
How To: Use the I-CubeX tennis racquet motion sensor system
Discover what happens when you hit a ball with your tennis racquet by instrumenting it with I-CubeX sensor technology! If you ever wanted to improve your game, this is the way to do it.


Discover what happens when you hit a ball with your tennis racquet by instrumenting it with I-CubeX sensor technology! If you ever wanted to improve your game, this is the way to do it.

Pharmacist Sherry Torkos shares the story on how L-theanine was discovered to be a calming and relaxing supplement.

Super Smash Bros. Brawl smashed its way into the US market this weekend, and the Mahalo video games team has been all it, uncovering the unlockable characters and discovering gameplay tricks. We took a gander by the line at the midnight launch, and spoke to Mark about what makes this game so special. Game!

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Higher-fidelity 3D content and next-generation AR experiences take more computing power than most modern AR headsets and mobile devices can handle. But Nvidia is introducing a new cloud-based solution to address that need that will stream AR content to modern devices.

Parkinson's disease, a condition that can impair movement and coordination, affects over 10 million people worldwide. And with around 60,000 Americans being diagnosed every year, we're on track to see almost one million Parkinson's afflicted Americans by 2020.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

The Association for Computing Machinery's annual Siggraph conference, taking place next week in Los Angeles, will bring researchers from around the to show off their latest innovations in imaging and display technology.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

The last time The Weather Channel showed off its broadcast augmented reality, the internet couldn't stop talking about how immersive the presentation looked, despite being shown on a 2D display.

Adding another arrow to its quiver of augmented reality acquisitions, Apple has reportedly acquired Spektral, a computer vision company with technology for real-time compositing (otherwise know as the "green screen" technique in broadcast TV and film).

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.
A new augmented reality framework from Disney Research could make it possible for fans to take selfies with an augmented reality Mickey Mouse, Darth Vader, or Iron Man that mimic the user's poses.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Although the HoloLens is still primarily the domain of developers and researchers, the device is nevertheless on the cutting edge of showing us what will be possible with augmented reality in the coming years. The latest example comes via Microsoft Japan and a new concept video that shows off how the HoloLens will be used in the relatively near future to pilot autonomous ships.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

A top executive from Baidu's telematics division believes the company will become the word leader in driverless by 2020, according to a report in today's South China Morning Post.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.
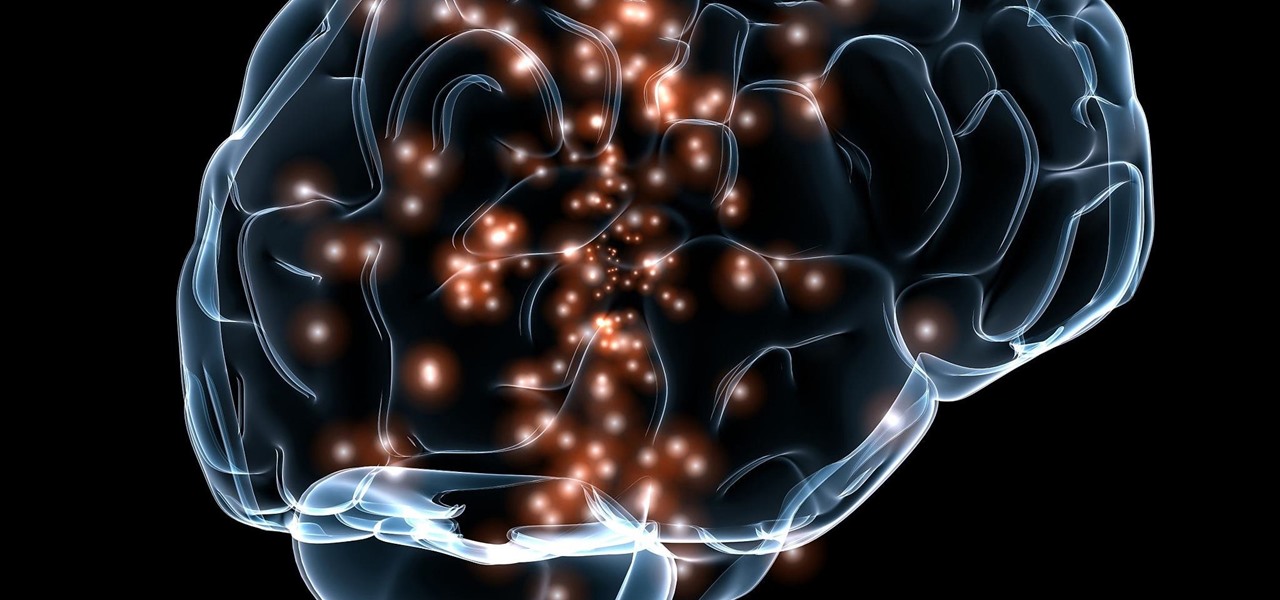
Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.
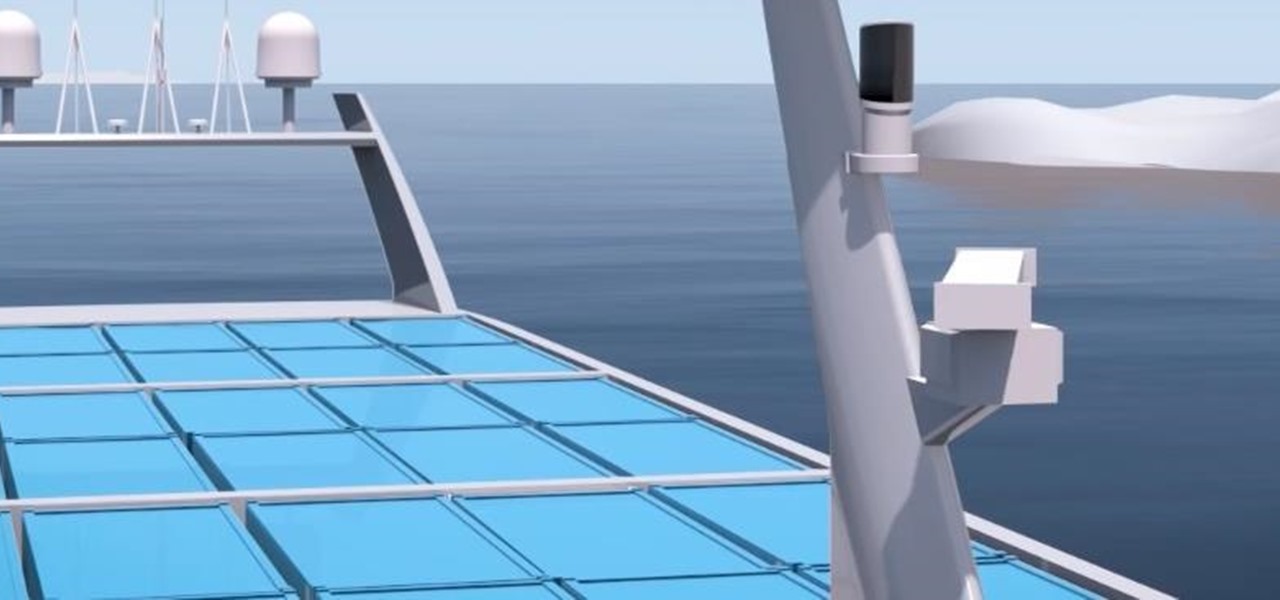
A Norwegian carrier's launch of a pilotless container ship next year could lead the way to a new era in sea transportation and shipping if successful.

For months, consumers have been itching to know whether it will be Samsung or Apple that has the first in-screen fingerprint scanner in their next smartphone. Now, reputable researcher Jiutang Pan has taken to Weibo to report that the answer is neither.

Oh, Uber. It's not often to hear your name in the news and have it mean something good. You're being sued, you're crashing, your driverless program is falling behind. But I have to hand it to you; when the world is crumbling around you, you continue to fight against it. You've even made it to Canada.

It seems like everyone wants to be flying without wings these days, and some big players in the autonomous car industry want a piece of that airborne action. Google co-founder Larry Page just invested in flying car startup Kitty Hawk, while Uber is adamant that its own-brand of flying vehicles will be zooming around the US come 2020.

In March, we wrote about the growing threat of yellow fever in Brazil. At the time, the disease had killed just over a 100 people. Unfortunately, the disease has only spread since then with many more people infected and more killed.

Just like in the Spy Kids 3D movie, US soldiers may soon upgrade their mission planning from 2D to 3D. Welcome to the wonderful world of augmented reality, US Army.

Augmented reality seems to be the talk of the town lately, with everything from glasses to furniture stores prepping to implement exciting, new AR technology. Well now, it looks like even our food is getting a makeover for the augmented reality future.
Apple is combining internal and external talent in an effort to give them in edge in the augmented reality market, though we still don't know what form their foray into alternative realities will actually take.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

Dutch police are using a system very similar to Pokémon GO on smartphones, but they aren't walking around trying to catch little pocket monsters. The purpose of this system is to give augmented reality help to first responders who may be less qualified to work a fresh crime scene. If successful, the idea of a contaminated crime scene could be a thing of the past.

We're inching closer towards the singularity—that point where technology advances to the steepest slope of the logistic function S-curve and simply skyrockets at a rate we've never seen before. Somewhere along the way, the line between humans and the tech we rely on will become blurred, and MIT's latest project might very well be a step in that direction.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

Hackers have stolen over 225,000 Apple user's account information from countries all over the world—including the United States, China, and France—in what many are reporting to be the biggest known Apple hack in history.

Security researcher Samy Kamkar, best known for his MySpace Worm, and most recently for his online calculator that can help you crack any Master Lock combination, is at it again. This time he's figured out how to break into security doors that have a motion-sensing egress system.

Today we are pleased to announce the end to the Apple vs. Android war. About a year ago, our Gadget Hacks team started working on a top-secret project to dual-boot both Android and iOS on the same phone—and we couldn't be more proud to announce that we've finally succeeded! Your phone can now run both iOS and Android—whenever you want. Right now.

With the countless daytime talk shows starring and featuring doctors, nurses, and other medical specialists, discovering new ways to live a healthy life is just a remote click away. Although their shows might draw you in with incredible facts and mind-blowing secrets to weight loss success, it's important to take each televised recommendation with a bit of suspicion—most of these familiar faces aren't exactly telling the truth.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.