A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

It may sound irrational, but I bet a lot of you actually avoid doing any work at work—but not on purpose. You might be simply struggling with motivation, or you might just be overdosing on the caffeine. Whatever the issue, getting focused takes lots of time and effort.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Apple released the first public beta for iOS 14.3 today, Friday, Nov. 13. The update includes ProRAW support for iPhone 12 and 12 Pro, upgrades to air quality in Weather, support for the PS5 controller, among other new features and changes.

Apple released the first developer beta for iOS 14.3 on Thursday, Nov. 12, only to pull the update back, push it back out, and finally release it for real. An afternoon marred by Apple server issues spanning macOS Big Sur downloads to iMessage and Apple Pay could have been part of the issue. The new update for iPhone adds ProRAW support for iPhone 12 Pro and iPhone 12 Pro Max.

Google's been on a mission to improve the privacy and security of Android lately, and Samsung's always been at the forefront in these areas. As a result, One UI 3.0, which is based on Android 11, is the most secure OS version to ever hit Galaxy phones thanks to few key changes and new features.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

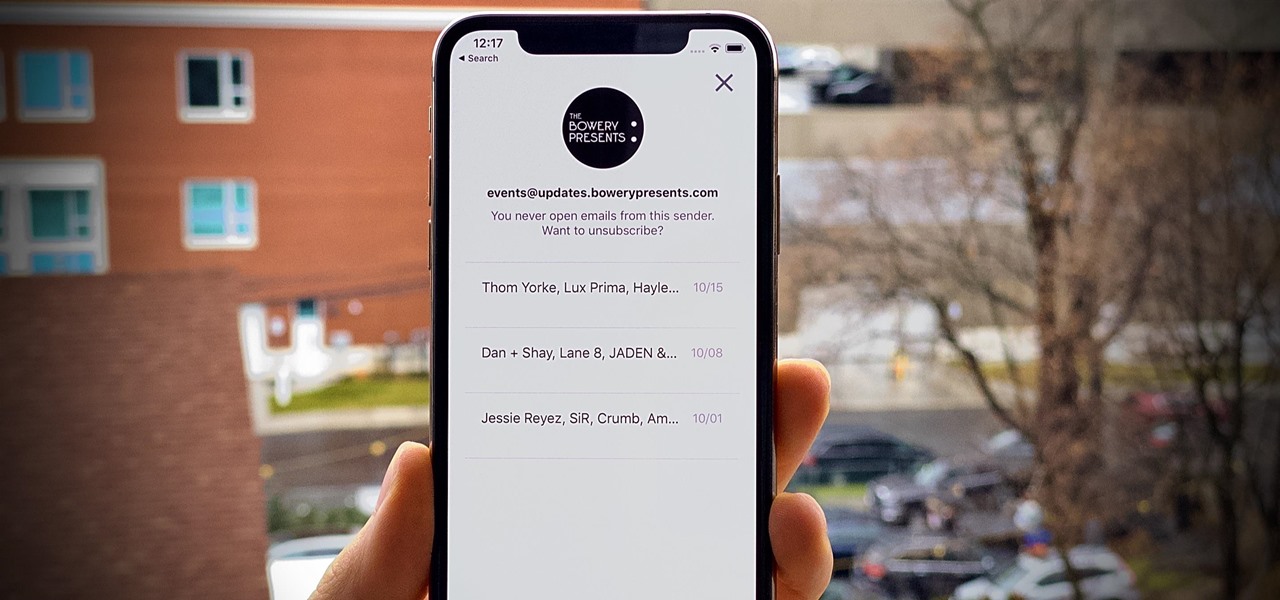
Edison Mail's big 1.17.0 (iOS) and 1.12.0 (Android) updates introduce a new, powerful Assistant to the mix. Aside from the fresh calendar integration and extensive customizability, you'll probably be most interested in the Assistant's unsubscribe feature. It helps to locate and cut down on your inbox's ever-growing jungle of spam. Here's how it works.

At least one hurdle to China-based augmented reality startup Nreal going mainstream in the United States may be about to be knocked down, thanks to behind the scenes legal movements Next Reality has uncovered.

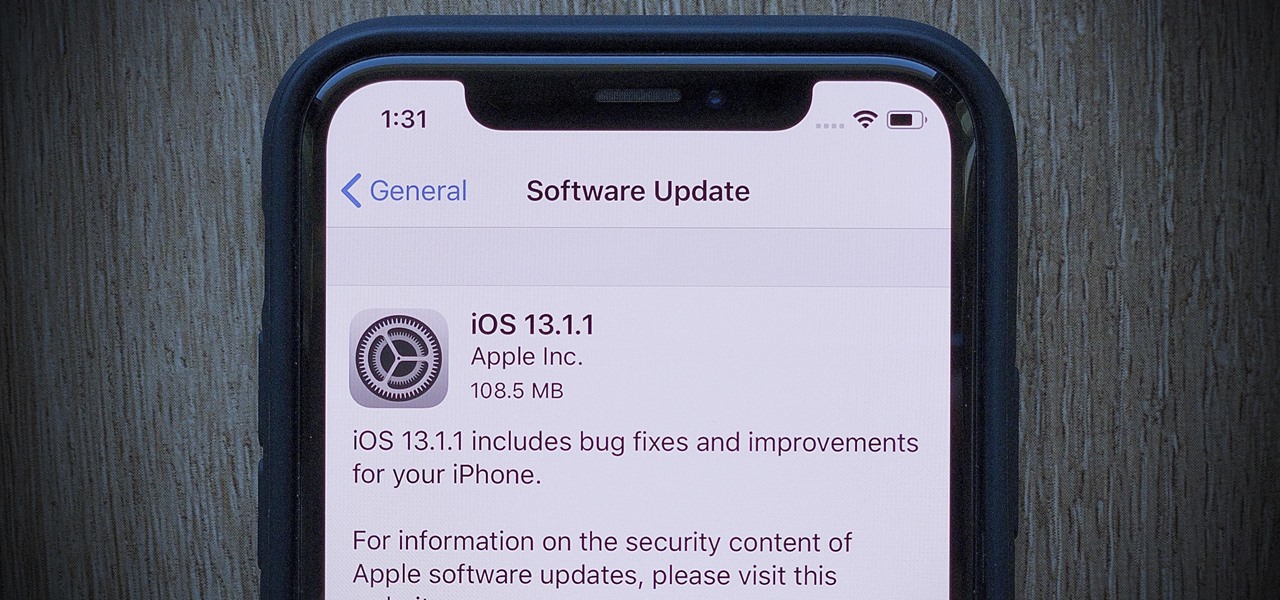
Is Apple trying to set a record for the highest number of updates within a two-week period? You wouldn't be blamed for thinking so. Just eight days ago, Apple publicly released iOS 13.0 for all compatible iPhones. Then, just five days later, Apple seeded iOS 13.1 with 22 new features to boot. Now, just three days into 13.1's tenure, Apple has released yet another update, iOS 13.1.1.

The legal drama framing the closure of Meta Company continues even after the company's assets have been sold to a new owner.

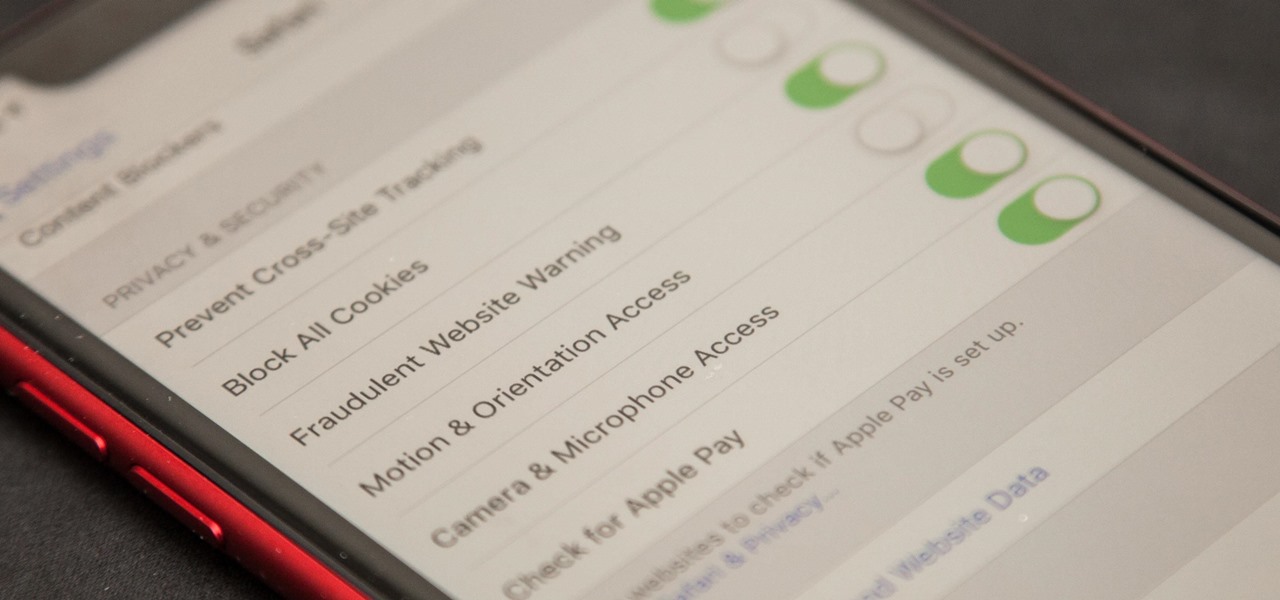
Apple first added the "Do Not Track" option to Safari in iOS 7, which sent a request to site owners and advertisers to not track your browsing activity. By tracking your activity, those third-parties could tailor content to you that you're more likely to interact with. While the feature was always opt-in, it's no longer a feature at all in iOS 12.2 on your iPhone.

In recent days, I've twice talked about brining the Magic Leap One out into the world with me to test its mobile capabilities. But you may have been wondering how I carried the device with me. Did I just stuff my brand new $2,300, hard to obtain device in a backpack and hit the road? Hardly.

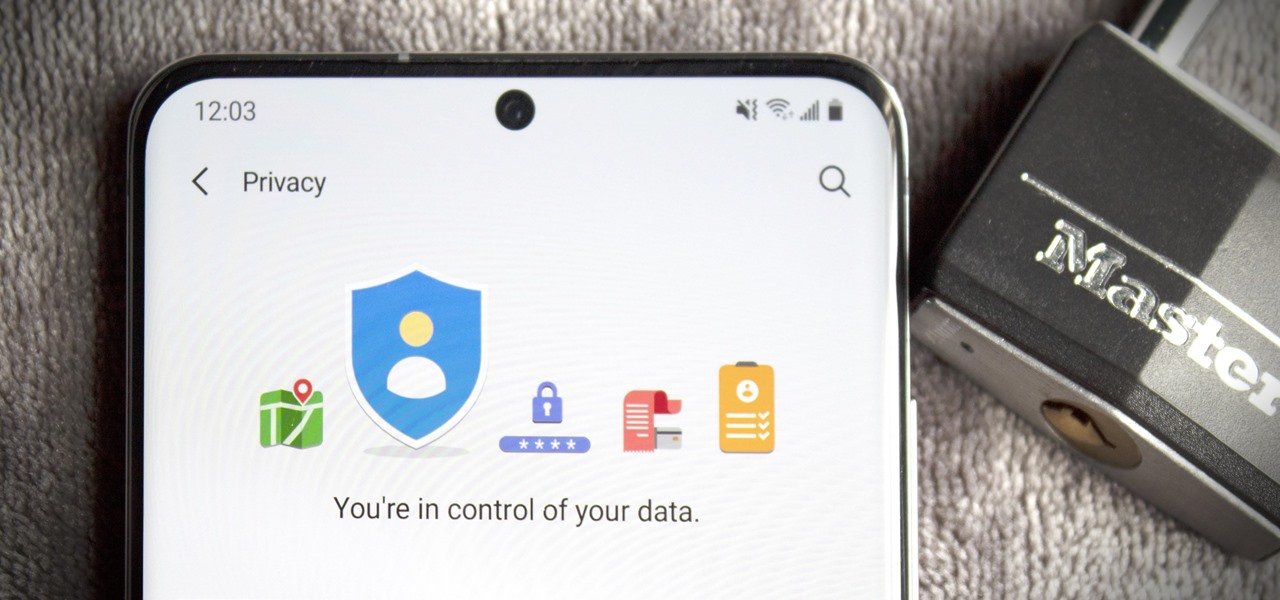
There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

If you have some experience in the Google world, you'll know that Google Assistant has had location-based reminders since it dropped nearly two years ago. Before that, Google Now offered the same feature. Even with that precedent, you've never been able to ask Google Home to remind you to, say, pick up eggs when you reach the grocery store. That is, until now.

After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.

Avegant Corporation has begun shipping display development kits based on its light field technology that other companies can use in their augmented and mixed reality devices.

Apple recently scored a patent (number 9,488,488) to create augmented reality maps, hinting at possible AR integration into the iOS Maps application for iPhone. Does this mean we'll be seeing super visionary projections of places in the app in the near future? Maybe.

Want to actually catch 'em all? Pokémon GO has long-teased the opportunity to hunt for Pokémon in the real world through augmented reality, but few have had the opportunity to actually see it in action.

!!!WARNING!!! !!!Because of misleading informations please wait for the new post about this same argument instead of reading this post!!!

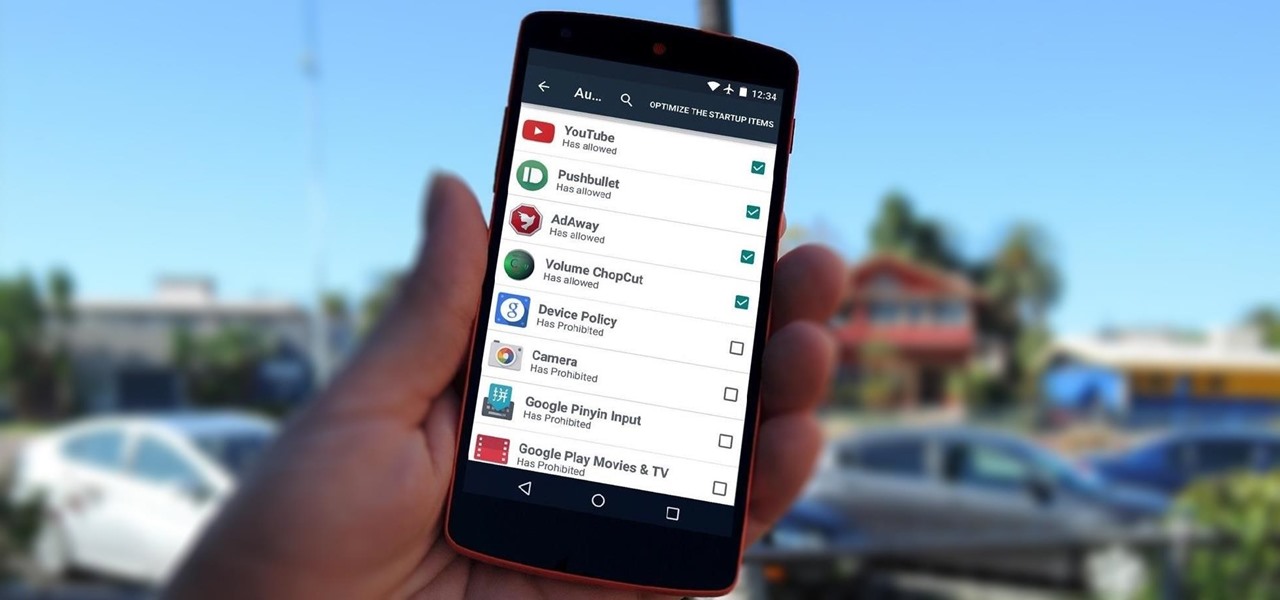
By default, any app that requests a certain permission can run automatically as soon as you start your device. Since Android doesn't offer a granular permission control system like iOS, this gets lumped in with all of the other permissions that you have to accept when you're installing an app from the Google Play Store, and you effectively have no choice in the matter.

OnePlus One's CyanogenMod firmware comes packed with personalization options that standard Android devices could only achieve with root-level access. By simply entering the Settings app, OPO owners can make changes to their lock screen, status bar, and notification drawer, as well as apply themes and gestures to make their device a little more customized.

While the majority of photos taken on phones are used for personal reasons, mediums like Instagram and Flickr offer a means to show them off to the world. But those pictures of your brunch or beach day can actually go beyond that to make you some money.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

Change is something everyone needs every now and then. President Obama used it as his campaign slogan and adult movie stars use it to hide their real identifies. Change is in itself versatile. You never want to have the same thing day in and day out, and that's why us Android users appreciate the massive amount of customization available.

With iOS 7, Apple is finally fighting back against spam, offering the option to block certain phone numbers from sending you text messages or iMessages (plus, phone calls and FaceTime too).

Most of the time, asking to borrow someone's car will elicit a really long string of excuses. But unlike letting your buddy use your car, which usually gets you nothing more than an empty tank, GM has found a way to make car sharing beneficial for everyone involved. If you're one of the 6 million people who have a GM vehicle that's connected to OnStar, you're in luck: according to an OnStar employee, you can make up to $1,000 a month just by letting other people rent out your car when you're ...

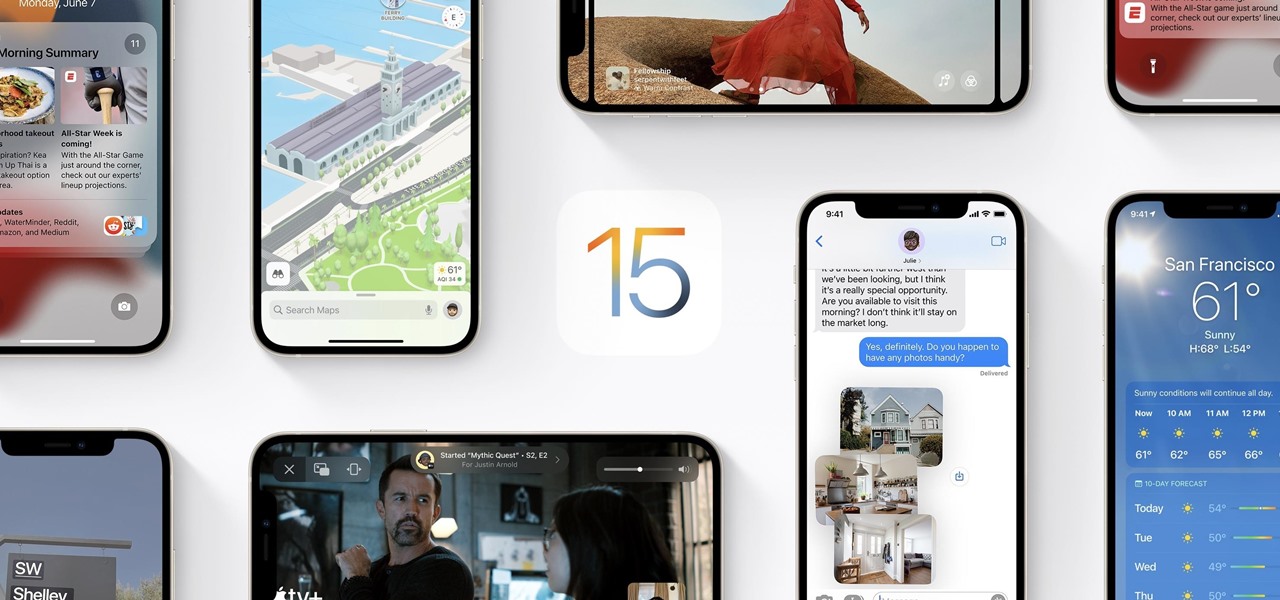
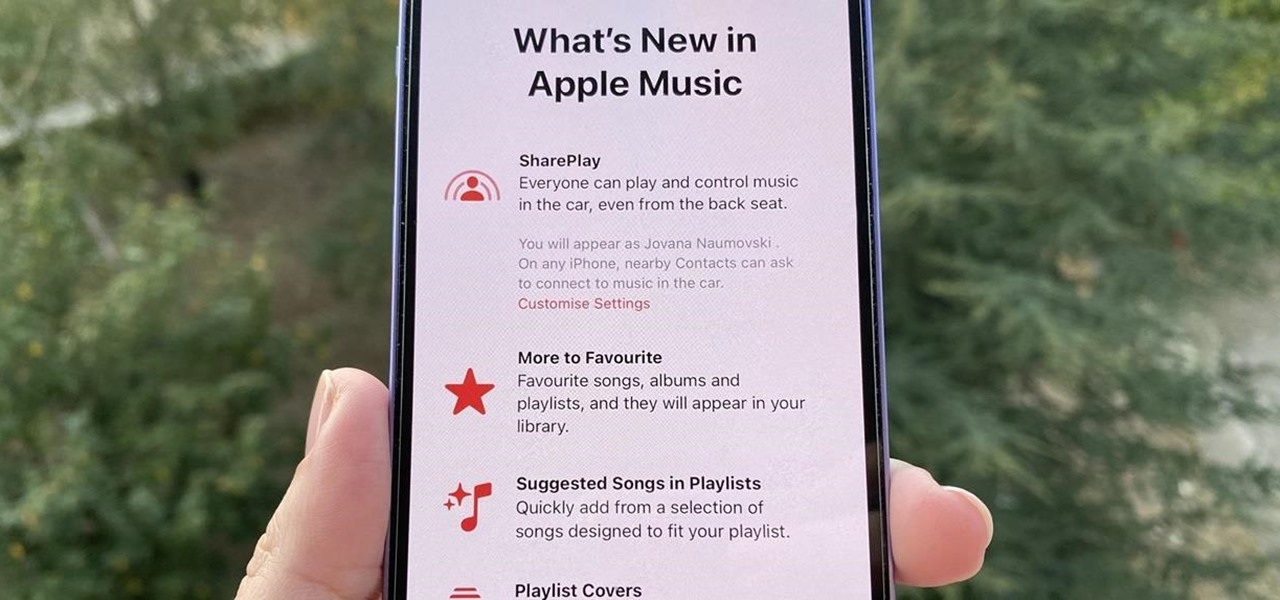
Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

You see the status bar nearly everywhere on your iPhone, and it almost always looks the same. But you can use a few tricks to spice things up a bit — without jailbreaking your iPhone.

In case you missed it, Apple has added a lot of new features and enhancements to the Music app on your iPhone, changes that benefit both Apple Music subscribers and non-subscribers. Chances are, you haven't seen all the changes yet, especially since many of them weren't released when iOS 17 first came out, but we'll go over them all with you.