Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

Want to disguise your URLs so that they appear suspicious? In the style of websites such as Tiny URL that take your original URL and give you a shortened one to post on your blog or twitter feed, Shady URL takes your original URL and gives you one that might convince people not to click it. Go to Shady URL and paste the URL you wish to disguise. Click submit, and on the next page it will give you a URL that looks, well, shady. It might include something about a mail order bride or an investme...
» Homeland Security Report Lists ‘Liberty Lovers’ As Terrorists. A new study funded by the Department of Homeland Security characterizes Americans who are “suspicious of centralized federal authority,” and “reverent of individual liberty” as “extreme right-wing” terrorists. » British police get battlefield weapons.

If you suspect that there may be something wrong with the fuel pump on your Saturn car, you should make sure you have proper voltage in the connector in your trunk. If you do, the next step is to check the ground.

Suspicious of the pumpkin pie filling you can find in the store? Just feeling ambitious and want to try to make your own filling? Here's how you can bake a traditional pumpkin pie using real pumpkins. Make sure you get the right kind of pumpkins!
Want music now? Not keen on downloading software or suspicious files to get it? This is a handy media trick from Tinkernut on how to torrent audio files without downloads. Stream music torrents without having to download any torrent software using Bitlet.org .

Skin Cancer Expert Dr. Coyle Connolly, D.O., does a full body check up on patient to detect if there are any new or existing moles or suspicious lesions that could be precancerous or cancerous.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.

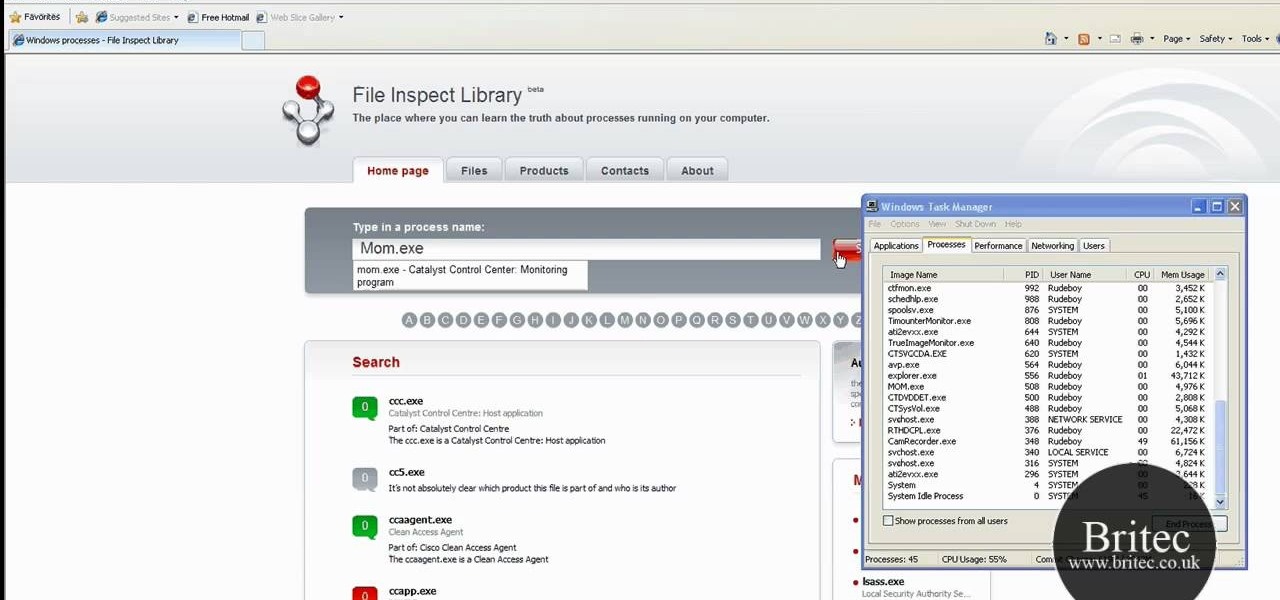
Need help figuring out what a suspicious process is up to on your Microsoft Windows PC? With FileInspect, it's easy to figure out whether a given process is benign or malicious. So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For complete details, including step-by-step instructions, watch this video guide.

Earlier last week, there were a number of fake five-star WhatsApp reviews to be found on the Google Play Store. Now, Gmail, Chrome, Messenger, and Firefox are all the latest victims to be saturated in five-star spam that wrongly refers to the word "game" in reference to non-game apps.

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

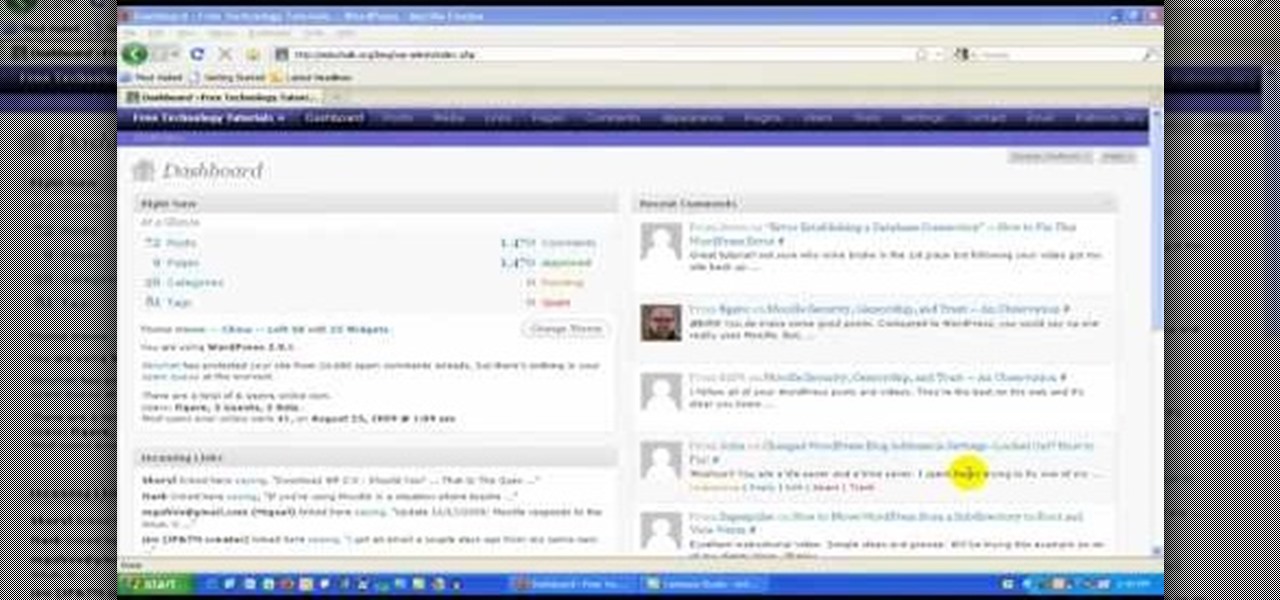
In this video tutorial, viewers learn how to locate and remove spam accounts from a WordPress blog. Begin by logging on your blog and select the User tab. Search through the user list and look for suspicious email accounts. Some keys that reveal spam accounts are: emails that have .ru, poker, Viagra, pharmacy and accounts with more then one dot. Use your common sense to find spam accounts. Select the account you want to delete. Select Delete and click on Apply. This video tutorial will benefi...

The Climbup Insect Interceptor is a new monitor for the use of detecting bed bugs. This is a new monitor. It's a passive monitor. You can place the monitors underneath one of the legs of a sofa or bed or other suspicious piece of furniture. This will not rid your home of bed bugs. This is a way of letting you know where the infestation is or isn't. It is a monitor, but it does not control them. Once the bugs fall into the trap, they can't get out. You will need to properly dispose of them, af...

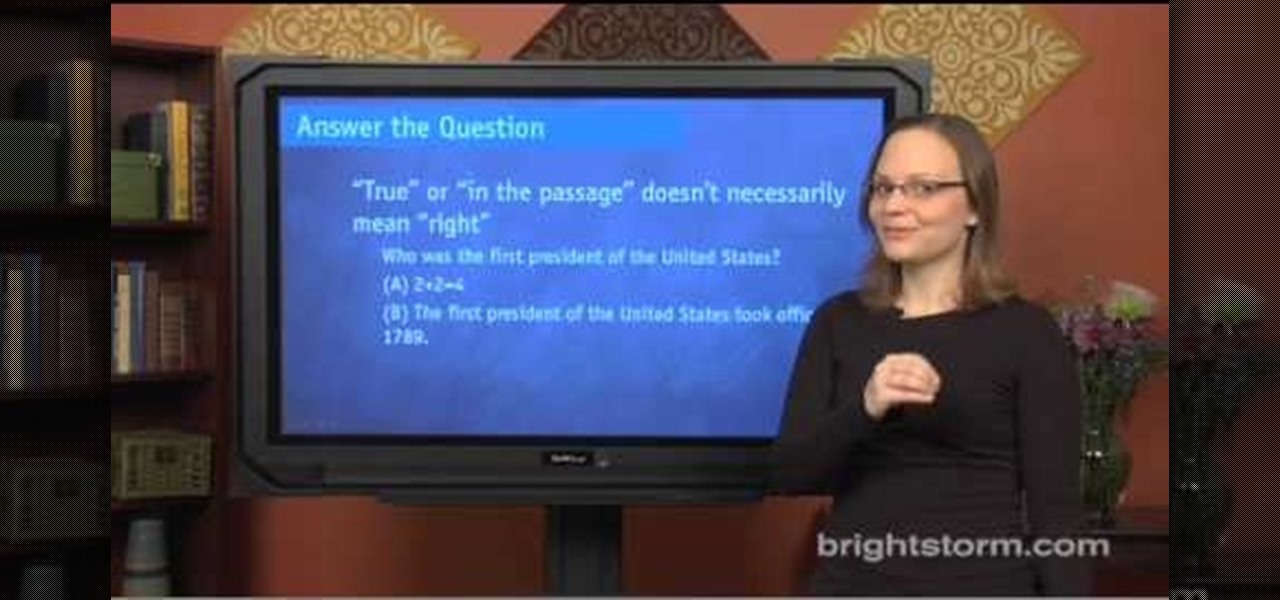
In this Education video tutorial you will learn how to avoid wrong answers on the SAT critical reading area. Five principles to keep in mind are rephrase the question and predict the answer, answer the question being asked, find evidence in the passage, extreme answers are suspicious and finally remember a little wrong is all wrong. To rephrase the question, read 2 lines before and after, ask the question in your own words and find the answer choice that best matches your prediction. Now comi...

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

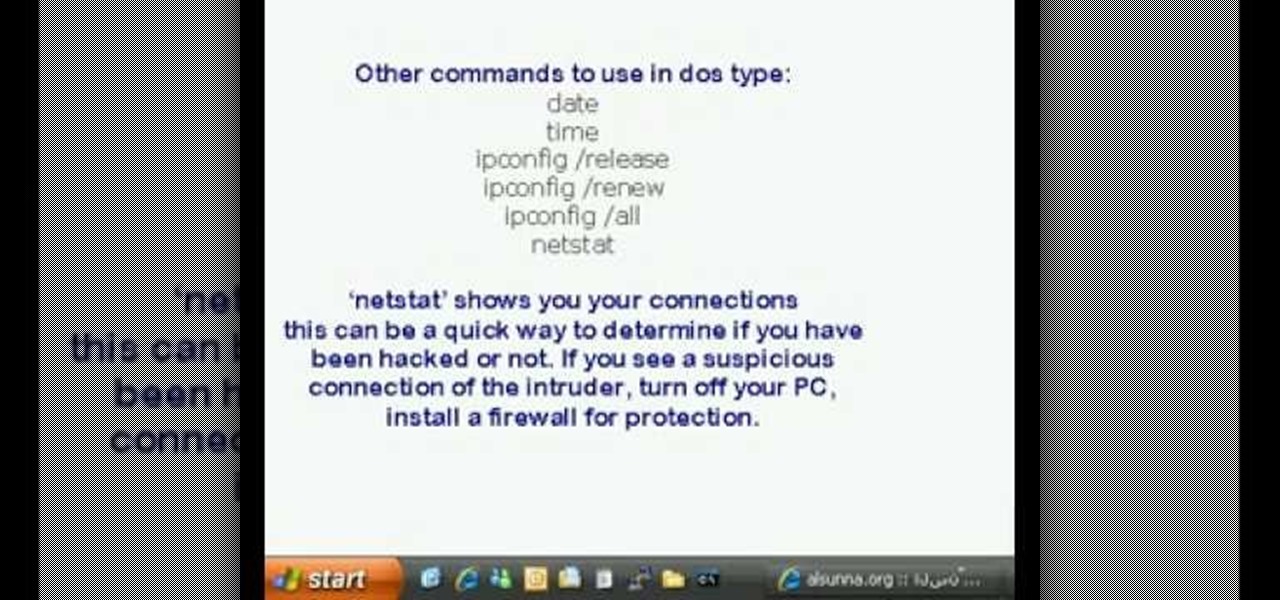
This is a video tutorial in the Computers & Programming category where you are going to learn how to find and ping your IP address. Go to start > run and type in "cmd" to get the DOS window. Here type in "ipconfig" and hit enter. If you are online, your IP address will be displayed. If you are offline, go online and try again. Then in DOS type in "ping yahoo.com". This is to see if you can connect to Yahoo. If you are online, the site will reply 4 times. If you type in "netstat", it shows yo...

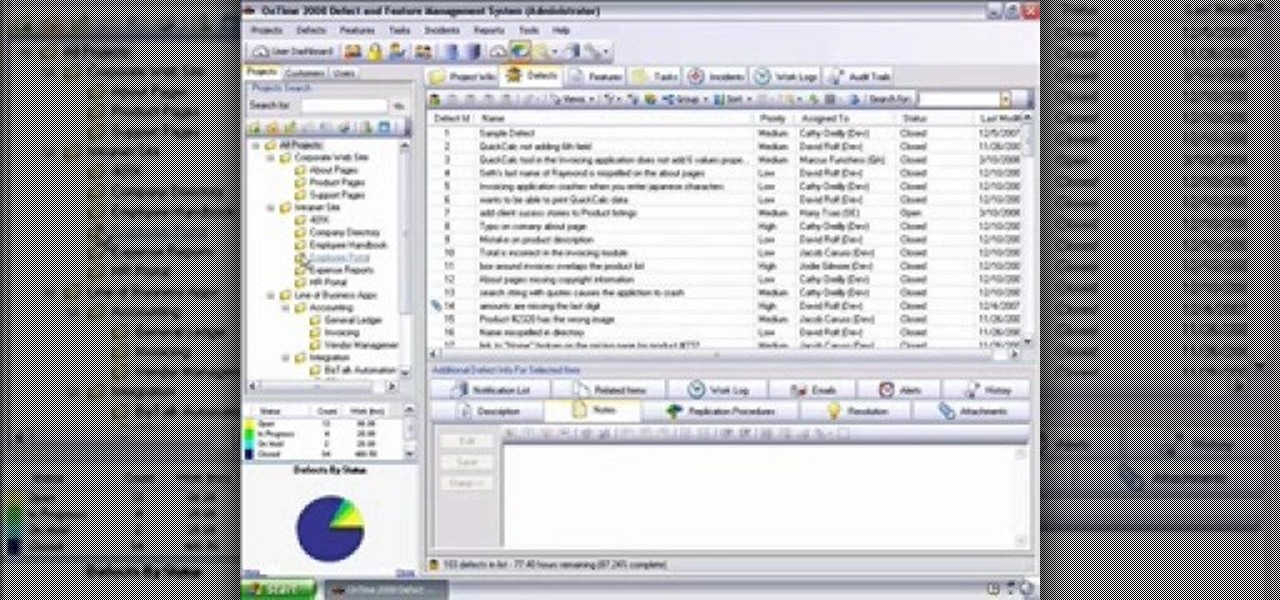
Need some help getting started running reports? This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers the basics of running reports and sending data to those reports. Did you know there are four ways you can manipulate what data is sent to a report without any direct report customization? Take a look!

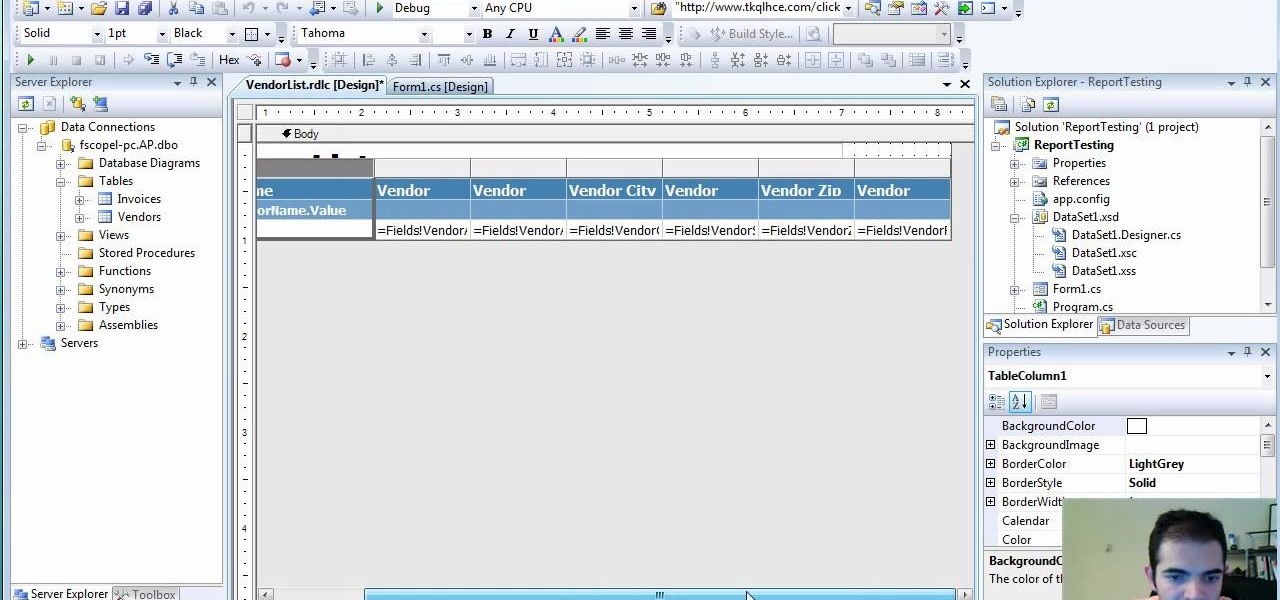
If you're not sure about creating reports in Visual Studio, this two-part video will cover the entire process. This assumes that you already know a few things in Microsoft Visual Studio and the C# programming language. So, if you're not a beginner and still need help to create reports from data in the SQL Server, this is how you do it. Also, learn a quick and easy way to pass parameters to reports in C#.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

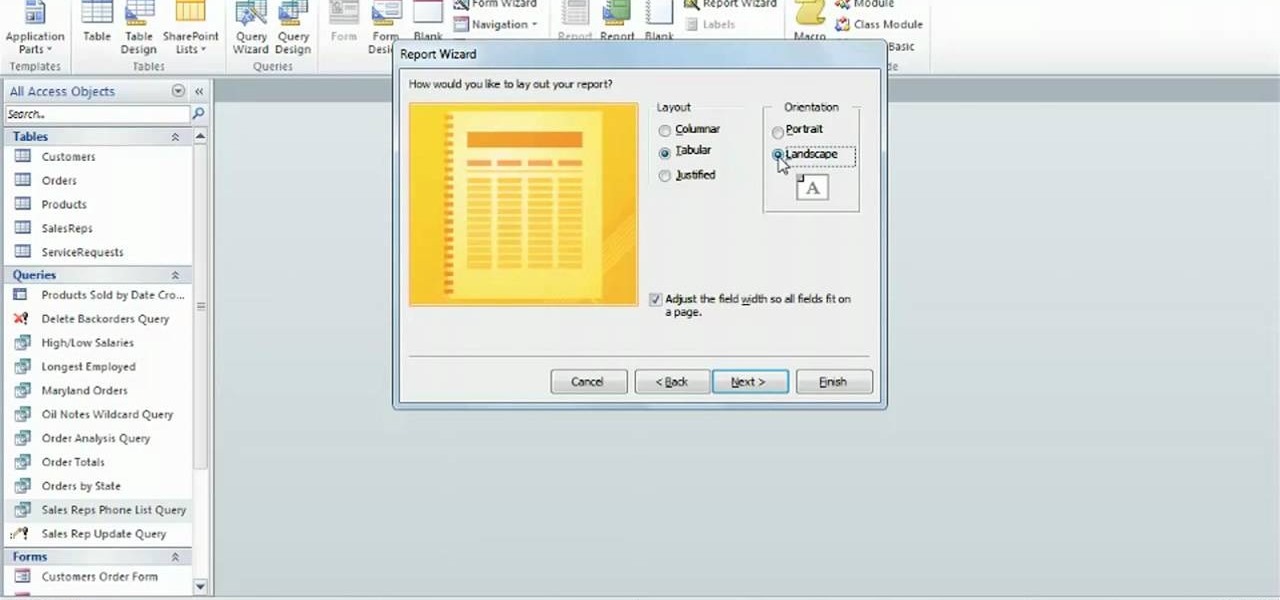
Learn how to work with the Report Wizard tool in Microsoft Access 2010. Whether you're new to Microsoft's popular database management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using the Report Wizard in your own Access projects, watch this free video guide.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

In this video, we learn how to speak English: Reported Speech/Reference Words. Reported speech is reporting another person's words or telling what someone else said. Indirect speech doesn't use the use the exact words that we use. Examples of reference words are: her, she, herself, him, and himself. Types of references can be pronouns or possessive adjectives. Listen to who the speaker is so you can change the reference words so that the statement is logical. Use this example as a reference: ...

In this Language video tutorial you will learn how to report another person's words. In other words how to restate what someone else said. This video focuses on two aspects. #1. What's the difference between quoted and reported speech? #2. When can we use say and tell? In quoted speech you quote the exact words spoken by a person within inverted commas or quotation marks. It is also called direct speech. Here is an example. Jennifer said, "I like birthdays." Whereas, reported speech does not ...

In this video, learn how to export reports to Word, PDF, Excel, and/or TXT formats. Learn step-by-step how to export your reports to any program or format in just a few easy steps.

The first thing that comes to mind when your car is stolen is: ####!! However, once calm, cover these bases when your car is stolen to notify relevant parties and help ensure vehicle recovery or replacement.

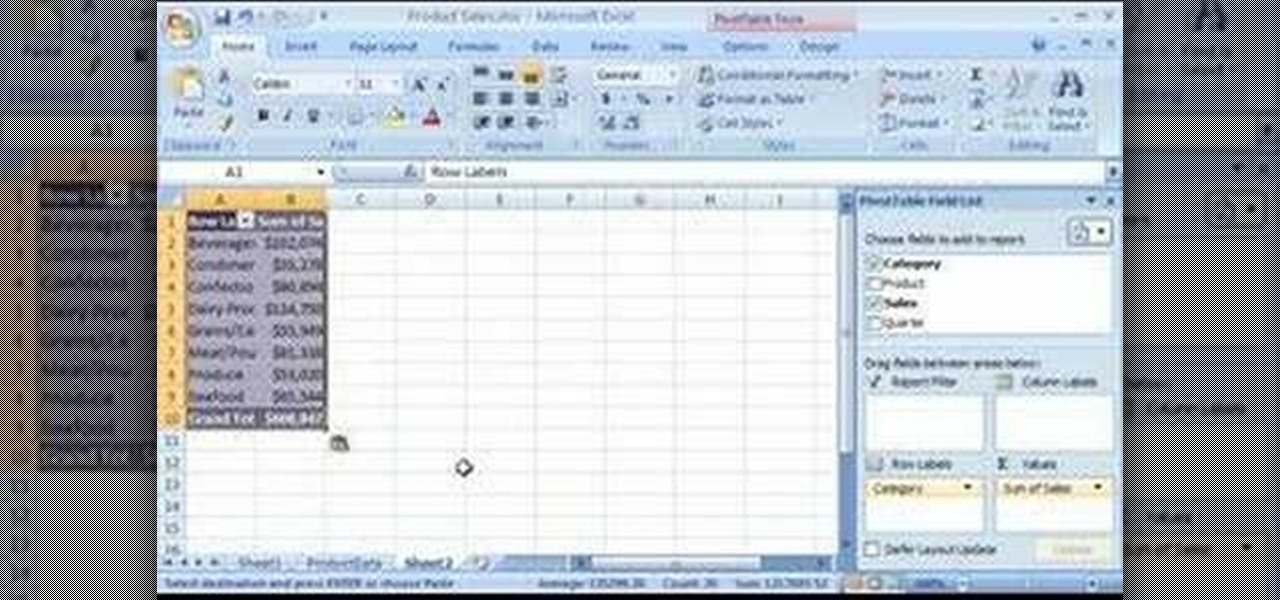
With PivotTable reports in Microsoft Office Excel 2007, your sales report will sparkle with power, flair, and functionality. Take a look at this instructional video to learn how to show the big picture, show all the details, or show anything in between. Easily create multiple worksheets to switch back and forth between the various versions of your report. Sort, filter, and summarize your data any way you like. Show the details of any summary value in your report.

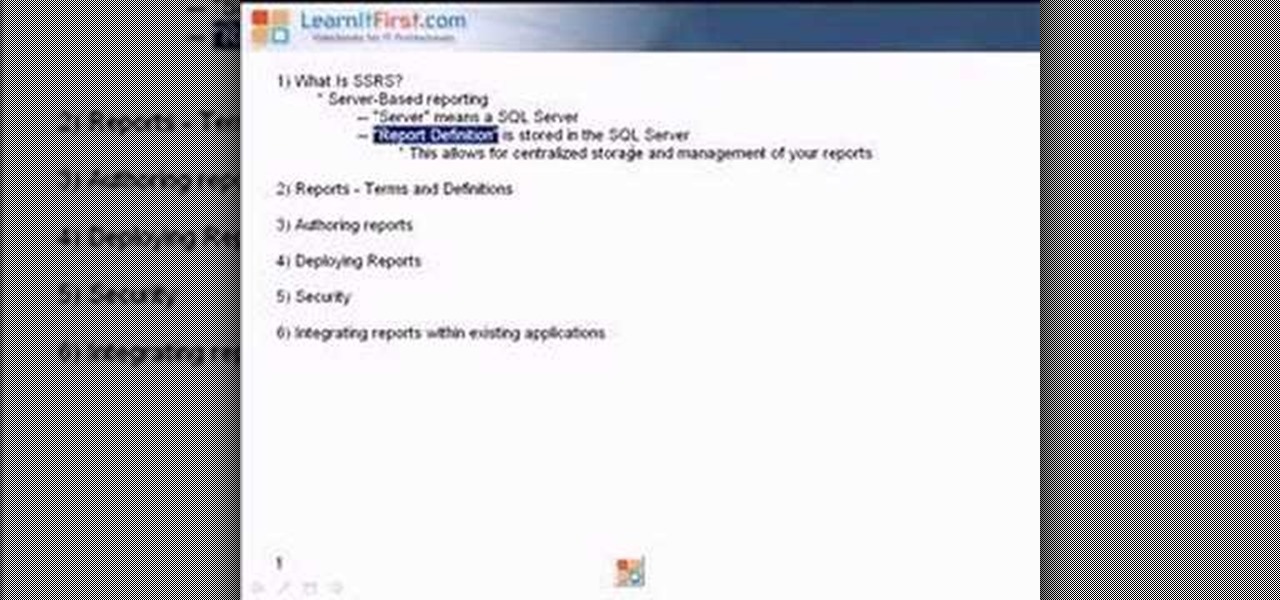
This video talks about what SQL Server Reporting Services (SSRS) is and designed for the absolute beginner - someone who wants a high-level overview of Reporting Services.

Learn how to spot a fake invite on MySpace and report the scam. This happens a lot with music and bands so help them out and report the scams - this video shows you how!

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

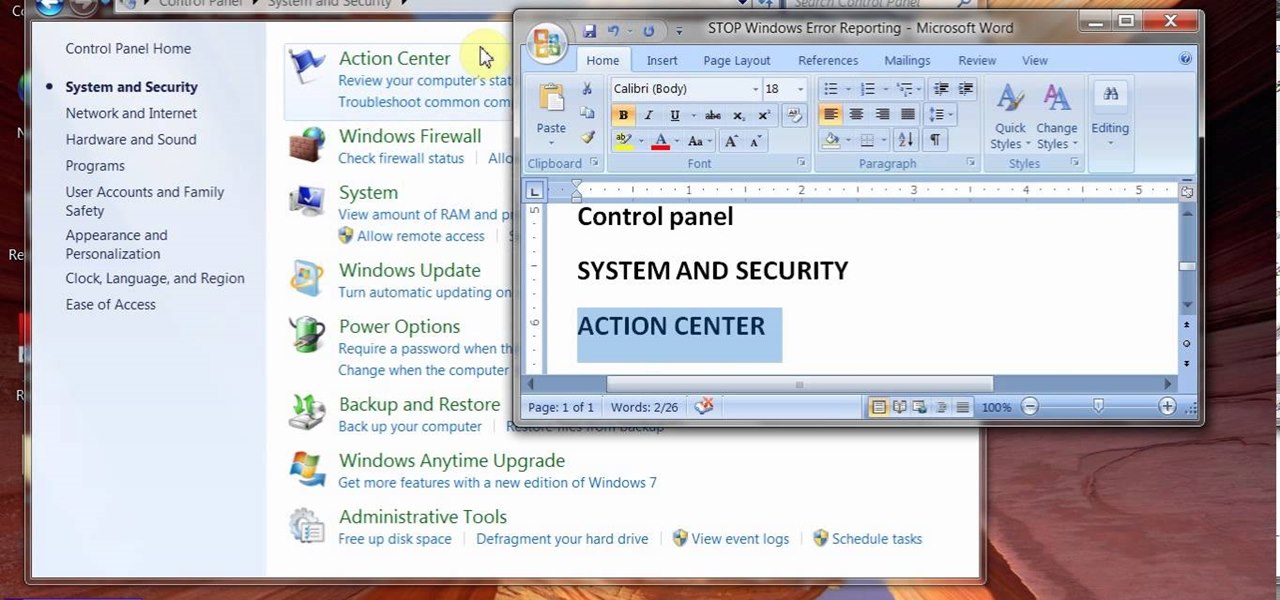
Error reporting in windows 7 sometimes create problem for users. They want to stop or disable this error reporting. Here are the steps to follow for stopping Error Reporting.

You should watch this video if you want to improve your credit score with just 3 steps. To improve your credit score: Check your credit report. It is where your score comes from. You can also get a free copy of your credit report once a year at Annual Credit Report. Check it for errors. Timing. If you're going to apply for a loan as the application month approaches, stop charging because if your balance happens to be reported while it's big, it will temporary lower your score. Don't close you...

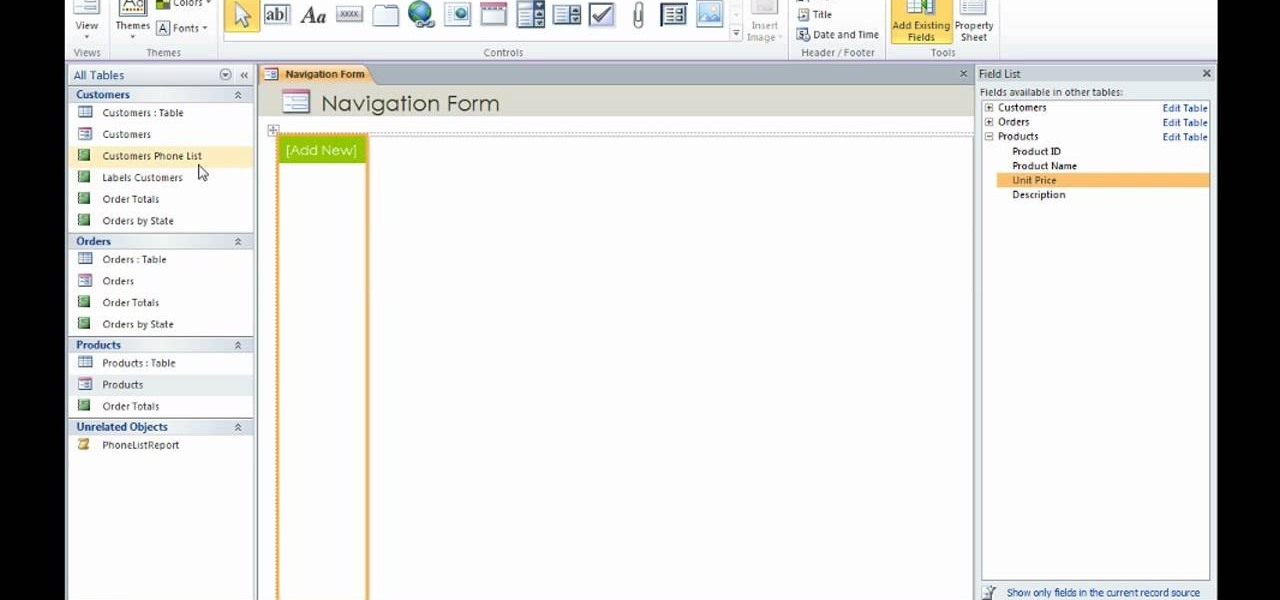
David Rivers shows us how to create navigation forms in Microsoft Office 2010 without writing codes or using logic. A navigation form is kind of like a homepage that will give you a list of reports. There are pre-designed layouts you can choose from to make your navigation form. You will just need to customize your form by adding reports to the navigation pane. What this means for business owners is that you can see customer orders and store reports just by looking at one page. Simple to make...

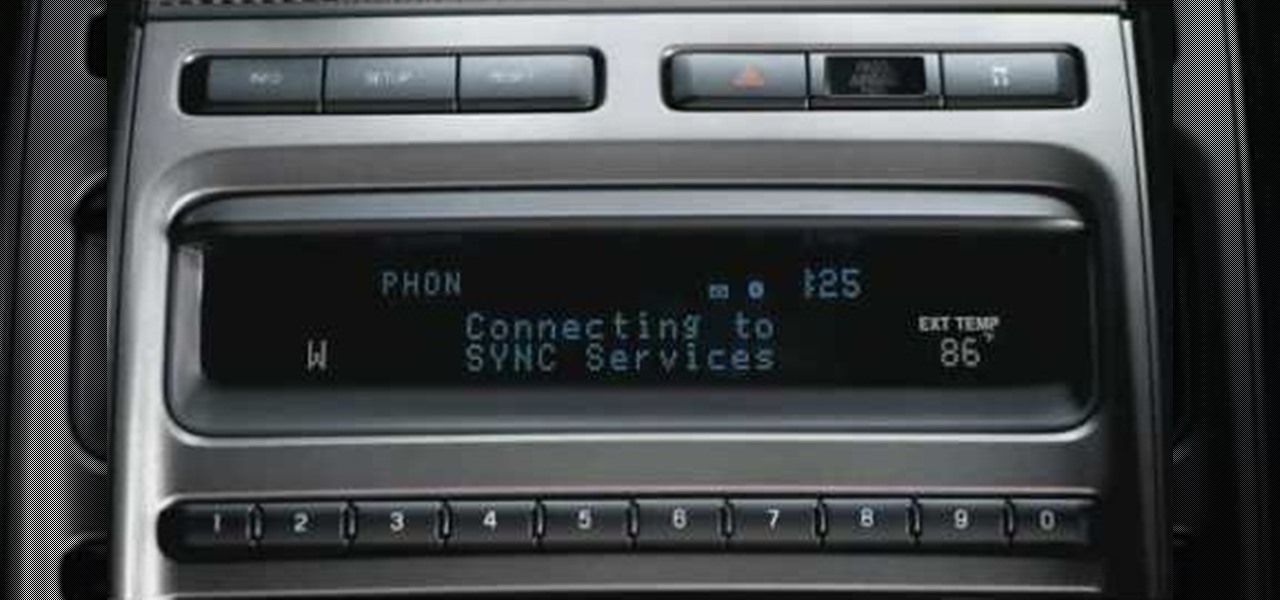
Knowing what traffic lies ahead is detriment to getting home on time. If you get stuck in a traffic jam or road construction, then the only thing you gain is frustration. But with Ford's new SYNC system, you can get up-to-date real-time traffic reports for your local area or specific drive home. Real-time traffic reports help keep you posted on construction, accidents, and other accidents in your commute. You just need to set up some simple preferences on your online owner's account.

To make sure your car is healthy and up to par with required maintenance, you can use Ford's new SYNC system to get vehicle health reports for you car. It gives you vehicle diagnostics, scheduled maintenance, recall information, and more. You just need to go online to your owner's account and set up your reports.