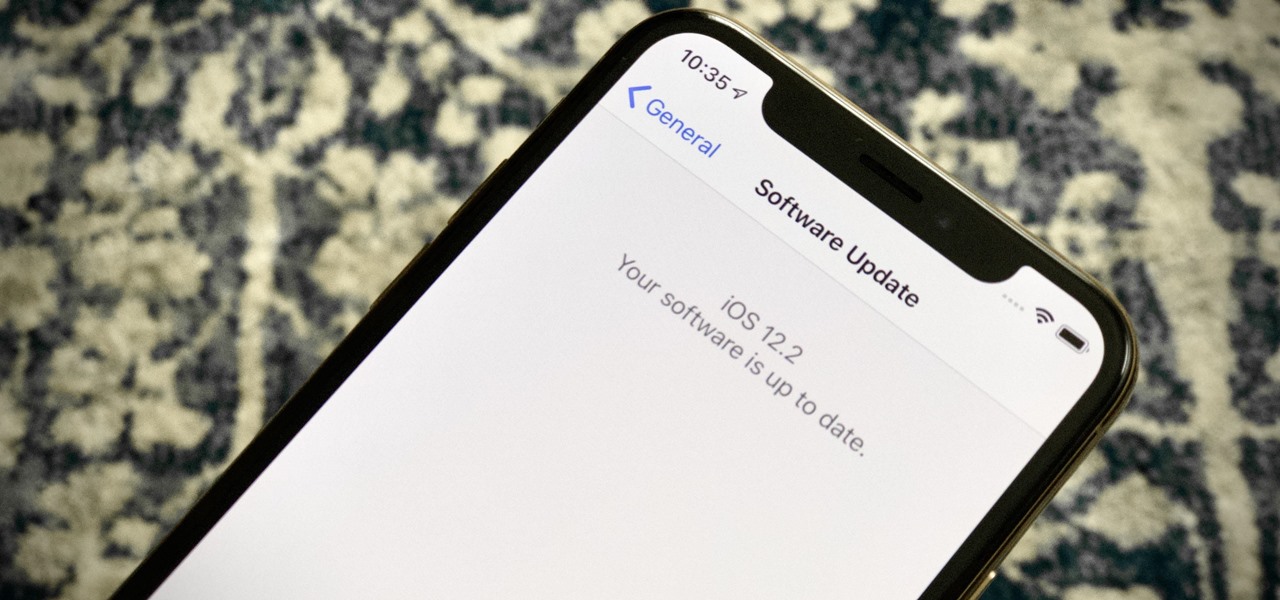
If you're an iOS app developer, your Monday just got better; Apple just released iOS 12.2 developer beta 5 to your Software Updates today, March 11. This fifth beta includes a number of small UI changes and tweaks, and likely some degree of under-the-hood improvements and bug fixes.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?