If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particular app.

If you have a hard time remembering what you've just read on your iPad or Kindle, try changing the font next time. The typeface you use to read books, newspapers, and online articles is either hurting or helping your memory, and you'll be surprised which ones are killing your brain cells.

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

You know how annoyed you get when you put a quarter into the vending or washing machine and it gets stuck? There's a quiet rage that boils inside you. Now, imagine that quarter is a sixty dollar video game, and it's stuck inside your brand new, four hundred dollar PlayStation 4 system.

Tomorrow's the 1st of April which means it's the one day of the year you can put aside the daily grind, and go at it Dwight Schrute and Jim Halpert style. Yes, there are easy apps to do your dirty work, but if you're old school and you like to do it the old fashioned way, here are 10 simple pranks for torturing your co-workers.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

What happens when a entrepeneur/theme park creator and special effects artist/magician team up? You get a team crazy enough to create the first true virtual reality theme park (sorry, Six Flags). They only have a single experience so far, but it's already taken a giant leap beyond the wonders we've seen in today's consumer virtual reality headsets.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

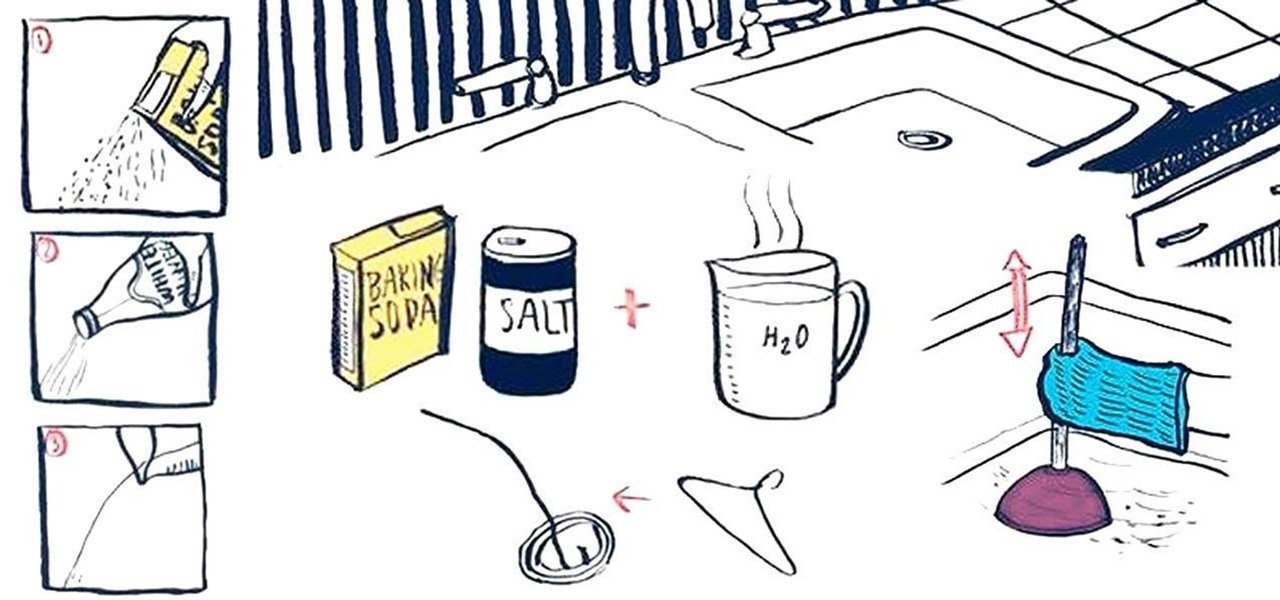
Oh, boy. A stopped-up drain. It'll inevitably happen with any home plumbing system and your kitchen sink is no exception. That clog won't go away on its own and will require immediate attention to keep any standing water from rising. But you don't have to resort to calling an expensive plumber or using a bottle of hazardous chemicals. Using simple kitchen staples or common household objects, as well as some determination, you can unclog your kitchen sink on your own without paying a dime.

With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions.

You're reading this so you're probably already safely huddled up in your house or apartment, watching as the entire planet grapples with the unfolding coronavirus health crisis. But unlike some others, you're lucky enough to already have a couple of weeks of supplies and now it's just about what you can do to entertain yourself and your family as you weather the current situation.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

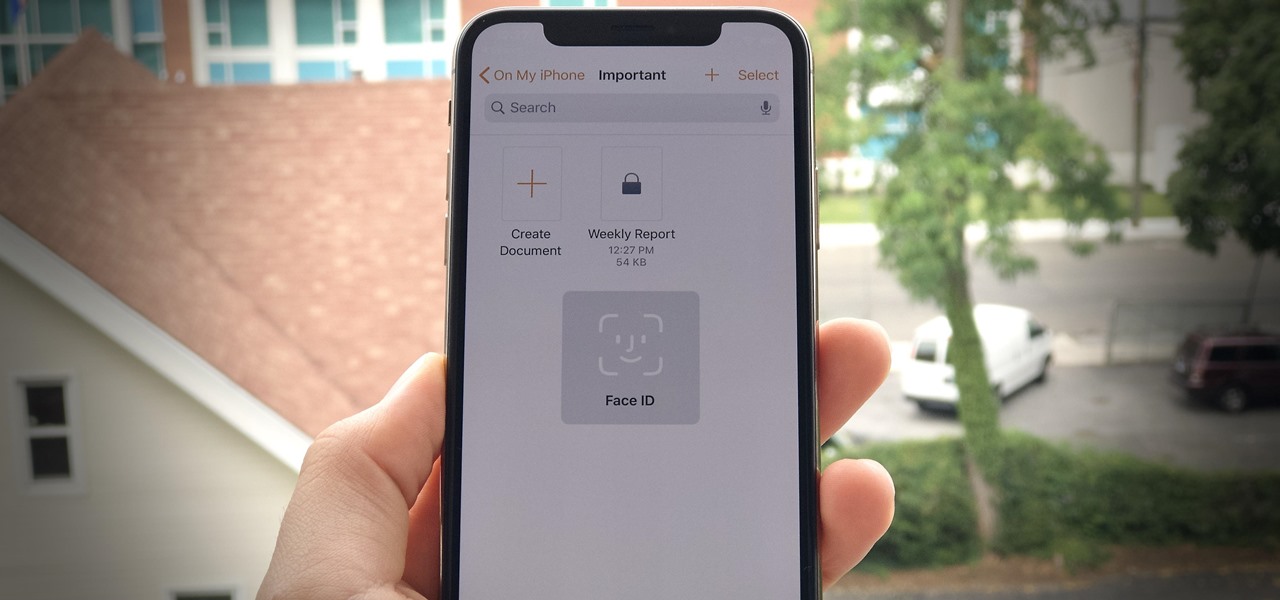
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

So you forgot to send that super important email to your boss, teacher, or another important contact. We've all been there. Spark makes these panic moments a thing of the past. With "Send Later," you can schedule emails to send at any time you want, even when you're not by your phone or computer. You just need to remember to write the email in the first place.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

This week, the recurring theme in augmented reality can be summed up fairly succinctly: content is king.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

These days, it's easy to cut the cord. Thanks to a new crop of streaming TV apps, you can get the same service offered by a traditional cable subscription at a fraction of the price. After some extensive testing, we believe we've found the absolute best apps for cord cutting.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

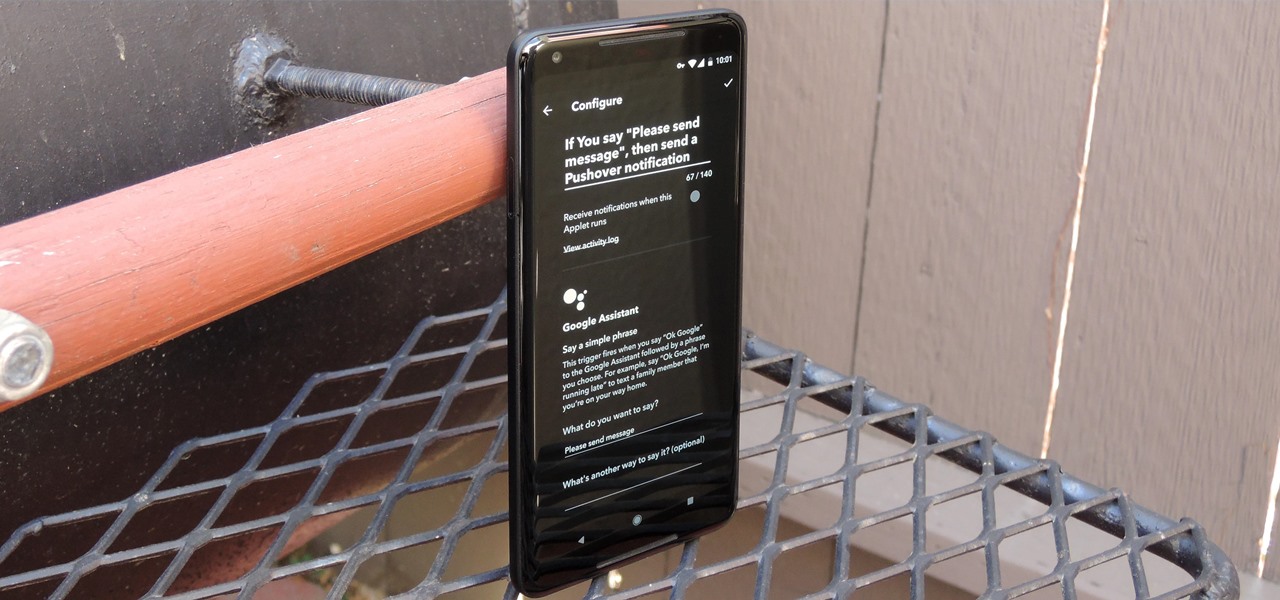
IFTTT is a fantastic tool that lets you trigger actions on your smartphone that normally require more advanced hacking. With the help of its friendly user interface, turning your phone into a more personal device has never been easier. However, the app has some more intricate options under the surface, making advanced implementations of applets difficult for beginners.

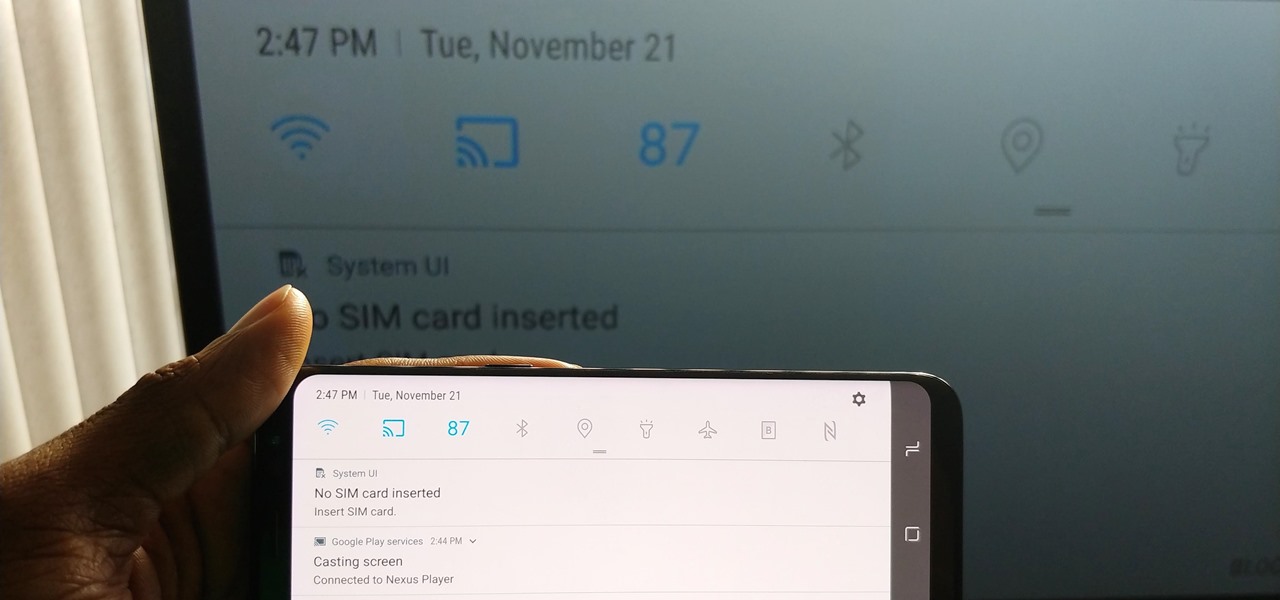
Android's Quick Settings menu gives you easy access to certain actions from any screen, but the tiles available are largely dependent on your phone's OEM skin. For instance, the Google Cast button that can cast your entire screen has been exclusive to Nexus and Pixel devices, even though other phones have the requisite software to use it. Fortunately, there's a way to add it on any device running Nougat or higher.

Twelve-year old Rory Staunton took a dive for a basketball during gym class and came up with a cut on his arm. The school nurse applied a couple of band-aids, without cleaning the cut, and off he went. In approximately three days, hospital physicians told his parents there was nothing else that they could do for their son; he was dead.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

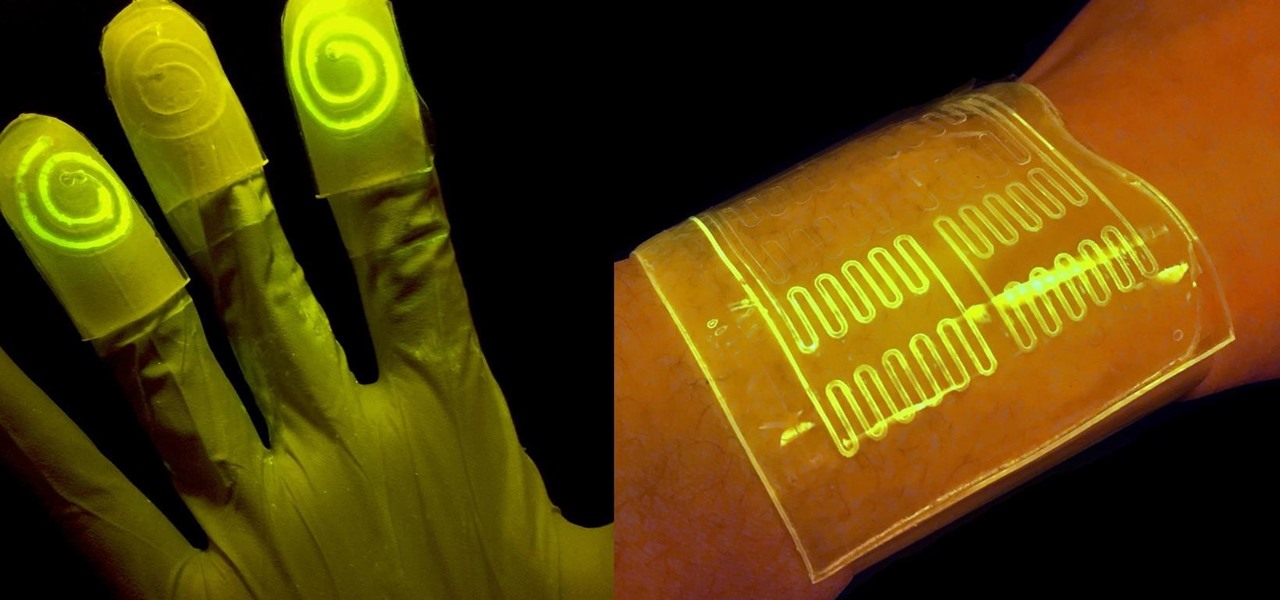
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

We recently covered an app called Fingerprint Quick Action that let you use your fingerprint scanner to expand your notification tray like the Google Pixel, along with a few other actions. It's definitely a useful mod, but there's a similar app can make your fingerprint scanner do almost anything—literally.

Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world.

We like our Egg McMuffins around here, albeit homemade with our preferred ingredients: whole wheat (or homemade sourdough) English muffins, a slice of thick Tillamook cheddar cheese, a meat, perhaps, like Canadian bacon, and finally—that perfectly-fried, perfectly-shaped egg.

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

With over 10,000 possible combinations, a four-digit passcode may seem secure, but it's fairly easy for someone to crack your code—no matter how clever you think it is. Luckily, there are many other options for securing your iPhone's lock screen—especially if your running iOS 9.

Android Beam is one of those features that makes you look at technology in awe, wondering how exactly something like that works.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

There are many reasons to root Android, but for me, the most important one is to have the Xposed Framework. Xposed gives you access to hundreds of modules, which take away the need to manually modify core system files to add new features and functionality to your Android device.