There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Wonder Woman has always been a Halloween and cosplay staple. It's a costume that's both dependable and stylish — just like the Amazon who wears it. This year's reprise with Gal Gadot offers a fresh take on the old standby, with more muted colors, a tougher demeanor, and a decided lack of stars or stripes. Tahnee Harrison from CineFix's DIY Costume Squad has come up with a compromise between the old and new costumes. It's got the cut, styling, and details of Gal Gadot's 2017 costume, but the b...

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

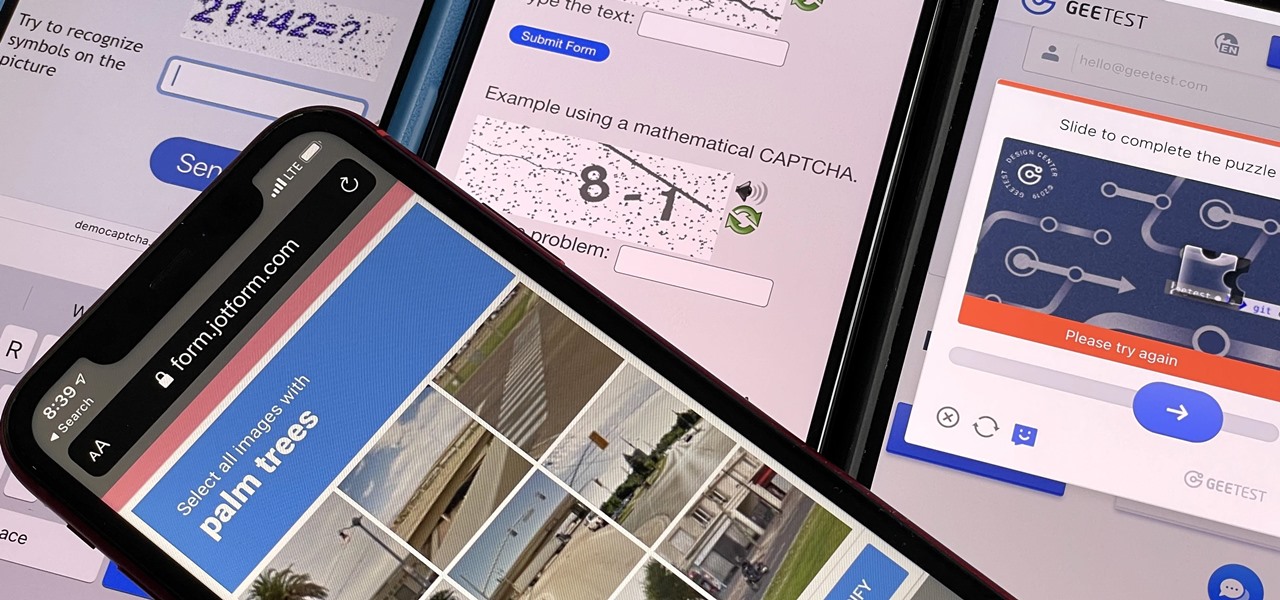
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

Google Voice has a hidden feature that lets you record any phone call you're participating in, and unlike other apps, it doesn't cost a dime.

For most Shortcuts automations you create on your iPhone, you'll get a "Running your automation" notification every time the task is automatically triggered. If you find those alerts annoyingly unnecessary, there's a less-than-ideal workaround to blocking them, but Apple gives us a better option in its iOS 15.4 update.

If you're using a VPN app to block ads or secure your Galaxy's internet connection, Samsung has decided you need yet another non-dismissible notification from One UI to tell you about it. Not just a status bar indicator like Bluetooth or Wi-Fi, but a full-size alert that can't be dismissed. The entire time your always-on VPN is running.

As first reported by Next Reality last year, game developer Preloaded, in partnership with BBC Studios, has finally launched BBC Earth - Micro Kingdoms: Senses.

One of the worst-kept secrets in the tech world is Apple's plans for consumer-grade AR smartglasses, still unconfirmed publicly and only recently corroborated through a leaked account of an internal employee meeting.

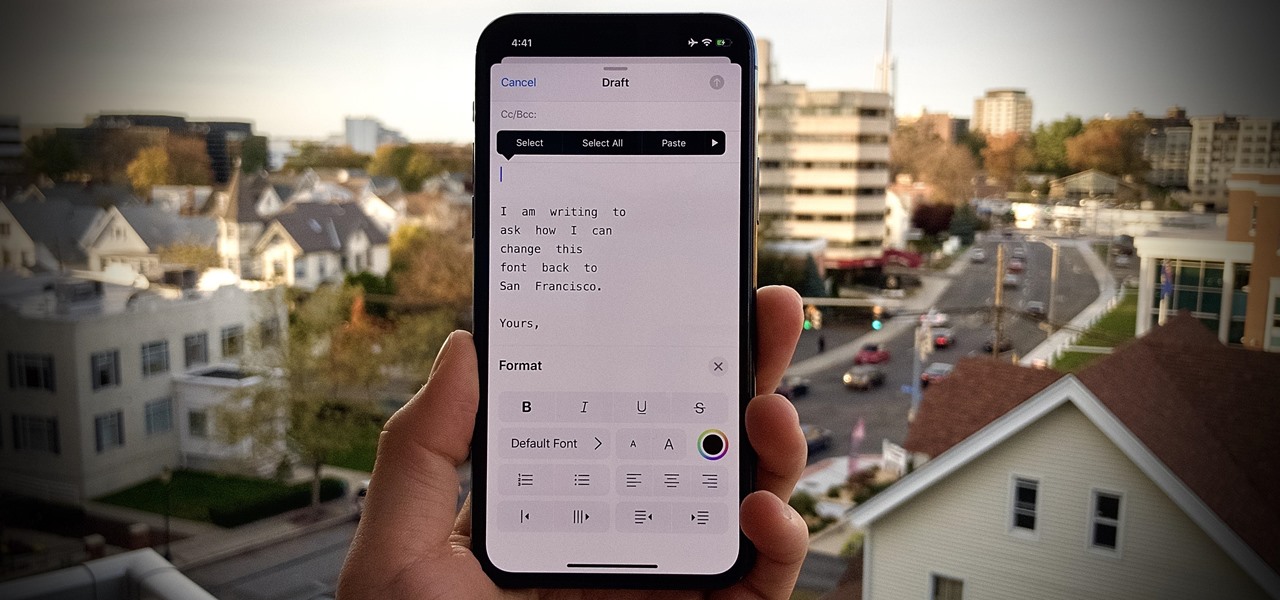
One of iOS 13's coolest features is the ability to download, install, and choose fonts in select apps like Pages and Mail. However, you might notice an issue when writing an email with a custom typeface: there's no option to return to the default font. What gives?

Higher-fidelity 3D content and next-generation AR experiences take more computing power than most modern AR headsets and mobile devices can handle. But Nvidia is introducing a new cloud-based solution to address that need that will stream AR content to modern devices.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

With Snapchat making the leap into the smartglasses realm, Facebook had to find a way to try and steal its competitor's augmented reality thunder.

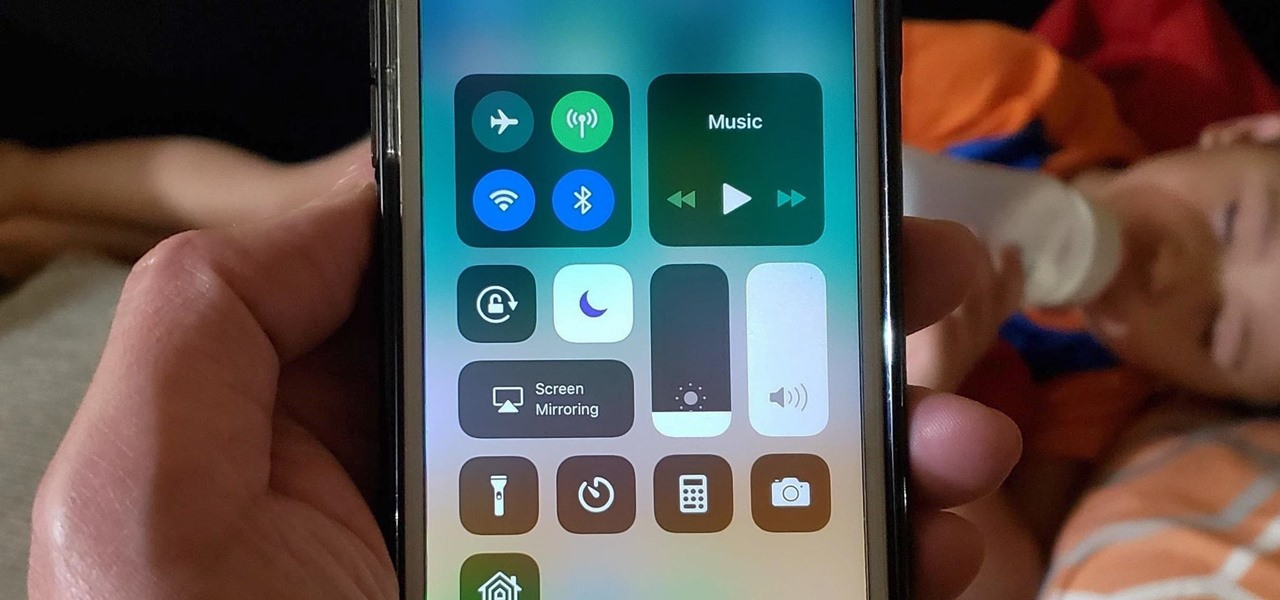
I don't know about you, but I like to listen to music throughout the day. As I am writing articles or doing some cardio at the gym, I go through my playlist, only stopping the music in situations where I have to. And ever since I switched to the Samsung Galaxy S10+, this has gotten even easier to do.

For those about to rock, Live Nation salutes you, now with augmented reality. This week, at the Cannes Lions Advertising Festival of Creativity in France, the live entertainment giant unveiled a suite of AR experiences that music festivals and their sponsors will be able to deploy in their mobile apps to engage attendees.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

While North has yet to add third-party app support to its Focals smartglasses, the company has been diligent as of late in its efforts to add more functionality to the bare-bones AR device.

Your Google history is mostly a binary choice — either you enable it fully, taking advantage of all its features while letting Google record your activity, or you disable it, staying incognito but also missing out on some fun stuff. But now, Google will let you auto-delete your history, allowing you to utilize all the perks that come with recording your history while maintaining some level of privacy.

Smartglasses maker Vuzix made a big splash at CES 2018 with the inclusion of Amazon's Alexa voice assistant among the AR superpowers of its consumer-centric Blade smartglasses.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

A week after reducing the base price of its Focals smartglasses by nearly 50 percent, wearables maker North is now reducing its workforce.

Just over two months ago, smartglasses startup North opened the doors at its two brick-and-mortar retail locations in Toronto and New York and began accepting orders for Focals. On Thursday, the company announced that those initial customers can get ready to pick up their wearables, as the first shipments have now arrived in stores.

Not all enterprise augmented reality tools require a high-end headset and heavy computing power. Sometimes, a smartphone can do the job just as well. Along those lines, software maker Atheer is now bringing its workforce AR platform to iPhones and iPads via a native app.

The tradition of using cutting edge technology to prepare for missions in space, in this case, augmented reality, continues with a new team of international astronauts slated to board the International Space Station (ISS) later this year.

We are in the midst of a mini-boom for communications tools designed for augmented reality headsets, with the introduction of Avatar Chat and Mimesys for Magic Leap One and Spatial for the HoloLens within the last few months.

Whether it's for health reasons or just to look better, many of us want to get in shape. It's a long process that starts with nutrition, and dieting is never easy. Fortunately, there are some great food-tracking apps that will make it a lot easier to become a healthier version of yourself.

Any real Star Wars fan knows that fear is a path to the dark side, as it leads to anger, and then suffering. For players of Star Wars Jedi Challenges, though, access to the antagonistic side of the Force is now available through their mobile apps.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

You just brought a brand new Pixel 3 from the Google Store, and you insert your SIM card only to find the phone won't recognize it at all. No matter what you do, the SIM card won't register and your Pixel won't connect to your carrier network. That's what happened to me and several other Pixel 3 owners. The good news is a fix is coming, the bad news is Google doesn't have a date for that fix.

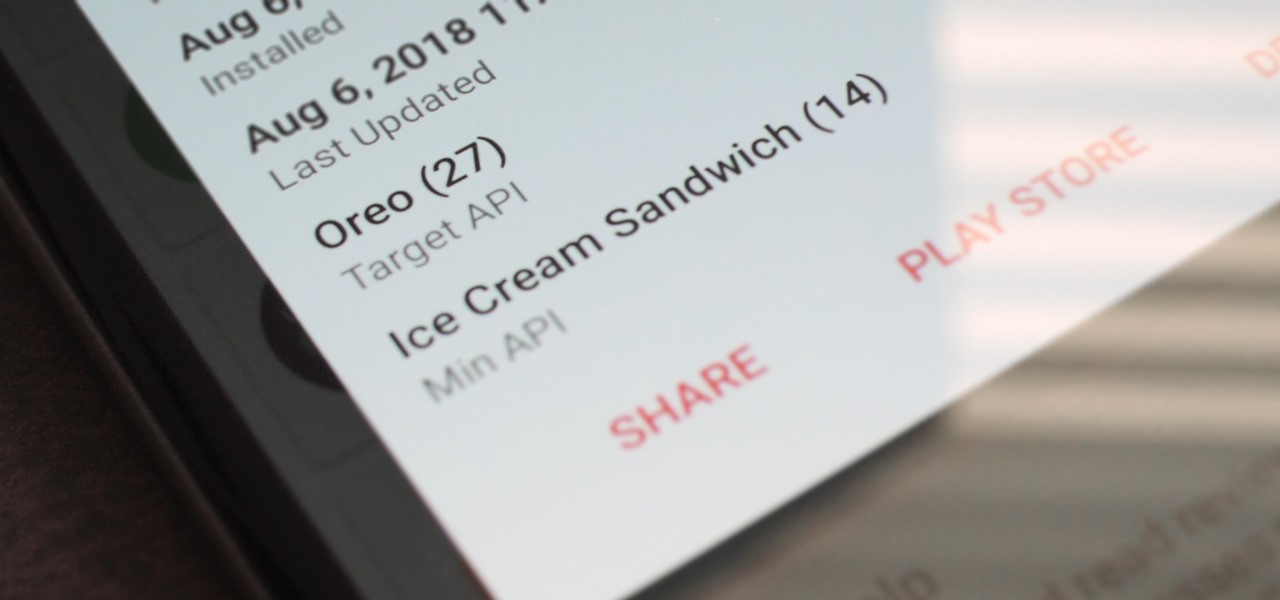
Starting November 1, 2018, Google will require that all new apps and updates to existing apps target Android 8.0 Oreo or higher. This move means the developers behind many of your favorite apps are now scrambling to get their software modernized, while others are considering abandoning outdated apps altogether.

Better known among consumers for its virtual reality apps, Jaunt is now pivoting toward solutions for augmented reality developers.

With iOS 12, Apple is offering users more options than ever to create, store, and manage their saved passwords. Not only can iOS 12 make you new passwords via the AutoFill feature, you can quickly and efficiently access your entire iCloud Keychain using Siri. Why go hunting for the passwords yourself when you can ask your iOS assistant to find them for you?

With the arrival of iOS 12, Do Not Disturb has received long-overdue enhancements to make the feature more user-friendly. Among these changes is a subtle but incredibly convenient feature that helps ensure you remain undisturbed for short periods of time to more focus on your task at hand — without having to worry about turning it off manually or messing with complicated settings.

The roster of handsets supporting Google's augmented reality toolkit now includes 46 Android models as well as support for ARKit-compatible iPhones and iPads.