Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

Reading through various internet forums, it certainly sounds like the Google Pixel and Pixel XL are attracting more iPhone users than any of Google's previous Nexus devices. The sales figures seem to back that up, too, as the Pixel is outpacing last year's Nexus 6P, and pre-order demand has exceeded Google's expectations, causing delays in shipments. (We reached out to Google but they wouldn't give us any specifics on sales numbers or numbers of switchers.)

Android device manufacturers may see the new Pixel "Phone By Google" devices as just another competitor, one that likely won't upset their entry-level margins. But that would be a mistake. Pixel is Google's call to action. With Google now offering as near to perfect an Android experience as we've had so far, OEMs that want to keep selling smartphones in a world flooded with them will need to start working for the privilege.

Forget headphone jacks and "Courage." Look past the shiny Jet Black finish and beyond the minimized antenna lines. Sure, quad-LED flash and dual cameras are nice—but dual-SIM would've been much better.

Microsoft enjoyed a few months in the spotlight after releasing the developer version of the very first mixed reality (MR) headset, but now we're starting to see the competition jump in.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

If you're ever lost or hurt out in the middle of nowhere with a dead cell phone, you might be able to "flag" down help as long as you're near some railroad tracks.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

A little-known company in India is making waves after announcing that it will sell an Android 5.1 Lollipop smartphone for less than $4 (or, more precisely, 251 rupees). The Freedom 251, from Ringing Bells, sounds almost too good to be true. Is that because it is?

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

Being an Google fanboy means that I pretty much use anything with the company puts out, so it's no surprise that out of all the cloud services out there, I stick with Google Drive. But, this is way more than just some blind allegiance.

Baking is one of life's greatest joys. There's something truly magical about taking a half a dozen humble ingredients, mixing them until they're an odd-colored sludge, tossing them into an oven, and watching them emerge as something elegant and delicious.

When you have a parent who cooks—and has you act as sous chef—the kitchen automatically becomes a less intimidating place. In other words, kids who know their way around the kitchen will most likely become adults who cook for themselves, which also means that they'll eat more unprocessed whole foods, save money, and maintain a healthy weight.

Welcome back, my novice hackers! As we saw in my first tutorial on Facebook hacking, it is not a simple task. However, with the right skills and tools, as well as persistence and ingenuity, nothing is beyond our capabilities.

Welcome back, my nascent hackers!

If you've ever searched for a new job online, chances are you've been completely overwhelmed by the process. Clicking through pages and pages of semi-relevant job postings, sending out hundreds of emailed résumés, and filling out applications is tiresome and dull.

While rooting your Galaxy Note 2 certainly has its advantages—everything from increasing security to relieving the Power button of its duties—it's definitely not for everyone.

The Academy Awards, commonly referred to as The Oscars, are airing this weekend. If you're a movie buff or just want to watch the dimes walking on the red carpet, The Oscars is not to be missed.

The bread at your local supermarket will most likely always be fresh, but how do you know which loaf is the freshest out of the bunch? You can squeeze and inspect them like an annoying TSA agent, but there's actually a much simpler way to do it.

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

It's almost here. Another year has come and gone, and it's time to watch the Baltimore Ravens and the San Francisco 49ers battle it out in New Orleans for Super Bowl XLVII. For the truly football-obsessed, this Sunday is a day almost as exciting as Christmas. Personally, I just use it as an excuse to cook food that's way less healthy than usual since I never quite became a football fan (sorry, Dad).

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

Did you know that there's a way to start a fire by squishing air? In this project, I'll show you how to build a tool that does exactly that—and I'll give you a sneak peak into the principals of how a diesel engine operates!

3D printing has been around for a while, but until recently it was used mostly for prototyping and research. Now, with technological advancements, it seems like everyone is using 3D printers, from crime scene investigators to garage hobbyists and hackers. Below are some of the most innovative uses people have come up with so far.

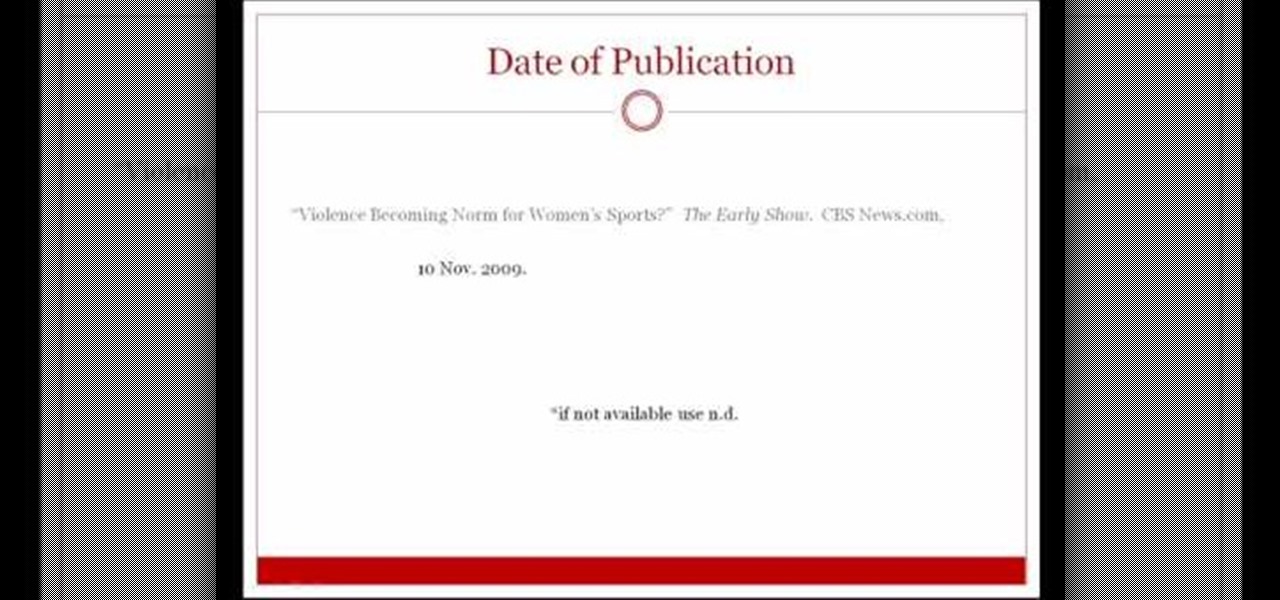
If you're writing a college essay or report, your bibliography is a painful, yet necessary part. And thanks to all of the information available on the World Wide Web, most colleges and universities accept websites as resources in your bibliography. But citing websites can be confusing when using the MLA citation format. This video will breakdown the process.

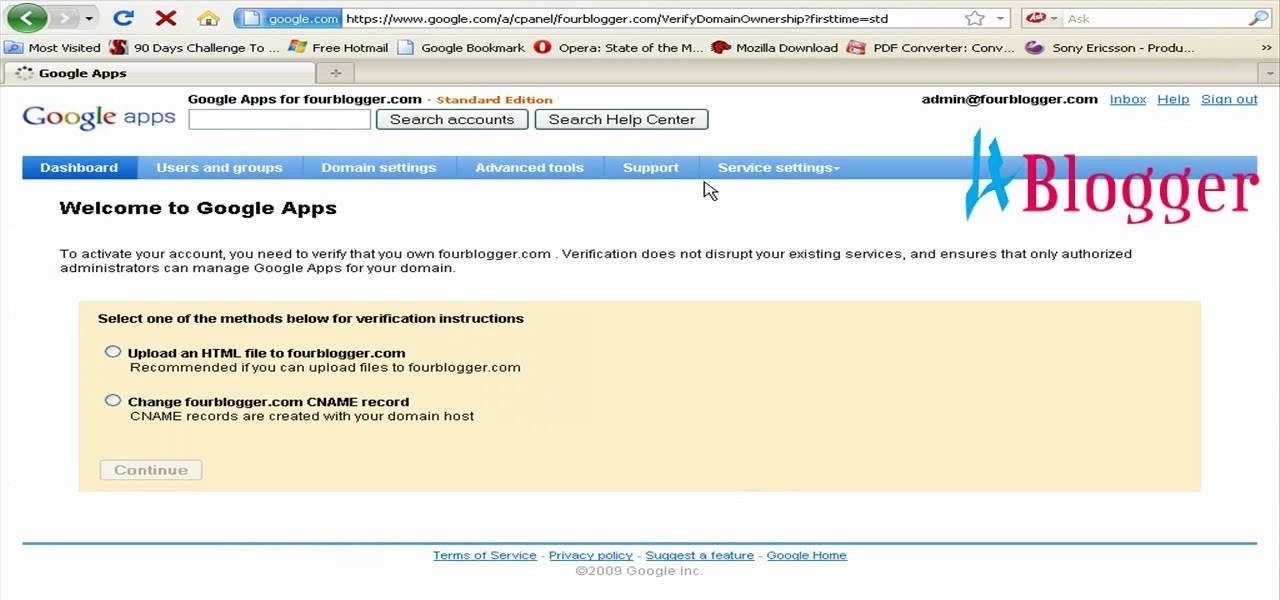
You can create the Google apps email like Gmail for your domain. So to do this first you need to go to the google.com/a and click on the standard in "other Google apps editions". Now click on "get started". Now select "administrator: I own..." and enter your domain name and click get started. Now on next page create your account by filling all the fields and click continue and now fill the info of your administrator account and click I accept button. Now next step is for the verification of y...

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.

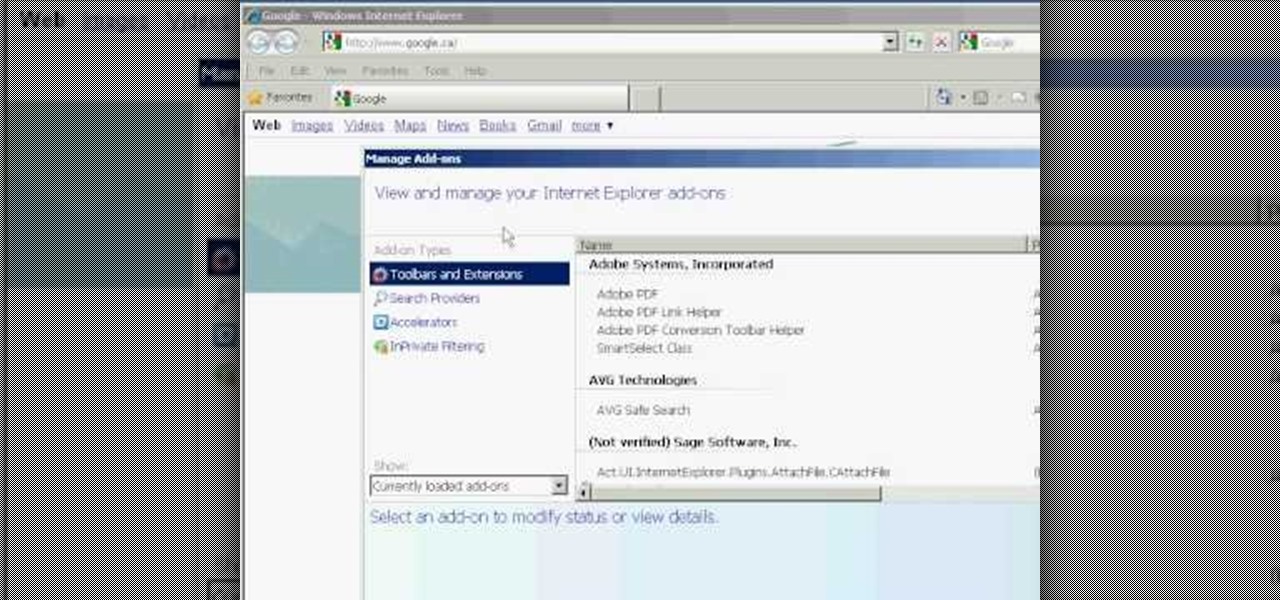
Whethamsolution’s Quick tip walks us through some of the issues caused by use of add-ons in Internet explorer 8 web browser. The video also shows how to manage the add-ons installed in IE8. Add-ons are software’s which enhance the functionality of a web browser. Though most add-ons enhance the browser functionality to a great extent they often tend to slow down the browser drastically. Moreover unwanted add-ons like toolbar's and malicious scripts may cause nuisance to browsing experience...

1. Open the web browser and type www.facebook.com and press enter. 2. In order to be a member you will have to first sign up as a facebook member.

Jennifer Pompa, from the Hairtalk TV Show, describes, "Pop", the company who makes the "StyleMaker" who has the great new "Put on Pieces", which is made of a lot of gorgeous hair on a rubber band that is strong and durable.She says "It's a heat friendly synthetic fiber that you can wear it straight or curly, you can blow dry it to accessorize your look and treat it like your own hair."For a chignon, you can twist your hair into a pony-tail and use the POP as a lovely chignon by twisting it ar...

Cathie Filian and Steve Piacenza demonstrate the way of making medieval candles using tissue paper transfer technique. Steve asks you to first take a piece of tissue paper and a square-shaped chunky stamp. Then you should load the stamp with black pigment. Once the loading is completed, you should cut the tissue paper in square shape and place the shining side on the stamp and give a nice light press with your fingers. Then once you get the stamp image on the tissue, gently take it out and pl...

Our instructor will choose set 2, 6 and 8 to show you what the company offers. On the wrappers are pictures of the types of beads possible with each set. She will create from set 2 today, which makes oval beads. Inside of the packages, such as this package which holds set 2 are several items. First is the thin metal pins or rods that can go into the baking oven with the polymer clay molded around them. Next, two pieces for the mold, a bottom and top that fit together with grooves. There are a...

There's nothing better than being your own boss some say. If you are ready for the risks and the work, take your passion to the next level and start your own business. Learn how to start your own business with help from this video.

Wearing a seat belt while in a car can save your life. Do you know how to adjust and properly use it? Learn how to drive safe and use seat belts properly (Ford DSFL). A professional driver explains how to fasten your seat belt properly.

What do you know about braking in an emergency situation? If you're not even sure what kind of brakes you have on your car or truck, then you need to do some research. Learn how to drive safe and deal with emergency stops (Ford DSFL). A professional driver explains the differences between braking with Antilock Braking Systems (ABS) and standard braking systems.

Driving a vehicle is a big responsibility and road safety is paramount. Improve your driving skills by using your most important tool -- your EYES! Learn how to drive safe and always look ahead (Ford DSFL). A professional driver explains why it's important to look where you want to go, not at an obstacle, when you're driving.

When you're on the road, you want to be in control of your vehicle. The only way to be in control and improve your driving skills is by having good hand positions and correct and comfortable seating position. Learn how to drive safe with a good hand and seat position (Ford DSFL). A professional driver gives this important tip about seating position.

Want to fulfill your dream of becoming an ice cream truck driver? If the idea of rolling around in the sunshine selling ice cream sounds good to you, here's what you need to do.