It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.
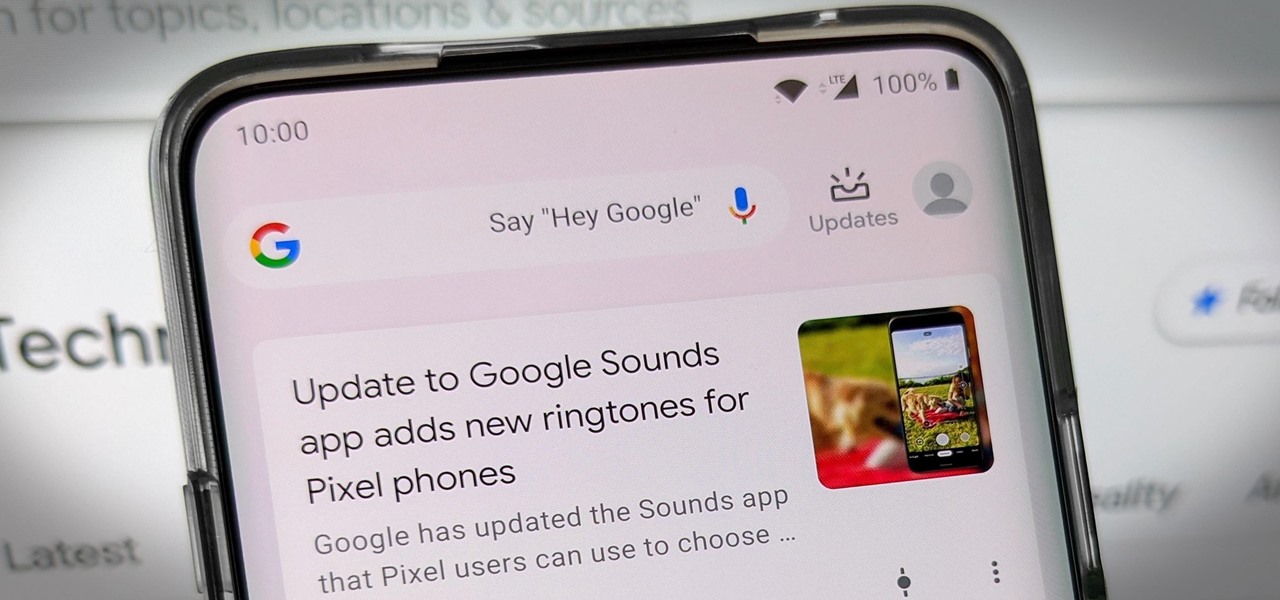
Pixels and other near-stock Android phones have the Google Feed baked into their home screen, but sadly, the default OnePlus Launcher doesn't. Even more disappointing is the fact that the OnePlus Launcher actually has the Google Feed code built into it, but it's not activated. Let's change that.

Apple revealed its newest line of iPhone models on Tuesday, Sept. 10, at its "by innovation only" event in Cupertino. While the release date for iOS 13 wasn't announced at the event, Apple issued a press release with the date. If you missed the event, you can still watch it from your computer, smartphone, Apple TV, and any other device that YouTube works on.
Apple revealed three new iPhone models on Wednesday, Sept. 12, at its "Gather Round" event in Cupertino, as well as announced the official release date of iOS 12, its newest mobile operating system. If you missed it and want to watch the full event, here's how to do it on your computer, smartphone, or Apple TV.

There's one thing that I've always liked about iPhones, and that's their centered digital clock in the status bar at the top of the screen. On Android, it's always on the right side by default, and there's no easy setting that lets you just change it to the center position. But if you have a Google Pixel XL, there's a simple modification you can perform to get exactly that—a centered status bar clock.

Depending on your device, Android's power (aka restart) menu can range from utilitarian and boring to almost completely useless. Some devices don't even allow you to reboot, let alone reboot to recovery mode or Fastboot, and for such a centralized menu, the glaring lack of Material Design seems like a serious oversight.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

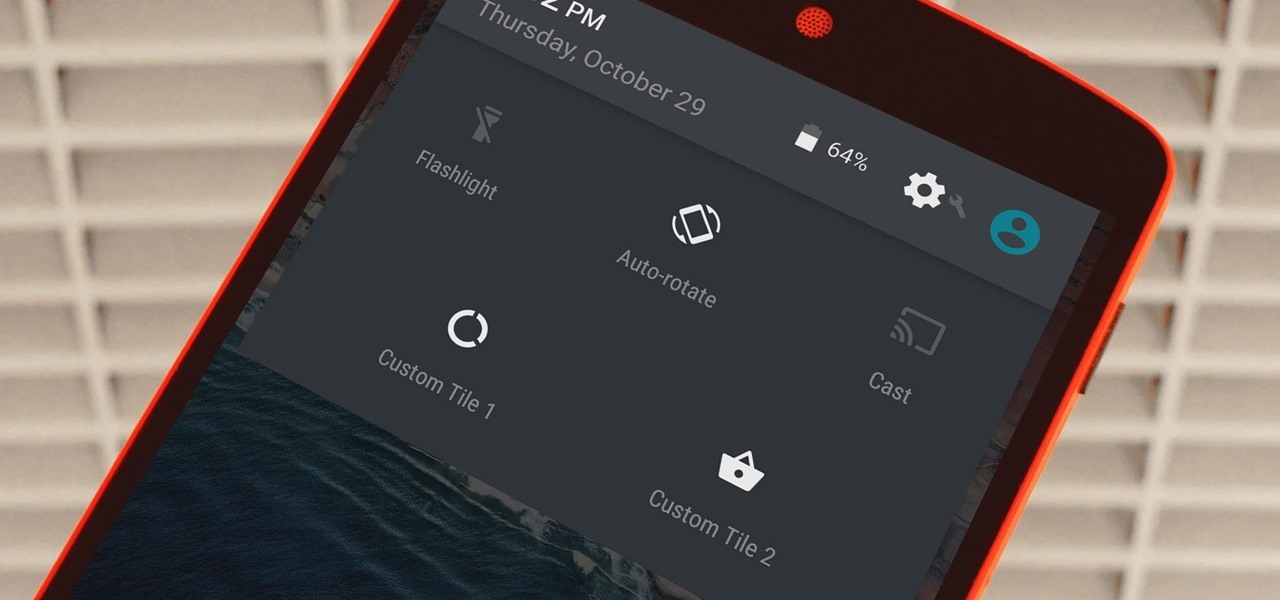
Android's Quick Settings menu is quite handy—just swipe down with two fingers from the top of your screen and you're ready to toggle several different system settings on or off. It got even better with Android 6.0 Marshmallow, since you can even use the hidden System UI Tuner to rearrange and remove your Quick Settings tiles now.

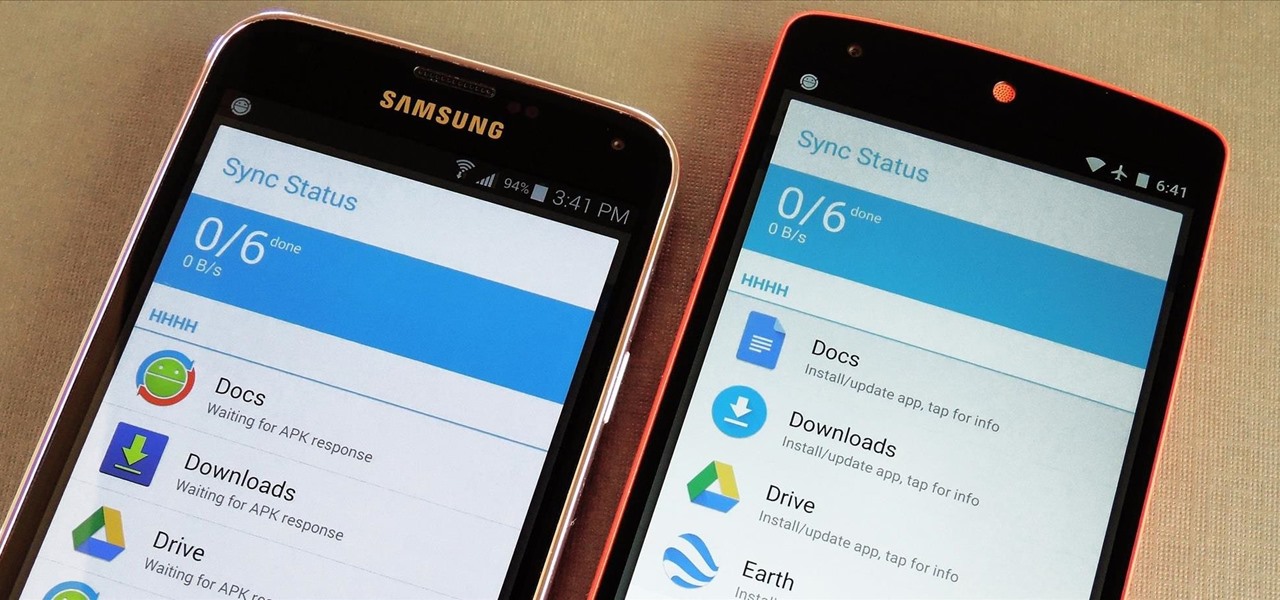
If you own multiple Android devices, you're surely familiar with the struggle of keeping apps and games in sync. While games with proper Google Play Games support will indeed sync progress across your phone and tablet, many developers neglect to include this feature in their wares.

Android's new Material Design language is truly a thing of beauty. Slated to make a full debut alongside the upcoming Android "L" release, the vision and simplicity of this UX design recently won Gold Prize at the annual User Experience Awards.

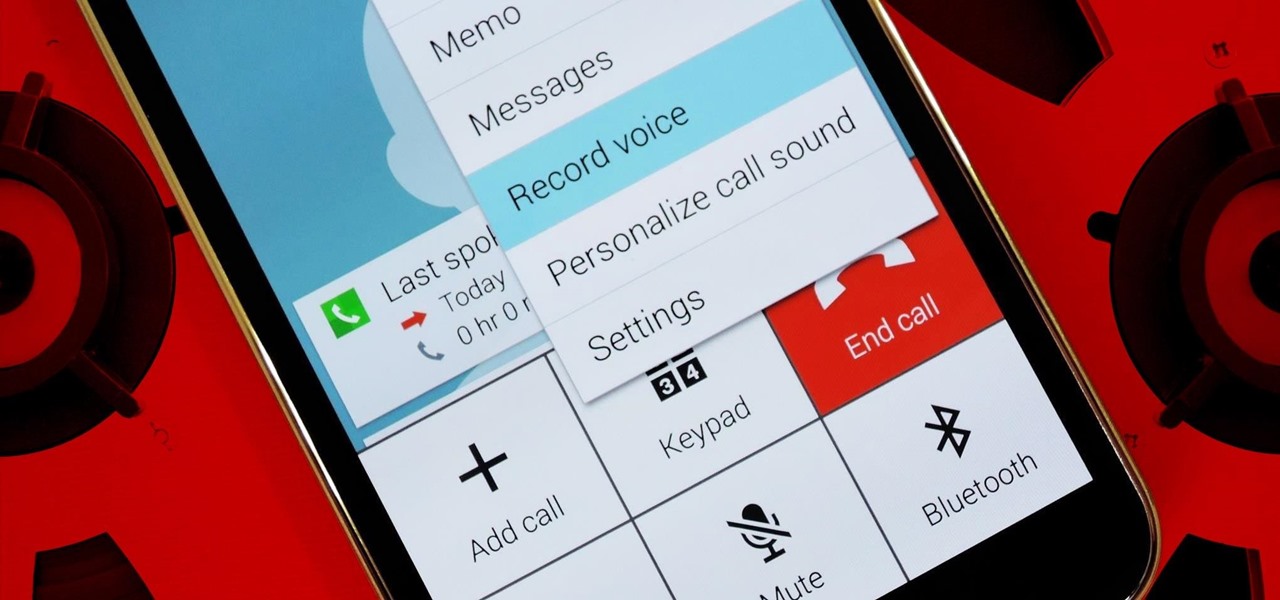
Before your carrier got its grubby little hands on your Galaxy S5, there was less bloatware installed and more functionality offered by the Samsung flagship device. Case in point: the GS5 that Samsung designed was capable of recording phone calls, yet the one that you own probably isn't.

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.

Don't be too disappointed if you don't have the spiffy new Kindle Touch, there is an up side. The benefit to owning the older (duller) models is that the firmware remains the same throughought generations, so the hacks retain their usefulness. This has given the modding community for Kindle a bunch of time to flourish, with tons of great code, hacks and homebrew. Today's Null Byte is going to show you how you can root, and then remove the crappy original screensavers that come installed on th...

In this how to video, you will learn how to set up a tone arm on a record player. First, you will notice the counter weight at the other end of the tone arm. Remove this first. Set the dial set to zero and have the lever pushed forward. Slide it on and lift the arm off of its rest. Play around with it until the arm floats. The next thing to do is to balance the cartridge. Many cartridges have different weight requirements. If you do not have the weight set up behind the arm, you cannot use di...

Still got stock? Many factory installed exhaust systems not only sound anemic, they actually are because they scrub power. The designers who are given the task of producing these pipes are often handcuffed by several different requirements that add up to one big compromise. Exhaust engineers are required to build systems that are quiet and that meet certain types of emission standards, but not all of the design concerns are driven by government regulations. Some are based on a perception of w...

Check out this video tutorial to see how to use the BD Genie Safety Lancet blood sampler device. BD Genie Lancets are high quality, safety-engineered, single-use capillary blood sampling devices. They offer a permanently retractable blade or needle feature that minimizes the possibility of injury or reuse. BD offers a full range of blade depth and needle gauges for sufficient blood volume in multiple sample requirements. All Genie's can be used in conjunction with BD Microtainer Tubes.

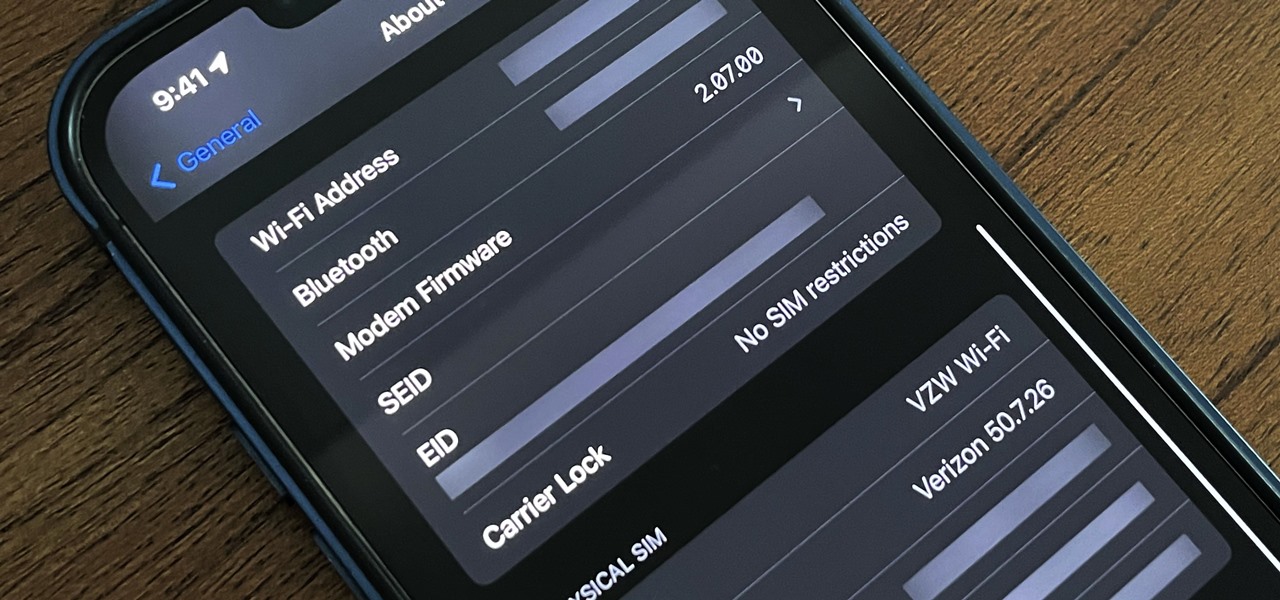
If your current cellular provider costs too much, has poor reception in your area, or doesn't support features you'd like to use, switching to another carrier is the obvious move. But can you bring your current iPhone or Android phone?

Stadia is a lot like an Xbox or PS4, except there's no console — the games just stream from Google's servers to your phone, computer, or TV. But Stadia is limited to Pixel phones for right now, and when Google does expand support, it will still only be for select phones. Thankfully, there's a workaround for that if you're rooted.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

With beta testing coming to a close, it's quite likely we will see the stable Android Oreo OTA roll out for the Galaxy S8 in late January. Yesterday, a Reddit user posted a link to an official Oreo OTA build for the Galaxy S8. We've already detailed everything that's new in this stable build. Now, let's take a look at how you can install the update on your device.

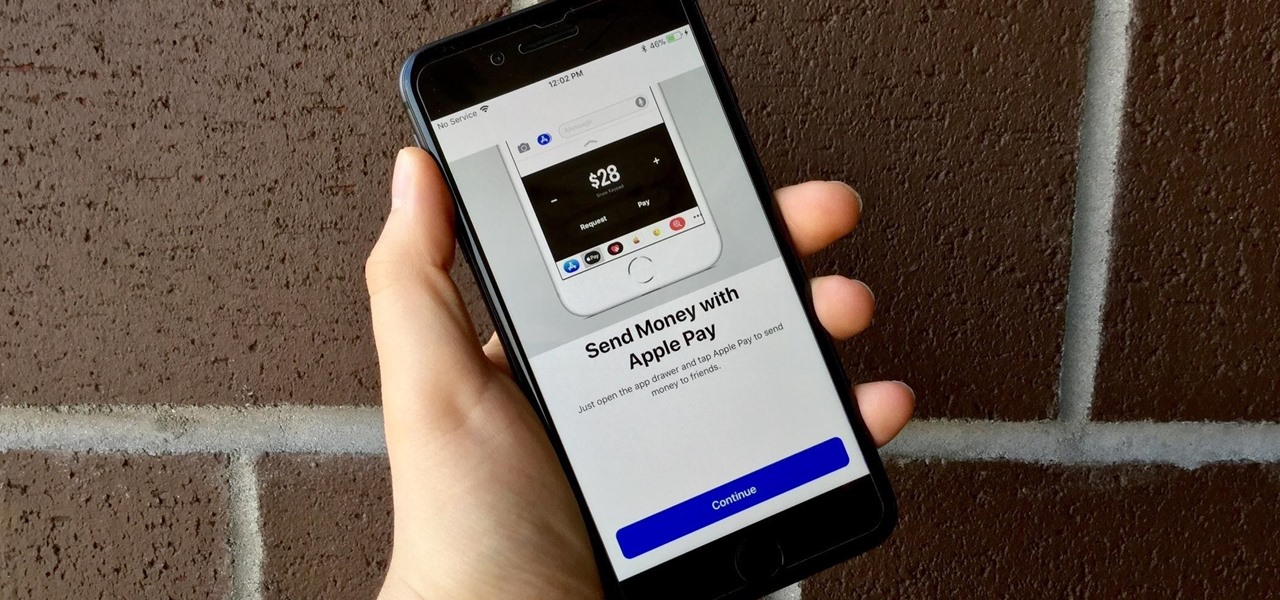
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

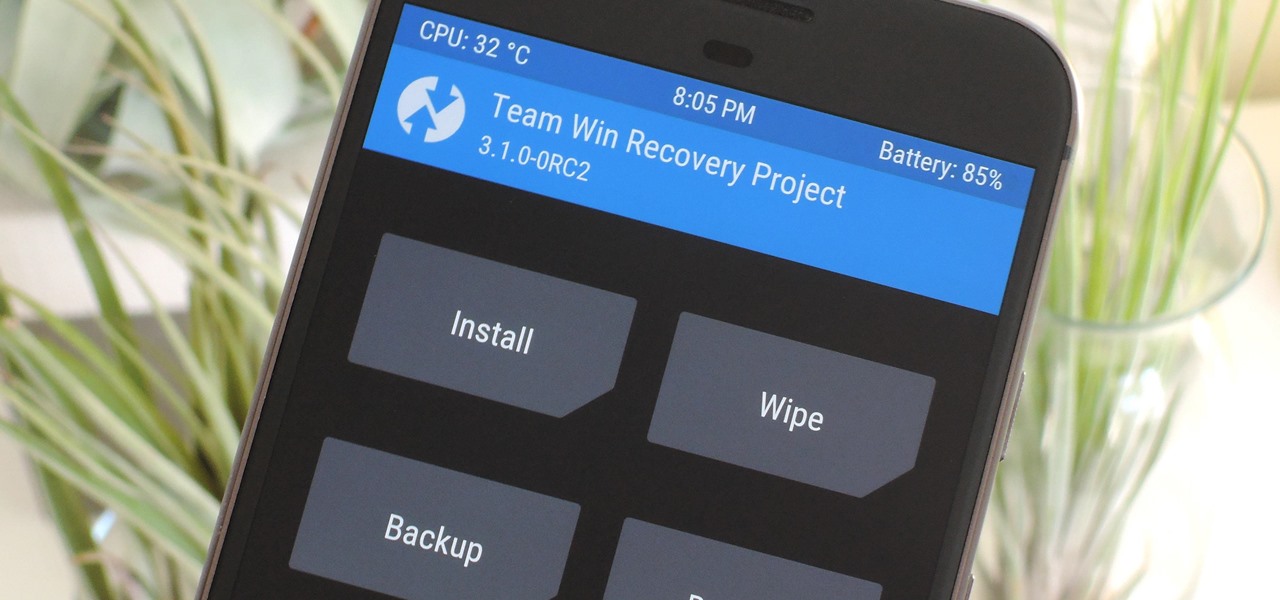
When it comes to modding Android, root gets all the glory, but a good custom recovery is really the only thing you need. Not only does it allow you to back up your entire phone, install flashable ZIPs, and load custom ROMs like LineageOS, but a custom recovery will even let you root your device. For years now, the only custom recovery worth mentioning has been Team Win's TWRP.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.

Seeing that wonderful blue verified badge on Twitter really adds something to your public persona, doesn't it? That's why, when I found out that the average person could get verified on Twitter with the right tools, I jumped on the chance to add that little blue check to my own personal account.

The V20 is an amazing phone from LG powered by Android. Packing impressive features such as a removable battery, expandable storage, and the latest Android version straight out of the box, the V20 is a tough phone to beat.

If you're running iOS 10 or lower, there is no built-in way to make a screen recording on an iPad, iPhone, or iPod touch directly from the device, but that doesn't mean there isn't a way to record your screen at all.

Video: . Hi, this is a quick demo about how to backdoor executables (software) sent over HTTP using MITMF, backdoor factory

A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unlock your smartphone.

For those of you who've already gotten Beta Preview or Developer Preview access to Mac OS X 10.10 Yosemite, I highly recommend installing it on a separate partition on your hard drive.

With portable devices being a necessity in modern everyday life, they may be subject to overuse, improper charging, or normal wear and tear. For those people who carry around their smartphone or iPod with them all of the time, how many times have you been out and about just to have your portable device die on you?

There are a lot of things on your computer that can reveal information about you when you are surfing the Internet. If you are like me, then you will do anything to maintain your privacy and prevent those little leaks of information from happening. Here's a list of a few of the "threats" that can reveal information about you:

It takes talent and training to drive a semitrailer. See if you have what it takes to operate one of these rigs on the open road.

I feel like doing a bit of chemistry today, how about you? To my knowledge, thermite is the hottest burning man-made substance. Thermite is a pyrotechnic composition of a metal powder and a metal oxide that produces an exothermic oxidation-reduction reaction known as a thermitereaction.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

While there are completely legitimate reasons to use Bitcoin, it's also used by terrorists, drug dealers, and other shady people that need to be investigated. That's where SpiderFoot comes in, which has a command-line interface to search for Bitcoin wallet addresses on a website and query the balances associated with them.

For the past five years, Apple has been hosting live media events in September to reveal new Apple products and the stable release for its latest operating systems. This year is no different, and it has a Sept. 15 date, but it may not be the only event coming up before the end of 2020.