Learn how to properly use a import slide tool on the older Playstation 2 console in this instructional video. With this tool, you'll be able to play those import games that never made it to the US. Keep in mind that the slide tool can break your disk tray if its used improperly.

Many injuries do not require an ambulance, but they must be referred to medical aid for further treatment. This first aid how-to video will show you how to identify wounds that require further treatment. Underlying and dirty wounds, foreign objects, and stitches are all injuries that require a patient to go to a doctor or hospital.
In this video tutorial, Chris Pels will show how to deploy a web site using the Copy Web Site Tool in Visual Studio. First see how to connect to a remote web site and deploy an entire site to the target location. Next, learn how to synchronize an entire source and target web site. In addition, see how to copy and synchronize individual or groups of files including how the Copy Web Site tool provides status indicators of differences between files. As part of this process see how the tool provi...

Surprisingly, in single layer mode the Eraser Tool doesn't really erase. Part one of this Photoshop podcast covers Eraser Modes and Background Colors. Part two covers the other Eraser Tools include the Magic Eraser and Background Eraser. And these eraser tools really do erase.

This guy has a lot to say about using the text tool in Photoshop, so he put it all into a 4 part video. Part one covers create, select and edit Text, Point Text and Paragraph Text options. Part two covers Options bar, Great Shortcuts, Character Pallet and Resets. Part three covers Text align, Paragraph palette, Hyphenation and Justification. Part four covers Text for Web, Text Wrap, Text Masking.

The extract tool in Photoshop is one of the most frequently used - and useful - tools you'll ever learn to use. Extracting allows you to remove a picture from its background or even filter away flyaway hair.

In this video, Chad West shows you some more precise color correction methods and explains a little bit about the dodge, burn and sponge tools. Those of you who already know your way around Photoshop should probably not waste your time watching this video. It's meant for beginners.

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

After introducing and launching Reality Composer alongside iOS 13 and ARKit 3 last year, Apple is making it easier for developers to create apps with it.

TWRP is a name many are familiar with since it allows your Android device to install any custom file of your choosing. You can create a NANDroid backup to keep your data safe or even use Magisk to achieve full root access. In fact, TWRP is often seen as the gateway to modding your system for creating a unique user experience.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

We're still weeks away from a probably HoloLens 2 release, but Microsoft's immersive computing team is still hard at work on other aspects of its "mixed reality" ecosystem.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

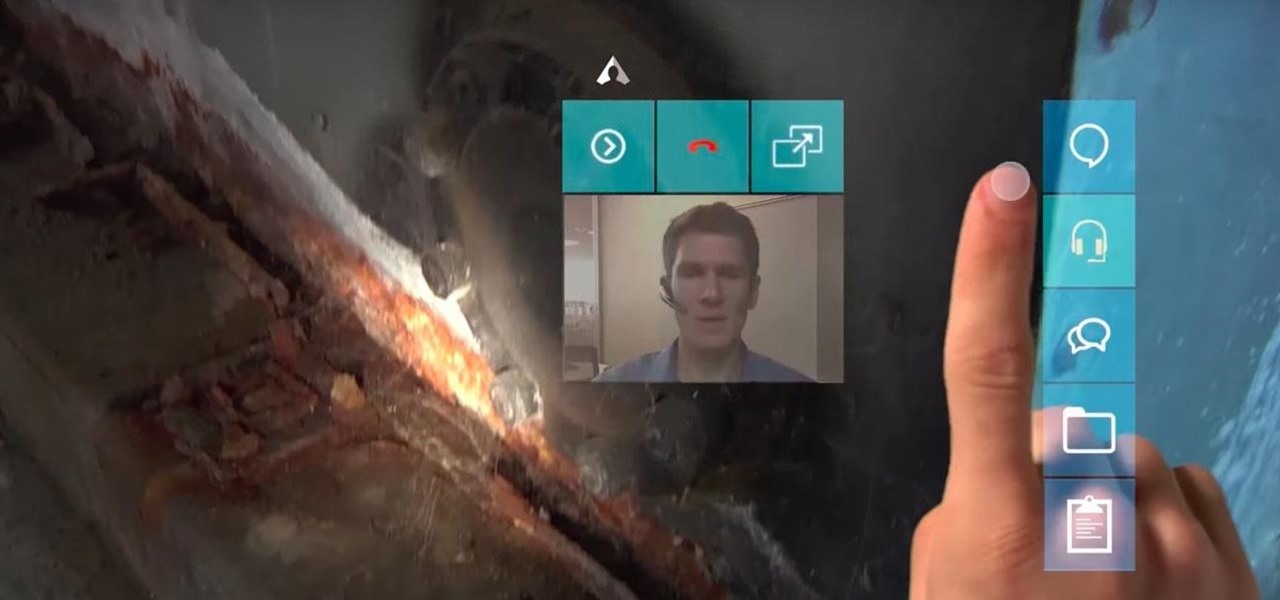
Not all enterprise augmented reality tools require a high-end headset and heavy computing power. Sometimes, a smartphone can do the job just as well. Along those lines, software maker Atheer is now bringing its workforce AR platform to iPhones and iPads via a native app.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

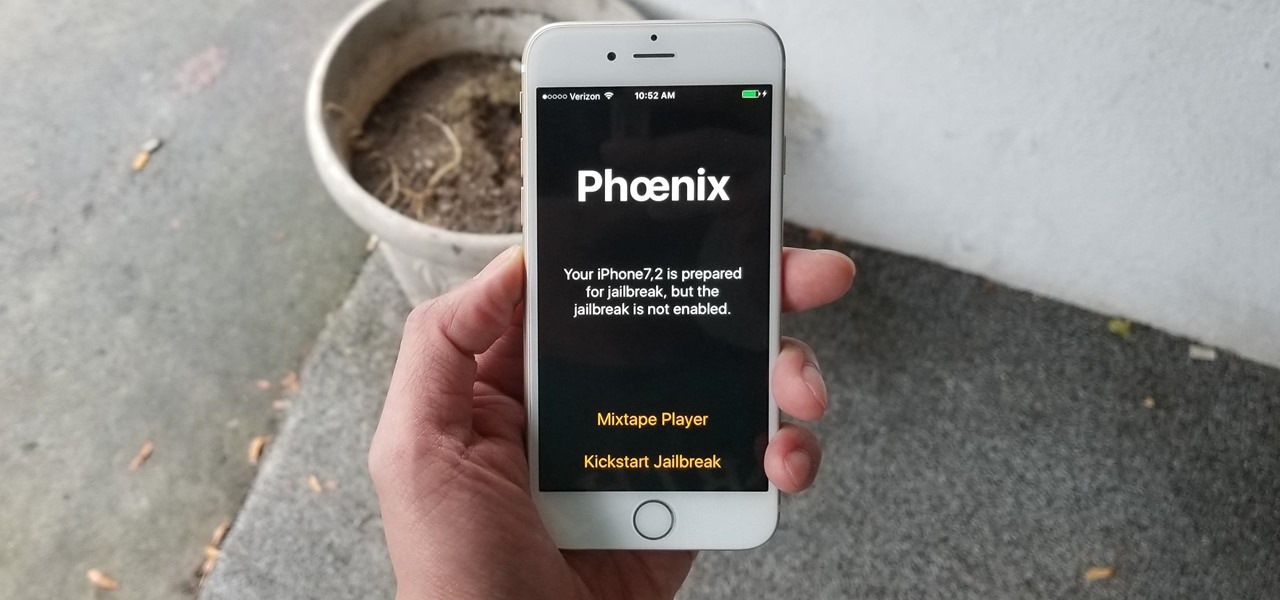
Unlike fully untethered jailbreaks such as Yalu's iOS 10.2 method, semi-tethered jailbreaks require users to re-enable the mod each time their device is turned off. Fortunately, the process of kickstarting a jailbreak is easy to do, since it's already embedded in your iPhone's OS and doesn't require reinstallation.

At Next Reality, we've been following the Microsoft Hololens because of its enormous potential. Unlike virtual reality, which enshrouds the user in a complete virtual world, augmented reality melds the virtual with what's really there in front of you. And while some of us may use AR technology to stealthily surf the web during working hours, others are looking towards using AR for the betterment of society. Like putting the HoloLens in space.

The Samsung Galaxy S8's almost bezel-less display is truly a sight to behold, especially when set to Immersive Mode. While transparent when on the home screen, the navigation and status bars on the S8 will often turn opaque depending on what app you're using at the moment. This, in turn, can detract from the overall experience when viewing anything from the S8's display, as the bars along the top and bottom of the screen bump the phone's aspect ratio down to lower levels.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

Hello, everyone. If you've been following my recent articles, you'll know that I've been rather busy lately working on a project, a rather large one. I've been working with Pheonix750 and Ciuffy to build the Null Byte suite of tools! I got the green light from our admin a while ago, and we've been developing like mad ever since! I'm very excited to launch this project. So, let's start by explaining what it is...

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

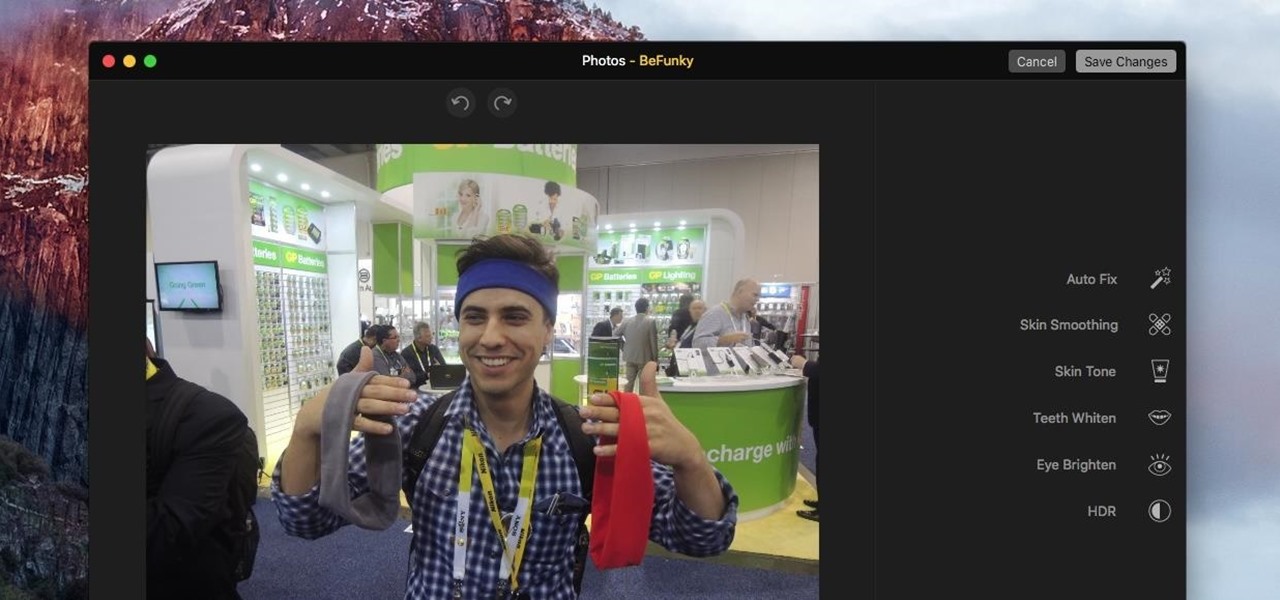
For minor adjustments and color-correction, the Photos app is extremely useful, but its capabilities are limited to just the basics. Now, with Mac OS X El Capitan, Apple is opening the door for third-party extensions, meaning we can utilize additional, unique tools when editing pictures in Photos.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Brought to you by Purdy Paints The art of painting requires excellent tools. And with so many options on the market, it can be hard to find a brand that works for you and your DIY project. That's where Purdy comes in.

One of the best times to get creative during the year is Halloween, and if you're one of those people that like to make your own costumes and decorations, then here's a little something you can do for that scary night... A GHOST!!!

The thermal fuse in your dryer is a safety device designed to prevent the dryer from overheating. The fuse is heat sensitive and when the dryer becomes too hot it will blow. If the fuse has blown then the dryer will either stop working or there will be no heat when the drum is turning. A blown thermal fuse is simple to replace. With a few tools, a do it yourself warrior can save valuable money from being wasted on a service call. Here is a detailed set of instructions on how to replace a ther...

This slime is toxic-free and can be used as either a kid toy or to make a great prank. This slime can be made in just a few minutes and doesn't require much for materials. Our video explains in detail how to accomplish this project with step-by-step instructions.

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

Use the Xara Web Designer 7 Premium Mould tool to mould, re-shape and change perspectives of objects. The Xara Web Designer Mould tool will allow you to create some very interesting effects to make your website stand-out and have depth. Even the thumbnail shown for this web design video tutorial was created with the envelope tool. If you have ever seen the software boxes shown on various those are usually created with an envelope tool to give the box its perspective.

The fill tool will allow you to alter the appearance of objects in your web design document and can be very useful for marketing purposes. The fill tool can be used to give objects one solid color for simple designs.

Plasti Dip coating is a rubber like coating that can be dipped or sprayed on. I first remember the coating available as a dip years ago. It was first introduced as a coating used to dip tool handles in to provide a grip. However, since then, the coating has became available in a spray can. It has also became popular on car parts, such as wheels, emblems, and even entire cars.

The Desire HD's Smart Dial autocomplete tool makes dialing numbers a snap. Learn how to use it with this quick, official guide from HTC.

Lockpicking might not be the most well-respected discipline in the world, but it's very useful for crime, survival, and all sorts of other disciplines. This video is of a presentation from a lockpicking conference that focuses on economical lockpicking. Topics include getting cheap tools and space as well as using heat treating to turn cheap lockpicks into more durable effective ones.

Threaded metal rods and bars are useful to have around because they allow you to make custom length bolt and nut combos whenever you like. Cutting them to the right length in such a way that your nut will still fit on the bolt can be tricky, but this video will show you just how to do it with a hacksaw and other tools.