Some bacteria can already do it—generate electric current, that is—and those microbes are called "electrogenic." Now, thanks to the work of a research group from the University of California, Santa Barbara, we know how to easily turn non-electrogenic bacteria into electricity producers.

We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

A recent study underscores a connection between climate change and infectious disease, raising concerns about our quickly warming planet.

Sleep lets our body processes rest and restores us for the next day, so a bad night's sleep can ruin the following twenty-four hours and even make us feel sick. Now, new research published in the journal Sleep cements the idea that loss of sleep actually leaves us vulnerable to sickness.

Most of us equate feeling cold with catching a virus—but we've also heard plenty of debunkers proselytizing that being cold isn't what gives you the flu.

A terrifying antibiotic-resistant superbug, one thought to only infect hospital patients, has made its debut in the real world. For the first time ever, the superbug carbapenem-resistant Enterobacteriaceae (CRE) infected six people who hadn't been in or around a hospital in at least a year, and researchers aren't sure how they got infected.

Have you ever wondered what makes a healthy vagina? Bacteria play an important role in vaginal health. If you've ever had your vaginal microbiome—the bacterial community that lives in your vagina—wiped out by taking antibiotics, you probably are well aware of that.

Editor's Note: The research described in the article below has been criticized and any conclusions based off this research should be examined with a skeptical eye. The article has been edited to reflect these issues.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

Naps provide some serious mental and physical benefits, but not if they last too long or occur too late in the day. Ideally, you want to awake from a nap feeling alert and refreshed enough to attack the rest of your tasks with renewed zeal, but not energized to the point where you can't get to sleep at night. Alas, most of us don't know these tricks and end up messing with our sleep cycle (guilty).

Most days, getting through an eight-hour work shift is a struggle. There are a million places you'd rather be, and none of them include your desk. It's difficult to find the motivation to tackle the growing number of emails in your inbox when your mind is back at home, comfortable in front of your gaming system.

I have an embarrassing habit: I type with six fingers. Just as your grandma pecks at the keyboard with her two index fingers, I rely solely on my index, middle, and thumb fingers only. But it's not as slow as you think, and I'm not the only one out there that does it.

In this video tutorial series, DJ James Zabiela shows how to use effects to enhance your DJ set, utilize a feedback loop, and discover new music. In the second half of the series he shows how to alter live vocals, incorporate a few of his signature moves, and edit digital scratches into your DJ set.

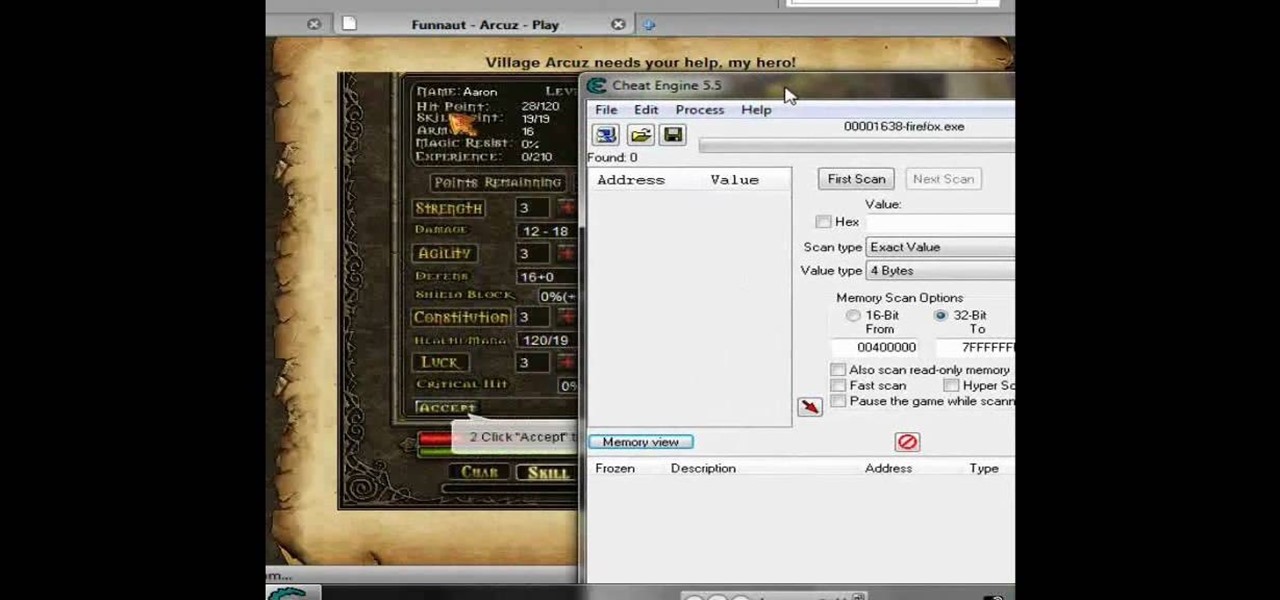
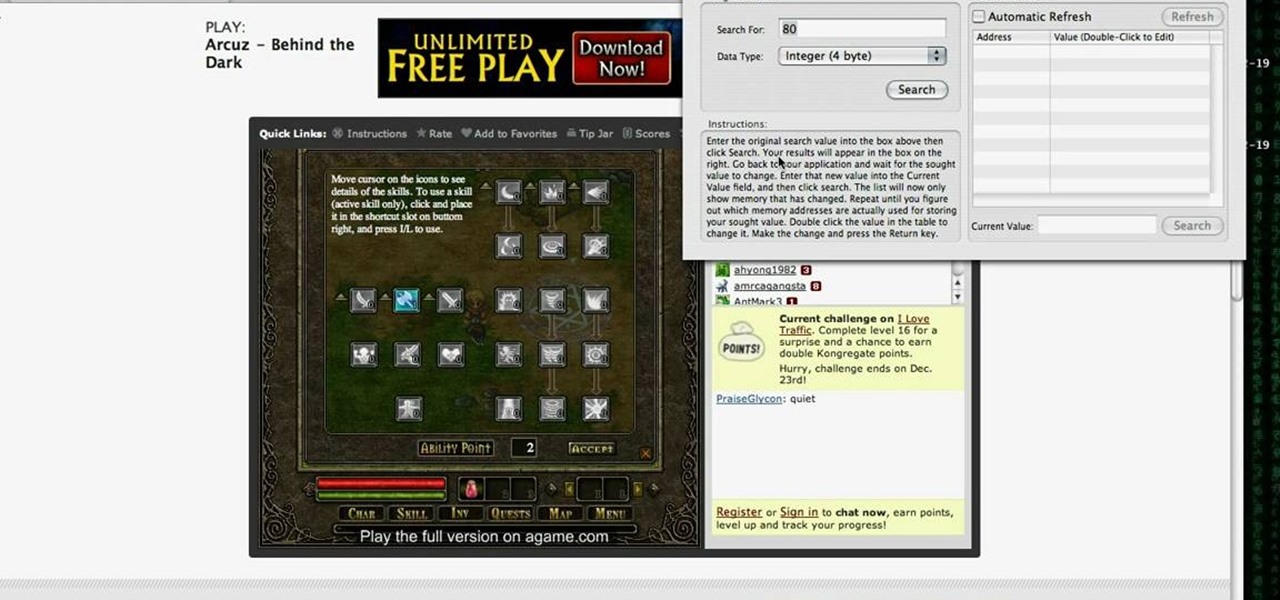
Play Acruz online and hack it, too! With this handy hack, you can cheat your stat points, levels, and money. You just need Cheat Engine.

If you want more money, character points, and skill points on Arcuz online, then this video should solve your dilemma. Just use Cheat Engine.

Looking to give a personalized gift for a birthday or for the holidays? How about a personalized bar of soap, specific to your friend or family's style? In this episode of ThreadBangers's Decor It Yourself, Meg visits Bobbie Thomas, an editor for the "Today Show" and learns how to make your own soap, and how to customize it to be just about any color, shape, or size!

Ever desired your very own masquerade mask? ThreadBanger takes us through the fun, multiple steps to acquire your very own custom-fit plaster mask! Materials needed include plaster wrap cloth, water, scissors, petroleum jelly, spray paint (in your color choice), sand paper, paint sealer spray, and decorative additions to personalize your mask! This project will need to dry overnight, so be sure to leave enough time before your party or event.

Steal Lady Gaga's eccentric look from MTV's 2009 VMA Awards for your next big costume party with help from ThreadBanger. You will need some poster board, red spray paint, flesh-colored stretch fabric, an excessive amount of red lace, sewing skills... and about four hours. Blonde ratty wig not required, but a big plus!

Ready to get into custom hat-making? Be your own milliner, with the tips from this video fashion lesson. In this video episode, Rob and Corinne hook up with Hat make Victor Osborne for a super DIY lesson on how to make Hat Molds on the cheap.

The Newport Harbor Lawn Bowling Club would like to help you learn how to lawn bowl. Just watch this great video introduction to the much under-appreciated game of lawn bowling.

Got some information you want to circulate quickly and extensively? Learn what it takes to get people to pass it along.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

The Google Feed is a great source for relevant news articles from your search history, package delivery updates, and much more. Now known as the "Discover" page, many Android users turn to this useful menu on a daily basis. However, as Google recently pointed out, the all-white theme is not ideal for battery life, nor is it easy on the eyes at night.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Apple continues to build its augmented reality hardware and software team in stealth mode. The latest addition comes via the hiring of a former DAQRI user experience designer and VR app developer.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

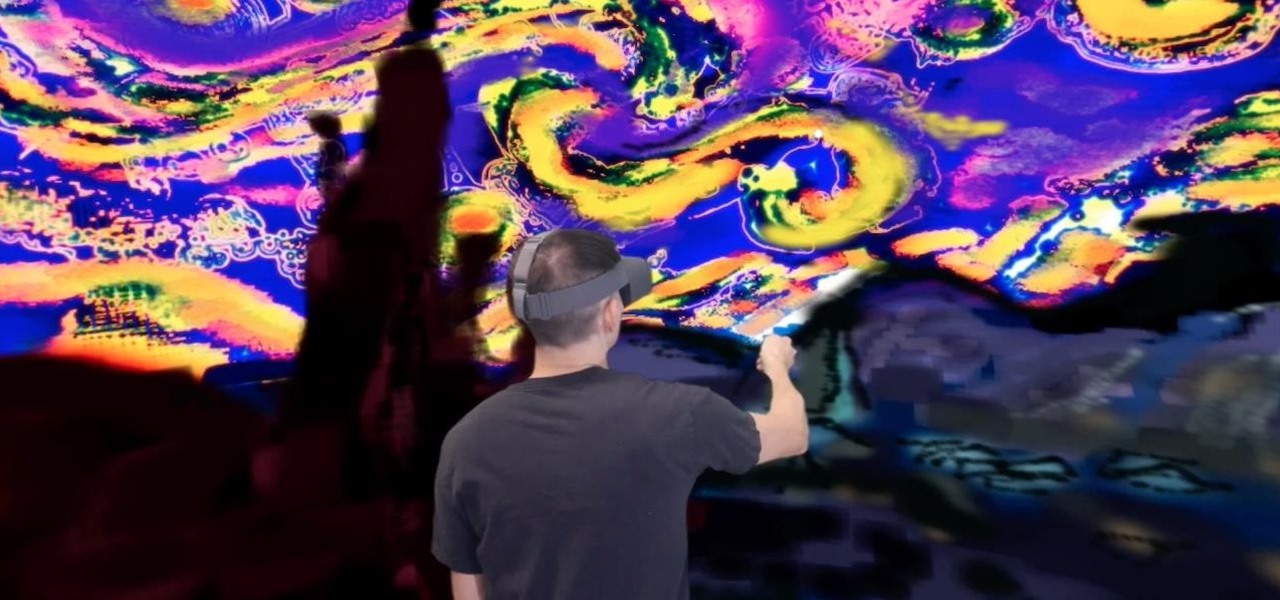
The research team at Google has found yet another way for machine learning to simplify time-intensive tasks, and this one could eventually facilitate Star Wars-like holographic video.

Seeing your baby for the first time via ultrasound is an exciting moment for new parents, but a new augmented reality twist on the experience could make the experience even more powerful.

A camera app demo that uses Apple's ARKit has been blowing up on Twitter recently and it very well might be the future of how we take pictures with our iOS devices.

The best go-to method for reducing your risk of infection is to wash your hands. Next time you reach for the soap, here is some news you can use.

While no longer native to the United States, hospitalization from malaria occurs in this country more than most would believe. Why is that, and what can you do to protect yourself when you travel abroad to regions where malaria is active?

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.

Exposed to hormones, pharmaceuticals, and other chemicals, the beautiful wild fish in Canada's Grand River have taken on some pretty odd characteristics—they're turning into females. A long-term study suggests using bacteria to manage polluted water could turn the tide for feminized fish.

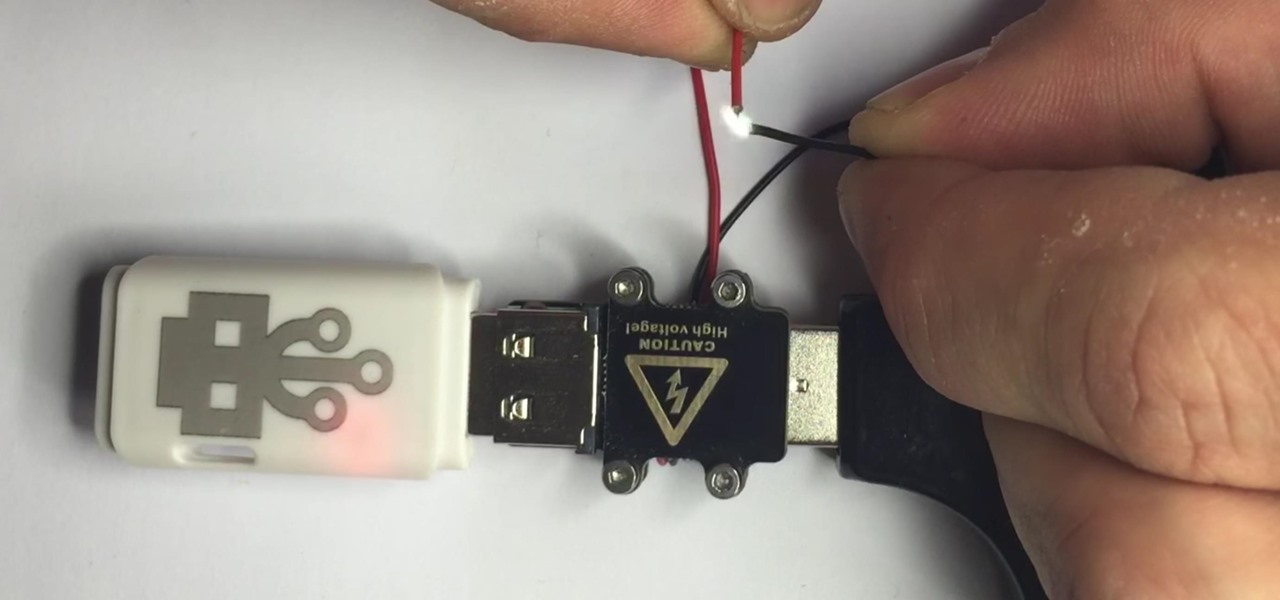
There are two types of bad USBs out there. One lets you trick the computer into thinking it's a keyboard or other USB device, and the other goes straight over malicious into computer killing territory.

Samy Kamkar, security researcher and friend of WonderHowTo, just had one of his devices featured in Mr. Robot.

Opioids, or narcotic painkillers, serve as our primary method for alleviating physical distress. They also happen to be a leading cause of death due to their addictive nature. AppliedVR hopes to introduce a safer alternative: virtual reality gaming. They utilize the existing Samsung Gear VR for the hardware, but provides specialized software that offers up a distracting experience that fosters greater pain ignorance.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.