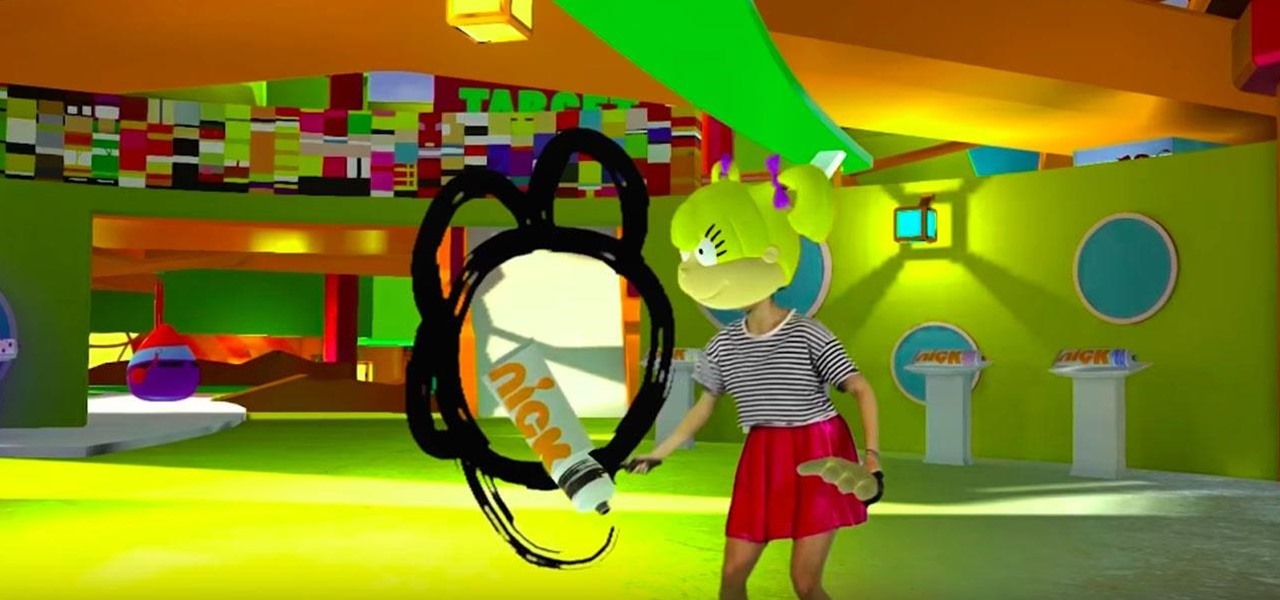Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

You're at your friend's house. All you've heard about all day is his new laptop. He's got a brand new top-specced MacBook Pro, and he won't stop going on about it. It particularly annoys you as all you've got is a 4 year old cheap laptop, even if it is running Linux.

You can find a plethora of tennis games on the Google Play Store, but if you're a true tennis fan and gaming enthusiast, you should check out Tennis Racketeering by Core Aplikacije. The game lets you use an additional Android device as a racket, giving you Wii-like abilities without Nintendo. It's simple to set up and extremely fun to play, so follow along below to see how it works.

These days, we increasingly have more and more devices in our everyday possession. While a notebook computer, a tablet, and a smartphone may seem like overkill, they do work to make our lives easier and even help reduce clutter in certain ways.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

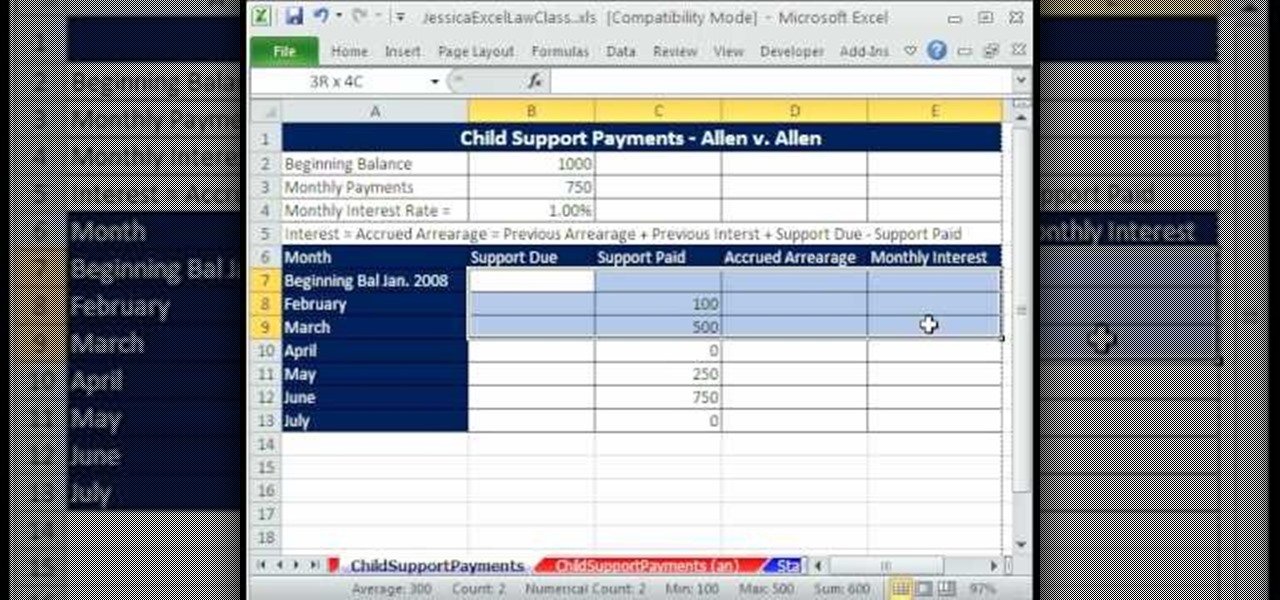
Looking for a primer on how to calculate child support payments in a Microsoft Excel spreadsheet? You've come to the right place. In this free video tutorial from everyone's favorite MS Excel guru, YouTube's ExcelIsFun, you'll learn how to do just that. For more information, including detailed instructions on how to find child support payment amounts yourself, watch this helpful how-to.

Nine inch storage shelves are spaced and constructed in a practical way. It shows the right screws. This requires a drill some wood. The viewer is shown how to make a good back brace for the shelves. It shows how to make the shelving unit level. You learn the screw head must be flat. You are also shown how to put in a good support for underneath the shelves. It shows the center support being constructed. He shows how to set the shelves up so there is support from all sides and to make the she...

If you think you have a good swimming technique and you're not sure how you can gain more speed in the water, moving support perception drills can help you improve your skills. The specialized drills focus on the motions you do while swimming to give you more speed and consistency while swimming.

Minor lower back injuries can occur during many physical activities. This is why it is important to use lumbar support to prevent and treat back injuries. Learn how to treat lower back injuries and stay fit in this sports medicine how-to video.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

If you want to program an RCA universal remote control, you can follow this professional's advice. Make sure the batteries are in place, and turn on the device you want to control. On the top row of the remote control, there are buttons labeled with the names of different devices. Press the button for the device you want to program, and press ON/OFF button at the same time. The light under the ON/OFF button will light up indicating you are in program mode. Press the play button on the lower p...

The Paris-based technology conference Viva Technology, which hosted the likes of Apple's Tim Cook and Facebook's Mark Zuckerberg, is now over.

For over three decades, Microsoft's landmark program, Excel, has helped businesses accomplish tasks and problem solve quickly and efficiently. Whether you're a budding entrepreneur or navigating a remote career, Excel can help you apply your business skills at a higher level.

I got my first Philips Hue White and Color Ambiance bulbs because they're the consensus best of the best for colored lighting. But after spending 90 bucks on two light bulbs, when it came to all the accessories like switches and buttons, I went with cheaper third party options. Little did I know, I was overlooking a great first-party accessory with a surprisingly reasonable price.

Microsoft has unveiled practically every detail of the HoloLens 2 except for when eager developers and enterprise customers can expect to receive the device.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

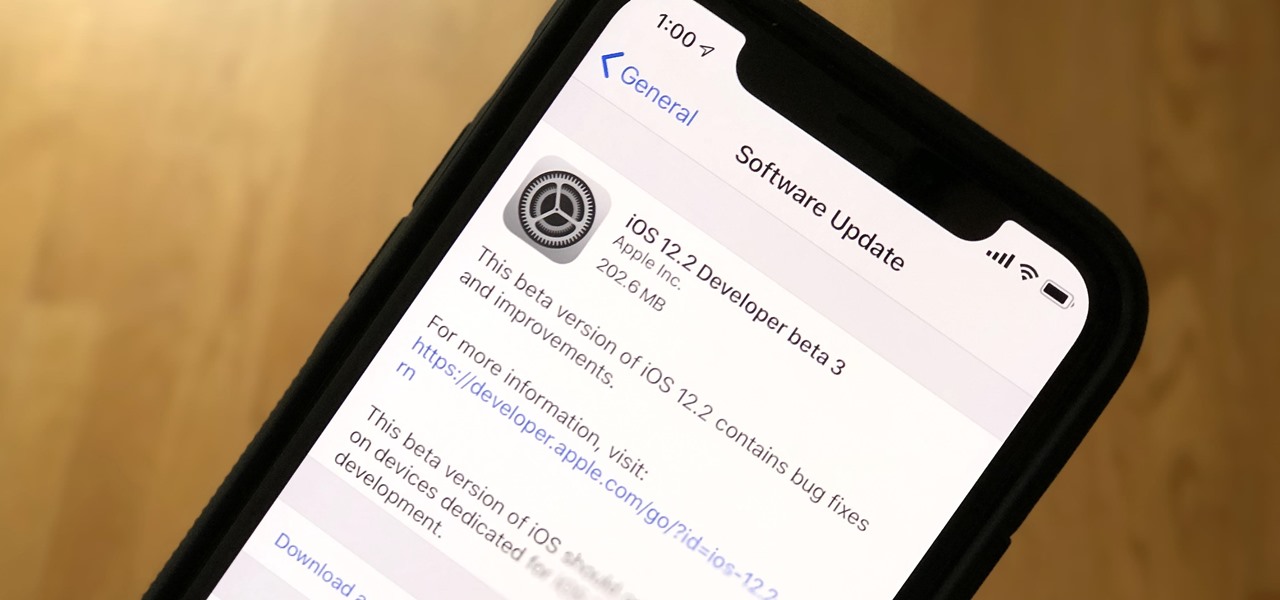
Apple just released the third iOS 12.2 developer beta Tuesday, Feb. 19, fifteen days after the release of iOS 12.2 developer beta 2. Beta 3 fixes an issue with the lock screen, and reintroduces Group FaceTime to beta testers. Overall, iOS 12.2 hosts a wealth of new features as well as bug and security patches.

The mystery surrounding the release of the next version of the HoloLens has been swirling for months, but at least some of that mystery may removed in the coming weeks.

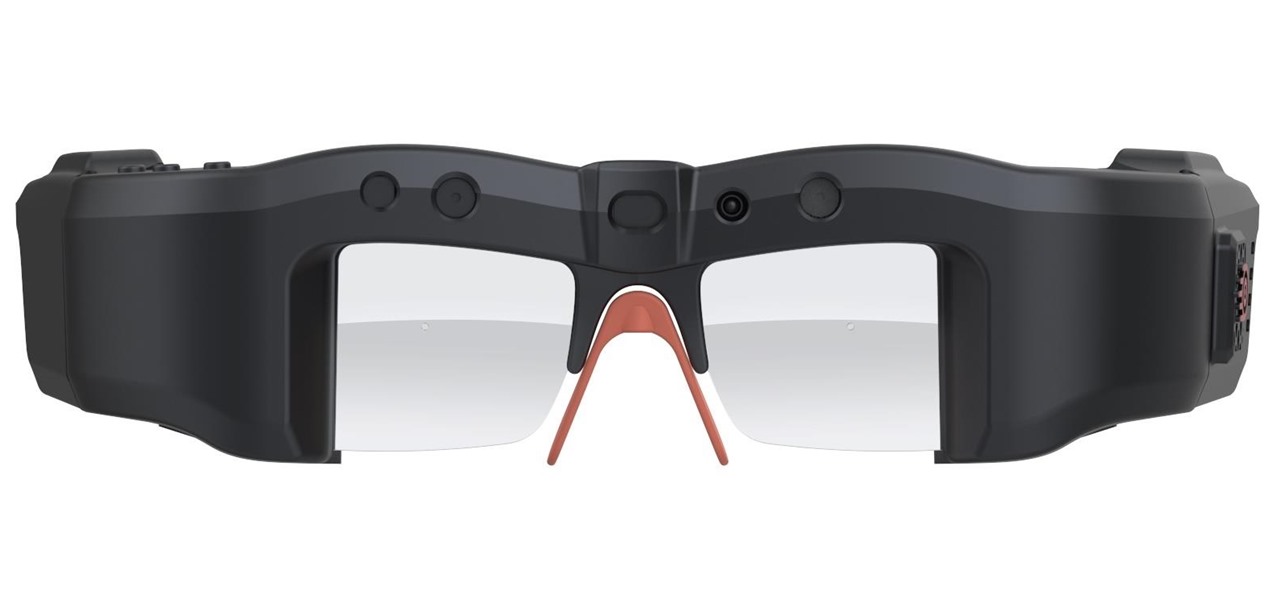
Augmented reality wearables maker ThirdEye Gen, Inc. has officially released what it claims are the "smallest mixed reality glasses" in the X2, which will be available for hands-on demonstrations at the company's CES 2019 booth this week.

Cable TV network Nickelodeon is looking to break new ground with a new series that will be experienced in virtual and augmented reality.

The old school staple of many US homes with children, the remote control race track, has been given new life in augmented reality thanks to the Room Racer app for iPhones and iPads.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Looking to inject a little more processing juice into your HoloLens? Unity can fix you up with the Standalone Universal Windows Platform Holographic Emulation.

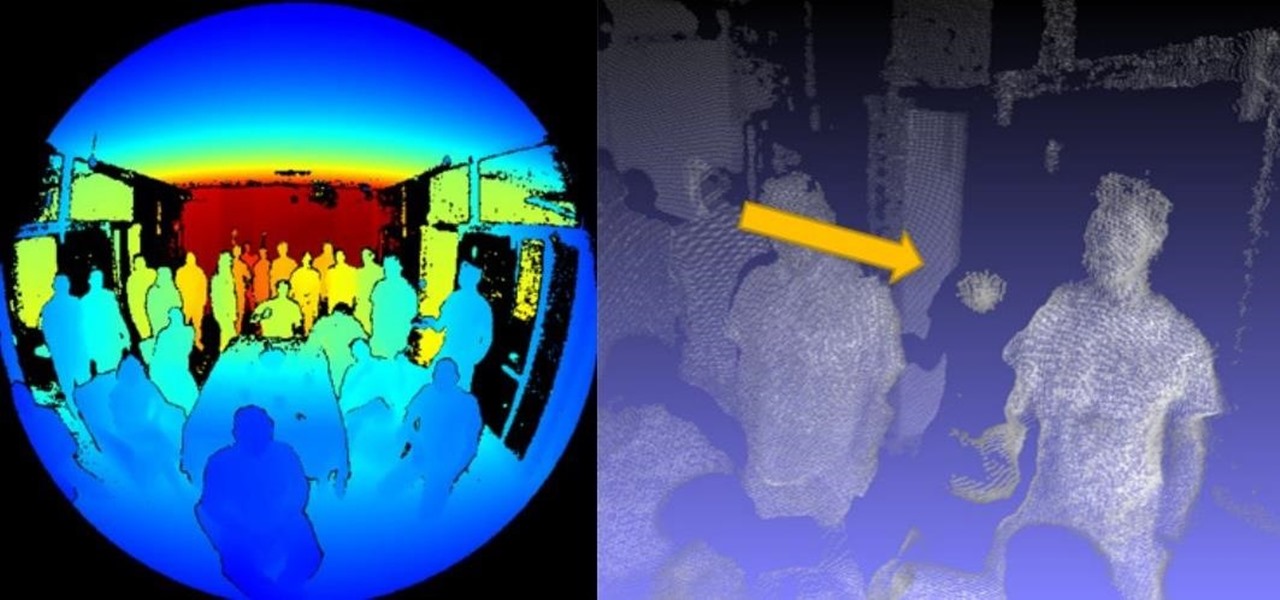
Images captured by Microsoft's next generation Kinect depth-sensing camera that will facilitate augmented reality experiences in the next version of the HoloLens and give computer vision to untold multitudes of connected devices in enterprise facilities, have made their way into the wild.

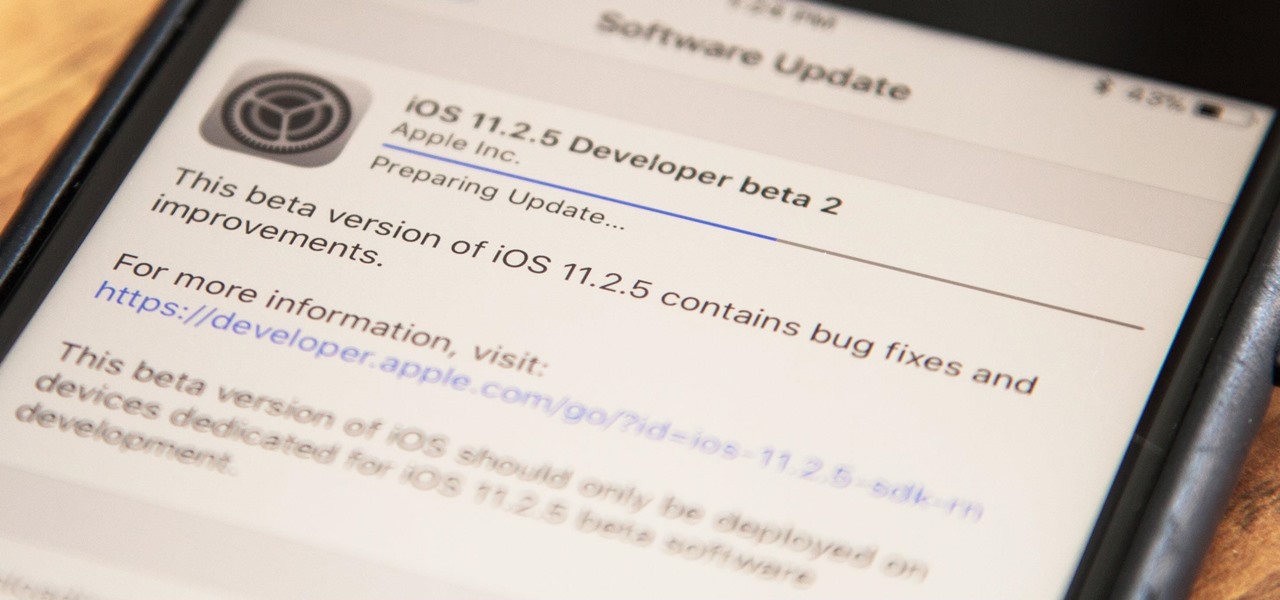
Apple has released the second beta for iOS version 11.2.5 for developers on Dec. 19. The update comes six days after the release of the first 11.2.5 beta which updated the Music app to include a persistent "play bar" at the bottom of the window, along with some bug fixes. Public beta testers received the update on Dec. 20.

If competition in the augmented reality space was a spectator sport, then ARKit, ARCore, and HoloLens dominate the prime-time broadcasts on ESPN.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

In an early morning blog, Jimmy Alamparambil of the Unity team announced a major new update to their ARKit plugin. Developers now can use Unity and ARKit to create AR experiences and test directly from Unity's editor, without deploying to the device.

Artificial intelligence and augmented reality go together like spaghetti and meatballs, and Lenovo has some ideas on how to spice up the recipe.

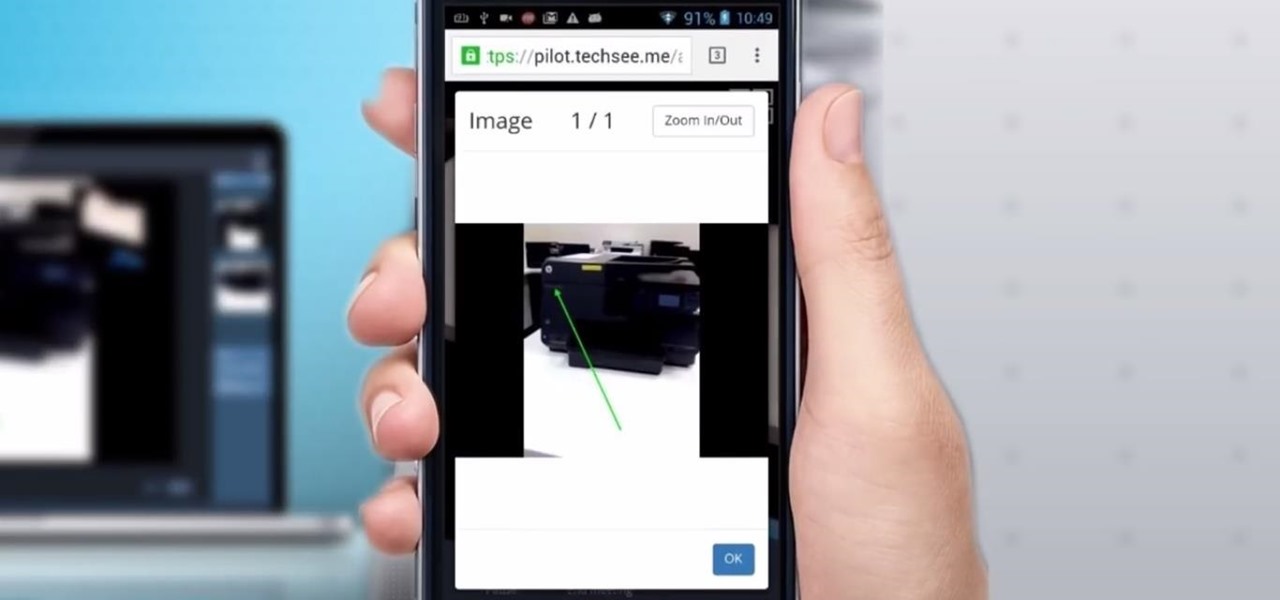
Four augmented reality companies made deals this week to grow their businesses. Two companies, TechSee and Car360, completed funding rounds, while DAQRI signed with a production partner and Decalomania landed a prime spot with a top retailer.

While not quite a true self-driving car, Mercedes is gearing to release a vehicle with a plethora of assistive-driving features, some that might have you excited about what autonomous vehicles can do in the future.

Virtual reality headsets like the Oculus Rift and HTC Vive tether to desktop computers with robust GPUs in order to harness their power. The free-roaming, cordless Microsoft HoloLens forgoes those chains but loses a bit of graphical processing power in the mix. However, a recent report suggests we may get the best of both worlds.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

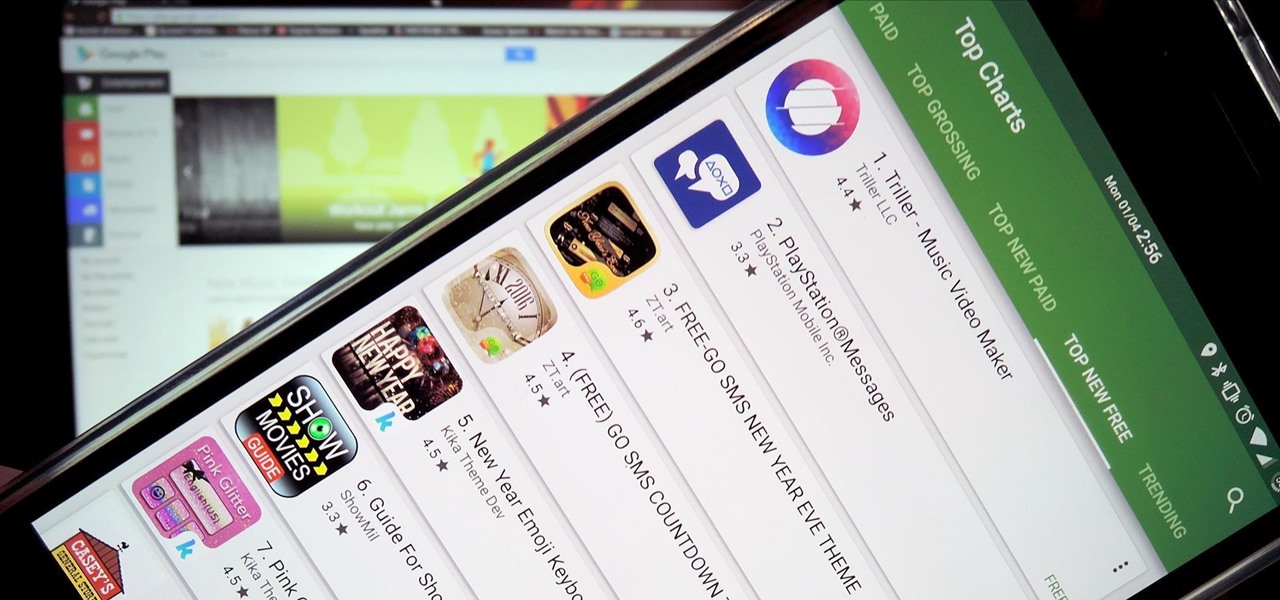
With hordes of games populating the Google Play Store, it's grown increasingly difficult to find trending, non-gaming apps that you might find useful on your Android device. There are a few in the Top Charts pages, peppered in among the various games you'll never play, but other than that you'll have to do some serious searching to discover any new apps.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

Hi , Today i will show you how to do HID Keyboard Attacks With Android BUT without using Kali NetHunter BUT You will need to install custom kernel to your Android device, that will add keyboard+mouse functions to it's USB port,So Lets Get Started