Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

While the iPhone came before the first Android smartphone, every new iOS version seems to include a wealth of features already existing on Android, and iOS 17 is no exception.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

The latest iPhone update introduces big features like Live Activities and Clean Energy Charging, but those aren't the only things you'll notice different on iOS 16.1. If you build your own shortcuts in the Shortcuts app, there are a few things you'll definitely want to know about the new software. It's not a massive feature drop as with iOS 16.0, but they are important changes.
It hasn't been long since Apple released iOS 16.0 with over 350 new features, but iOS 16.1 just came out with even more cool updates for your iPhone. While some of the recent upgrades were expected, others are somewhat surprising — and there's even one that you may not even think was possible.
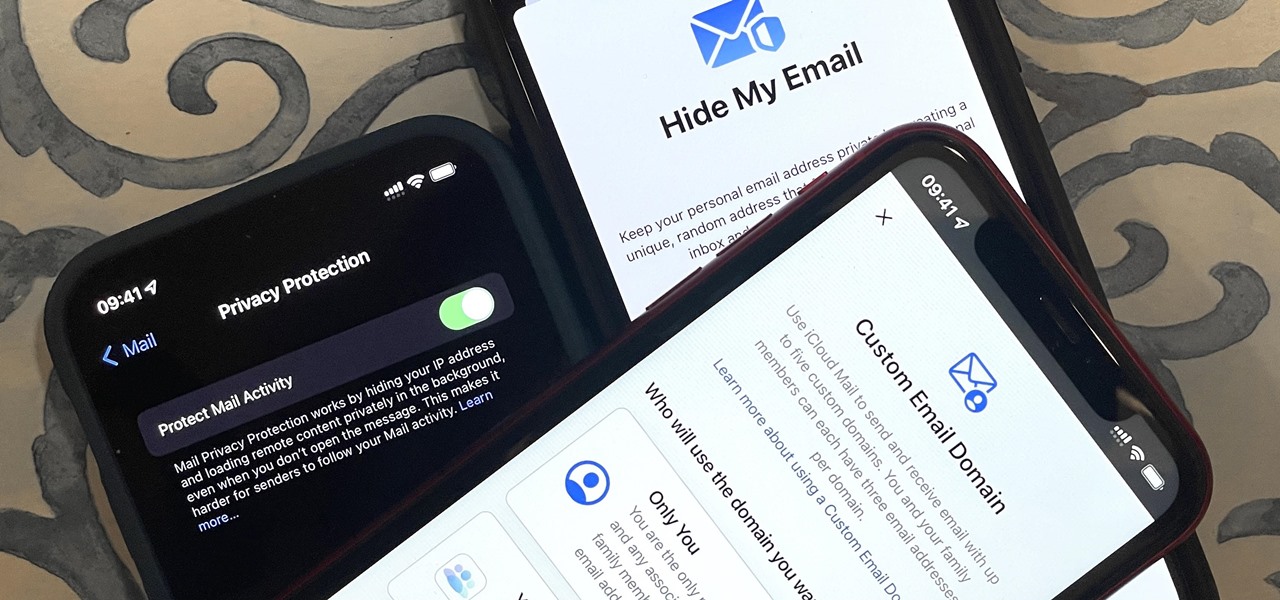
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

In these times of social distancing, video calling is becoming the technological substitute for face-to-face connections. For those who carry an iPhone, the art of video calling defaults to FaceTime, the native app on iOS that is exclusive to Apple devices. But what do you do if you or the other party is on Android?

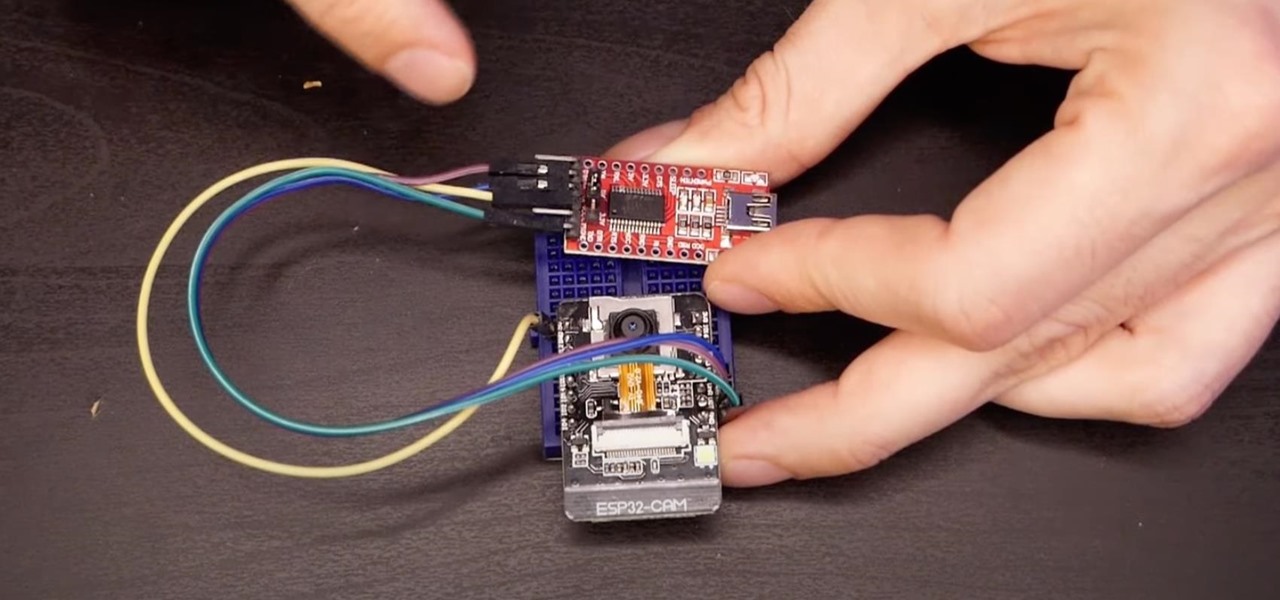
The ESP32-CAM is a convenient little camera module with a lot of built-in power, and you can turn one into an inconspicuous spy camera to hide in any room. There's only one issue: it does omit a USB port. That makes it a little harder to program, but with an ESP32-based board, FTDI programmer, and some jumper wires, you'll have a programmed ESP32 Wi-Fi spy camera in no time.

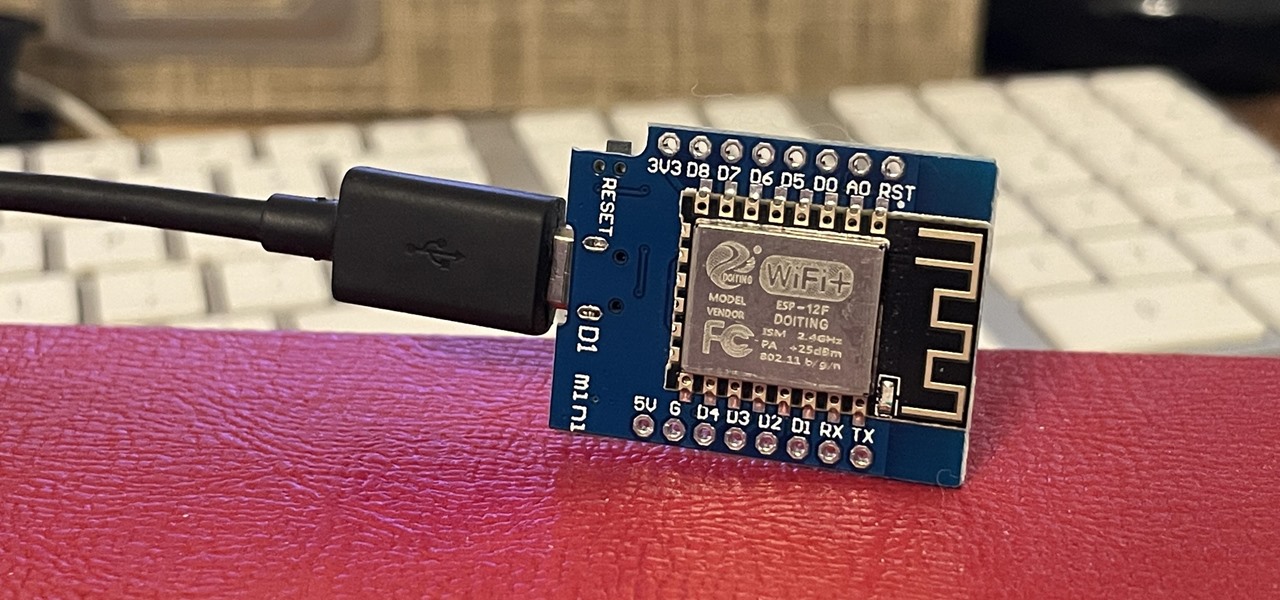
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got the best picks to slim you down to the essentials.

Apple's latest iPhone software update — iOS 17.5 — is finally ready for prime time. Released on May 13, it includes at least 32 new features and changes you need to know about, from a new game and offline news access to new wallpapers and anti-stalking capabilities.

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

Apple previewed new cognitive, speech, and vision accessibility tools for the iPhone back in May, and they've finally been realized with the iOS 17 release. But there are more accessibility features than that hiding in Apple's latest software update — and they're not just for users with disabilities.

There is a whole world of smartphone accessories out there, some of which are more quirky than others and don't get the recognition they deserve. But these sometimes strange, sometimes embarrassing products can really make life easier on your iPhone or Android phone.

Rumors about the 2022 iPhone series stirred well before the iPhone 13 models were even released. While Apple remains quiet on the next big iPhone, as it always does, we're seeing more and more leaks and reveals for the iPhone 14 series as we lead up to a likely fall release.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Apple's iOS 14.0 update has come and gone, and now we're sitting on iOS 14.2, the latest version of the iPhone's operating system. While it may be too late for you to revert to the last iOS 13 version, if the iOS 14.2 firmware is giving you problems or you're not just digging it, you can downgrade to iOS 14.1.

Adobe Illustrator Creative Suite 4, or CS4, software is a comprehensive vector graphics environment that is ideal for all creative professionals, including web and interactive designers and developers, multimedia producers, motion graphics and visual effects designers, animators, and video professionals. But having the program isn't enough; you'll need to know how to use it. In this video tutorial, you'll learn how to reshape a path outline in Adobe Illustrator CS4. Take a look. Reshape a pat...

The Displace modifier in 3ds Max acts as a force field to push and reshape an object’s geometry. You can apply its variable force directly from the modifier gizmo, or from a bitmapped image. The 3D Studio Max displace modifier works on Shapes, Meshes, Polys, Patches, NURBS. Displace is often used to make terrains or to add finer texture to 3D models with out having to model in extra texture. It can also be used in a very controlled way to manipulate geometries. With the use of procedural text...

Artist Sascha Nordmeyer presents her concept Communication Prosthesis as the “ultimate communication tool,” or the solution to self-expression. Once inserted into the subject's mouth, the prosthesis forces strange (and horrific) expressions.

If you've ever had to call a large communications company with a customer service issue, you've most likely experienced the hopelessly not-at-all helpful operator from hell. Thanks to a program on VRT Belgium, you can now experience a small sense of vengeance for tortured customers everywhere.

16-year-old Alexander Kendrick has invented a low-frequency radio that allows for cave-texting, meaning deep underground cellular communication.

This collection of instructional videos from BaseballRox will help you develop your running mechanics in the sport of baseball. These baseball videos are aimed to help young players and coaches improve their performance on the field. See how to take a lead off base and steal bases in baseball.

This how-to video explains how to set up voice communications in Second Life. This can be helpful to anyone who is confused on how to enable voice chat for this game. Set up voice chat in Second Life.

3 Effective Techniques for Following Up With Leads The follow-up phase of the sales cycle is like having a goldfish for a pet, in that it's easy to forget about it, especially compared with the excitement of finding new sales leads. This is unfortunately, though, because you can outperform your competitors by following up with leads and encouraging them to choose your business.
In my early life I was deeply impacted by the work of physician and psychoanalyst John C. Lilly. I still have my dog-eared copies of The Mind of the Dolphin (1967) and Programming and Metaprogramming in the Human Biocomputer (1968). Lilly's work, with dolphins and the development of the sensory deprivation tank, has formed the basis of movies, music and television productions.

In recent years, communication has become more intimate with the advent of applications like Skype and FaceTime, but what about the longing for actual physical contact? What if you could feel a loved one's hand, or even exchange a kiss? Impossible, right?

New to eBay? Don't worry, setting up an account and buying and selling doesn't take that much effort at all. Everyone who has an Internet connection has at one point come across eBay, to find the perfect gift for their loved ones, to find the cheapest deals on plasma televisions and computers, or to get rid of their dusty, old record album collection in their web store.
This week, researchers from Symantec shared information on the recent discovery of a new variant of the Zeus Trojan. This new variant of the popular and ever-changing banking Trojan makes use of P2P communication exclusively, making the botnet have no single point of failure and ensuring it can be kept alive and gathering data that the cybercriminal can profit from. In other words, this new variant requires no central Command-and-Control server to control the bots.

A hacker from Anonymous broke off communication with an FBI agent posing as a Symanec employee after being offered $50,000 to not publish the Symantec pcAnywhere code online. And in a not surprising turn of events... the code was released today on peer-to-peer networks.
The first and only curated page investigating google + for the healthcare, health and pharma community. For all healthcare professionals involved in communications and e-marketing for their company, charity, brand or organisation.