Use double sided paper, 12-30 parts. Six parts is too small and you can't see the form of the rose. Fold in half. Fold in half again. Fold the bottom tip to the first line and rotate. Repeat with other tip. Do your right side because that's how you attach the units. Be careful not to rip or wrinkle the paper. Fold corner under. Rotate. Fold opposite corner across. Fold down and crease. Repeat on opposite side. Should have two pointed edges. Fold each edge down to form a diamond.

In this video, we learn how to block annoying applications on Facebook. Instead of just deleting these, you can block them so they won't show up on your page anymore! First, click on where it says "via (application name)" it will take you to the application's Facebook page. On the left hand side of the page, underneath the profile picture, there will be a button that says "block this application". Once you click this, you will just need to confirm that you want to block it and those types of ...

Stephanie teaches viewers how to get rid of nasty split ends in hair. First, grab a brush and brush your hair. You'll want to do this very slowly and gently. Avoid pulling your hair out. You should do this to your whole head. Next, wrap a strand of hair around your pinky and underneath the next finger, and over the next and under the next finger. Next, grab hair cutting scissors, drag you fingers down, and you'll see the split ends pop up. Simply split them off when you see them pop up. Repea...

Learn how to make crochet chain stitches to start rounds on a beanie cap with the help of "Shred Betties" Things you need: hook and yarn. Instructions: To start round 2 you need to chain 3 now. Insert your hook into the last loop you made making the yarn placed over. Pull yarn through the loop. Repeat the steps (yarn over, pull yarn through). Make sure the yarn hugs the hook comfortably. Pulling it too tight will make small stitches, making it too loose. It causes unwanted bagginess. Repeat t...
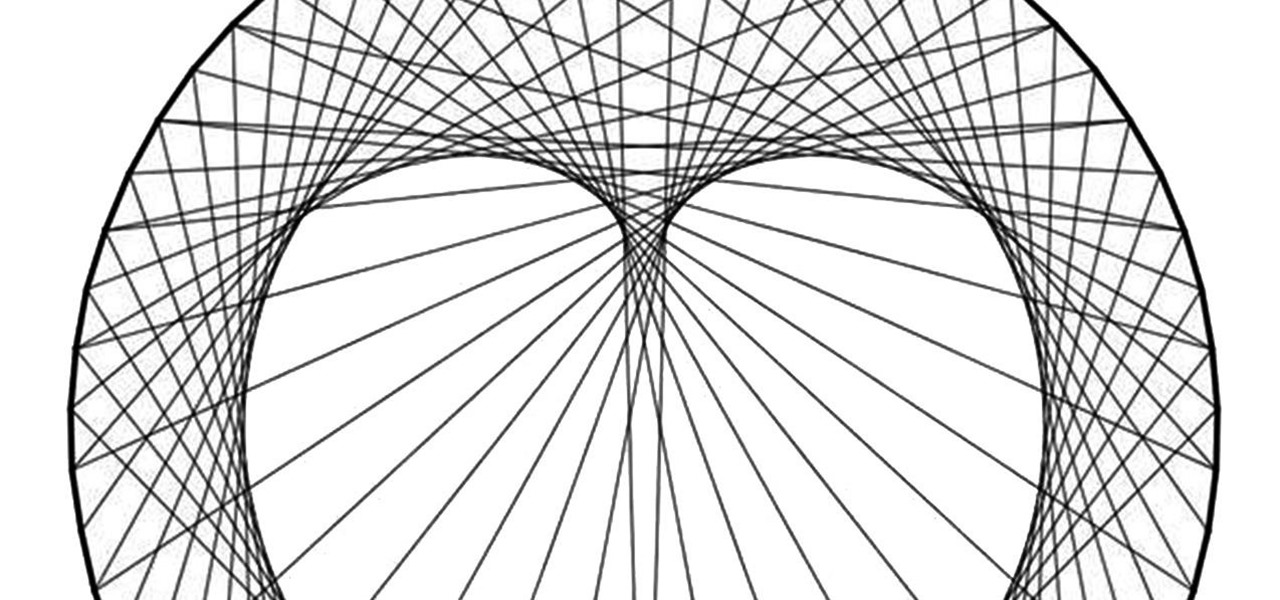
Using only a circle and straight lines, it's possible to create various aesthetic curves that combine both art and mathematics. The geometry behind the concentric circle, ellipse, and cardioid dates back centuries and is easily found in the world around us. From an archery target to an apple, can you name these geometric shapes?
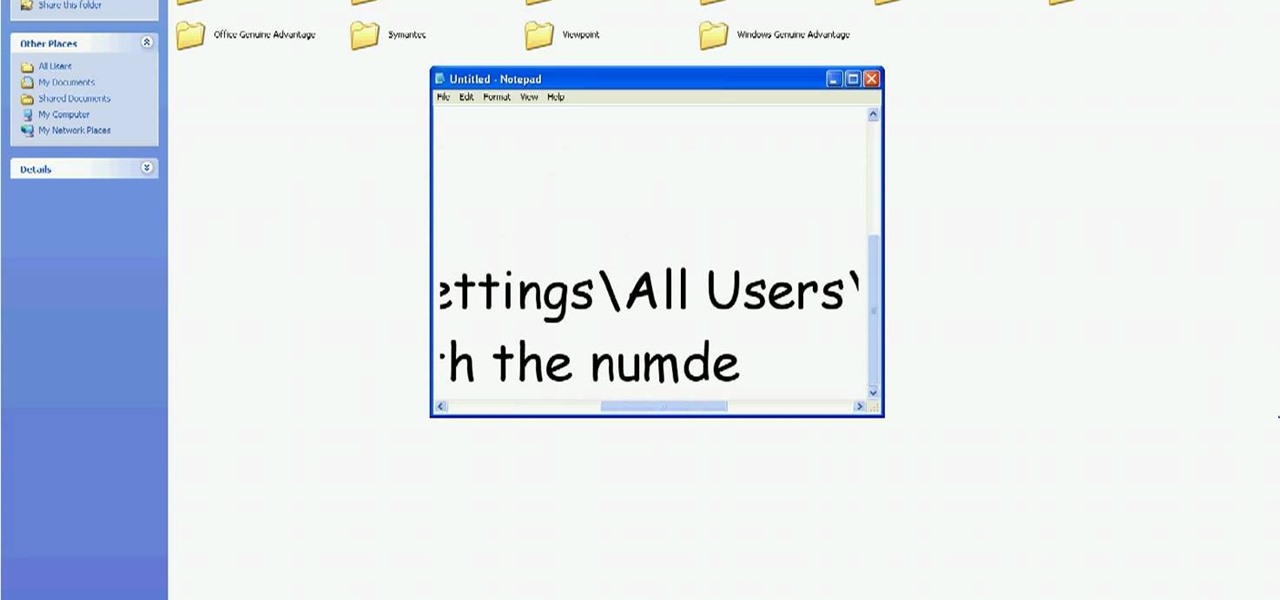
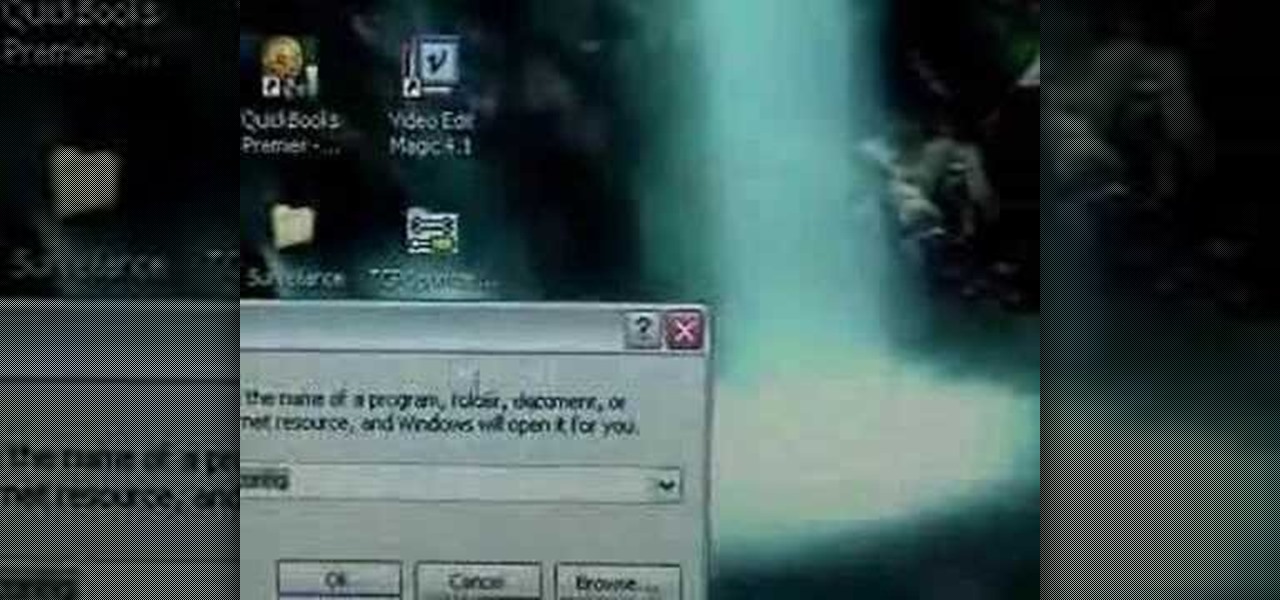
In this tutorial, we learn how to delete Security Tool from your computer. First, you will need to restart your computer. After this, go to your documents on your computer. Then, type in "Type C:/Documents and Settings\All Users\Application Data". After this, delete the file with all of the numbers. If you now get an error that says "access denied" then restart your computer again. Once the starting screen appears, press "F8", then select safe mode and redo the steps that you just took. After...

In this clip, you'll learn how to add or remove software on a Mac. With a little know-how, it's easy. So easy, in fact, that this video guide can offer a complete overview of the process in a matter of a few minutes. (In most cases, it's just a matter of dragging and dropping!) For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

In this tutorial, we learn how to use Eraser to permanently erase data. First, open up Internet Explorer and search for "eraser". Once you do this, click on the first link that you see. Then, go to the download section of the website and download the first version that you see, it will be the newer version. Choose the bit processor that you have, then wait for it to download on your computer. Now install it and go to your Start menu to find the application. After this, open up the Eraser, the...

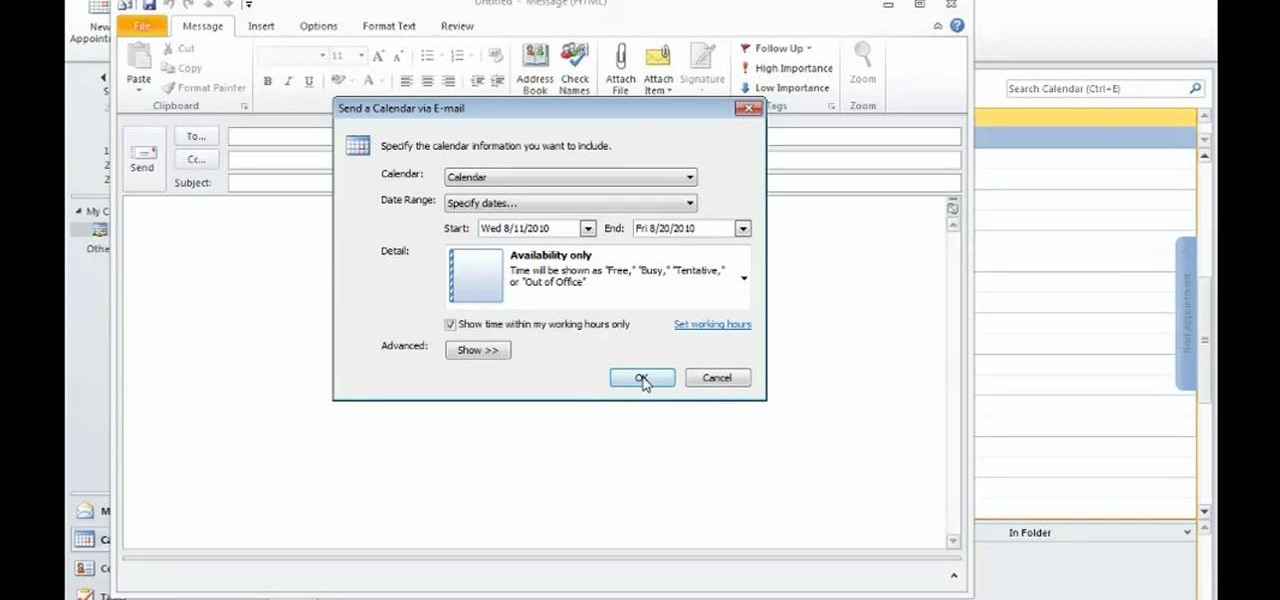
Interested in sharing a calendar? With Outlook 2010, it's easy. This clip will teach you everything you'll need to know. Whether you're new to Microsoft's popular email and scheduling application or a seasoned MS Office professional just looking to better acquaint yourself with the Outlook 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started organizing your own inbox, watch this free video guide.

Go to Cydia and add a new source http://Cydia.xselize.com. Now search there for supreme preferences and install it.

Applying foundation is one of the most basic and most important makeup skills a girl needs to know, yet for many women this is the hardest step. Problems with application, such as not matching the foundation color with your skin color, not choosing the right formulation, and not applying correctly result in foundation that looks fake and caked on.

In order to register a domain name at Name.com, you will need to set up an account at Name.com. When you have set up an account, by supplying a username and password, you will need to log in. You will be able to check to see if your domain name is still available by typing it in, in the orange search bar, near the top of the page. After you type it in, click on search. Try ".org" first.

Just because you update to the Windows 7 operating system doesn't mean you have to lose all of your older programs and applications. Windows 7 has a virtual PC option that you can download, which allows you to use older programs and apps via Windows XP Mode.

There's a lot of questions about screen capture on Android cell phones like Motorola's Droid and the HTC Droid Incredible. Currently (and unfortunately) there is no simple way to take screenshots of you Droid's screen. There are no applications, except for ones that require a rooted phone. But this way may be the easiest for you…

Initially you computer performs at its maximum speed when you install a new operating system. But as time progresses and you install more and more applications the computer slows down due to the various changes in configuration and other settings. So you have to tune up your PC regularly to maintain its performance. Alternatively you can also increase the memory or use a better processor. But even then if you don't optimize your operating system you will face the problem once again. So go to ...

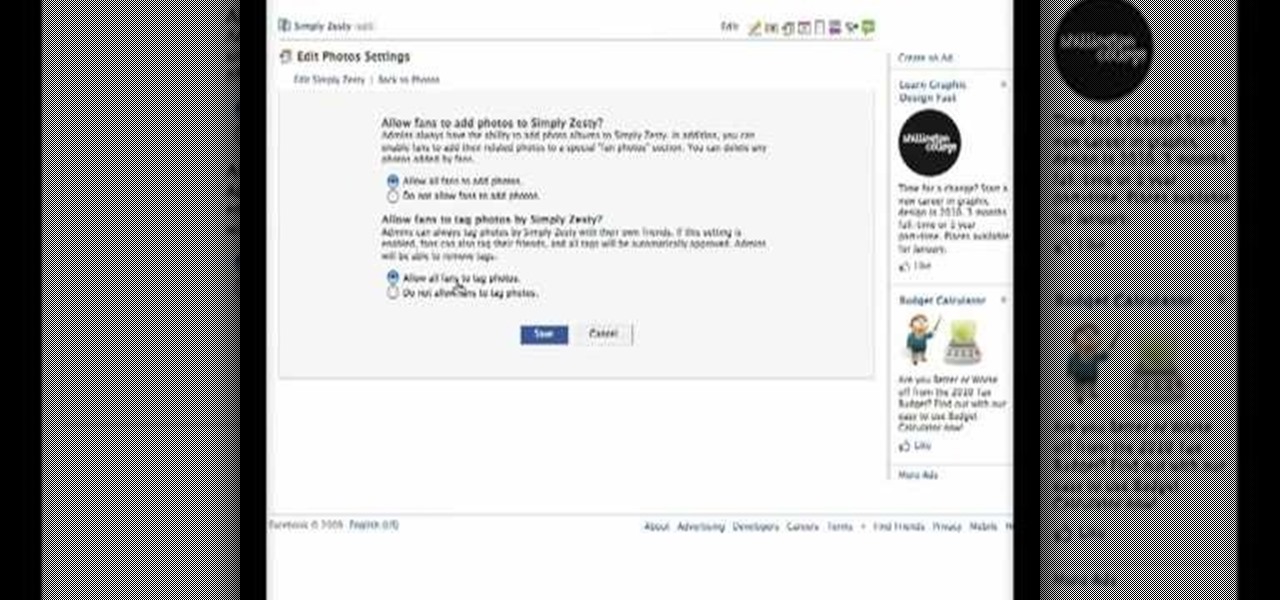
Facebook is the most popular social networking websites that can be used to stay in touch with friends and family. Using facebook you can look up your friends and even see the photos they have uploaded. You can also tag photos in the application. To do this go to your editor page and scroll down to photos. Now click edit settings inside it. At the bottom select 'Allow all fans to tag photos' option and save it. Now when you go to your home page and open the photos section you can tag them and...

In this how-to video, you will learn how to embed a social or fund raising widget on to your Facebook page. Look for static fbml on the Facebook search function. Click on it and add to page. Next, press add static fbml. Now you are finished. Go to edit page and click edit on the application. Now you can embed whichever code you need to paste into your Facebook page. Do not worry about what the code does, as you do not need to know it in order for it to work. Save the changes and go back to th...

Worlds Playground shows you how to install Installous on a jail broken iPhone or iPod Touch. You must have an iPhone or an iPod Touch first or second generation. Your first step is to open your Cydia app. Go to the manage tab of the app and then click on the sources button. The next step is to go to edit and then add. The source you need to add is "http:/cydia.hackulo.us/". After adding that source go to changes and download the MI patch. Once that is done go back to Cydia and changes and cli...

How to Install Installous on any iPhone or iPod Touch? Learn about it in this video tutorial in the Electronics category. For this purpose you will need a jailbroken iPod Touch or iPhone. First go to Cydia and open it. It takes a little time to load. Go to manage -> source -> edit -> add. Then type in this source: Cydia.touch-mania.com. Download and install it. Now you go to search and type in Installous in the search box. Download it and go back to your springboard. Open it up, search for an...

FROMAN1115 teaches you how to change your NAT type to Open on your PlayStation 3. On the PlayStation 3, go to Settings-Network Settings-Settings and Connection Status List and write down your IP. Go to your PC and start your internet browser. Type in 192.168.1.1. This will bring up the router settings page. Go to Applications and games and then DMZ. Check the first box that says Enabled. Enter your IP address below and click ok. Your settings have been saved and you can enter a new internet m...

This short video from The Ceiling Tile Guy, at ceilume.com shows the process and applications of installing an illuminated drop ceiling. These ceiling tiles are amazing, and beautiful. They come in all kinds of patterns and would make an amazing impact on any room in your home or office. With these "Smart Ceiling Tiles" from ceilume you can create a brilliant designer ceiling on a do it yourself budget. This is a fantastic idea to look into if your thinking about starting a similar project at...

This video is a quick overview for installing the "Google Chrome Frame" to speed up applications in your internet explorer.

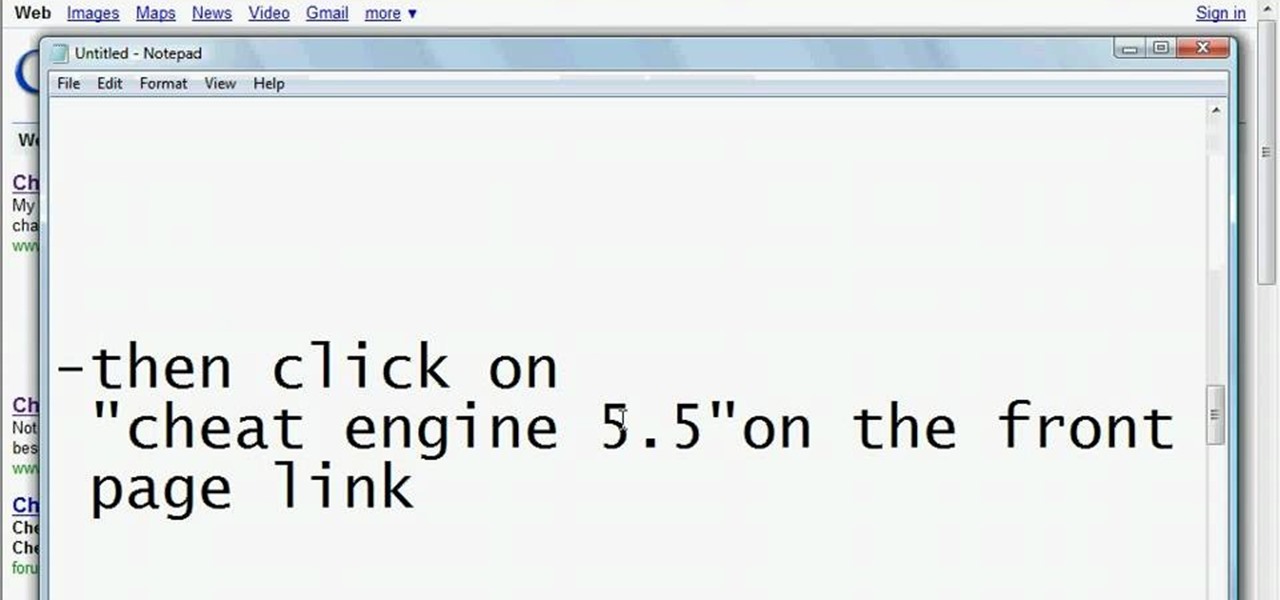
Need the newest version of the flash game hacking tool, Cheat Engine? You can hack just about any game you please with this handy dandy application, but where exactly do you find it? That answer is easier than you think. A simple Google search will bring the Cheat Engine 5.5 download right to you in the first result. Simply click on the first result to go to cheatengine.org or click here to go directly do the download page for Cheat Engine 5.5. Happy cheating!

IMVU is a 3D avatar chat, instant messenger, and dress up game. Get help with all of your IMVU avatar needs with these IMVU tips and tricks! Watch this video tutorial to learn how to make hair for an IMVU avatar pic in Photoshop.

IMVU is a 3D avatar chat, instant messenger, and dress up game. Get help with all of your IMVU avatar needs with these IMVU tips and tricks! Watch this video tutorial to learn how to make a catalogue picture for IMVU. This will show you all about making your catalogue picture using such programs as Paint and Photoshop.

Green eye makeup, as shown in this how-to video, is very complimentary to brown eyes. The cosmetics used to create this look are MAC Liner - Teddy, MAC EyeShadows - Juxt, Humid, Juiced, Milani Liner - Golden Eye, NYX EyeShadow - Sahara, Urban Decay EyeShadows - Graffiti, Shag, Maybelline Define-A-Lash (pink bottle) - Very black, Max Factor 2000 Calorie - Black, MAC - Feeling beauty powder, Revlon Colorstay liquid - Caramel, Posner Coverstick - light/med, Revlon Colorstay Concealer - Deep, Mac...

For most automotive applications a battery needs to supply a lot of current for a short period of time to turn over the engine and get the car started. With the engine running, the car's alternator produces all the power the car needs. Thin plates inside a starting battery increase the surface area and produce this relative burst of energy. Thicker plates in a deep cycle battery provide a steady amount of current over a long period of time. Deep cycle batteries excel in reserve capacity (RC),...

Check out this quick video tutorial on how to install Opera Mini 4 on the T-Mobile Shadow cell phone.

File collaboration is one of the best integration features between Office 2003/Office 2007 and SharePoint. These task panes allow you to access and modify content in a SharePoint site from within Office without having to navigate to the site using your browser. The feature is available in the following Office 2003 and Office 2007 applications: Word, Excel, Microsoft Project, OneNote, PowerPoint, and Visio.

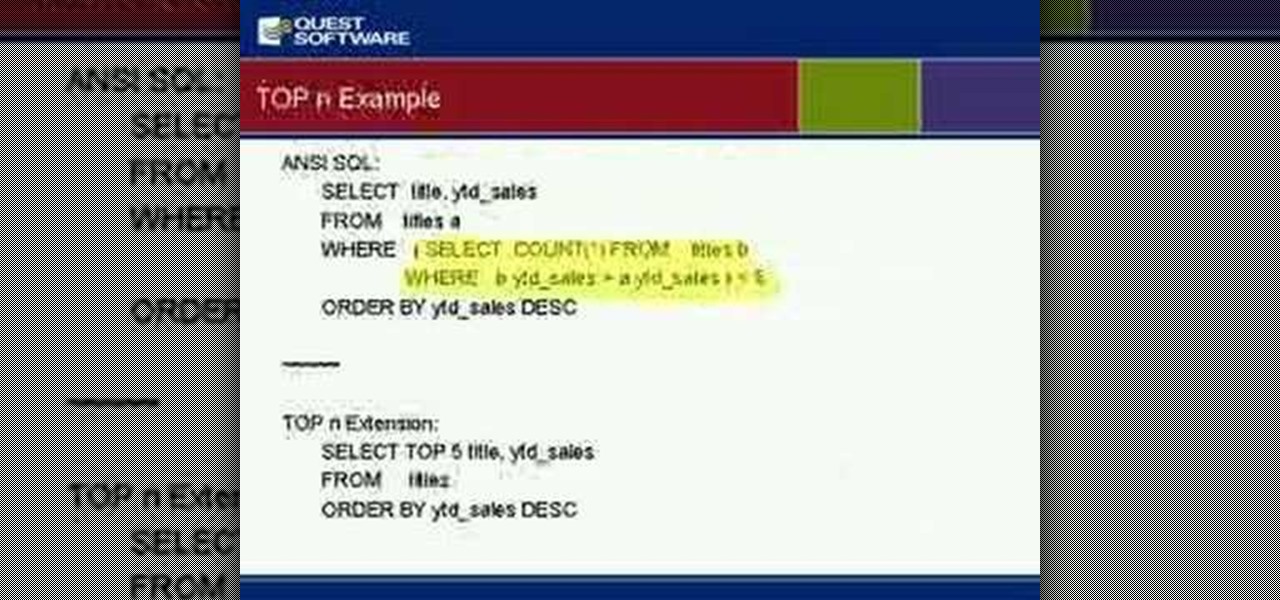
Gain insight into best practices for SQL Server optimization and ways to alleviate many root causes that can impact performance of your SQL Server database. Kevin also will discuss how to manage for planned and unplanned changes, speed time to implementation of your applications and ensure that your databases are running as they should.

Jill Kennedy is the famous UK author of several books on her favorite art - silk painting. In this video, she demonstrates how wax is often preferential to gutta or other resists for it's ability to contain or hold colors. It can be used in larger areas while providing similar effects to gutta's ability to contain dye within regions. Here she emphasizes the ability to work with dyes immediately after application and demonstrates how fun it is to use traditional Indonesian tjantings and Japane...

With Google taking on the sidewalks with augmented reality walking navigation for Google Maps, Apple has its sights set on the road.

The longer it takes Apple, Snapchat, Facebook, and other tech giants to build their own version of augmented reality headsets and smartglasses, the longer runway of practical experience Microsoft gains with the HoloLens and its sequel. The latest example: AR cloning.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

While some widely praised immersive computing initiatives at Google are shutting down, over at Epic Games things are just ramping up, and it involves quite a bit of cash available to indie augmented reality developers and startups alike.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

On Wednesday, in addition to uploading another batch of videos from its L.E.A.P. conference to its YouTube channel, Magic Leap also launched a new video series for developers called Spacebar.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

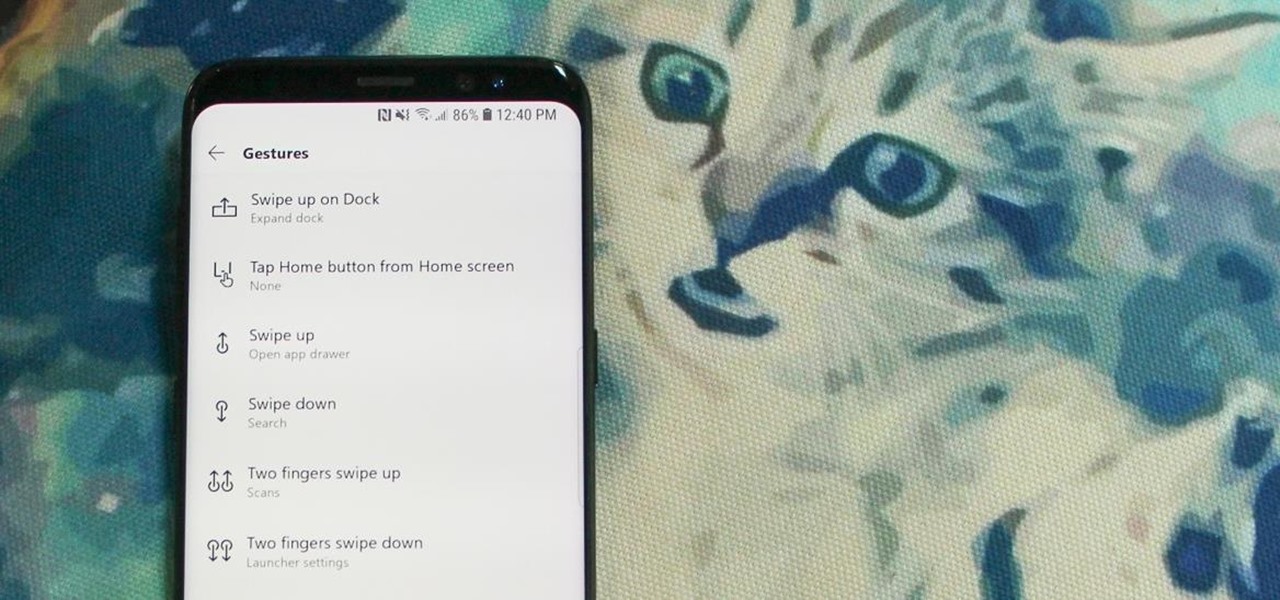
Ever-shrinking bezels and disappearing hardware buttons make for good looking phones, but they also increase the need for gesture controls. Android Pie comes with seven new swipe gestures, but if you don't have the update yet (or find its default gesture options to be lacking), you should take a look at the Microsoft Launcher.