Developers looking to create shared experiences that support both HoloLens as well as ARKit may be able to get it working in Unity since that the engine supports both platforms — though, the amount of effort it might take to get that working could be a bit much. Up to this point, Unity has been the only real approach to attempt this combination — at least, until now.
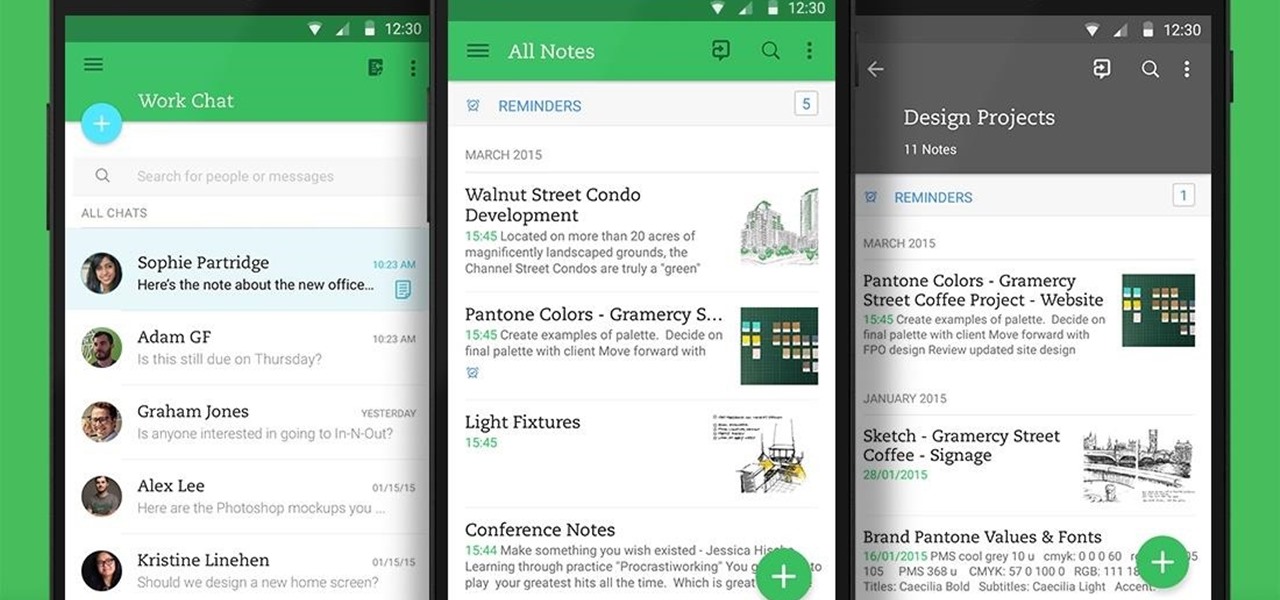
Not many people use their phone exclusively for making calls or sending messages today. If you're an Android user, the chances are high that you're using your phone or tablet for work-related activities. However, the basic set of apps and services your device was shipped with won't satisfy most users. The good thing is that Google Play Store has a nice selection of productivity apps for every task. Below you'll find a list of apps that will help you gradually optimize and organize your digita...
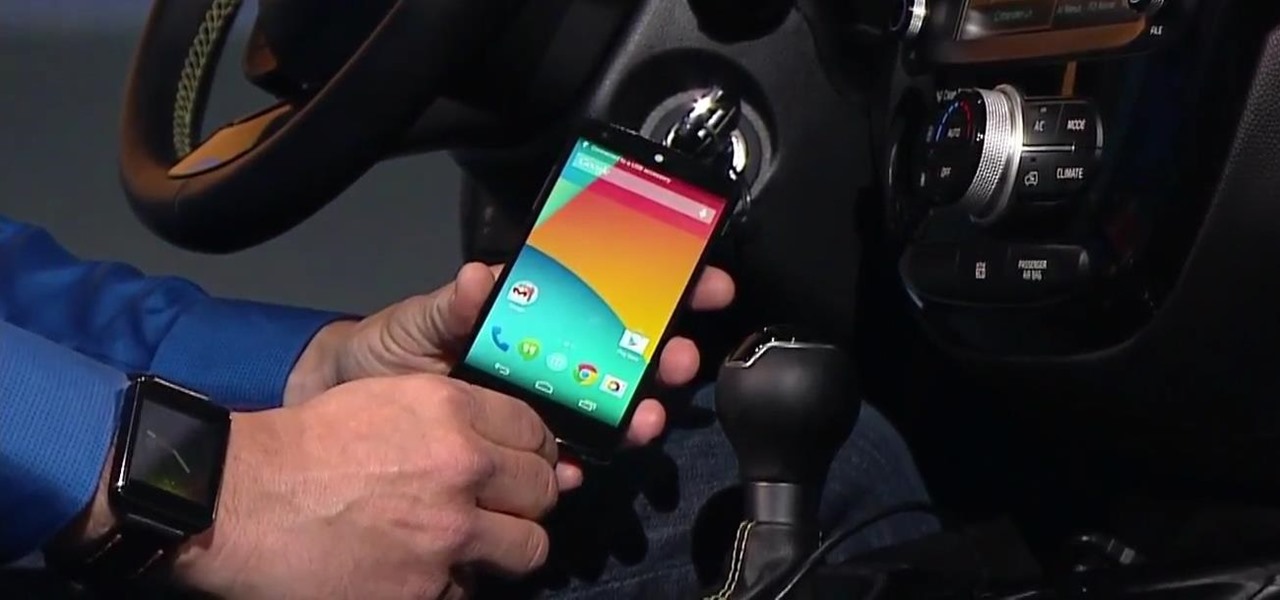
This year's I/O was all about bringing Android into the future and onto new devices. On top of announcing the upcoming "L" release of its mobile OS, Google showcased Android Wear, Android Auto, and Android TV.

Your beloved Samsung Galaxy S3 is nearing the end of its life cycle. Sure, it can do most of what newer devices can, especially if you were lucky enough to receive the KitKat update, but your diminishing battery and scratched up screen have seen better days.

The League of Legends champion Kayle, or Judicator, received a rework a while back and now plays slightly differently because of that. Take a look at this champion spotlight guide by Riot Games on how to build Kayle as a hybrid support champion using the right runes and masteries. Be sure to take advantage of her ult so that you can save someone at the right time with invincibility!
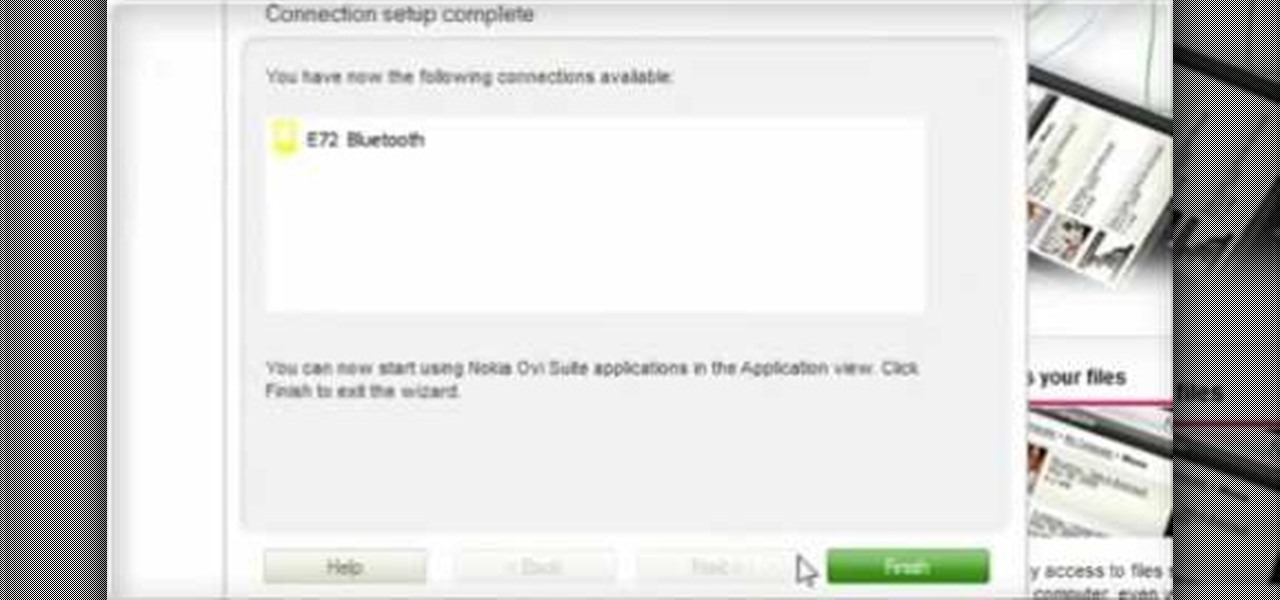
Calendar data, images, sounds, videos, and messages can be easily synchronized between your Nokia Booklet 3G netbook and supported mobile devices and phones when the two are connected using Bluetooth. To find out how to use Nokia's Ovi Suite software to synchronize your data, take a look at this tech support video from the company.

This system won't replace the need for a tripod entirely, but it's a great way to use both a superclamp and an articulated arm to give you a little extra camera support if you can't use a tripod for a particular shot.

This video shows you the most effective ways to use a helicopter as air support when you're playing as the cops in the hot new video game, Need for Speed: Hot Pursuit. Helicopters are especially good at laying down the spike strips.

In this clip, you'll learn how to implement mouse wheel support in Silverlight. Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

In this video tutorial, viewers learn how to chaturanga, pigeon and supported fish yoga poses. For the chaturange pose, go into a push-up position. Then raise your body up into an arch and back down. For the pigeon pose, bring one knee up directly behind the adjacent hand and bring the other leg back. Then bring the bent foot of the bent knee forward. For the supported fish pose, lie down on the floor with a block behind your shoulder blades and upper back. Lie down on top of it and let your ...

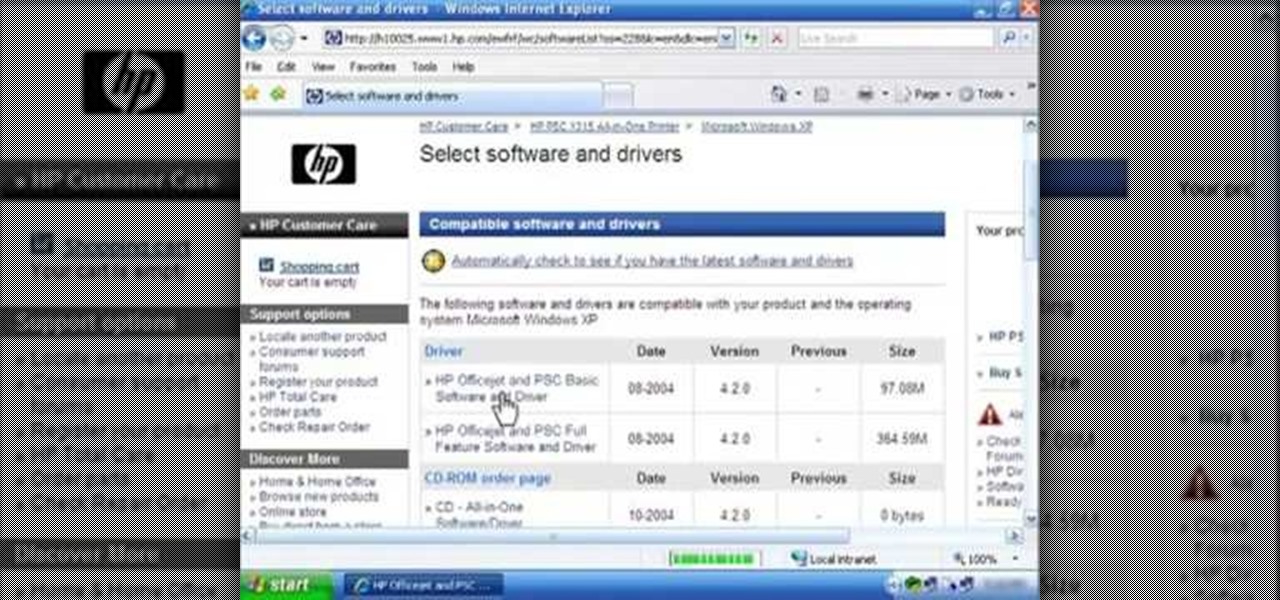
This silent video shows you how to install HP printer drivers for Windows XP. Start off by turning on the power on the printer. Do not connect the USB cable to the computer yet, it'll ask you at a later time. Now go to HP's support webpage by typing "www.hp.com/support" on your web browser and then choose the region and language you want the support for. Now click on the "download drivers and software" option and type in your printer's model number. Select the correct printer from the list an...

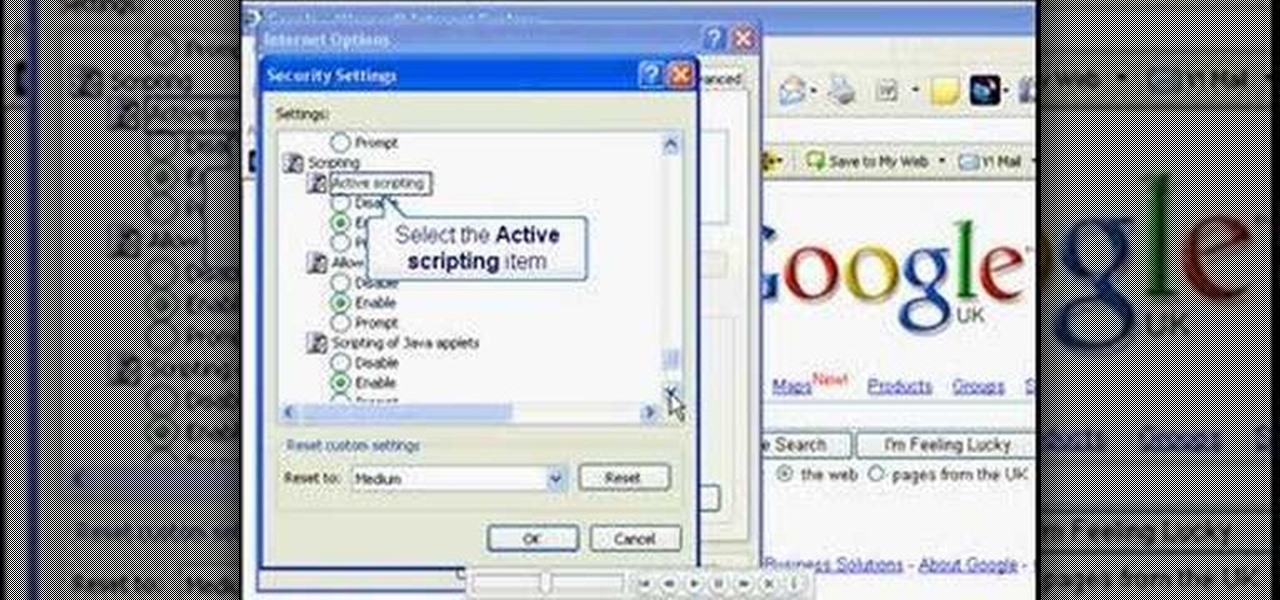
In this video, you will learn the steps to take to enable JavaScript in Microsoft's Internet Explorer (IE) web browser. Although JavaScript support is typically enabled by default in most modern browsers and many web applications depend on JavaScript being enabled to function properly, some persons and organizations may occasionally disable JavaScript to negate the effects of annoying or insecure implementation of JavaScripts on some web pages (such as pop-ups, hidden tracking links, unwanted...

Did you know that there is a difference between knee support and knee braces? Knee braces are great for stabilization, while knee supports have hinges and much stronger. Learn how to treat sports injuries with knee apparatuses in this diet and health how-to.

Slings and shoulder supports are good devices for minor shoulder strains. Learn how to use shoulder supports and stay fit in this sports medicine how to video. Another good suggestions for injured shoulders offered by our host includes getting lots of rest.

Lawrence Moroney shows you how to build an instant messaging application in Silverlight using ASP.Net controls to support international text entry. If you want to add an instant messenger to a web site or web tool and have it support international text entry, then you should watch this Silverlight ASP.net programming tutorial.

Bring harmony to your digital world by getting your iPhone and your computer to work together. Watch this video to get the scoop on RemoteMouse from Cydia, a hack that will turn your iPhone into a remote control for your computer.

Most cars have them… keyless remote entry systems, and the newer Lincoln model cars have them, too. The Remote Keyless Entry System lets you unlock the doors and liftgate by simply pushing a button on the key fob. There is also a panic alarm on the key fob that flashes the parking lamps and sounds the horn. No more fumbling with car keys! Watch this video to see how to use the key fob on your 2010 Lincoln vehicle.

If you're new to DreamCoder for PostgreSQL, one of the first things you may want to know how to accomplish is to connect to a remote PostgreSQL database. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a connection between a given PostgreSQL database and the DreamCoder for PostgreSQL, take a look!

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is to connect to a remote MySQL database securely via SSH tunneling. Happily, this tutorial will walk you, step by step, through the process. To learn how to establish a secure connection between a given MySQL database and the DreamCoder for MySQL, take a look!

Learn how to use your Windows Mobile phone to control your computer. You never have to get off the couch again! Jesus, that's sad.

Tired of squinting over your laptop? There are several ways to turn a big-screen TV into your new computer monitor and enjoy video games, web content, and photos like never before.

Keeping your home clean is an endless battle with time, motivation, and the easy availability of cleaning supplies. That's where the Hard Surface Floor Cleaning Robot Vacuum comes in. This magical device will save you time by automatically keeping your floors clean, never requires motivation, and doesn't require additional supplies beyond occasionally emptying the dust bin.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Although styluses and smartphones have existed together for years, the iPhone has always ignored the pairing. After all, "Who wants a stylus?" But ever since the Apple Pencil made its debut on iPad, the rumor mill has churned out the idea that an iPhone could one day see stylus support. That day will probably come with the release of iPhone 11, and there's a good indicator to make its case.

As you already know, the Galaxy Note 10 and 10+ have gotten rid of the beloved audio jack (RIP). Fortunately, it has never been a better time to switch to wireless. There are Bluetooth headphones and earbuds for every budget and every need.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you have a modern iPhone, you have an excellent video recorder at your disposal. Every iPhone since the 6S has the ability to shoot in 4K resolution, and each new iteration has brought new capabilities to the table. But even the best mobile shooter can use a little extra help. That's where these video recording apps come into play, to ensure the footage you capture is as good as can be.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

The roster of handsets supporting Google's augmented reality toolkit now includes 46 Android models as well as support for ARKit-compatible iPhones and iPads.

A new set of APIs for Unity promise to make it easier for developers to publish apps that support both ARKit and ARCore.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

Smartphones have become such a big part of our lives these days that they're now closely associated with our personal identities. No longer is it Ford versus Chevy, rock versus rap, or PC versus Mac—now, you're either an Android person or an iOS person.

Making sure you have the best gallery app available for your Android device used to be as easy as just installing QuickPic. But late last year, Android's top photo-viewing app was sold to a company who is notorious for permission spamming, so QuickPic quickly lost everyone's approval.

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

Welcome back, my rookie hackers! Now that nearly everyone and everyplace has a computer, you can use those remote computers for some good old "cloak and dagger" spying. No longer is spying something that only the CIA, NSA, KGB, and other intelligence agencies can do—you can learn to spy, too.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.