
How to Train Your Python: Part 13, Advanced Lists, Slicing, and Comprehension
Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.


Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Hello everyone. I've recently made the annoucement of the Null Byte suite of tools, and we've covered how to download and install it. Now it's time we cover how to submit a tool for inclusion into the suite. It's relatively simple, but we need to get a few ground rules out of the way.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!
Not too long ago, Sony was looking to create a method for theming the interface of their Xperia smartphones and came up with a framework called Runtime Resource Overlay (RRO). They then contributed this framework to Android's main code base, and Google has since taken over the development of RRO as a way for manufacturers to implement themes in their skinned versions of Android.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Google now has an iOS version of Android Wear, so if you own an Android smartwatch (Moto 360, ASUS ZenWatch, Huawei Watch, LG Watch Urbane, Sony SmartWatch, etc.), you can finally connect it with your iPhone.

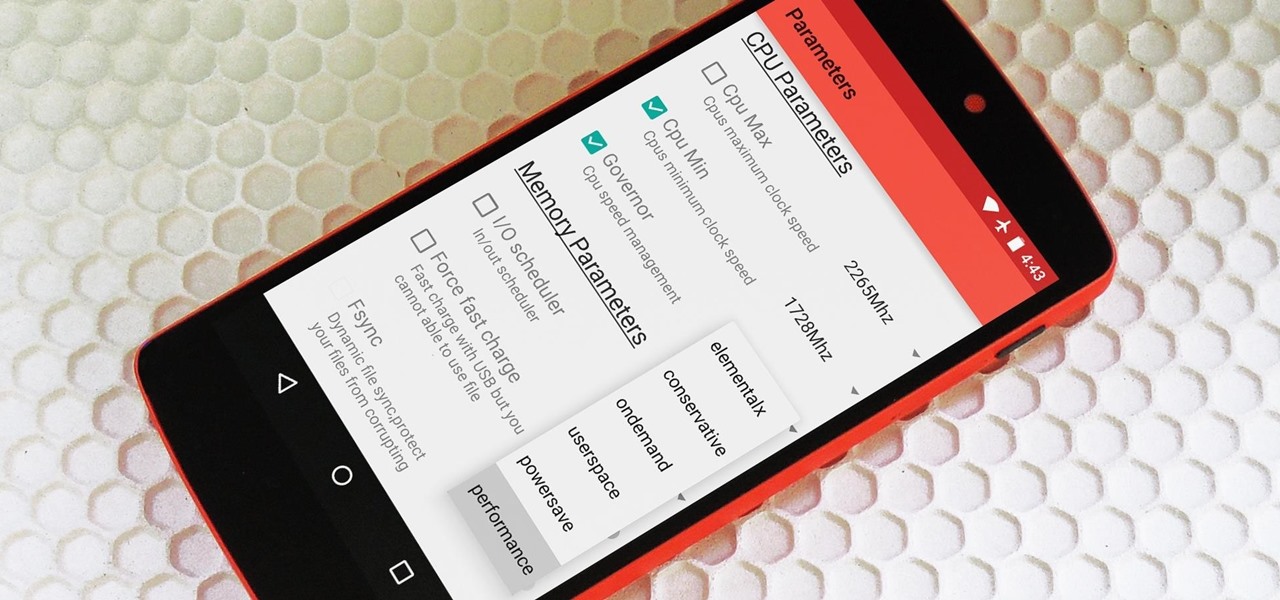
There are many reasons to root Android, but for me, the most important one is to have the Xposed Framework. Xposed gives you access to hundreds of modules, which take away the need to manually modify core system files to add new features and functionality to your Android device.

Although iOS 8.4 was just released, the team behind the iOS 8.3 jailbreak have updated their tool for the latest operating system, and will work on an iPad, iPhone, or iPod touch. So if you've been wanting to get all your tweaks back, or want to start exploring all of Cydia's options, now's the time to jailbreak.

KNOX is a major pain for Samsung owners who like to modify their devices. Its combination of hardware and software security measures make things rather difficult when you're trying to modify system-level files and functions without voiding your warranty.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...
Deep down at the core of Android lies the system kernel, which serves as a bridge between software and hardware. Custom kernels can be installed in place of the stock offering, and these are generally optimized for better performance or increased battery efficiency.
HTC's Sense UI is generally regarded as one of the best manufacturer-skinned versions of Android. This is mainly due to the subtle and classy styling of the interface, as well as some unique features that are added in here and there.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.
UPDATE 11/17/15 The Xposed Framework now officially supports Android 5.1 through 5.1.1 Lollipop devices as well. Everything will still work the way it has with Android 5.0 through 5.0.2, but there are a separate set of files for the newer Android version. I'll cover both below, but make sure to download the proper file for your particular version of Android.

We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all.

Android is all about customization: "Be together. Not the same," as Google's latest ads for the platform put it. Changing your device's boot animation, for instance, is one of the many great ways you can add a touch of personal flair.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.
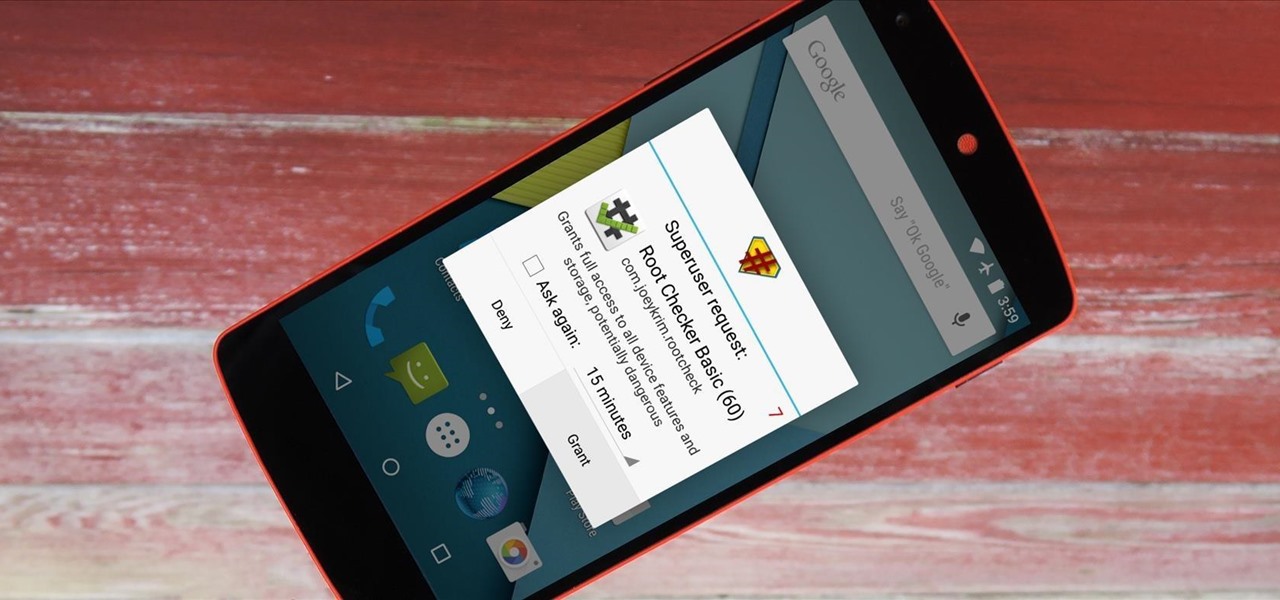
It didn't take long at all for developer Chainfire to sort out a root method for the new Android 5.0 Lollipop. After handling a few issues with changes to the SELinux kernel module, Chainfire pushed out an update to his popular SuperSU root app.

When you're actively using your phone, a certain amount of battery drain is to be expected. But, if your device is just sitting in your pocket draining its battery, that's when you need to take action.

If you've ever noticed that the stock launcher on an Android device seems to just feel faster than any third-party home screen replacement app, this is not a placebo effect. Most manufacturers, Samsung included, force their stock launchers to reside permanently in your phone's memory, thus reducing the risk of redraws.

Many Android games use large, storage-heavy OBB files to store supplemental data. Generally, games with high-end graphics download these extra files when you install them from the Google Play Store.

Most Android devices allow you to simply replace a ZIP file in your /system/media folder if you want to change your boot animation. Unfortunately, though, this isn't the case for the Galaxy S5, as it's been buried deep in Samsung's TouchWiz skin.

The Galaxy S5's fingerprint scanner feels like something straight out of a sci-fi movie. Giving you the ability to lock your device without having to fuss with a PIN or password every time you go to use it, the feature is definitely one of the device's main selling points, especially now that you can use it to unlock individual apps.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.
Because of Android's massive array of supported smartphones that carry vastly different display sizes and resolutions, the operating system uses a value known as DPI to determine the size of icons and visual assets that will best suit a given screen.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.
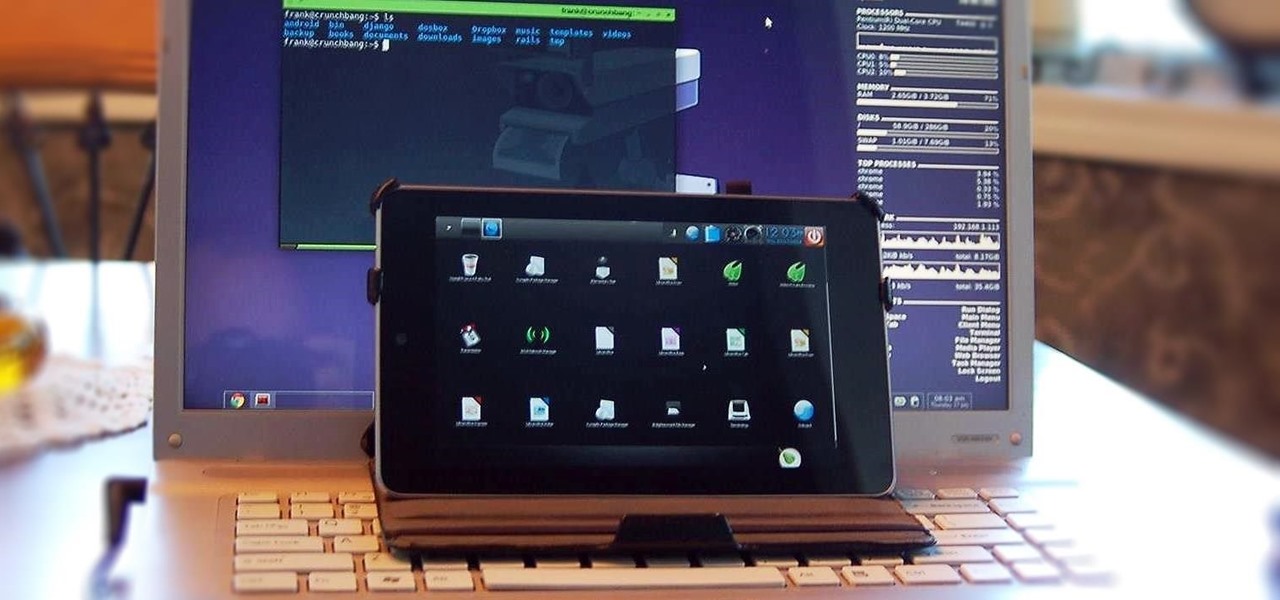
When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.

Like Costco's price codes or the tags on your bread, the numerical codes printed on those sticky little fruit and vegetable labels can reveal a lot of information to us consumers. Once you understand the codes, you can look at that little label (also known as PLU, or "price look up" label) and know whether the produce you're about to buy or eat was treated with pesticides, genetically modified, both, or neither. Before we go any further with deciphering the codes on these labels, let's take a...

Apple released the fifth iOS 14.7 betas to developers and public testers today, Thursday, July 8. The update appears to be minor, adding new splash screens when opening Reminders and Podcasts for the first time.

Apple released the third iOS 14.7 public beta for iPhone Tuesday, June 15. The update comes one day after Apple released the third 14.7 developer beta, and twelve days after the second iOS 14.7 beta, which was only released to registered developers.

Apple's exclusive chat services, iMessage and FaceTime, force many of us to stay locked into iOS, iPadOS, and macOS to communicate with other Apple users, so chatting with Android-using friends means SMS texts, third-party messaging apps, and third-party video chat services. However, Apple is breaking boundaries with iOS 15 so that we can FaceTime with Android, Linux, and Windows users.

Apple seeded the second beta for iOS 14.7 today, Wednesday, June 2. The update (build number 18G5033e) comes two weeks after Apple released the first 14.7 beta, and nine days after the company released iOS 14.6 to the general public.

Apple seeded developers the second iOS 14.6 beta today, Friday, April 30. The update (build number 18F5055b) comes four days after the launch of iOS 14.5, which introduced over 60 new features and changes to iPhone, and eight days after the first 14.6 beta hit developers' iPhones.

The progress Tooz has been making in the smartglasses space has been mostly kept under wraps, but the company is slowly giving us a deeper look at what it has in store for smartglasses wearers.

Apple released the eighth iOS 14.5 public beta on Tuesday, April 13. The update (build number 18E5199a) comes three hours after Apple seeded developers 14.5 beta 8, so we know that it contains little-to-no surface-level features or changes. Any changes, at this time, appear to be under the hood.

Apple's iOS 14.5 is the biggest update to your iPhone since iOS 14. The new software features over 40 features and changes, including 217 new emoji, controller support for PS5 and Xbox Series X, and battery calibration for the iPhone 11 line. Now, Apple is inching closer to the finish line with 14.5 beta 7.

Apple released the fourth public beta for iPhone today, Monday, Mar. 15. The update (build number 18E5178a) comes three hours after the fourth 14.5 developer beta, and includes references in its code to a new "City Charts" playlist feature in Apple Music.

Apple released the fourth developer beta for iPhone today, Monday, Mar. 15. The update (build number 18E5178a) comes 13 days after Apple seeded developers the third 14.5 beta, and 12 days after public testers received their third 14.5 update.

Fresh software updates can be amazing or a nightmare, but they're mostly the former since new and updated features can give your iPhone improved functionality. There are over 200 benefits in iOS 14 alone, and hopping on the iOS 14.2 beta includes new emojis and fresh wallpapers. For the longest time, however, being away from Wi-Fi meant no update for you. That is, until now, thanks to 5G.