Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

As Microsoft continues to bask in the glow of its HoloLens 2 unveiling and begins ramping up the hype to launch, Nreal and Vuzix are carving out their own niches in the AR hardware landscape.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

To combat their poor coverage in rural areas, T-Mobile spent nearly $8 billion on 600 MHz spectrum in 2017, which was converted to LTE Band 71. With such a low frequency, the signal can travel further, providing LTE speeds to more Americans. But your phone also has to support this frequency, and so far, only a handful do.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.
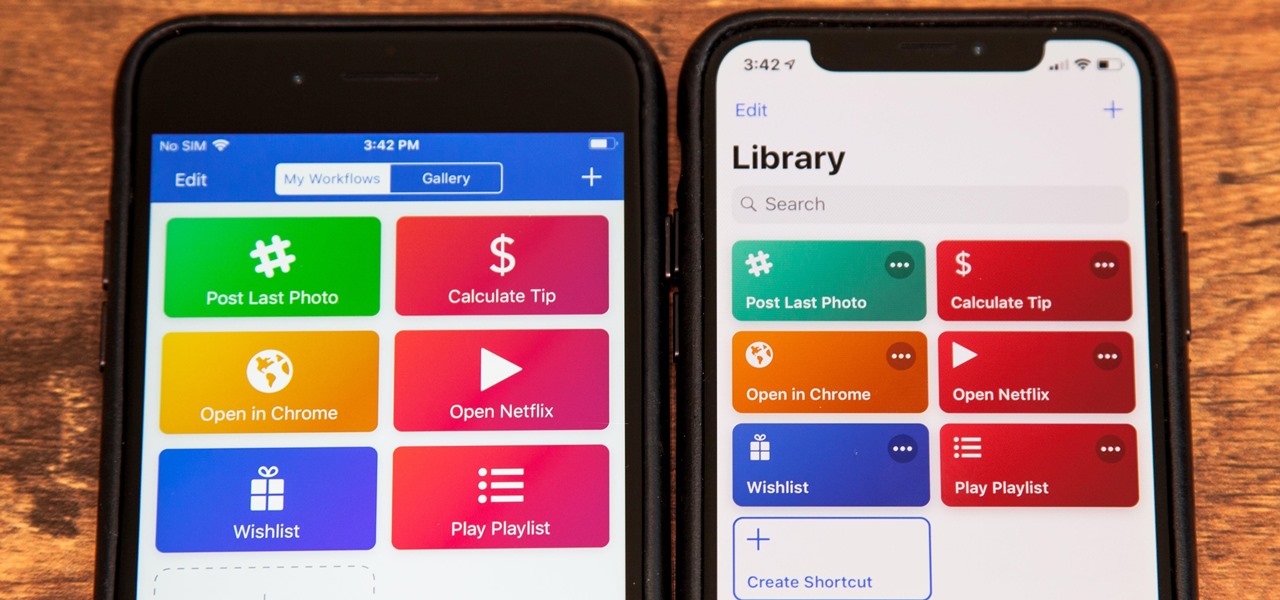
After months of beta testing, Siri Shortcuts has finally arrived on all iPhones that support iOS 12. Anyone familiar with Workflow will understand how useful it is to set custom Siri commands for your favorite apps. Of course, your favorite apps need to be compatible with Shortcuts in order to take advantage of the new feature.

There are dozens of apps like Glympse, Family Locator, and Find My Kids that let parents see where their children's phones are, but they all have one fatal flaw: It's incredibly easy to spoof locations to make it look like the phone is somewhere else.

Apple's testing a new app for iOS 12 called Shortcuts, and it has a lot of overlap with their existing Workflow app. So much overlap, in fact, that Workflow won't be sticking around for much longer.

Action Launcher has some exclusive features that add real value to your overall experience. One such feature is Shutters, and like with most aspects of Android, there's a workaround that will let you enjoy this functionality on other launchers.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

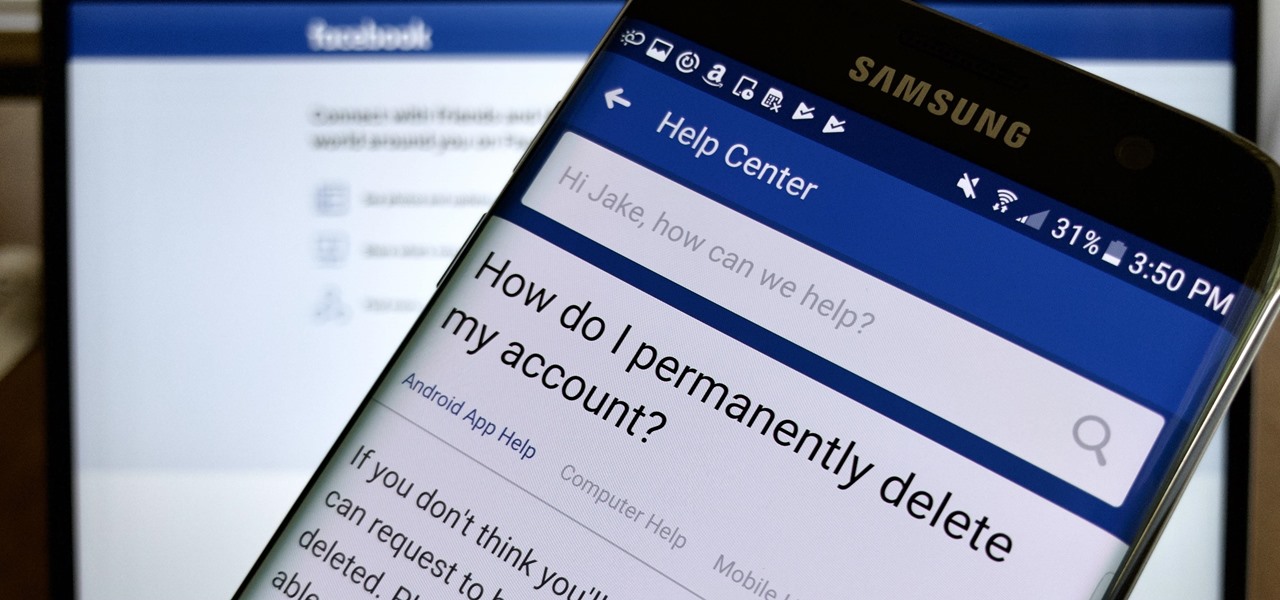
With the news that Cambridge Analytica obtained over 50 million Facebook users' information without their consent, there are no doubt many of us considering that terrifying yet alluring endgame — deleting Facebook. While difficult to figure out, deleting your Facebook account is actually a quick affair. You just need to know where to look.

Technology ages rapidly. We're conditioned to refresh our iPhones every one or two years, and why wouldn't we? New iPhones are fast, and our old ones inevitably slow down, sometimes to an unusable degree. However, it turns out, there's something we can do about that, and it doesn't involve buying a new iPhone at all.

Augmented reality was recently named the "Mobile Disruptor of the Year" for 2017 by Mobile Marketer, but the technology is showing no signs of slowing down as we head into 2018. In fact, the technology appears to be gaining momentum.

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

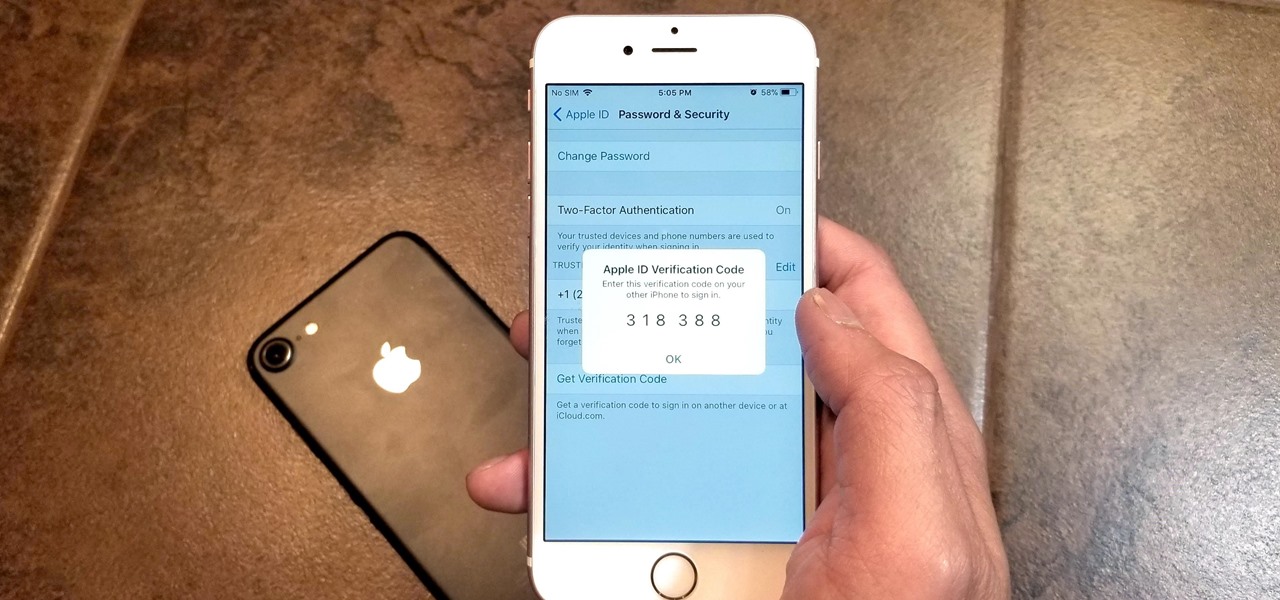
Two-factor authentication has been around since iOS 10. It's a handy option that adds an extra layer of security to your iPhone and makes its almost impenetrable security even stronger. This feature has remained intact in iOS 11 and iOS 12, and thanks to the straightforward nature of iOS, is relatively easy to enable.

For as long as 14,000 years, the First Nations people of the Heitsuk Nation have made their home along the Central Coast of the Canadian province of British Columbia. Among the territory's inlets, islands, rivers, and valleys lie a clay deposit on the north side of Kisameet Bay, near King Island. For as long as most can remember, the tribe has used the clay as medicine. Now science says microbes that live in that clay may have important antibacterial properties.

Crusty, itchy, red eyes? There is a decent chance you could have conjunctivitis, or pink eye, an infection of the thin lining around the eye and the eyelid, caused by bacteria, an allergen, virus, or even your contact lenses. Whatever the cause — you call up your doctor to get a prescription to clear it up, right? Not really.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.

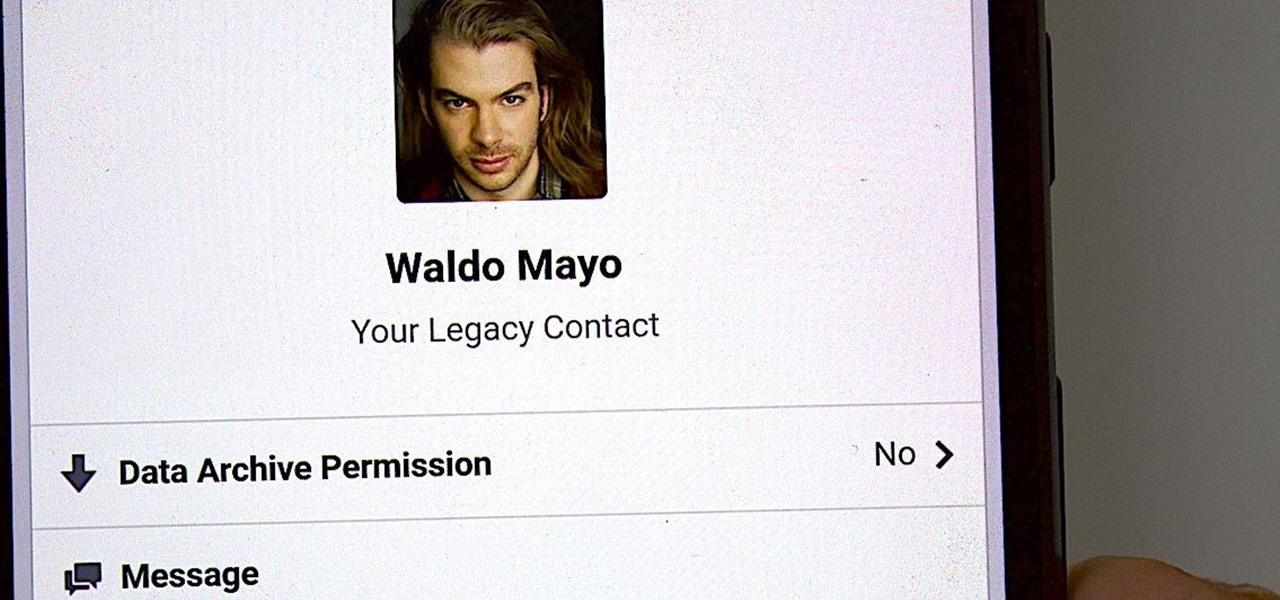
It's time to set your Facebook "Last Will and Testament" straight. Do you want to assign a contact to look over your account, or would you prefer to have all your online memories fade away the minute you die? It's a tough decision, but with a little time, you can set up at least one of these options to ensure that your account isn't left to sit pretty without you for the rest of time.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Dutch filmmaker Anthony Van der Meer published his 2015 thesis short from Willem de Kooning Academy in South Holland online in December 2016. It's a brilliant piece of work that managed to be touching, alarming, and informative at the same time. His documentary, which already has over 6 million views on YouTube, covered the journey made by a stolen smartphone and how the theft and ensuing tracking affected all parties involved.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

Among the many changes in Android 7.0 Nougat, a less talked-about feature may very well be one of the most interesting. As part of a new system-wide API, apps can now create their own Quick Settings tiles, and it doesn't require any complicated workarounds like it has in versions past.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

If you want free Poké Balls and eggs when playing Pokémon GO, you can find them at PokéStops in variation locations around your city, which are marked with towering blue icons on your map. Once you're at Level 5, they'll also grant you Potions and Revives to help you in your battles against other trainers, so they're definitely something you should be visiting whenever you can.

We like to think of ourselves as caprese connoisseurs. When we made our first batch of the iconic tomato salad, we became obsessed with the classic combo of fresh basil, sweet tomatoes, and creamy mozzarella cheese. But after a while, we wanted more than just the basic, layered Italian summer staple.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

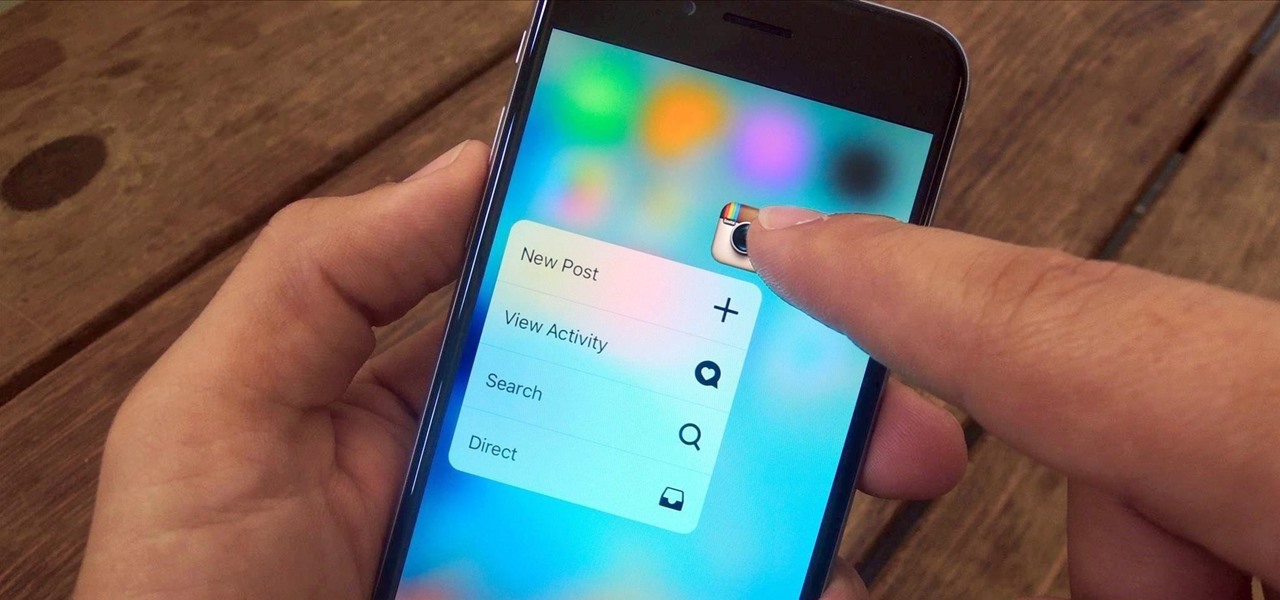
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.
Hello and Welcome back to another How-To on the Xbox Community Ambassadors World! In this How-To, I am going to tell you and kinda show you how to deal with or avoid angry Xbox Customers.

Modern medicine utilizes cutting-edge technology more than ever, so it would only make sense that the powerful handheld computers we all carry around these days could play a big role in wellness.