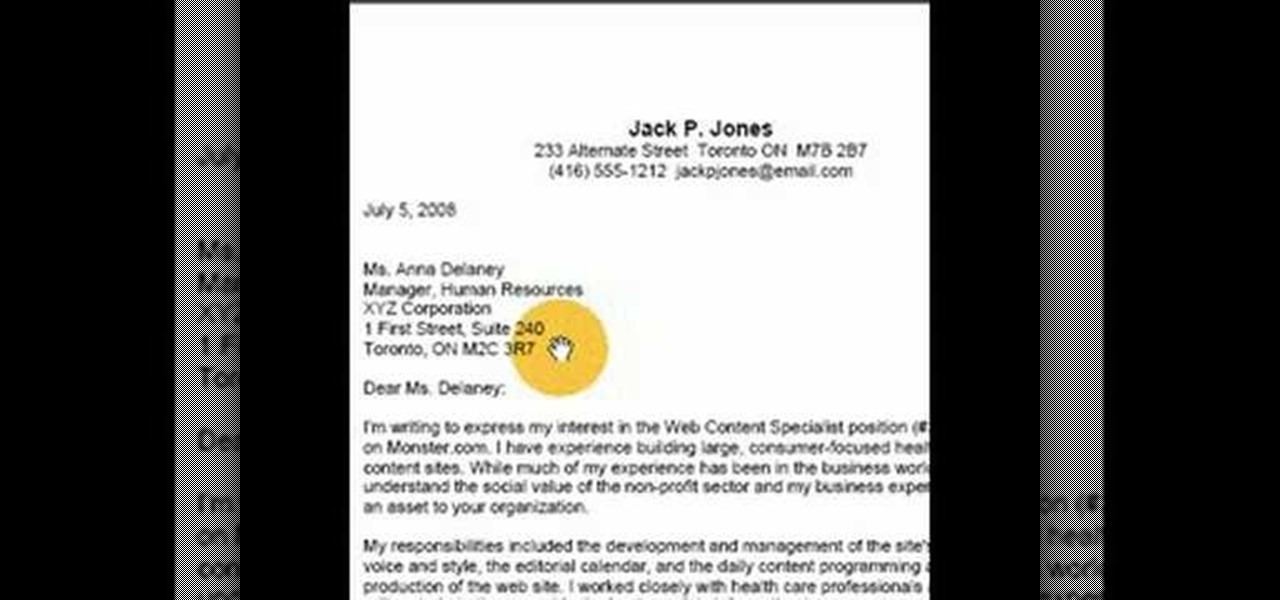
This video goes over cover letter formats, specifically in Full Block Style. Cover Letters accompany resumes in job applications. They should be sent ahead of the resume. They go over your experience, desires and objectives. The cover letter is important to both employers and employees. A human resources or HR department often receives thousands of letters that it must review before granting a job candidate a job interview or even reading their resume. This is a LIAD Production for World of W...
For all your jousting and costume needs, finally, an instructional video guide to building a chain mail suit of armor. While periodically inaccurate for Renaissance Fairs, Medieval Times employees or reenactment actors might be curious to either learn how to make the suit or at least witness the process. Chain mail was used as a protective armor in Medieval times, and was nearly impervious to arms of the period, but new advances in weaponry caused it to become obsolete. Chain mail is essentia...

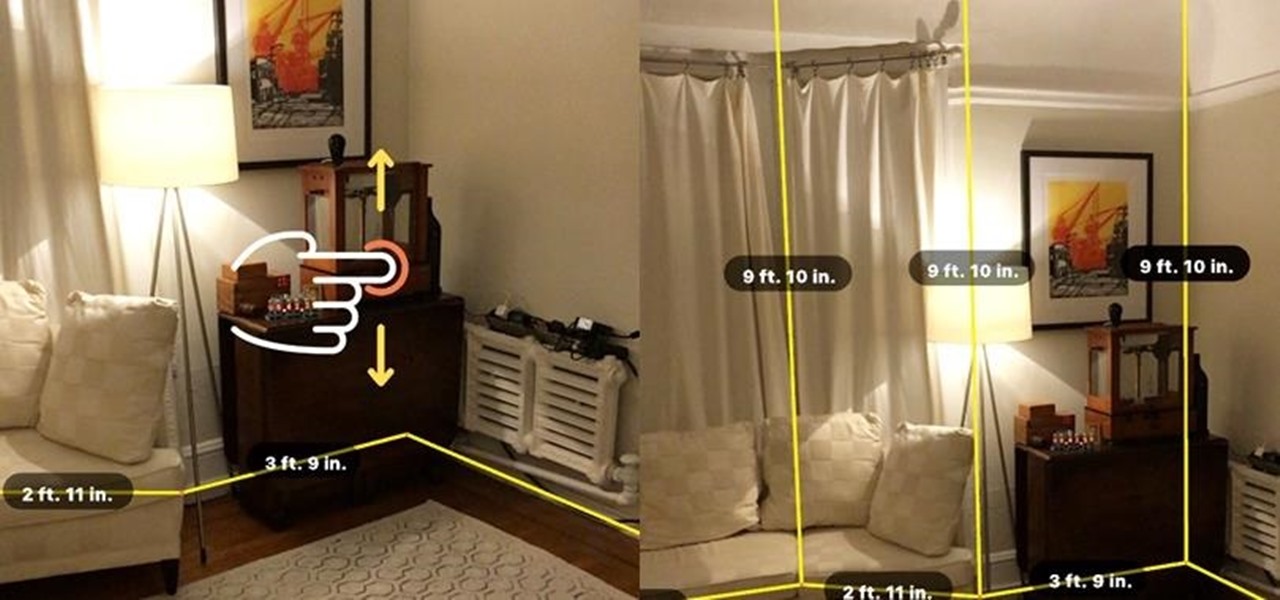
Less than a month after the worldwide launch of HoloLens 2, call center consultant BellSystem24 has already prepared an augmented reality solution for one of its clients.

Augmented reality hardware maker Avegant has reportedly laid off between 20 and 30 employees, with founder Edward Tang returning to the CEO role at the company.

With four major carriers, buying an iPhone X or iPhone 8 can be more complicated than you'd think. While Apple has its own iPhone upgrade program, AT&T, Sprint, Verizon, and T-Mobile all have versions of their own. Which plan you choose depends on your needs and, of course, your carrier. However, getting around to upgrading can be challenging to say the least.

It wasn't too long ago that Uber threatened to fire star engineer Anthony Levandowski. Eleven days to be exact. If Levandowski didn't turn over the documentation he allegedly stole from Google's autonomous car division, Uber informed Levandowski that they would take "adverse employment action." Today, The New York Times reported the ride-sharing firm has delivered on that threat. In a memo sent to employees Tuesday morning, Uber announced Lewandowski's official departure from the company "eff...

The race for the future of the automative world has never been tighter, with reports earlier this week that Tesla is now almost as valuable as Ford. The neck-in-neck companies are focused on the same next big step for automobiles: the driverless car.

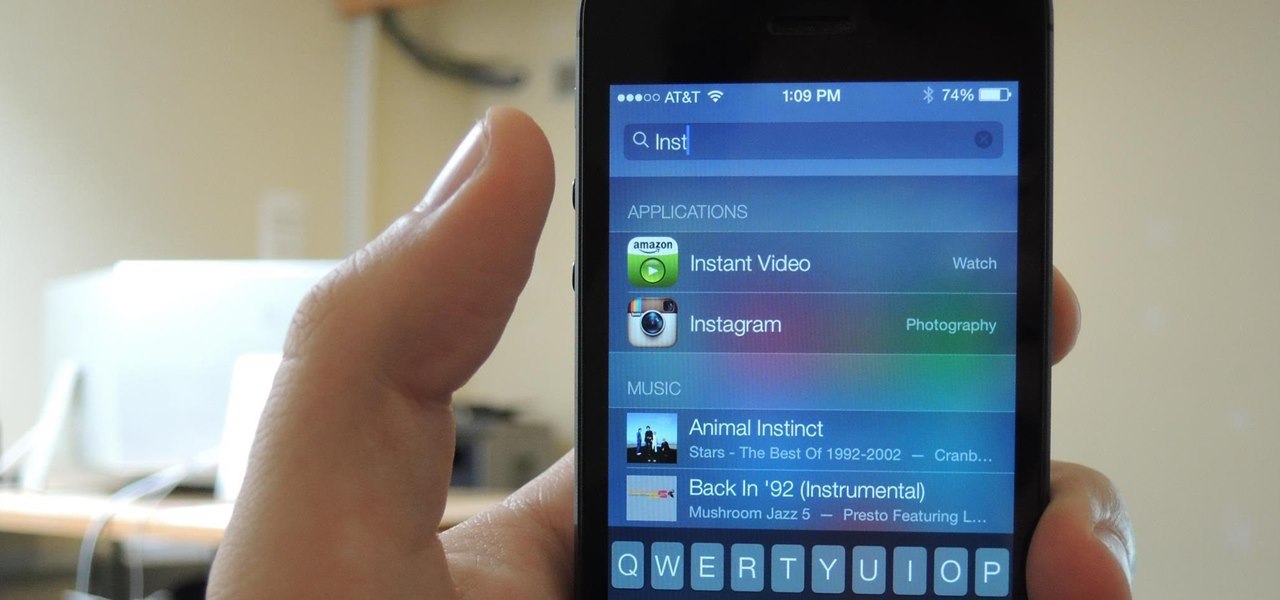
With all the little improvements that Apple made to iOS 7, some older features have been changed or moved (and sometimes, it's not obvious).

Who doesn't love a good prank? Taking advantage of unwilling and gullible bystanders is an obvious recipe for success—and some hilarious amusement.

There's absolutely nothing better than seeing the look of pure and utter shock on someone's face, and that is why I absolutely love this. It is by far one of the best pranks ever, and one of the best videos that I've seen in a while. Seriously. If you've ever used the drive-thru, you've gotta watch this.

Alright guys sorry for the delay, lets just get to it: » Pelosi Says Holder Contempt Charge About Suppressing Vote.

One of the worst-kept secrets in the tech world is Apple's plans for consumer-grade AR smartglasses, still unconfirmed publicly and only recently corroborated through a leaked account of an internal employee meeting.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Are you someone who always struggles to wake up in the morning, no matter how much you've slept? For most, the thought of getting out of bed any earlier sounds horrific. Yet dragging yourself out of bed and towards the coffee maker a few hours earlier each day can have benefits you've never realized. Here are six reasons that make a compelling case for ending our bad habit of sleeping a little too long.

No matter who you are, a little self-confidence can go a long way toward making your dreams come true.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

This week's Game Developers Conference came at just the right time for Magic Leap, a company that was riding a wave of bad news from legal troubles and rumors regarding Magic Leap One.

Noted poet T.S. Elliot once wrote that "April is the cruelest month." But Magic Leap might argue that March is the most miserable, as the Ides of March brought more legal woes to augmented reality startup. Elsewhere, its closely-held branding secrets have been spilled by way of the US Patent and Trademark Office (USPTO).

Cruise Automation follows Waymo's and Uber's lead with its debut of a beta version of an app-based driverless ride-hailing service for its employees in San Francisco, ahead of a possible launch of a full-fledged commercial offering within four years.

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

It looks like Chris Urmson has spent the six months since he left Google's Self Driving Car Project trying to build a get-rich-quick self-driving unicorn, along with Sterling Anderson, formerly with Tesla Motors. At least that is one of several scandalous accusations in a Tesla lawsuit aimed at the pair, and their secretive startup Aurora Innovation, LLC.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Remember how the bad guys in Scooby Doo would always use cut-out portraits to spy on people through walls? Well, unless your landlord is super cool, you probably shouldn't start cutting holes in your wall just yet, but you can make a higher tech version, thanks to NASA employee Mark Rober. Mark used a cheap picture frame and a portrait with the eyes cut out to make the "Scoob Cam," which also doubles as a surveillance device. He used an iPhone and an iPad to start a FaceTime chat, then taped ...

A Series B round of funding, totaling $30 million, will enable Helsinki-based startup Varjo to launch its industrial-grade augmented and virtual reality headset capable of "human-eye resolution" before the end of the year.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

Being the bearer of bad news is unpleasant; there's nothing more uncomfortable than offering up a spoonful of negativity. Whether you're a supervisor who spends a lot of time interviewing and rejecting candidates, or simply someone who has to say "no" to a friend, it's never fun to break bad news. But sharing unpleasant words or feedback with another person can become less of a burden with a few simple steps.

The coronavirus pandemic has ushered in an unprecedented time in modern history where terms like "social distancing" and "self-quarantine" have pushed their way into the zeitgeist.

Apple Card, Apple's foray into credit cards, is to be released this summer. There's no exact date set yet for when you can apply for one or when iOS will support it, but it's getting close. Apple just released iOS 12.4 developer and public beta 7, meaning we're almost there since iOS 12.4 is mainly intended to add Apple Card support for iPhone.

Four months after unveiling the latest productivity apps for the HoloLens, Microsoft now has a series of compelling real-world use case videos showing how the augmented reality device and its apps are helping oil giant Chevron.

When a firm like Techstars believes that augmented reality is an attractive industry to invest in, there's a high probability that it's right.

Over the past eight months, ten infants at UC Irvine Medical Center tested positive for the same strand of methicillin-resistant Staphylococcus aureus (MRSA). Despite the danger of this superbug due to its high resistance to most antibiotics, this information was only released to the public on Thursday. Thankfully, all ten babies survived and are currently healthy.

Autonomous vehicles, aka self-driving cars, are not yet available to the public (at least not ones SAE Level 3 and higher). However, this doesn't make the jobs any less in demand. In fact, if you meet the right qualifications, you could make a lot of money in this industry.

While augmented reality is mostly in the minds of consumers in the form of Pokémon GO, AR has been popular behind the scenes, with AR companies marketing it as a tool to help business operations become more efficient. This business-to-business market is the target of the new app DOTTYAR, which "provides 3D visualization tools for augmented reality viewers."

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...