Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

If you're anything like me, your day doesn't start until you've sloughed away your grogginess with a scalding hot shower. That perfectly-heated water can clear stuffed sinuses, relax the muscles, and make pretty much anyone feel squeaky clean. However, a cold shower can do even more for you if you can stand the low temperatures.

We've all walked into a restaurant with the best of intentions only to order something absurd, like a cheese-injected burger topped with bacon on a brioche bun. It's delicious for the few minutes it takes to eat the thing, and then you're left with a bellyful of regret and an inability to directly look at the numbers on your scale. Turns out that getting yourself to make healthy choices isn't as hard as one might think.
Both professional and home cooks have been rinsing raw chicken and turkey before cooking it for what seems like forever. It's one of those divisive practices—either you do it or you don't, and people tend to be rather opinionated on their stances.

Artists discovered the almighty vanishing point during the early Renaissance and haven't stopped using it since. The genius of the vanishing point is that it gives a three dimensional quality to a two dimensional space, meaning increased depth perception and more believability.
Want to learn about hacking Plock? You've come to the right video. Using Cheat Engine to hack Plock, you can do just about anything.

Swing dancing dates back to the 1920's, where the African American community, discovered the Charleston and the Lindy Hop, while dancing to contemporary Jazz music. The term "Swing dancing" is used to refer to one or all of the following swing era dances: Lindy Hop, Charleston, Shag, Balboa and Blues and extends to include West Coast Swing, East Coast Swing, Hand Dancing, Jive, Rock and Roll, Modern Jive, and other dances developing in the 1940s and later.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

People infected with HIV take many different types of pills every day to decrease the amount of virus in their body, live a longer and healthier life, and to help prevent them from infecting others. That could all be in the past as new clinical trials testing the safety and effectiveness of a new type of treatment — injections given every four or eight weeks — look to be equally effective at keeping the virus at bay.

Whether or not a microbe is successful at establishing an infection depends both on the microbe and the host. Scientists from Duke found that a single DNA change can allow Salmonella typhi, the bacteria that causes typhoid fever, to invade cells. That single genetic variation increased the amount of cholesterol on cell membranes that Salmonella and other bacteria use as a docking station to attach to a cell to invade it. They also found that common cholesterol-lowering drugs protected zebrafi...

Windborne microbes shifting in the snows of the great ice sheet of Greenland may be able to neutralize some of the industrial contaminants oozing out of the melting ice.

Significant strides have been in the race to find antibiotics to treat superbug infections — those caused by bacteria resistant to the antibiotics used to treat them. Now, an international team of scientists has discovered a new antibiotic produced by a microbe found in Italian soil.

In the US, ticks can spread several pathogens in one bite. A new test offers physicians the ability to identify what infections ticks are carrying and can detect if one of the pathogens could be the spreading Powassan virus.

After California college student Luis Ortiz blacked out and was taken to the hospital in 2015, doctors were startled to discover the reason his brain was swelling—a one-centimeter long, wriggling tapeworm living within a ventricle in the middle of his brain.

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.

Like in the original Black Ops, there are a bunch of funny and cool Easter eggs built into Call of Duty: Black Ops 2. Most have been discovered, like the Atari arcade invincibility on Nuketown 2025, but perhaps you didn't know about Thor's hammer?

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

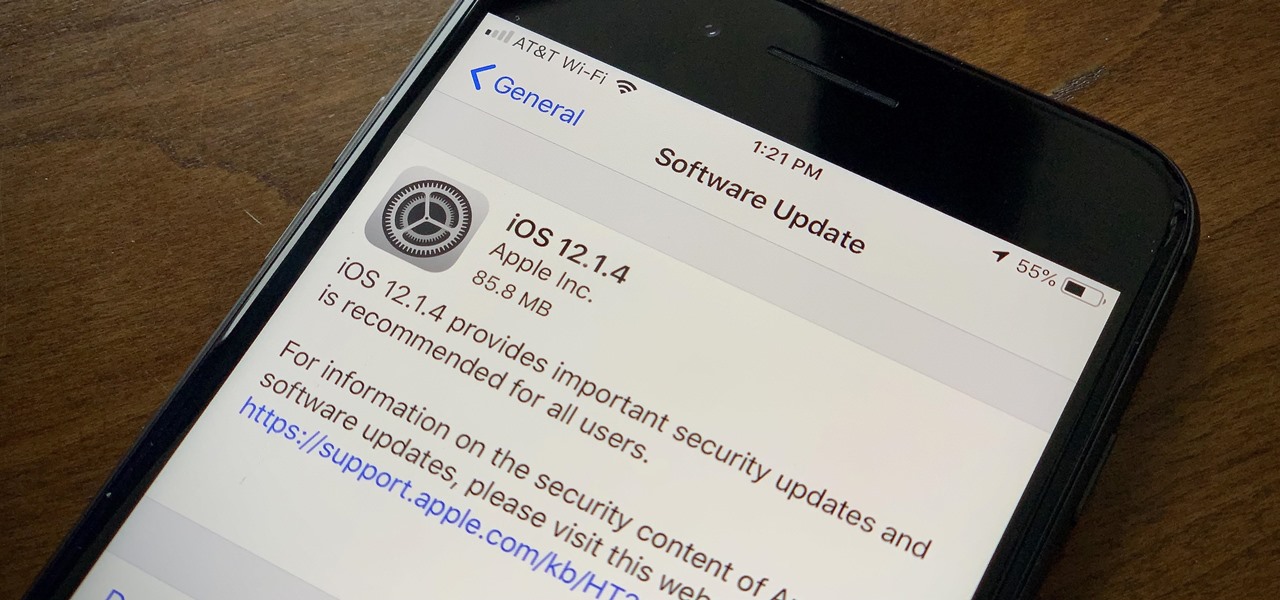
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

The cosmetics industry faced a rude awakening on Friday as beauty behemoth L'Oréal gobbled up ModiFace, one of the leading providers of augmented reality technology to the cosmetics industry (price details for the acquisition were not disclosed).

IFTTT (short for If This, Then That) is an amazing piece of software that automagically links actions on your phone with online services and real-world objects. For example, an applet could read: "if you come home, then turn on Wi-Fi." IFTTT goes further than just using simple smartphone functions, though — thanks to applets, it's fully configurable with a ton of smartphone apps.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Some types of bacterial infections are notoriously tough to treat — and it's not all due to antibiotic resistance. The bacteria themselves are rugged and hard to penetrate with drugs.

The body's usual response to a bacterial infection in the blood — called sepsis — takes time. It requires a carefully orchestrated sequence of events that gets the body's immune system ramped up to deal with the invading bacteria.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

The "Discover" tab in the latest version of the Google Home app has a new tip that says multiple users are now supported. Google Home uses a built-in speaker and microphone combo to give users access to smart search, a personal assistant, and smart home controls. This addition has the potential to make the voice-activated speaker powered by the Google Assistant much more efficient for households with more than one user. However, it seems that Google wasn't quite ready to announce this new fea...

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

We've already taught you how to clench your fist to make healthier food choices, and how to make sure you eat healthily at a restaurant, but it turns out there are even more mind hacks we can use in our never-ending quest to control our appetites.

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

Released last year for iOS devices, Frontback is a simple photo-taking and sharing app that not only snaps a picture of what's directly in front of the camera, but also behind it, which is to say, a selfie.

Hello! I invite all the readers, interested in space, to discover the origin of the names of the planets in our galaxy. Just simply follow my words,... Step 1: Planets and Stars

A continuation of my earlier science testing in Minecraft, I worked on a few things requested and retouched on TNT as there was suggestion of possible (and confirmed) altered circumstances.