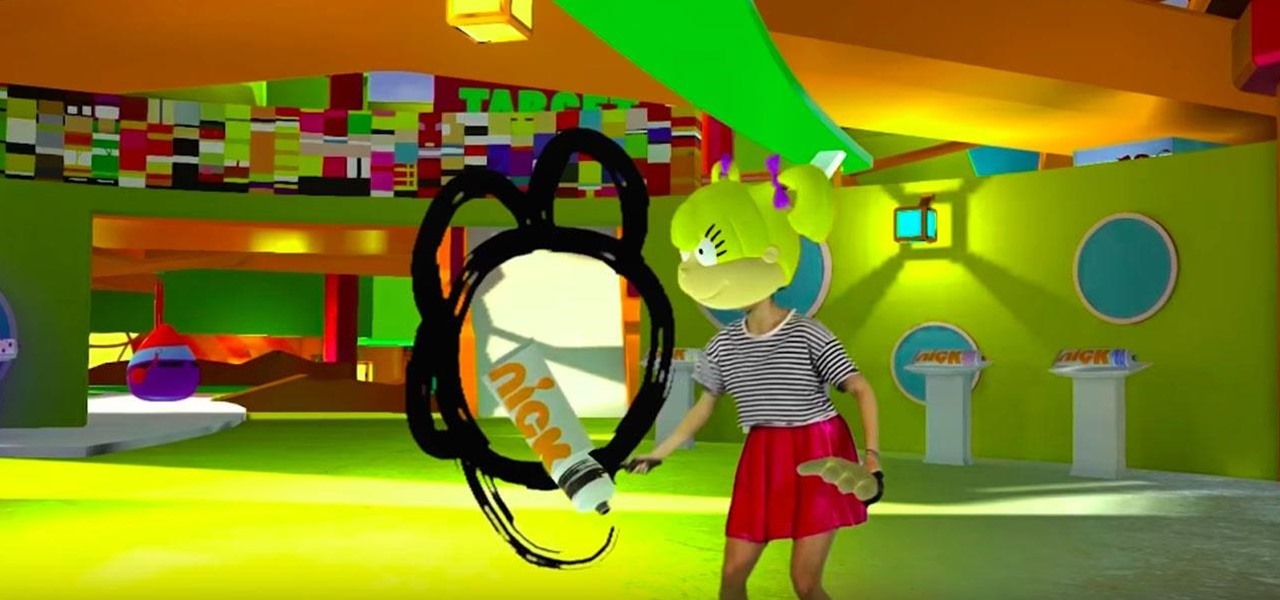Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

You can find a plethora of tennis games on the Google Play Store, but if you're a true tennis fan and gaming enthusiast, you should check out Tennis Racketeering by Core Aplikacije. The game lets you use an additional Android device as a racket, giving you Wii-like abilities without Nintendo. It's simple to set up and extremely fun to play, so follow along below to see how it works.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

If you want to program an RCA universal remote control, you can follow this professional's advice. Make sure the batteries are in place, and turn on the device you want to control. On the top row of the remote control, there are buttons labeled with the names of different devices. Press the button for the device you want to program, and press ON/OFF button at the same time. The light under the ON/OFF button will light up indicating you are in program mode. Press the play button on the lower p...

This blueberry crumb cake is practically a masterpiece, if you dare try too make it. If you're up for the challenge, this moist and tender crumb cake packed with fresh blueberries and a delicious crumb topping will never last a day in your home. This yummy cake is hard not to like. It's irresistible. Check out this video recipe for baking buttermilk blueberry crumb cake.

Make a cascading brick denim quilt out of household rags. Learn how to make a rag denim quilt in this free quilting lesson from an expert quilter and sewing class instructor.

If you've ever been in the kitchen making your grandma's famous cookie recipe and when it comes time for the brown sugar found yourself stuck with an unmalleable, rock-hard chunk instead of measurable granules, then you will appreciate this tip.

This video tutorial shows how to assemble an automatic Lego crossbow. Learn how to build and operate an automatic toy crossbow made out of Lego bricks.

This video very simply and accurately shows you how you should spread mortar when laying bricks or blocks.

Windows Media Player 12 is ONLY available for Windows 7 (sorry Vista and XP users), but with it's functionality, it may be worth the upgrade (if you haven't already). This video outlines a few of the simple tasks that WMP12 can perform in W7.

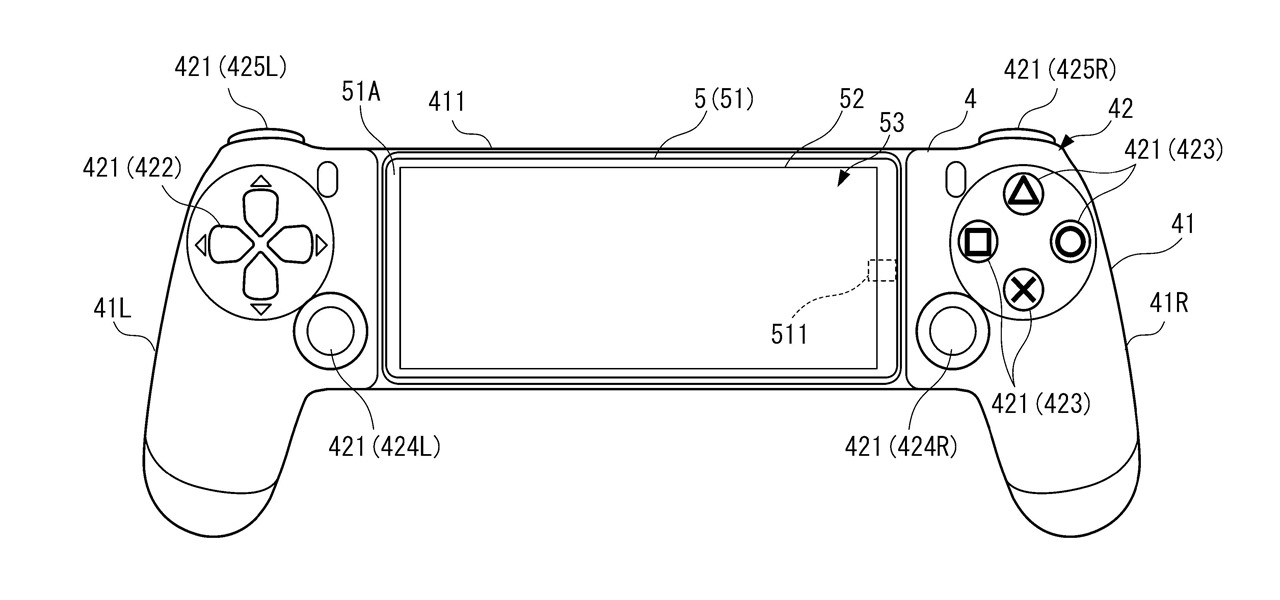
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

The Paris-based technology conference Viva Technology, which hosted the likes of Apple's Tim Cook and Facebook's Mark Zuckerberg, is now over.

When it comes to augmented reality wearables, it's currently an enterprise world. As such, Magic Leap's latest Lumin updates are centered on features that appeal to enterprise customers. And Epson and Spinar are joining forces with a solution for distributed workforces.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

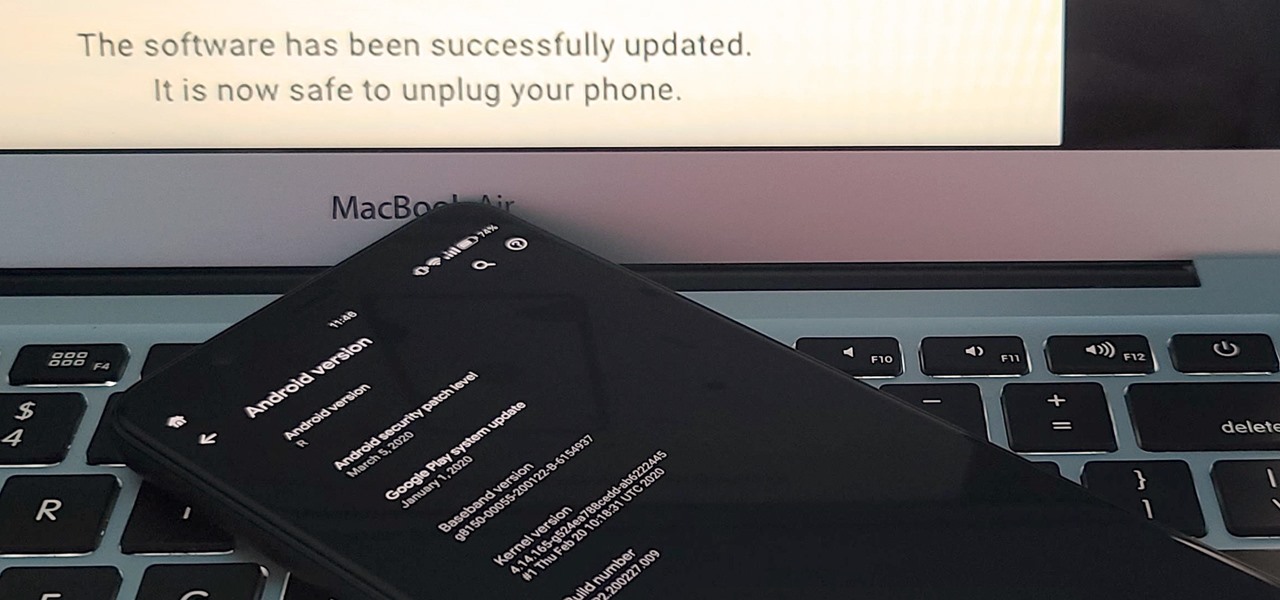
If you've ever tried to update your Android phone manually, you know the process can be unnecessarily hard. There are so many steps and parts, that if one thing goes wrong, the whole process doesn't work. Recognizing this, the Android team came up with an even easier way.

I got my first Philips Hue White and Color Ambiance bulbs because they're the consensus best of the best for colored lighting. But after spending 90 bucks on two light bulbs, when it came to all the accessories like switches and buttons, I went with cheaper third party options. Little did I know, I was overlooking a great first-party accessory with a surprisingly reasonable price.

We may or may not see Apple's long-awaited take on AR smartglasses this year, but the company is more than getting its practice swings in with its current wearables business, which hit record revenue in 2019 according to financial results released this week.

Microsoft has unveiled practically every detail of the HoloLens 2 except for when eager developers and enterprise customers can expect to receive the device.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

It's here! Apple just released the latest version of iOS today, Monday, March 25. Version 12.2 has seen six beta releases, spanning the course of fewer than three months. The new update sports 30+ awesome features, including new Animoji, air quality reports in Apple Maps, and AirPlay 2 support for compatible TVs, in addition to a slew of new UI tweaks and redesigns.

The debut of Microsoft's HoloLens 2 went off without a hitch, and now it's time to figure out if you want to hop aboard the updated augmented reality train.

The mystery surrounding the release of the next version of the HoloLens has been swirling for months, but at least some of that mystery may removed in the coming weeks.

Cable TV network Nickelodeon is looking to break new ground with a new series that will be experienced in virtual and augmented reality.

The old school staple of many US homes with children, the remote control race track, has been given new life in augmented reality thanks to the Room Racer app for iPhones and iPads.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Looking to inject a little more processing juice into your HoloLens? Unity can fix you up with the Standalone Universal Windows Platform Holographic Emulation.

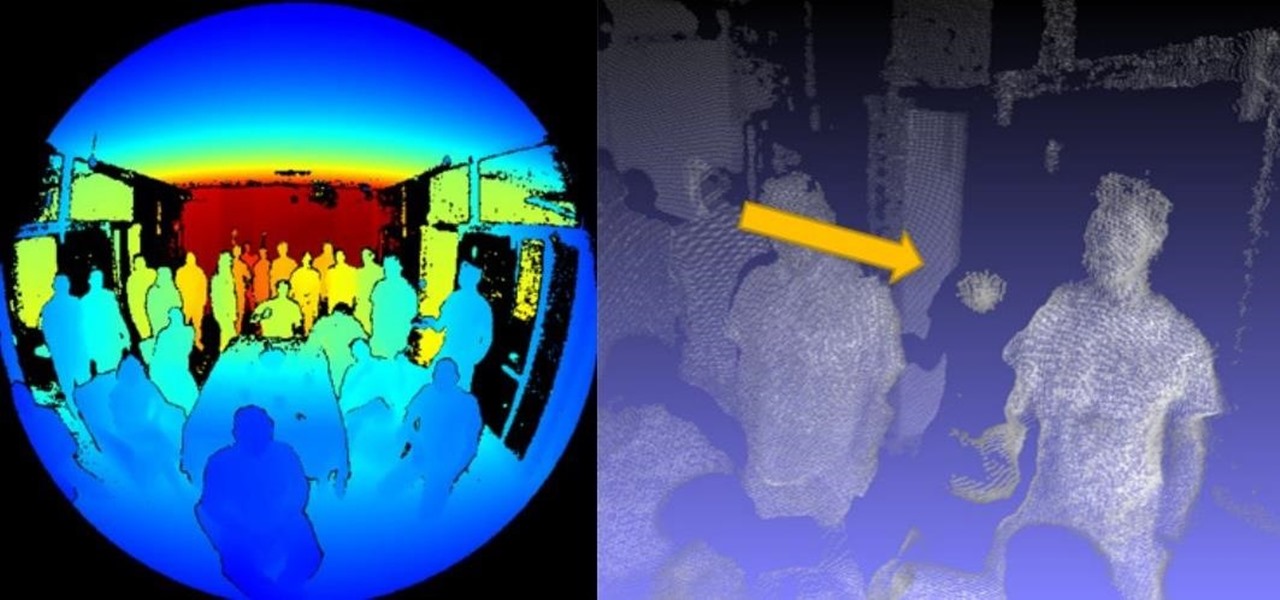
Images captured by Microsoft's next generation Kinect depth-sensing camera that will facilitate augmented reality experiences in the next version of the HoloLens and give computer vision to untold multitudes of connected devices in enterprise facilities, have made their way into the wild.

Magic Leap's recent flurry of patent applications prompted us to look around for any trademark movements from the company, and it turns out that the Florida-based company has been quite busy.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

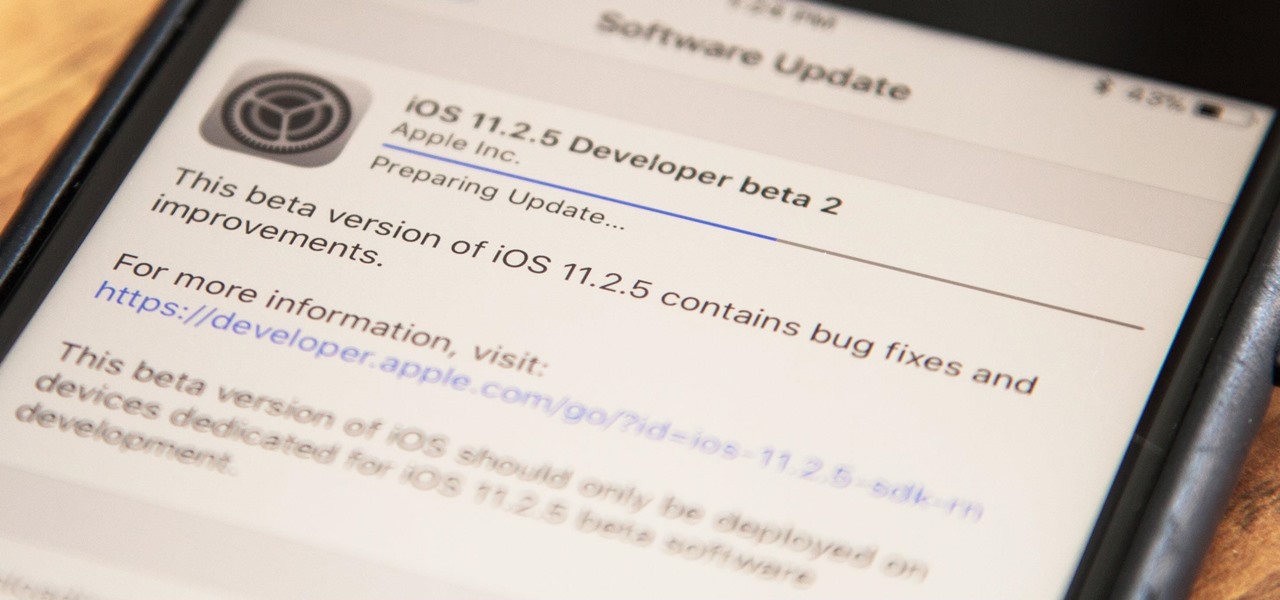
Apple has released the second beta for iOS version 11.2.5 for developers on Dec. 19. The update comes six days after the release of the first 11.2.5 beta which updated the Music app to include a persistent "play bar" at the bottom of the window, along with some bug fixes. Public beta testers received the update on Dec. 20.

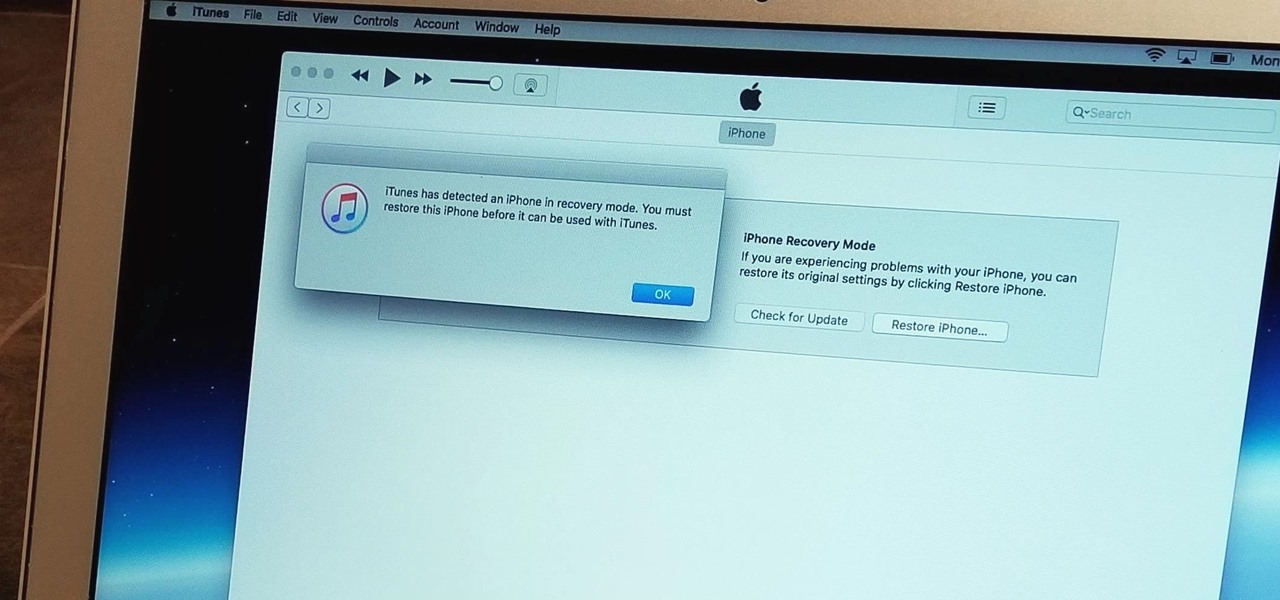
With the iPhone 8, 8 Plus, and the exclusive iPhone X, Apple has come full circle in transitioning its users away from the home button present since the first iPhone a decade ago. This gives us a window into Apple's design philosophy moving forward, but it also presents some new problems, especially when it comes to entering and exiting DFU mode in iTunes.

The Xposed Framework is an incredibly powerful tool. But because of this power, there's a chance that something could go wrong when installing a broken or incompatible module, which can cause bootloops or even soft-brick your phone.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

In an early morning blog, Jimmy Alamparambil of the Unity team announced a major new update to their ARKit plugin. Developers now can use Unity and ARKit to create AR experiences and test directly from Unity's editor, without deploying to the device.

Artificial intelligence and augmented reality go together like spaghetti and meatballs, and Lenovo has some ideas on how to spice up the recipe.

While not quite a true self-driving car, Mercedes is gearing to release a vehicle with a plethora of assistive-driving features, some that might have you excited about what autonomous vehicles can do in the future.

Virtual reality headsets like the Oculus Rift and HTC Vive tether to desktop computers with robust GPUs in order to harness their power. The free-roaming, cordless Microsoft HoloLens forgoes those chains but loses a bit of graphical processing power in the mix. However, a recent report suggests we may get the best of both worlds.

Instant ramen makes me nostalgic for my college days, when a bowl of this cheap noodle soup was my go-to comfort food for many all-nighters.