Forget Waymo, Uber, Tesla, and other other heavily mediatized driverless contenders — German premium carmaker Audi AG has become the first OEM to introduce a Level 3 car sold in retail channels.
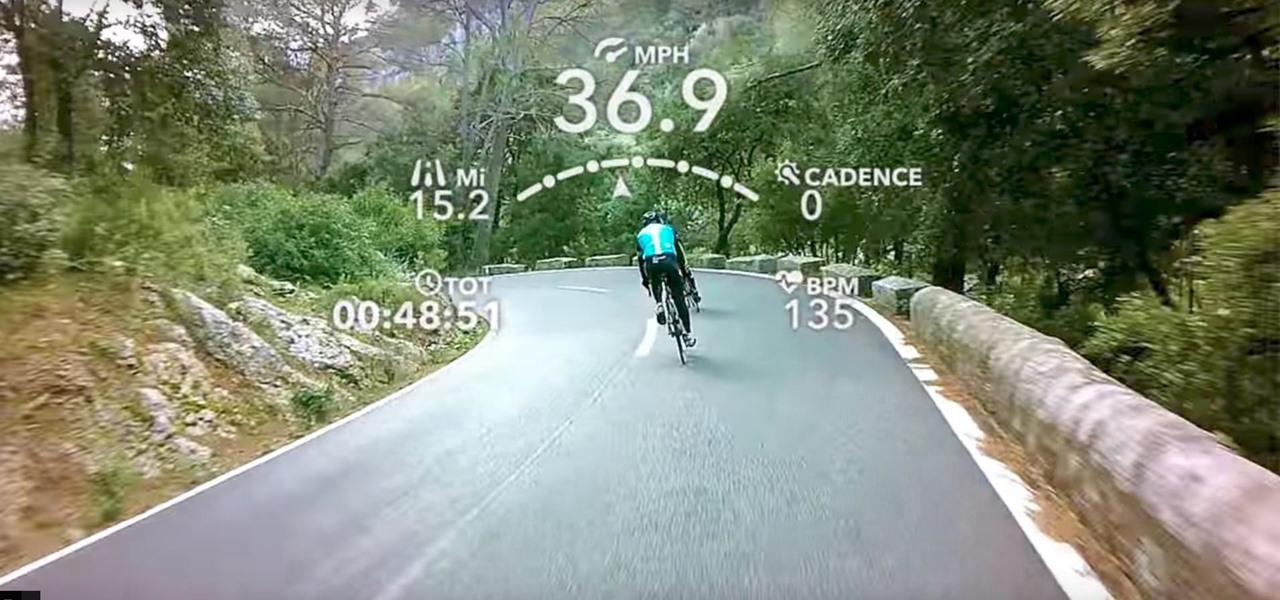
Cyclists of the world, new AR glasses are here to improve your rides. Possessing 2 GB RAM, a quad-core CPU, GPS, 16 to 32 GB of storage, an accelerometer, camera, gyroscope, magnetometer, barometer, Bluetooth, speaker, WiFi, and a mic, these aren't your regular UV-blocking sunglasses. Called the Everysight Raptor AR glasses, these shades project all of the information a cyclist could need to optimize their rides.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

We just keep discovering hidden features and settings scattered throughout the Galaxy S8's system like little digital Easter eggs that were largely left unadvertised. One such setting is an option that lets you change the placement of your S8's display brightness slider.
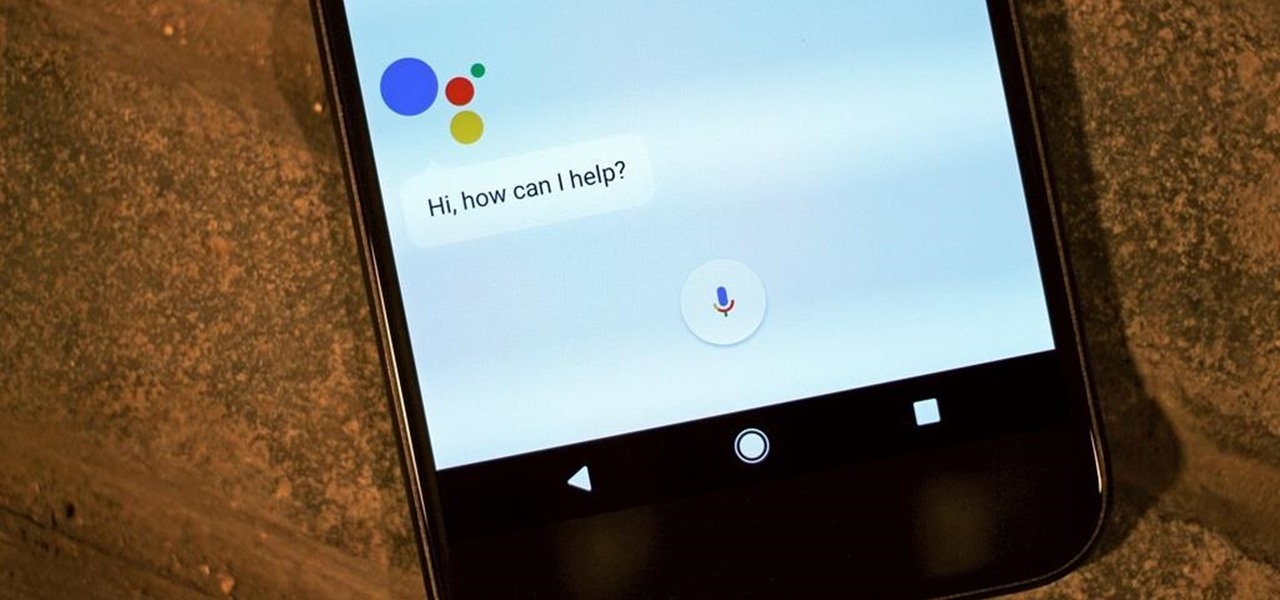
Rumor has it that Google Assistant will be coming to an iPhone near you. A "trusted source" broke the news of GA's arrival on iOS to Android Police ahead of Google's I/O conference this week.

Stop me if you've heard this one before. You plop a marshmallow down in front of a kid and propose the following: You can eat this marshmallow now, or you can wait twenty minutes and eat two marshmallows. What do you think the kid is going to do? Better still, what do you think you would do? Personally, I'd eat the first marshmallow without hesitation. But now we're getting off track ...

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

NBA star Andre Iguodala, of the Golden State Warriors, got to try out a Magic Leap demo in Florida and started dishing out some pretty revealing details about the upcoming mixed reality headset to CNET's Brian Tong.

Udacity, the online education startup that set out to train a school of self-driving car engineers, is now spinning off into its own autonomous tech company called Voyage.

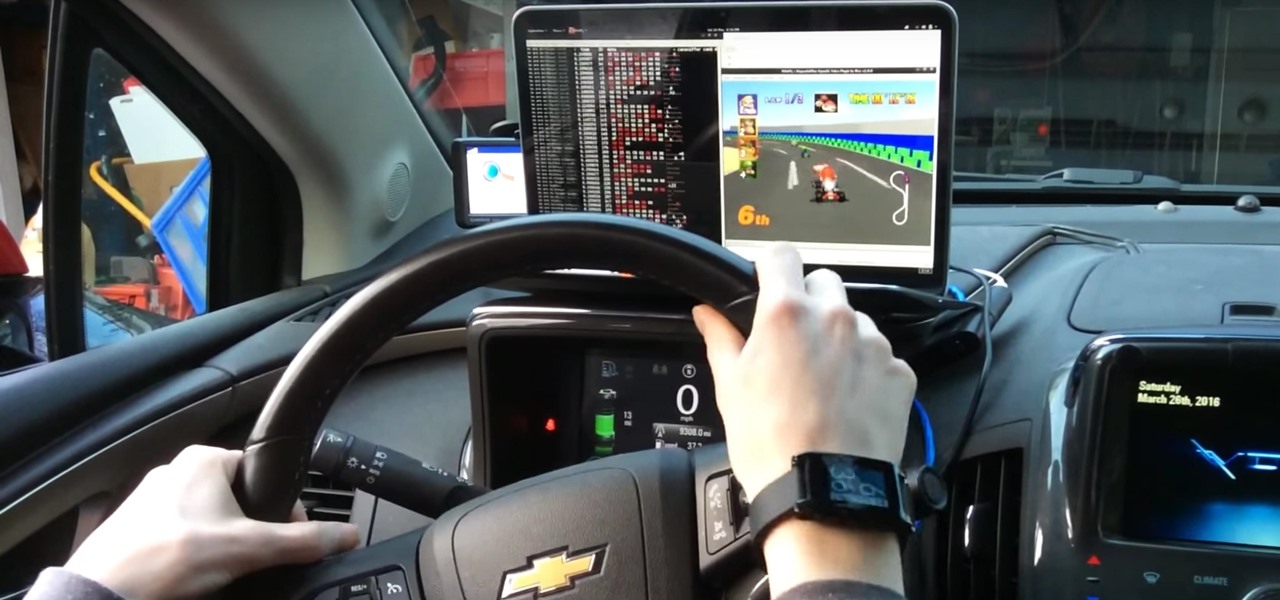
Oh, Mario. The guy that's been a part of our lives since as long as we can all remember. Well, Adam Ringwood and his friends did something pretty cool with one of Mario's most exciting games at the HackIllinois event in February 2016—they hacked a Chevrolet Volt's steering wheel into one big Nintendo 64 controller for Mario Kart.

Leaked documents from Uber, obtained by Re/code, detail the ride-hailing app's latest wins and failures in their self-driving experiment. The reports detail the number of autonomous miles traveled, the number of driver interventions needed, and the number of times the drivers had to avoid serious damage.

Both the US and UK seem to be leaning toward requiring level 3 autonomous cars to train their "eyes" not just on the outside world, but even on the driver itself.

If you're tired of fumbling with the Control Center every time you need to turn off your iPhone's LED flashlight, you'll be happy to know there's a faster way. Using a simple trick that was discovered by Redditor 49599066, you can actually toggle your flashlight off in less than a second in iOS 10 and higher.

If you have a mobility impairment that affects your hands, arms, or manual dexterity, a smartphone's touch-based interface can almost be a barrier between you and the mobile internet. Eye-tracking software requires too much computing power for today's smartphones to handle, so it might seem as though there's no good way to interact with an Android device.

Here at NextReality, we talk a lot about the many different ways of controlling holograms in the HoloLens and other augmented and mixed reality devices; New and creative ways are coming more and more every day. Most recently is something called the HoloSuit. In the 25-second clip below, you can see a woman moving the arm of a jacket which in turn moves a 3D model of Darth Vader on the screen. It's a simple idea with big potential.

Having control of your basic motor functions is something most people take for granted, but for individuals with Parkinson's disease, that is not the case.

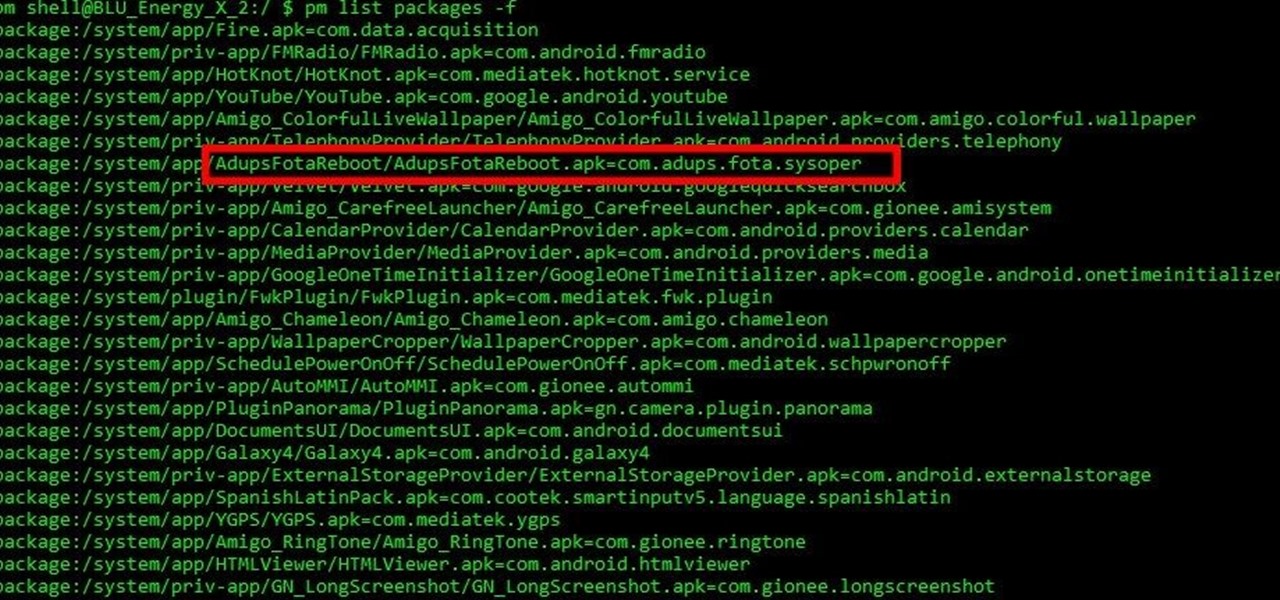
Mobile security researchers at Kryptowire recently uncovered spyware preinstalled on hundreds of thousands of Android smartphones by FOTA provider Adups which was gathering personally identifiable information (PII) such as call logs, app usage data, and even the full contents of text messages and sending these to a third-party server—all without the users' knowledge.

While Leap Motion and Microsoft are looking to capture natural human motion with cameras, Enflux figured out how to do it with a shirt and pants that feel completely natural.

Want proof that user experiences matter? Look no further than the HTC Vive and Omnipudding's particle generator, GPU Cubes VR, which lets you interact with thousands of colorful, cubic particles in a black void. If this was a simulator for your computer only, controlled with a mouse or keyboard, you'd be bored in seconds—but it's just simple, instant fun on the Vive.

Leap Motion created gesture control for all sorts of things, including virtual reality, long ago, but developers must build in support for their tracking peripheral to use its full potential. As a result, they've created an "Interaction Engine" for Unity, the primary platform for developing virtual and mixed reality experiences, to try and take gesture interaction to the next level.

If you've ever played the game of Would You Rather, you've probably been given the ultimatum between eating insects or doing something else that sounds absurd, like licking a cactus. I'm advising you to always choose the insects, and here's why:

Things are definitely starting to shape up with iOS 10. After three developer betas of the upcoming operating system, Apple has begun rolling out the developer beta 4 release for iPhone, iPad, and iPod touch, which focuses mostly on refining some of the cool new features.

Most virtual and mixed reality headsets offer unnatural controls, making you use awkward movements or physical devices to control the holographic elements in your direct view. This doesn't make a lot of sense because using your hands is more natural, so Manus developed a set of gloves that solves that problem entirely.

The mysterious Magic Leap just partnered up with Lucasfilm's ILM xLAB to bring Star Wars to their mixed reality headsets. Based on the video demo making its way around the internet, it looks pretty impressive.

We recently covered an app called Touch Controls for YouTube that allows you to swipe up or down on any YouTube video to quickly adjust volume levels or brightness. As awesome as that app is, commenters here and on our YouTube channel thought it was lacking one big feature—the ability to seek forward or backward in the video by swiping the screen.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Since its purchase by Microsoft in 2014, Minecraft has regularly been pushed to new platforms such as Windows 10, Wii U, and Fire TV. In that spirit, Microsoft-owned Mojang has been developing virtual- and augmented-reality versions of the blocky sandbox game.

This is a nice project that you can continue to work on and modify as you learn more Arduino projects. The Instructable linked below goes through the complete build for the Bluetooth-enabled robot seen in the first half of the video.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Welcome back to another C tutorial, this post covering the first part of control structures, if statements. Let's get right into it.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

Practically every smartphone comes with a built-in camera app, but these apps are generally created by the device's manufacturer. And let's face it, manufacturers are hardware companies first and foremost, so they don't always produce the best software.

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

YouTube has officially rolled out their new video player design, featuring transparent controls floating above the video, replacing the opaque ones. While you've been able to enable this player for a while now, YouTube finally flipped the switch and enabled it site-wide. Problem is, there's no way to turn it off, and that has quite a few people miffed. While the redesign is sleeker, it isn't everyone's cup of tea. Many users are complaining about everything from the idle progress being remove...

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

Usually when a hacker takes control of a system, they use it for a good purpose (on their end, anyway). But some hackers have made jokes or pranks with their hacks. Here is a list of the top of them...