Wearing a seat belt while in a car can save your life. Do you know how to adjust and properly use it? Learn how to drive safe and use seat belts properly (Ford DSFL). A professional driver explains how to fasten your seat belt properly.

What do you know about braking in an emergency situation? If you're not even sure what kind of brakes you have on your car or truck, then you need to do some research. Learn how to drive safe and deal with emergency stops (Ford DSFL). A professional driver explains the differences between braking with Antilock Braking Systems (ABS) and standard braking systems.

Driving a vehicle is a big responsibility and road safety is paramount. Improve your driving skills by using your most important tool -- your EYES! Learn how to drive safe and always look ahead (Ford DSFL). A professional driver explains why it's important to look where you want to go, not at an obstacle, when you're driving.

When you're on the road, you want to be in control of your vehicle. The only way to be in control and improve your driving skills is by having good hand positions and correct and comfortable seating position. Learn how to drive safe with a good hand and seat position (Ford DSFL). A professional driver gives this important tip about seating position.

Want to fulfill your dream of becoming an ice cream truck driver? If the idea of rolling around in the sunshine selling ice cream sounds good to you, here's what you need to do.

Looking to move the right way? Owning a piece of property is an important goal for many people. Here’s how to obtain a copy of proof of ownership.

Superman is one of the greatest and most known superheroes out there. Developed by DC Comics, Superman has seen the world… as in comics, television, newspaper strips, video games, movies, radio serials, etc. See how to make a Superman costume in this video from GiannyL.

Eagle Lake Woodworking, hosted by John Nixon, offers great do-it-yourself guides for building your own furniture, especially in the American Arts and Crafts style, and turning your garage into an amateur woodshop. Search Eagle Lake on WonderHowTo for more carpentry tutorial videos. From Eagle Lake Woodworking on this specific lesson:

Elegant fashion is easier to come by than many assume. This tutorial shows you how to sew your own simple V-neck women's tunic with added flutter sleeves. You don't even need a pattern, just a few torso measurements for your wearer!

If you want to stop telemarketers from calling, use this guide and try a multi-pronged approach. You Will Need

Professional camera cleaning is expensive and usually more than you need. Follow these simple steps to keep your lenses clear and smudge-free.

Why sweat through a boring exercise routine when you can achieve the same results while having fun? You Will Need

Your friends want you to marry them! Before you can officiate their big day, you'll need to jump through some legal hoops. Learn how to officiate at a wedding.

Learn how to write a grant proposal. If your organization has come up with a great idea that needs money to get off the ground, you'll need a great proposal. Here's how to write one.

It’s never too late to clean up your credit record – and save yourself thousands of dollars in exorbitant interest rates in the process. Learn how to repair your credit with this guide from Howcast.

Knitting with the wrong needles is like playing soccer with a bowling ball –you’ll end up frustrated and disappointed.

The most widely known Christian prayer dates all the way back to Jesus himself. It can be found in the Gospels of Matthew and Luke, though Matthew's version is the one most commonly used. Learn how to say the Lord's prayer.

Check out this video tutorial on how to make free phone calls from your iPod Touch or iPhone to any other phone out there. You will be using a free application from the iTunes App Store called Fring. This allows you to make VOIP phone calls.

Check out this instructional legal video sequence that shows you how to file a motion in family court. This video contains important information on preparing and serving a motion in family court. The most common reasons for filing a motion are to request a court order affecting child custody, parenting time, or child support. The court has forms and instructions for the most common problems. Please remember the court is a very formal place with a set of language and rules. This is the video i...

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Tim Carter shows a clever method that prevents tree roots from entering an underground sewer or septic line. Check for underground utilities before attempting this project.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

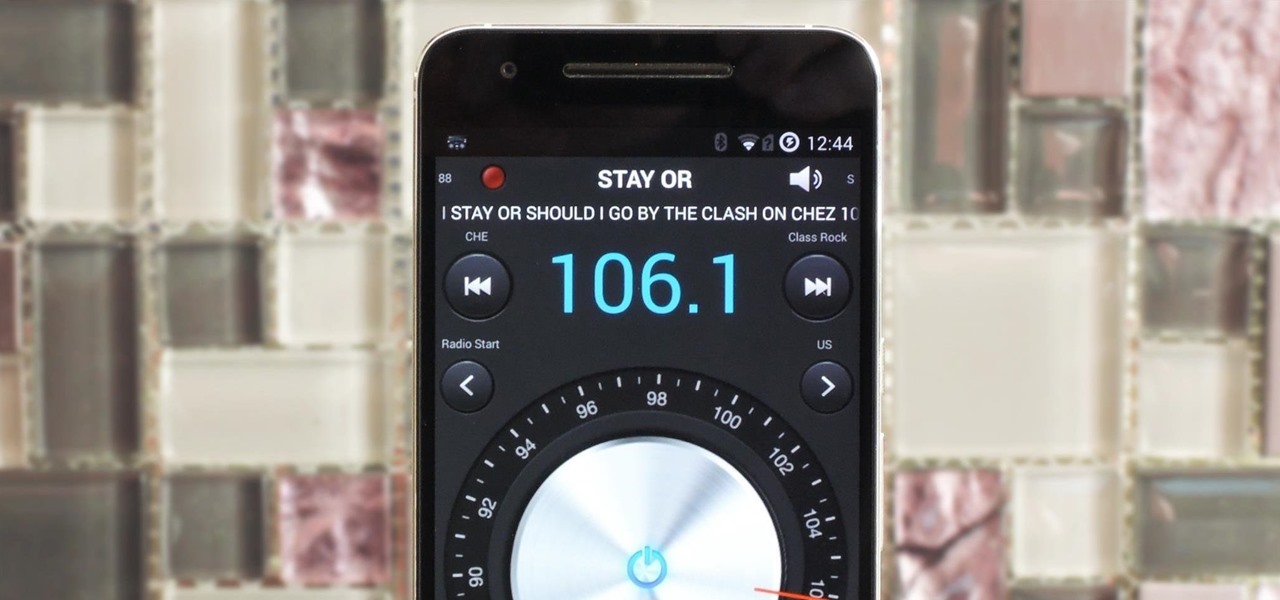
Android smartphones have all sorts of connectivity chips built in, including Bluetooth, Wi-Fi, GPS, NFC, and mobile data. But what about AM or FM radio, two of the most common methods of wireless communication?

Olivia shows how to make ‘Woolen Mittens’ in this video, by recycling an old sweater! She begins by washing an old sweater in cold water. After washing, she puts the sweater in a dryer at high heat mode, to shrink it. The washed, dried and shrunk sweater is then placed on a table. The required length of the mitten is decided, taking care that the bottom end of the sweater shall be placed at the point where the mitten ends on the arm. The arm is then placed on the sweater and a mark is made ab...

To play "People are Crazy," you begin with what is called the intro. For this song, the intro includes playing the same group of notes or strings two times; this is called "repeat" on the sheet music. All of the these notes will be played on the B-string except for one. The exception is played on the G-string and this is just played open. Start on the 10 thread (fifth string capo) holding it with your ring finger, count to the fifth string and play it twice, pause, then play 5, 3, 1, and then...

Looking at homes is the fun part. But before you go house hunting, make sure you have your financial ducks in a row.

Testing products for a living is a bit more complicated than it sounds. You Will Need

Here is a cake type of chocolate cake, it uses biscuit cookies. You will probably have to fight the kids off just because you want it all to yourself. The best part is that there is no baking required and it is very simple to make. The only thing you need is patience - just enough to make it and allow it to chill before you dig into it. Watch this how to video to learn a quick recipe for a chocolate biscuit cake recipe.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

This beauty and style video demonstrates how to make transitional dreads. First the color of fibers is chosen of required lengths. The strands are put around elastic supports held taught by two posts of bed or other furniture. The base color, in this case blue, is pleated like hair up to a length required. Before pleating, the fibers are loosened with a comb. The lower portion below the pleats is loosened with a comb and twisted tight. Over the pleats the other color, in this case cream, is w...

In this video tutorial, viewers learn how to make coleslaw dressing. This video provides all the ingredients required in order to make the dressing. The ingredients required include: 1 cup of mayonnaise, 1/2 cup of sugar, 1 tbs of white vinegar, 1 tbs of prepped horseradish and 1/2 tsp of celery seeds. Users simply add all the ingredients to a bowl and whisk it. The coleslaw can also be mixed with shredded raw cabbage or shredded carrots. Once mixed, leave the dressing in the refrigerator for...

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

In the US, law enforcement officials can make you unlock your smartphone with a fingerprint, but they can't force you to input a password or PIN, which would violate your Fifth Amendment rights. To help you from ever being in a scenario where you're forced to put your finger on the Touch ID sensor, Apple has a built-in way for you to disable biometrics on your locked or unlocked iPhone in mere seconds.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?