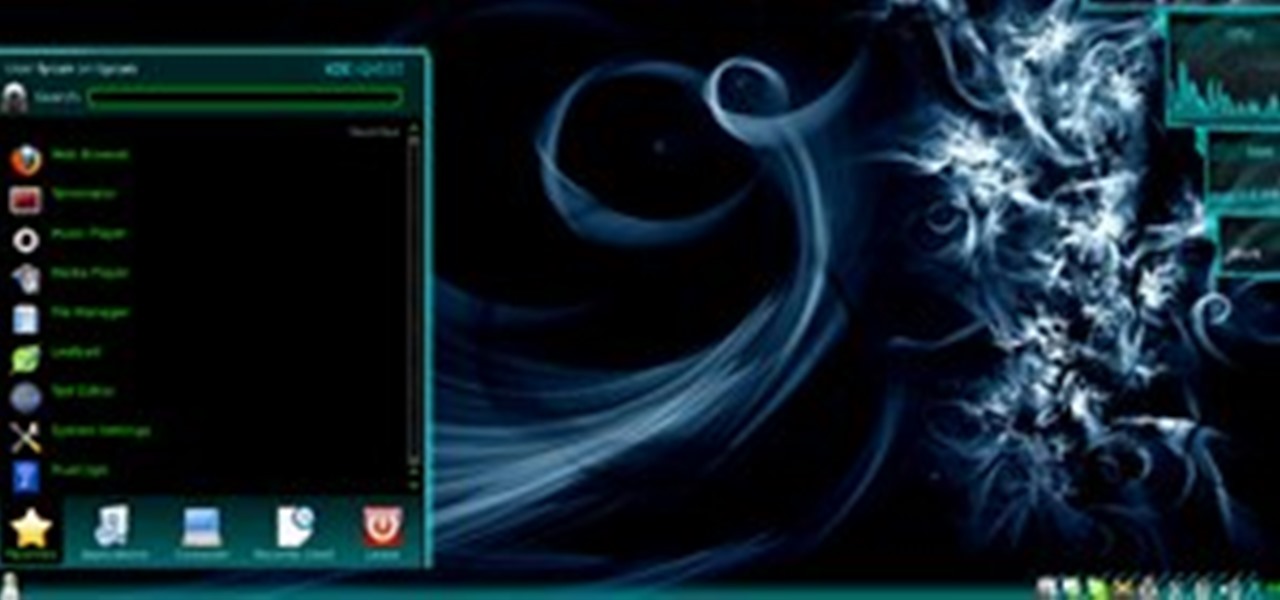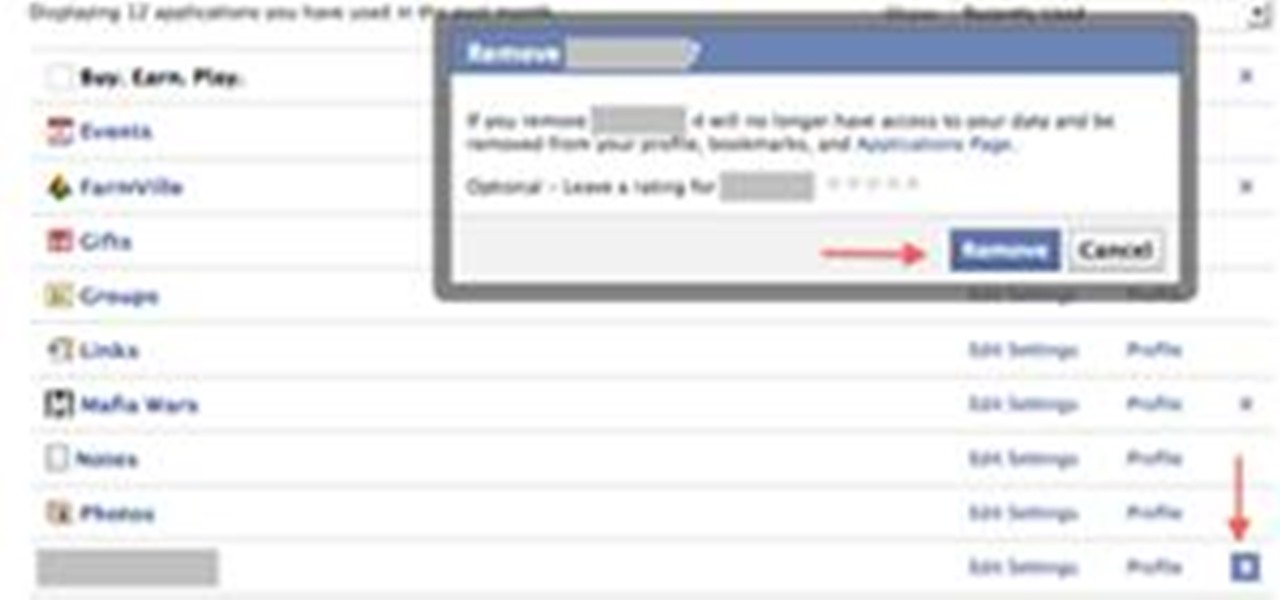
Please share this info with all your facebook friends. It's not just Farmville players that are affected by scams and spam! This post will help you keep your facebook account clean and safe. We start by showing you a scam and discussing what is real, then we show you how to remove pages you don't want, and finally how to remove apps you're not using. Please scroll down to which ever part you need!

Here ya go... Folsom Prison Blues! Have had so many requests for this one. Now tune in and learn this well loved song introduced by "The Man in Black"! You will be able to play in a few short hours by watching this easy to follow tutorial vid. I have taught 1000's of students from around the World. My lessons are now available to you for FREE. Go to my site and learn over 170 of the most sought after, popular songs. Also check out: http://www.youtube.com/user/erichandreas

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

What happened to please and thank you? When did asking someone to come look at your build degenerate into COME NOW or FOLLOW or sending out teleport requests to any and all currently on the server without asking?

In this article I'll show you how to make a simple IP address notifier. The program will text you your new IP address, in the event that it changes. For those of you with dynamic IPs, this is very useful. I'm constantly frustrated when my IP changes, and it's handy to be notified via text when it happens. To use the program, you'll need Python 2.7 or later, urllib2, and a program called "text" (see this article here to get it).

Linux can have the most beautiful interface in the world, because it is simply what you make of it. You can change every little detail with relative ease because that's what Linux is all about: Freedom and OpenSource.

Web-spying technologies like FaceNiff, Firesheep and Newstweek are out there showing the world just how easy it is to see what you're doing online, but they're amateurish in comparison to what real hackers could do to you if they catch you browsing unsecured websites.

So you just bought Photoshop, a DSLR camera and your first flash. Now what? If you have some experience with photography, but you're not completely fluent with the software and equipment, WonderHowTo's newly featured World Lights! Camera! Photoshop! is essential.

Android users are probably already familiar with the doubleTwist Player (free) from doubleTwist, available on the Android Market. They recently added AirPlay support for users with AirSync ($4.99) that allows streaming to Apple TV and DLNA devices, which is sure to provoke some cease and desist requests from Apple. But their second, newly unveiled feature is more enticing—doubleTap, which adds proximity-based file sharing for Android devices.

For travelers on-the-go, or penny pinchers who like to surf the web for free in public places, there are necessary precautions one must take when accessing sensitive information over a public WiFi connection. For advice on doing this safely, check out Glenn Fleishmann'sguide to staying protecting your private information. Fleishmann outlines how to:

Black Roses are here! These are the first of Limited Edition giftable seeds that you can master! This was announced in the last podcast.

Over the past few months I've written up several helpful How-To guides to help you with various FarmVille related issues. It's about time I put them all in one place so they are easy to find, learn from and share! It has been a pleasure writing for you all and I do hope I have helped you find ways to meet your personal gaming goals!

From LAist: As Los Angeles law stands today, you can only own and register up to three cats and/or dogs. More than that would require a resident to qualify for a kennel permit. Now a motion to increase that number to five is gaining traction on both sides of the issue, finds the Daily News.

In the past you may have blocked wall posts so you wouldn't get fuel, goods, and other random things from your applications. But you may wish to rethink this, at least for a while as the new truffle hunting feature requires wall posts.

More Storage is here for all! It takes up less space than a plot and once you expand it to 500, you can get rid of your other barns if need be and it will hold all 500 items on its own!
I'm having a hard time finding my older posts, so I'm sure you are too. I'll put them all here so you can find them easily. You can bookmark this if you want :)

I've created this guide to give you some ideas for how to progress quickly as well as some basics for how to operate FrontierVille. My tips are merely suggestions based on my experience and you are welcome to explore and play the game at your own pace. I hope you benefit from my posts and look forward to answering questions and bringing you more useful information here and on the Facebook page in the future! (All these blue links take you to more content just like this page, click them for mo...

How many Facebook friends do you have? The average person on Facebook has around 140 friends while some hit the ridiculous Facebook friend limit of 5,000. Facebook states that its services are for people you know in person. I don't think anyone has 5,000 friends in person, do you? Personally, I don't even think Megan Fox has 5,000 friends in person, so how could any regular person have that many? But that's beside the point.

I can't believe it, but I've actually read about dozens of people getting their iTouch, iPhone, or iPad stuck in a bricked recovery loop and then going out to buy a new one. This is overly unnecessary. When it gets stuck in the recovery loop, some people mistake themselves by thinking that it is impossible to get the device back into DFU (Device Firmware Upgrade) mode. Getting the device back into DFU mode would at least allow us to jailbreak the device, essentially bringing it back from its ...

There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and advanced alarms, obviously, but not for the reasons people normally think.

Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen.

Our first Community Byte went well! We had around 8 people in the room coding collaboratively and watching to learn. LukeStav did the kind task of hosting it on Gobby for all of us, so big thanks to him!

Welcome to part two in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

This week, we saw the implementation of collapsed comments, Google+ games were rolled out to everyone, and yesterday, there were several more announcements of enhanced features and tweaks.
On Thursday, March 9, there was a news story on the evening news about Khan Academy (NBC News). The story began when Sal Khan started tutoring his cousin in 2004. Since he was in Boston and she was in a different city, he decided to make and post videos on YouTube so anyone could watch the videos. Later he added videos for her brothers and for people that contacted him with requests for other videos. During this time Sal had a job that he later replaced with another job. Today Sal has 2010 vi...

It's only been a few weeks, and already there are a lot of misconceptions and myths floating around Google+. Let's take a deep breath, and tackle some of the more prominent ones.

+Tom Anderson of MySpace has been very active on Google+ over the first week, and he's not shy with his thoughts on the evolution of the industry he once owned. Here's his take on this morning's Facebook announcement and Mark Zuckerberg's response when asked about Google+.

Attention all National SCRABBLE Association members: You know that newsletter that you get in your mailbox every month or two? That SCRABBLE News mailing from the NSA? Well, they're axing it. No more printed SCRABBLE News. No more ink on your fingertips. No more surprises in your mailbox. It's done for... kinda...

Warnings Warning! These links are not all approved by Zynga. You use them at your own risk!

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

For a moment, picture a situation where you want to host some files or images, but you do not want it traced back to you. Perhaps you're working on a project with others and need secure data storage. Anonymity is the new shield of the 21st century—and you best protect yourself. As always here at Null Byte, we are trying to make that happen. Before someone can learn how to root a box, they need to learn how not to be found. I can not stress that point enough.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

Last week's round up was all about third party services that sprang up to fill any Google+ voids. This week, I'll let you know how to keep up with the latest Google+ updates, and give you some great tips for interacting with your followers.

So the fiance and I cannot imagine spending upwards of $500 on a DJ for our wedding when we have tons of perfectly good music on our computers. And the cross-fade feature... Genius!

Welcome everyone Today i will show you a simple but very useful way to stop your ip leaks . In order to stay anonymous on the web you HAVE to do this.

BeEF is an XSS-exploiting framework that lets you "hook" or gain control of victim web browsers. In this part of XSS exploitation, we will be working on finding an XSS-vulnerable website. We can simply do this by Google Dorking.