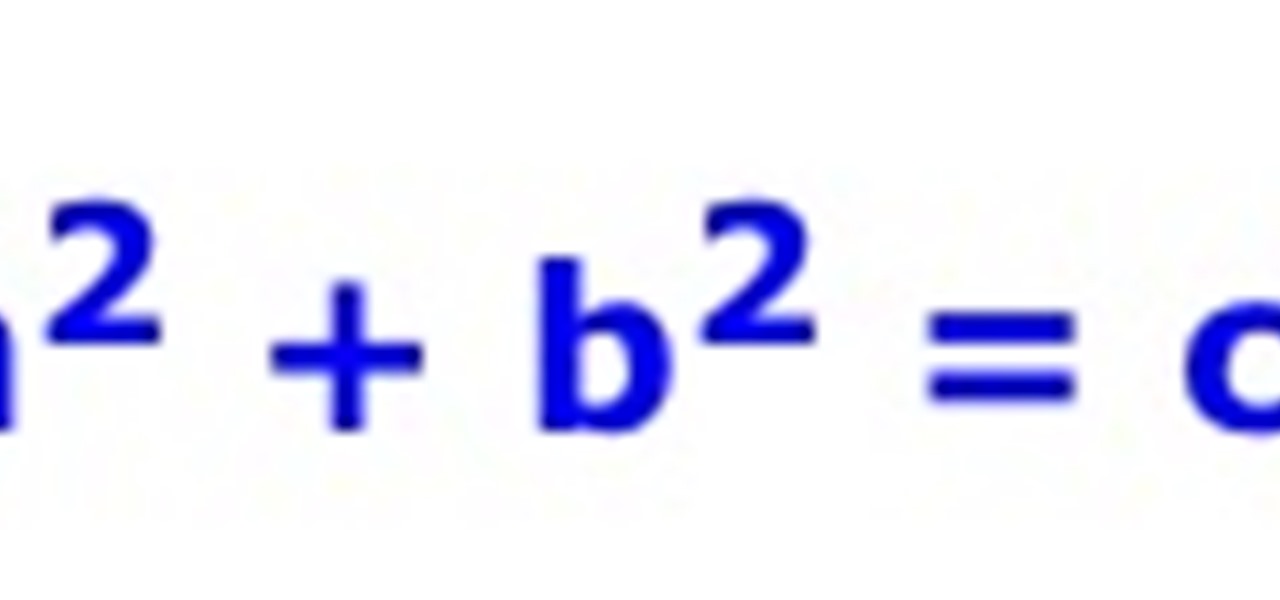One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...
If you're a Twitter user, it's a safe bet to assume that you've used a hashtag. On all social networking sites that have the capability, such as Instagram, Facebook, and Google+, the pound (#) symbol is used to mark and designate specific keywords or topics in order to make it effortless for users to connect with one another.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

In one of my previous articles, I showed off how to make water freeze into ice instantaneously. In this article, I'd like to elaborate on this, and show how a glass of water can turn to ice instantly on command. What exactly is this supernatural power? Discover the secrets to ice-bending—in real life.
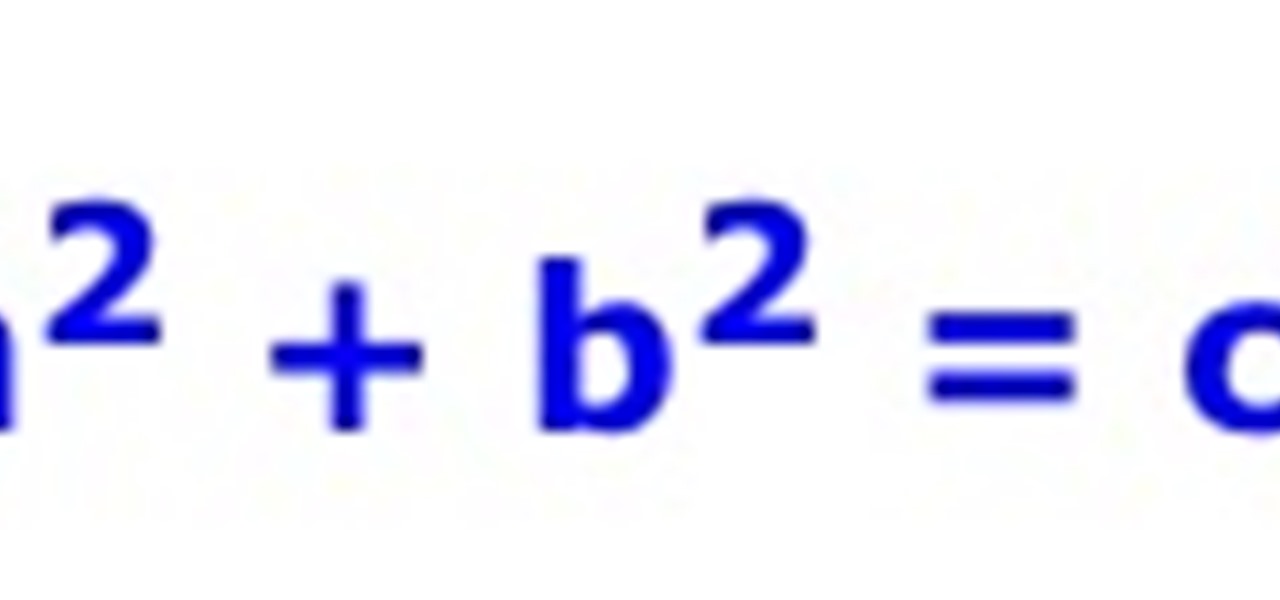
What Is Pythagorean Theorem? Pythagorean Theorem is an equation discovered by a man named Pythagoras. It can be used to determine whether or not a triangle is a right triangle and find missing lengths of a triangle. The equation is: Parts of a Triangle

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

Need to remove wrinkles from your shirt but don't want to bust out the iron and ironing board (or don't even have one)? Well, with a little bit of do-it-yourself ingenuity, you can "iron out" that wrinkly top in no time.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

Mason jars are a DIYer's best friend, nearly on par with duct tape and paper clips. Why? Because you can use mason jars for so many things besides just canning and drinking, and I'm not talking about other obvious uses like basic storage containers or miniature terrariums. I'm talking about MacGyver-style ingenuity. With a little creativity, the uses for those jars are practically endless.

Curve stitching is a form of string art where smooth curves are created through the use of straight lines. It is taught in many Junior High and High School art classes. I discovered it when my math students started showing me the geometric art they had created.

Make sure your next apartment rental goes smoothly by properly checking the property before signing a contract. This way you will avoid unexpected disappointments or problems that you were not aware off. Moving is hard enough, give yourself all the advantage you can by going in prepared.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

The year was 1947. Scientists had isolated a virus from a pyrexial rhesus monkey in Uganda and named it after the forest where the monkey lived — Zika.

Wish things were free? Well, with this hack, you can make sure all the gold is zero and everything costs nothing. How? With Cheat Engine!

Discover the art of Telescopic Pole Setup in this informative video, where we guide you through the process of preparing your pole for speedfishing. Whether you're targeting Bluegill, Crappie, Trout, or Perch, pole fishing stands out as one of the most effective methods to reel in a catch.

In this video series, let Mei-chiao Chiu teach you the beginning forms of Wushu. She explains the history of Wushu, and its importance in the world of martial arts. She shows you how to warm up and stretch before being any Wushu exercise. With her instructions, you can discover the exciting martial art form of Wushu today

In these rock and mountain climbing instructional videos, learn how to set anchors for lead and top rope climbing. Having strong anchor points is crucial to a safe and successful climb. Get professional tips and techniques on using strong rope knots to secure your climb. Learn how to rock climb with natural anchors like trees and boulders. Discover how to join anchors together for a more stable climb in unstable conditions. Watch this series and use these tricks on your next rock climbing trip.

Fabulous and creamy, make this scrumptious low-country carb stew. Follow along as Paula Deen shows you how to make it. This cooking how-to video is part of Paula's Home Cooking show hosted by Jamie Deen, Paula Deen. Paula Deen, owner of Lady and Sons, a famous Savannah restaurant, is Food Network's resident southern chef. Step inside her kitchen and discover delicious food that's both uncomplicated and comforting, like this recipe. Watch how easy this low-country crab stew is to prepare and c...

This was a busy week in the tech space. After everyone got over the major announcements of Apple's latest, we examined the metaverse through the lens of Hollywood, and then took a closer look at Facebook's first smartglasses.

From the front lines of mainstreaming augmented reality smartglasses comes the latest update from Snap and its Spectacles wearable.

The big day for Snap that resulted in the debut of brand new augmented reality Spectacles smartglasses is turning into a big week.

Google's "At A Glance" widget gives you the current weather conditions and upcoming events from your Google Calendar in a handy spot right at the top of your home screen. But on Pixel phones, this widget is permanently embedded into the launcher, so you can't just long-press it to remove it.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

Anyone looking to have a complete set of design tools at their fingertips needs to look no further than Adobe's Creative Cloud. This suite of applications is the go-to platform for creative software and is, in many ways, a must-know in fields like graphic design, video editing, and photography.

While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader. Fortunately, there is an expert guide to becoming an analyst that's now available to everyone.

Good communication is essential when managing teams and overseeing complex projects. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

Mobile privacy is one of the most pressing security issues in existence. Since we carry our phones with us everywhere we go, we need to ensure that we're safe from prying eyes.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?