Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.
If you are not interested about the huge amount of messages contain app and playing game invitation in Facebook, then you could stop those messages from coming to your end. This video shows how to block friends from sending apps and game requests o

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.
In the changes to the App Store Review Guidelines for iOS 11, Apple has announced that developers must use the App Store rating API. The API was introduced in the iOS 10.3 beta period as something that would eventually become mandatory. Now, Apple has followed through on that promise.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.
For parents that have an iPhone X, things are about to get a lot easier for you in iOS 11.3, which finally lets you approve app and media downloads on your child's iPhone using Face ID instead of typing in a password.

The iOS 14.4 developer beta was pushed out a day ago, and now the iOS 14.4 public beta is out and ready for your iPhone. At first glance, there's not much to look at in the new beta release, and it's not yet known if it lays out the groundwork for missing features such as 5G data with dual SIMs, shared third-party app subscriptions, and Xbox Core Controller.

The next big phase of iOS 14 has started with the release of the iOS 14.4 beta. Right now, the developer-only beta features only one known item. Apple introduced the ability to scan App Clip Codes in iOS 14.3 with the Code Scanner control, and now in iOS 14.4, you can launch a local App Clip experience via Camera, NFC, Safari Smart App Banner, or iMessage.

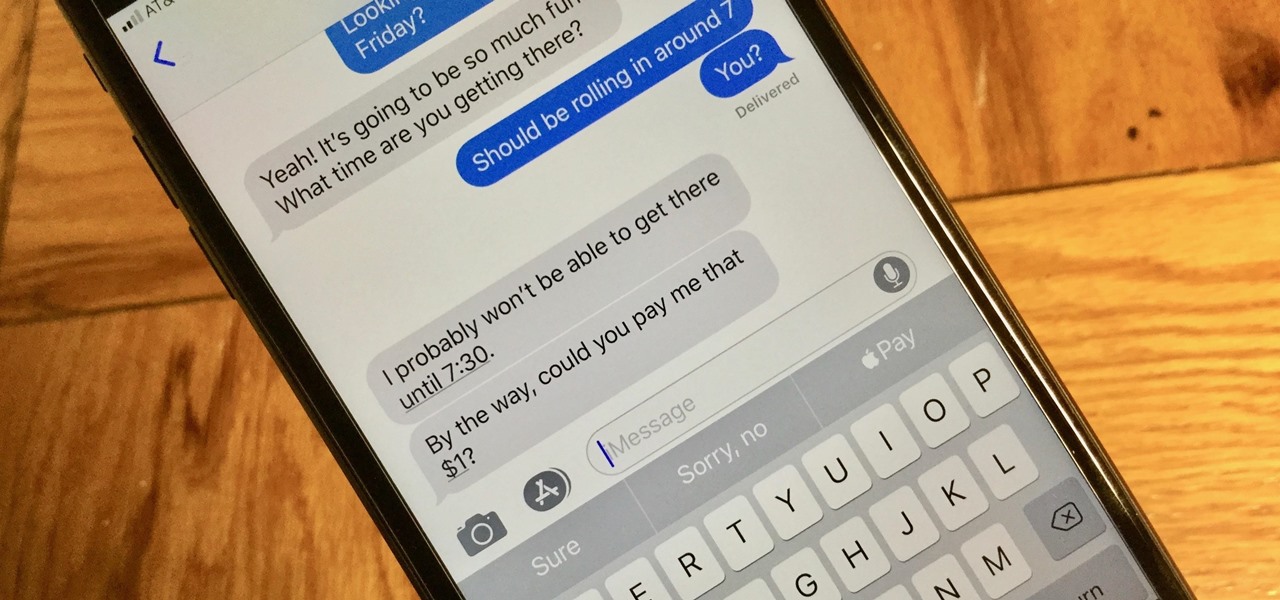
With Apple Pay Cash, you can easily and securely pay your contacts directly in your iPhone's Messages app. While you can always use the normal method of paying someone with Apple Pay Cash, there's actually a faster way, as long as your contact asks you for money in an iMessage.

Brace yourselves, because Siri has a trick up its sleeve that iPhone users have wanted for some time. Yep, that's right, I'm talking about the ability to use Siri without having to talk out loud for the whole world to hear. It's great for privacy, Siri-ing on the down-low when you're not supposed to, or ... you know ... if you have a speech disorder.

You may not always want to, but there will probably be a time when you'll want to know if an email you send — like a job application or a support request — is opened by the recipient. It's actually easy to implement, and you may be using an email client on your device right now that supports email tracking.

In this clip, you'll learn how to make HTTP requests with Silverlight's HttpWebRequest class. when working in Silverlight. Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

Don't want to see the nine millionth request to join Farmville? Tired of some people sending you stuff on Facebook? Stop the madness with this video! Go to the requests at the top page, right side of the site. Click the requester you received then you can see the options below. Block this application and ignore all invites from this friend. Then click the ignore button if you want to ignore that requester.

Auto accept facebook requests and gift back to your friends! In this tutorial, I'll show you how you can auto accept Facebook requests and gift back to your friends. If you're like me and get hundreds of Facebook requests each day - this will be a life saver. You'll be able to focus on playing the Facebook games - and let GiftAuto handle the rest.

Cool world. Check it out and post your ideas to the forum.

Here is a list of links you can use to ask for or give special gifts. First you need to find your Facebook ID number and copy it down somewhere, or memorize it if you can, then paste it into the links replacing the ###### symbols.

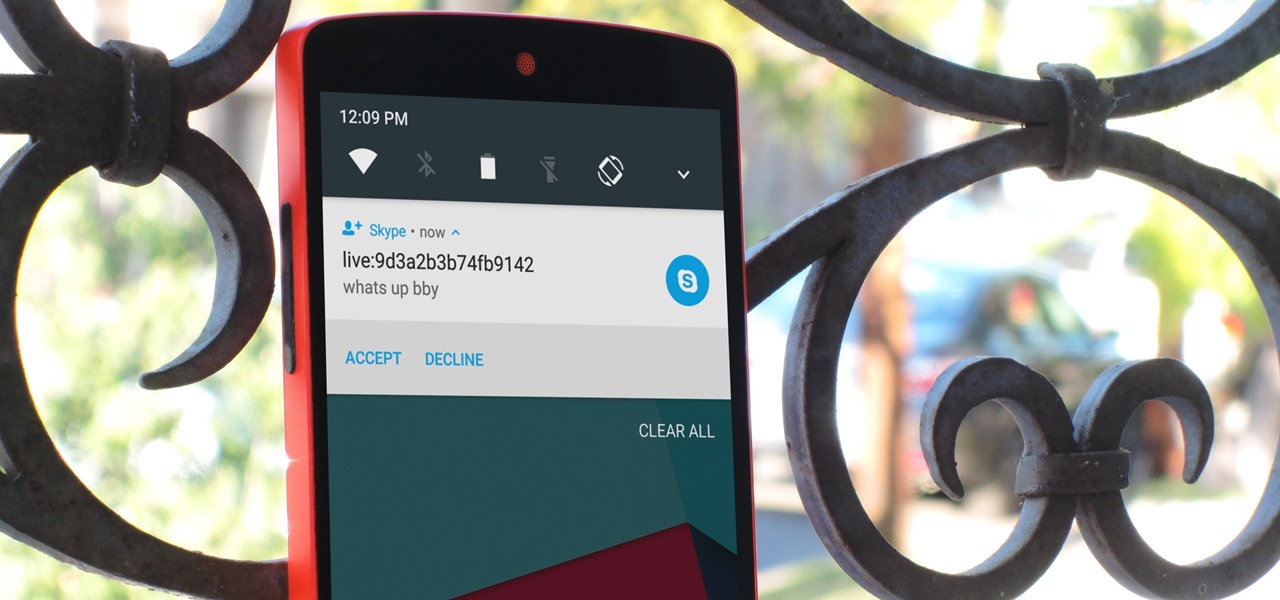
Skype is one of the most popular messaging and video chat services for a good reason—it's packed to the brim with tons of cool features. But one bit of functionality that Microsoft left out is the ability to block friend requests from people that aren't in your contacts, which can lead to a lot of unwanted notifications from spammers and bots.

In the latest update to the ongoing Meta Company patent infringement case, the court has responded to a request from the defendants, and the answer isn't good news.

Michael Jackson appears to be more popular know than he ever was, which always seems to be the case with fallen pop icons. Not just his music either… we're talking about art. Since MJ's death, more and more artists are looking for ways to create their version of musical master, and you can draw him, too. With the help of this step-by-step drawing tutorial, you can have your own Michael Jackson masterpiece.

Maybe you're tired of receiving annoying messages from apps or people on Facebook? Why not block them so you don't have to deal with them ever again? Take a look at this guide for information on how to block online games and apps on Facebook from sending you notifications, requests, or other information. You can even stop people on Facebook from sending you event notifications or posting on your page by blocking them too.

Embed Facebook directly into your Internet Explorer or Mozilla Firefox browser's toolbar using this nifty new add-on directly from the people at Facebook themselves. This addon shows you on the toolbar the number of pokes, friend requests, unread messages and upcoming events that you have, in addition to quick links to various sections of the Facebook site. In this demo video, Patrick from Tekzilla explains the cool new features and details.

A cranberry glaze can be used to make your turkey look scrumptously sexy and polished to a Midas glow. The glaze also adds succulent tart flavor to the richness and density of your turkey meat.

If there is one hairstyle we all remember the late and great Farrah Fawcett by, it's her feathery, winged back '70s hair from "Charlie's Angels." The sexy style has had celebrity imitations up to this day and is frequently seen on Carmen Electra and Cameron Diaz. For some, this will always be Farrah Fawcett hair.

Celebrities look amazing in photos, on the red carpet, and really just in general, but they can attribute their awesome beauty to more than just their heavenly descent to earth.

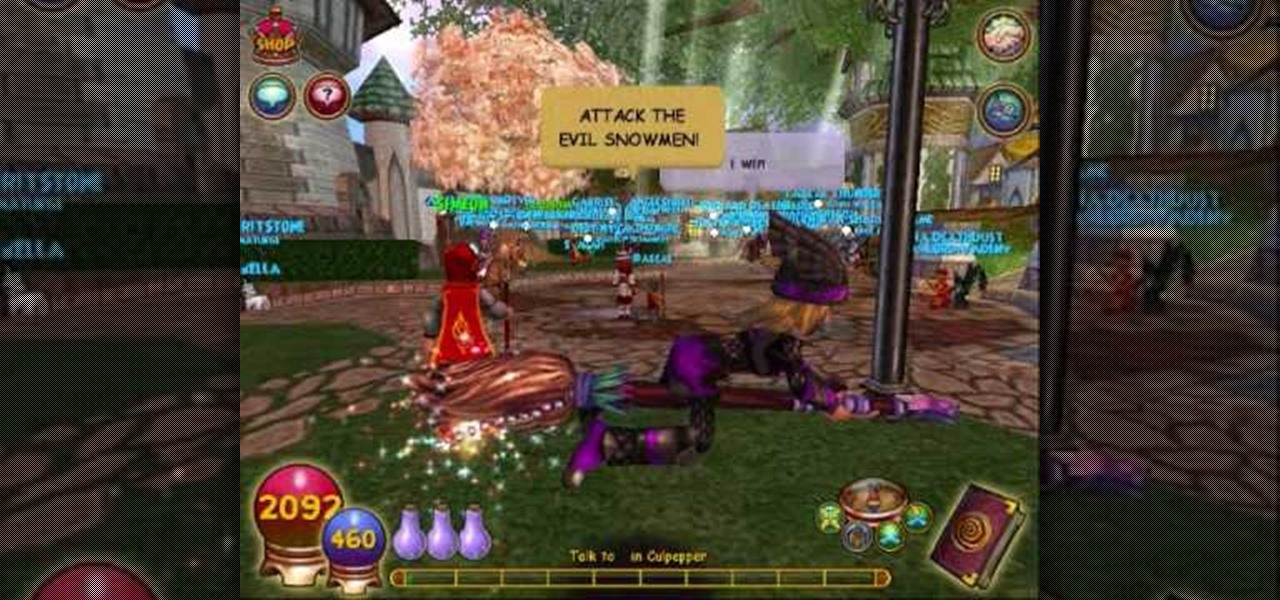
The Wizard101 Test Realm. You can play in it, but beware of scammers, beggars, and spammers! There's nothing worse than getting bombarded with these annoying requests.

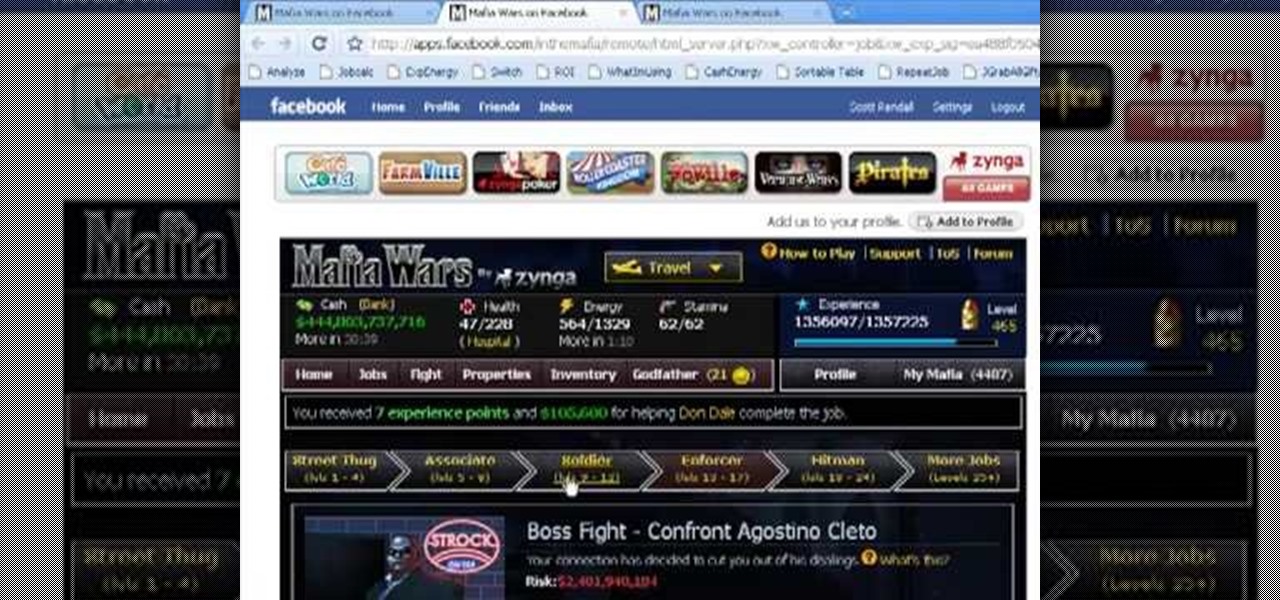
Hack Mafia Wars. Mafia Wars hacks, glitches, cheats. Mafia Wars is a popular facebook app / game. Watch this video tutorial to learn how to easily manage your Mafia Wars player updates.

Twilight, that steamy, dreamy love story between teen Bella and heartthrob vampire, Edward Cullen. This love story is based on a series of vampire novels (Twilight, New Moon, Eclipse, and Breaking Dawn) by Stephenie Meyer. True love, handsome boy, and vampire danger = perfect teen love story. Who's your favorite Twilight character? This makeup tutorial demonstrates how to create Bella Swan's makeup, based on the actress Kristin Stewart in the Twilight movie.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Even if you've received hundreds of requests for letters of recommendation (college professor? We thought so), every letter of recommendation should be personal and well thought-out.

In this video, we learn how to speak Spanish: Subjunctive with verbs of volition. Volition is requests when someone asks, needs, or wants something. To form these, you must first take the "yo" form and remove the final "o". Then, you will add in the opposite vowel endings. For example, with "yo hablo" you would say, "yo hable" or "hables". This will change if you are talking about a group of people, one person, or a formal group of people. A verb with the "er" ending will change to "a" or "es...

In this tutorial, we learn how to speak English: Imperatives or reporting verbs. Imperative sentences are sentences like "open it!", where you are asking someone to perform an action. You can also say this in a nice fashion, asking "please open it". There are many different forms of imperative sentences, which include: commands/orders, directions, instructions, requests, and warnings. All of these different types of sentences are asking someone to do something, just changing up the way they d...

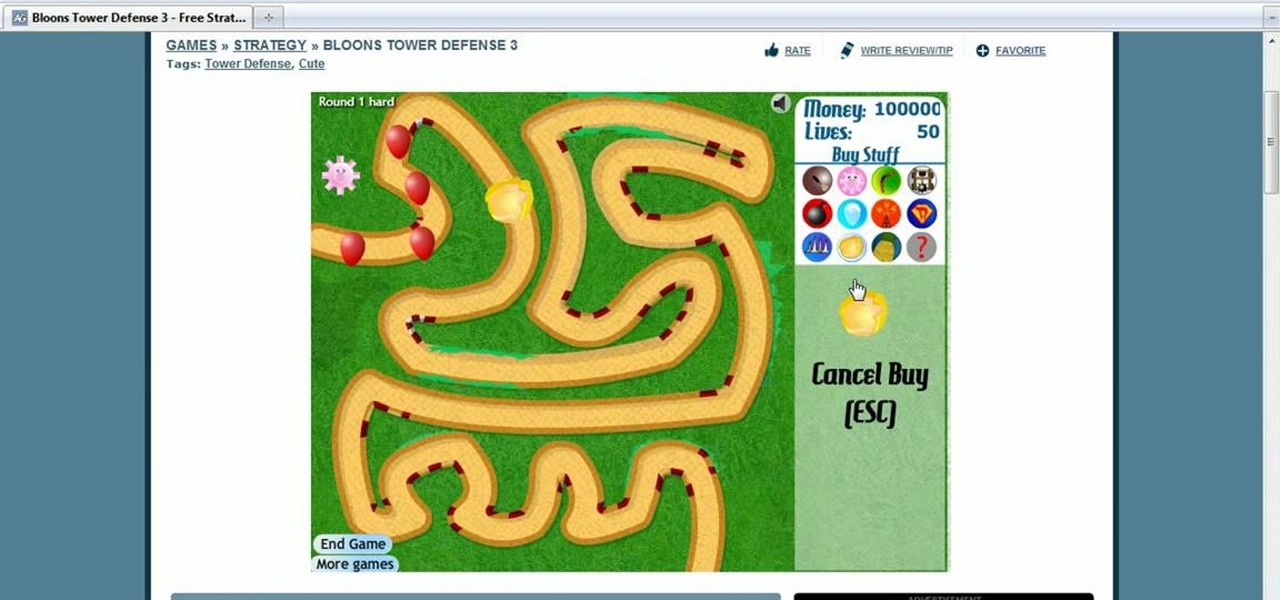
Bloons Tower Defense 3 is a flash game from Ninja Kiwi. Learn how to hack Bloons Tower Defense 3 with tricks and cheats. Watch this video tutorial to learn how to hack Bloons Tower Defense 3: unlimited money (09/24/09). Get unlimited money! You just need Cheat Engine 5.5.

This video shows how to change the advanced settings to make Firefox faster on Mac and PC.

Krazyboytx shows viewers how to make self-igniting spell incense! First you need an incense burner and place your incense in this. You then light this mound and it will ignite itself. One should note that this soap is very thick but it will light. First, to make this incense you need to base which is just sawdust. Next, you can add mugwart in this, or whatever choice you would like to add. Next, you should add in some potassium nitrate or a common name for this is 'peter salt'. For a stronger...

Do you want more money in My Pet Protector? Of course you do. Well, the fastest and easiest way to get more cash on My Pet Protector is to hack the game, and to hack the game you will need to use Cheat Engine.

While some of our group chats should probably remain private and closed off, others will only get better with more people. Whether you're organizing an event and need a headcount or you want to share a funny YouTube video with a large crowd, you can add all the friends you wish to on Facebook Messenger by sending them a unique link.

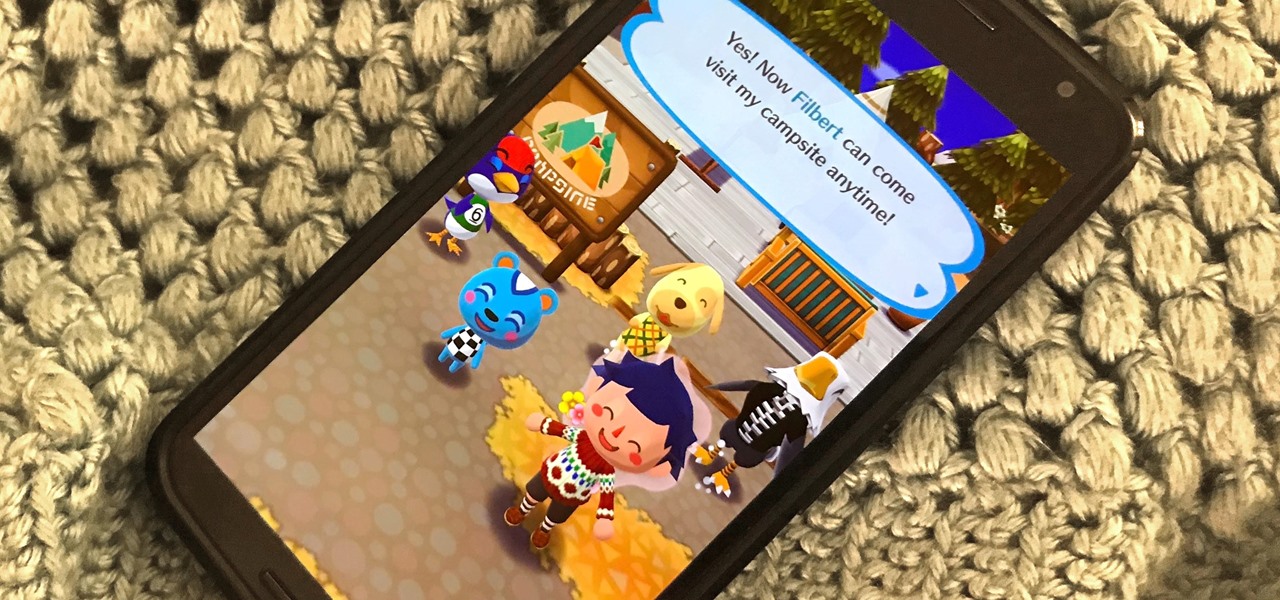
Friendship has always been a staple of Animal Crossing games, and Animal Crossing: Pocket Camp makes no exceptions. Check out this guide if you're interested in how to maximize time with your furry friends.

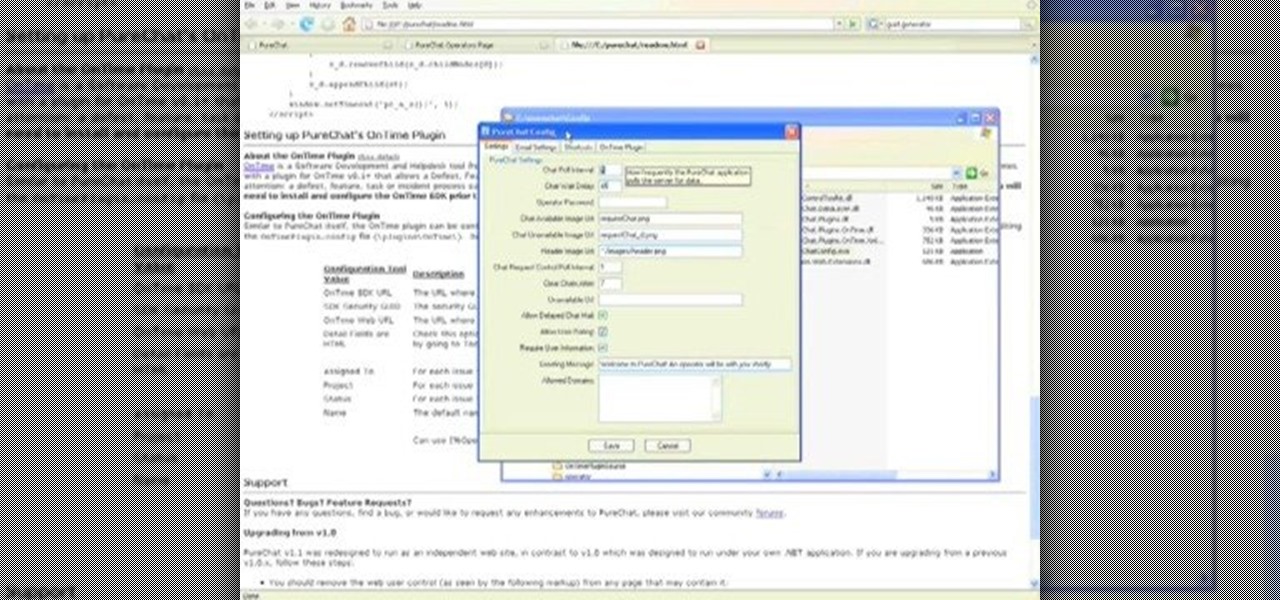
PureChat 2008 ships with an OnTime plug-in that allows you to quickly turn live web chat conversations into defects, feature requests, incidents or tasks in OnTime -- with just a few mouse clicks!