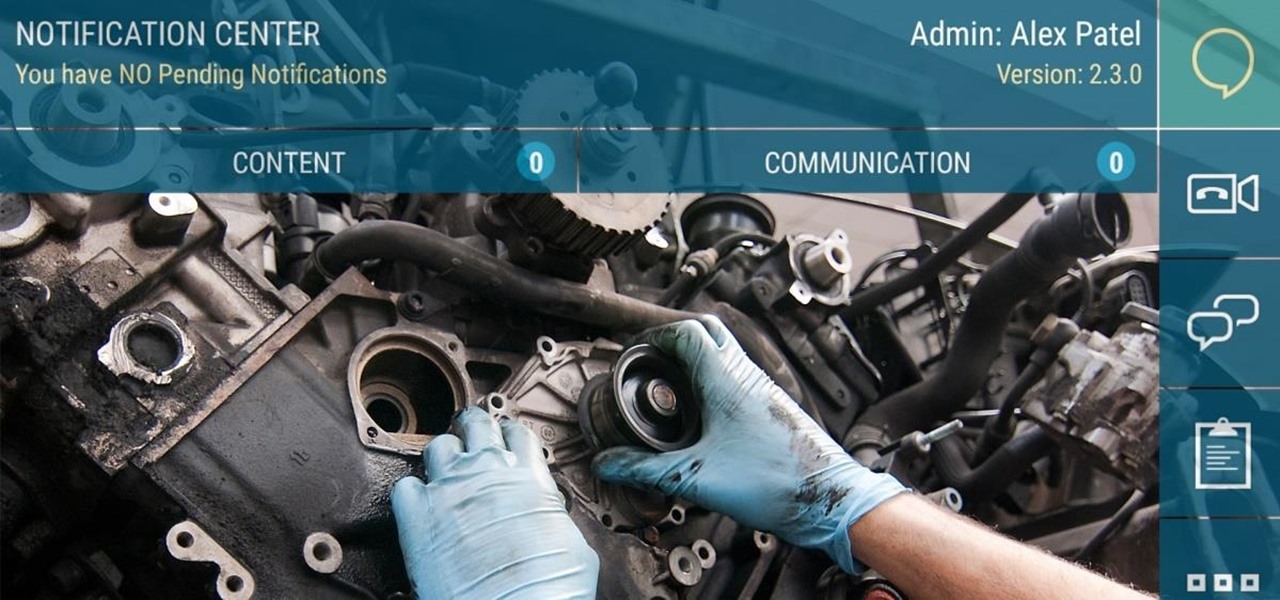
RC Car Action Magazine Edito Paul Onorato demonstrates how to remove and install clutch shoes using a DuraTrax clutch shoe tool. The clutch show tool makes the clutch easy to install and remove. Watch this video tutorial and learn how to use the clutch shoe tool on a remote control vehicle.

Computer vision is a key component in enabling augmented reality experiences, but now it can help give sight to the blind as well. In this case, that assistance comes from Envision, developers of mobile apps for iOS and Android that use optical character recognition (OCR) and object detection to provide an audio description of the user's surroundings.

Whether you're trying to become an influencer or just want to share better photos and videos, the best camera to start with is your smartphone. It is likely the only camera you always have on you and it's probably capable of excellent pictures and video capture. But with a little help, it could definitely be better.

Apple released iOS 12.2 beta 4 to developers on Monday, March 4, then shortly thereafter also pushed it out to everyone on the iOS 12.2 public beta program. All previous public beta updates for iOS 12.2 were released the following day, but this one changes course. In the iOS 12.2 public beta 4, there are new icons, an updated "About" page, and better Now Playing tile.

Upon Google's release of ARCore in February, the platform wasn't only playing catch-up with Apple and ARKit in terms of downloads, but it also lagged in capabilities, as Apple already had vertical surface recognition and image recognition on the way with ARKit 1.5 for a March release.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

The augmented reality productivity app market for is a crowded space, so differentiation can be an advantage. Atheer is doing just that this week with their AiR Enterprise application.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

The first sneak peak of Android O is finally here. The developer preview promises more features, stabilization, and better performance, according to the Android Developers Blog. Furthermore, there's speculation that the latest operating system will be code-named "Android Oreo," so it definitely sounds like we're in for a treat.

What if you forgot your car keys and that keyless entry remote banded to them, how are you going to get in your car? Well, if you haven't forgotten your cell phone, too, you can call up someone who has access to that keyless remote, so you can unlock your car or truck via the wireless mobile phone! What?!?

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

In this tutorial, from Zappos, learn how to make a simple stop motion video. This process is a lot easier than you would expect and this video is here to give you a step by step.

It’s late at night and your remote control runs out of batteries. When you go to replace them you realize you only have one batter left. Now you’ll have the quick fix knowledge to power your remote with just one battery until you can find another.

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

When it comes to augmented reality wearables, it's currently an enterprise world. As such, Magic Leap's latest Lumin updates are centered on features that appeal to enterprise customers. And Epson and Spinar are joining forces with a solution for distributed workforces.

While Google Stadia currently needs to be sideloaded on Chromecast with Google TV, there are a handful of games that are compatible with the streaming device and require a gamepad. But you don't need to buy a specific controller just for your Chromecast, you can use one you already have lying around.

Following on the heels of the announcement that ThirdEye's Gen X2 MR glasses began shipping in September, ThirdEye has revealed it has developed an app that helps soldiers aim their weapons during battle situations.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Visitors to the Unity booth at the Game Developers Conference in San Francisco will get a special augmented reality treat courtesy of Magic Leap and Weta Workshop.

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

On Tuesday, original design manufacturer (ODM) Flex used the CES spotlight to help introduce a smartglasses reference design aimed at companies interested in bringing their own enterprise AR headsets to market.

French manufacturer Renault Trucks is looking to the HoloLens to improve quality control processes with its engine assembly operations.

Influenced by the growth of augmented and virtual reality technology as well as 3D computer vision, Ericcson Ventures invested in Matterport, whose hardware and software help companies create AR/VR experiences.

GE Aviation and their software partner Upskill are seeing success by giving their mechanics smart tools and smart glasses, the latter in the form of Google Glass.

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

It's been a great week for Chromecast owners. First, Google released the development kit, allowing devs to install the casting code into their apps. Then, CyanogenMod dev Koush updated his AllCast app to support the Chromecast. That means you can shoot personal movies, music, and photos directly from your Android device over to a Chromecast-connected display.

Like insurance, it's always better to have a computer mouse and not need it than to need it and not have it. Honestly, I don't want to carry around a clunky mouse with my laptop, so I don't. I do something else, something more convenient. I use my Nexus 7. If you want to give it a try, I'll show you how it's done right now. All you need to is a Wi-Fi network and a specific Android app to control your computer with your Android tablet.

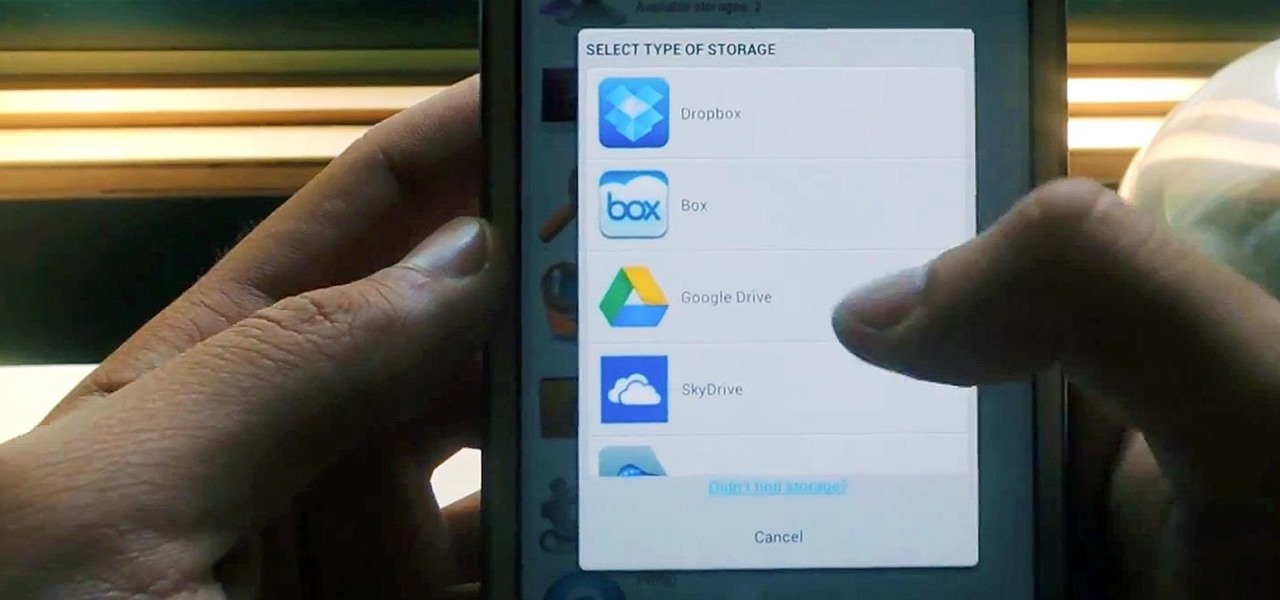
Cloud storage looks pretty good compared to the heavy restrictions that hard drives and other types of external memory carry. The cloud is not only limitless in what it can hold, but it can also easily be accessed from any device that has Internet—your smartphone, work computer, personal laptop, tablet, and more. While accessing a specific cloud storage system like Dropbox or Google Drive may be easy on your Samsung Galaxy Note 2, managing all of them individually can not only get confusing, ...

Samsung just concluded their live unveiling of the Samsung Galaxy S4! A more in-depth look can be found here.

With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Microsoft products, this tutorial will show you how to install the Windows 8 preview to try it out on your MacBook. First things first, you'll want to download the Release Preview on Microsoft's website (make sure to save ...

If your tailgate won't stay up you may need to replace the tailgate support cables. This video shows how to replace the tailgate support cables for any 2002-2008 Dodge Ram Truck. Replacing the support cables is a very simple procedure.

Installing clutch shoes is very simple. What you need are the clutch shoes, clutch shoe installation/removal tool which costs about $5 or a flat tip screwdriver. First, line up the clutch shoe. Plastic shoes wear out faster. Aluminum last longer. With the screwdriver method you bend the spring out. Take the bent out spring and push it down. Push it straight down. This is not the authors favorite method. Using the clutch shoe installation tool, simply push the spring out and push straight down...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to broadcast live online.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

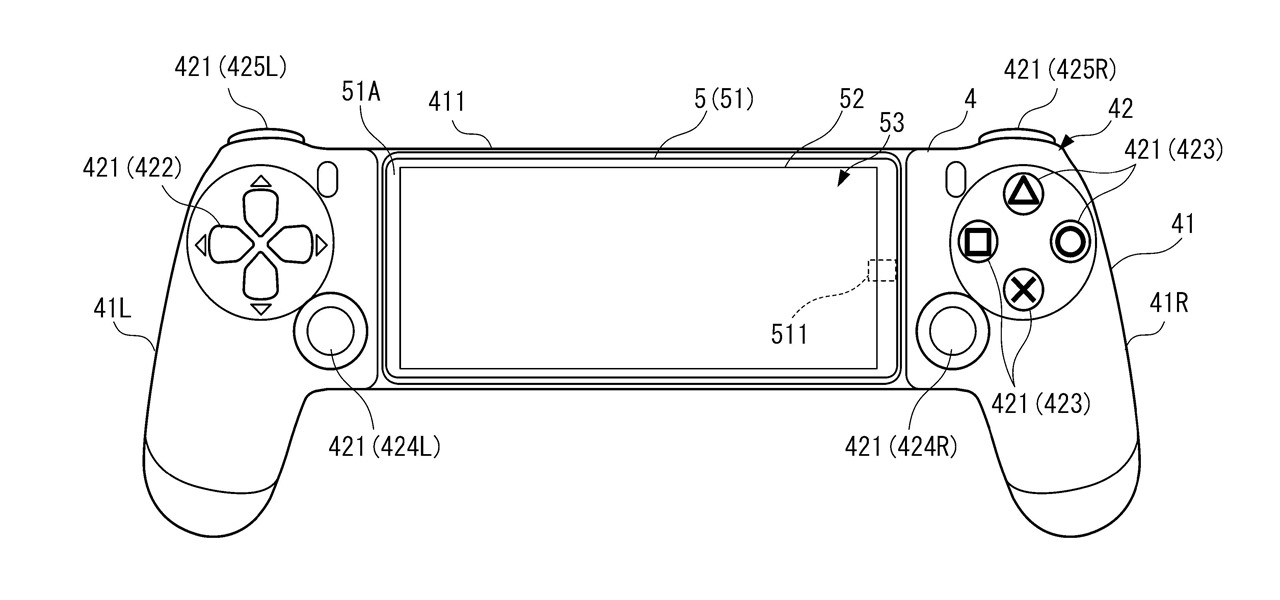
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

The enterprise-focused category of augmented reality doesn't often get the headlines due to its relatively sedate profile as a mostly factory floor and training-based tool.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.