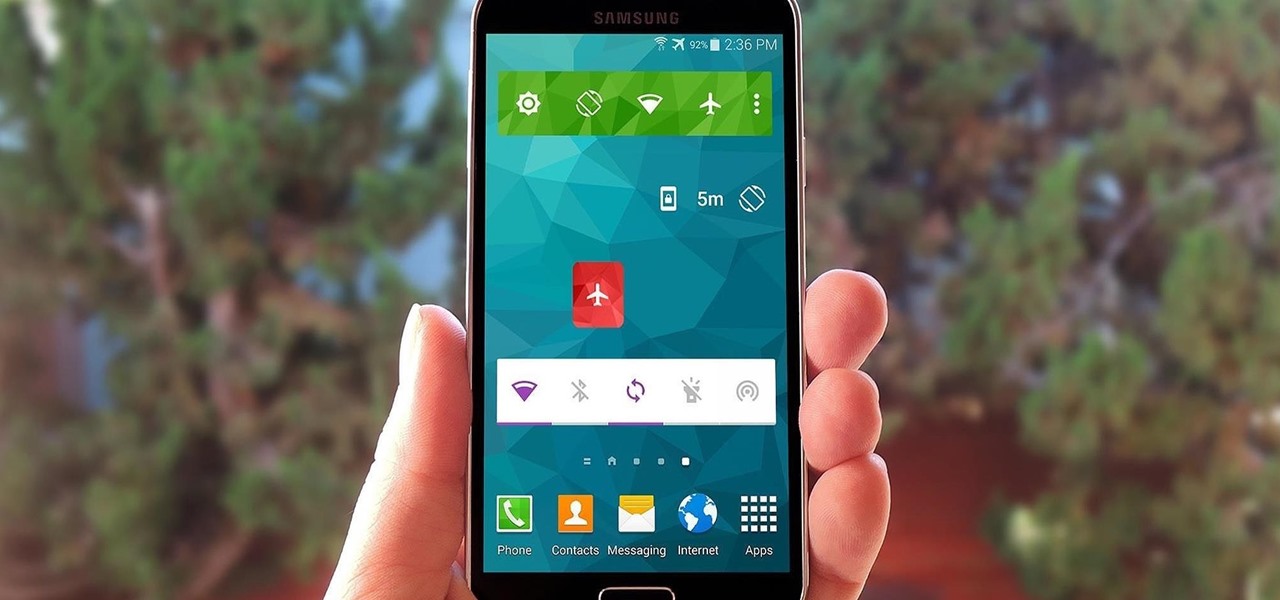
Widget toggles, or "power toggles" as they're often called, have been around for quite a while. They serve their purpose nicely as an easy way to add switches to your home screen or notification area for functions that don't come with the stock software on your device.

Shopping: you either love it or hate it. With a tight budget, shopping can become a huge headache for even the biggest shopaholic. We've all been there, and we've all given in to our impulses and bought something we probably shouldn't have. Yet strolling through the mall doesn't have to require a strong will to keep your credit card from entering a downward spiral. You just need to keep your hands to yourself.
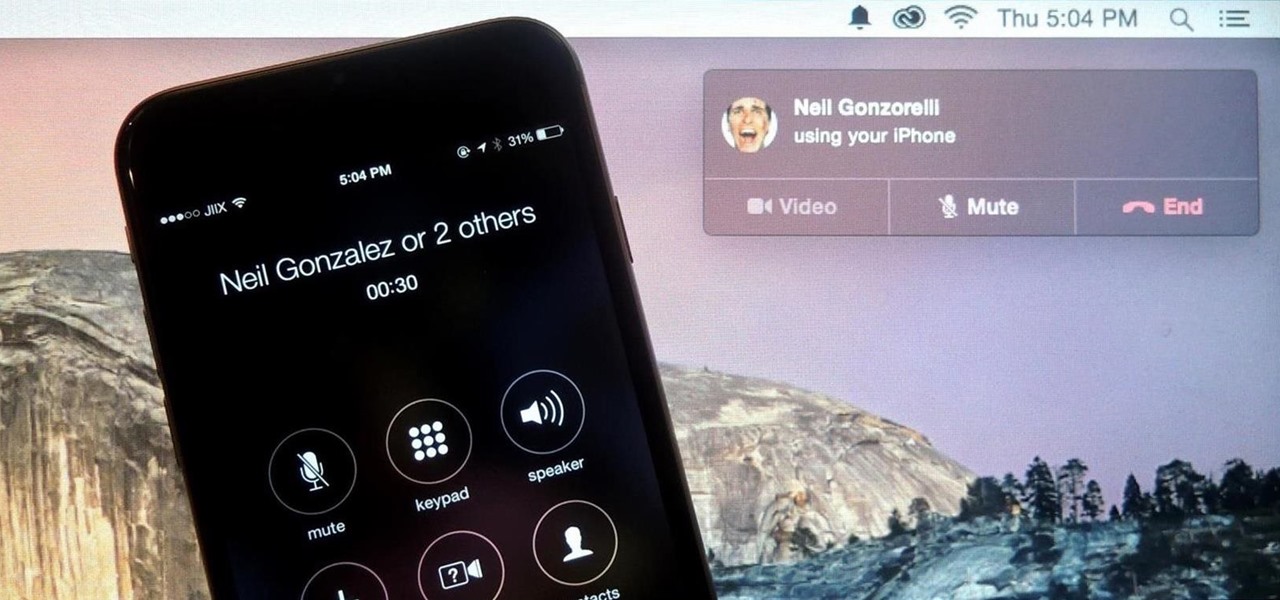
Earlier this year, Apple announced Continuity, a feature for Yosemite and iOS 8 that lets you connect your iOS devices to your Mac in order to access apps, receive phone calls, send text messages, and more while seamlessly switching between the two.

Decisions are rarely easy to make, and there are countless ways to mull your options over. You can sleep on it, pluck flower petals, make a list of pros and cons, or even follow the advice of a psychic. Yet to make the best decision possible, you might want to consider holding off until a certain time of the day—or even until you feel specific emotions. The state you find yourself in has significant impact on each decision you make.

Having someone send you flowers will almost always lift your spirits. Wilting, dying flowers, on the other hand, aren't so great to look at and smell even worse. While there are time-honored tricks to keep flowers alive longer (change the water regularly, put a penny in the bottom of the vase, and cut stems diagonally are three that come to mind), it turns out that a few items in your kitchen are pretty useful at making sure those blooms stay perky.

In 2012, VideoLan published a beta release of their wildly popular desktop media player, VLC, for the Android platform. However, because the non-profit development team did not have access to popular North American Android devices, they opted to exclude the USA and Canada from their initial release. That is, until now.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Apple announced the successor to Mac OS X Mavericks at their Worldwide Developer's Conference 2014, and it's called Yosemite. Named after California's Yosemite National Park, it will be available as a free upgrade from the Mac App Store for everyone this fall.

It's been rumored ever since the 2012 release of the Kindle Fire, and now Amazon's first smartphone is set to debut a little later this year.

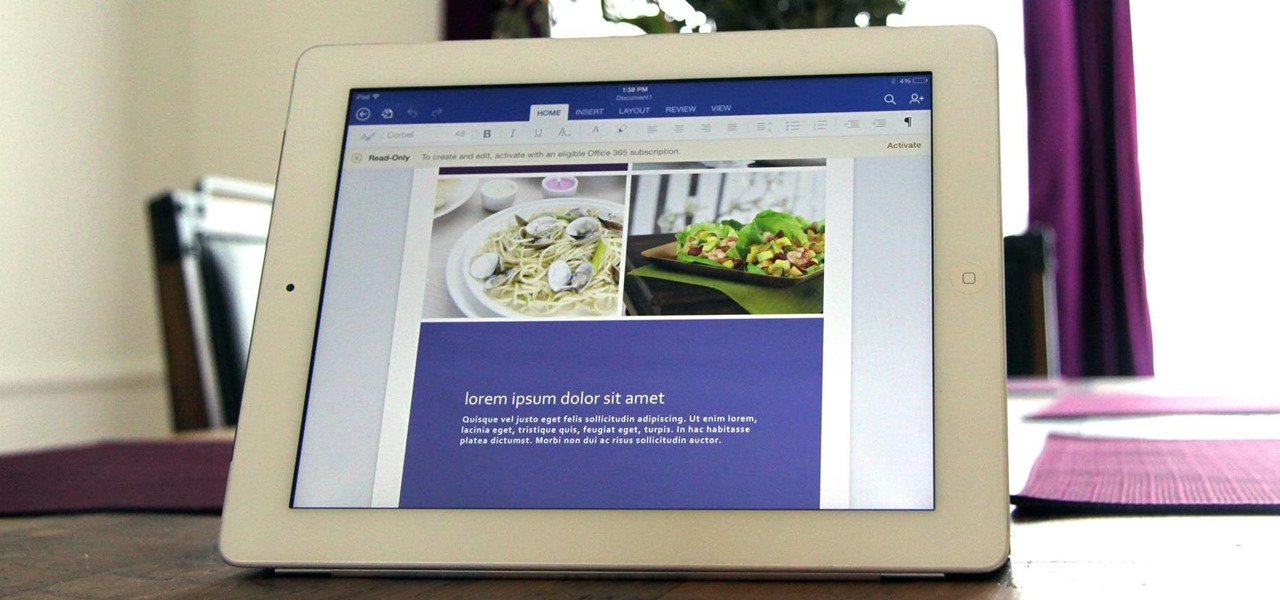
After much speculating, denying, and waiting, Microsoft has finally released their suite of Offices apps dedicated to the iPad. With increased competition and flocks of users going to apps like Quickoffice (which was recently acquired by Google) and Kingsoft Office, it was getting close to do-or-die time for Microsoft.

Photo mosaics have interested me since I was a kid. I could never understand how someone took the time and effort to make one large masterpiece out of hundreds of smaller images. Maybe I'm too daft to grasp the concept, but it seems extremely difficult. I certainly don't have the necessary skills to make my own work of art, but luckily my Nexus 7 does.

While the Galaxy Note 3 and Galaxy S4 are enjoying their official KitKat updates, those of us with Note 2s are left to play the waiting game. While we know our devices will eventually see an update to Android 4.4.2 KitKat, it's unclear when an official update for our devices will come.

Editor's Note: The claims by Vani Hari which were originally detailed in the article below about azodicarbonamide were unscientific in nature. This article has been updated to reflect that and provide more scientific context on the issue.

What do Hulu Plus, Pandora, and YouTube all have in common? Ads—and lots of them. Sometimes, an advertisement or two isn't a big deal, but when you're bombarded with them daily on your iPhone, they can get old really quick, and might even lead you to delete the apps entirely.

Fresh off the heels of their latest agreement, Google and Samsung may soon be further aligned in their mobile technology outlook. The two tech giants signed a cross-licensing patent agreement, but that doesn't mean that Samsung was just going to start putting out stock Android devices. Quite the opposite really, as we saw from leaks of its new Magazine UX. The new user interface was shown during Samsung's presentation of it's latest Galaxy tablet at this years CES, and as reported to Re/code,...

Finally, the much-hyped Xbox One is out, setting the stage for an epic holiday showdown between Microsoft and Sony. While the PS4 was released a full week before the Xbox One, Microsoft's next generation system is fully equipped with the latest games and acts as an all-out media hub.

Although mowing is key to keeping your lawn healthy and good looking, it isn't anything worth jumping up and down for when it comes time to doing it. As it turned out, the first time I mowed my lawn wasn't nearly as fun or exciting as Hank Hill made it out to be. Maybe it was the beer.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Every time Apple releases a new version of their mobile operating system, it comes packed with an assortment of bugs, issues, and other hindrances.

Apple's iTunes Match service is a great feature for people who have large libraries or want to sync their music across a lot of different devices. It lets you store any song in your library that exists in the iTunes Store on the cloud, even songs you imported from CDs, and even improves the quality of some of them. But, like any new service, it's not without its problems, and the fact that it costs $25 a year makes those problems seem even worse. Among the issues that users reported, unmatche...

Getting a new phone is like getting a pair of new socks—you can't wait to try them on and when you do, they feel totally awesome. Maybe that's just me, but for many customers that have already received their highly anticipated iPhone 5 in the mail, awesome is definitely not the word they are using.

Of all the places you'd think to check for bed bugs, I doubt that library books would be at the top of your list. As odd as it sounds, though, libraries and library books are some of the most common places for bed bug infestations. Libraries all over the country have reported bed bug problems this summer, and some have even had to temporarily close to take care of the problem. But before you vow to never set foot inside a library again, here's a little primer on how to check your books for be...

It's no secret that there's a lot of surveillance going on these days. It's easier than ever to end up in a database, and even former government agents are speaking out about the atrocious amount of spying being done against our own citizens. They've targeted our laptops, cars, IP addresses, and now they're coming for our iPhones. AntiSec hackers managed to get their hands on a list of over 12 million Apple UDIDs (Universal Device IDs) from an FBI computer, and they published 1,000,001 of the...

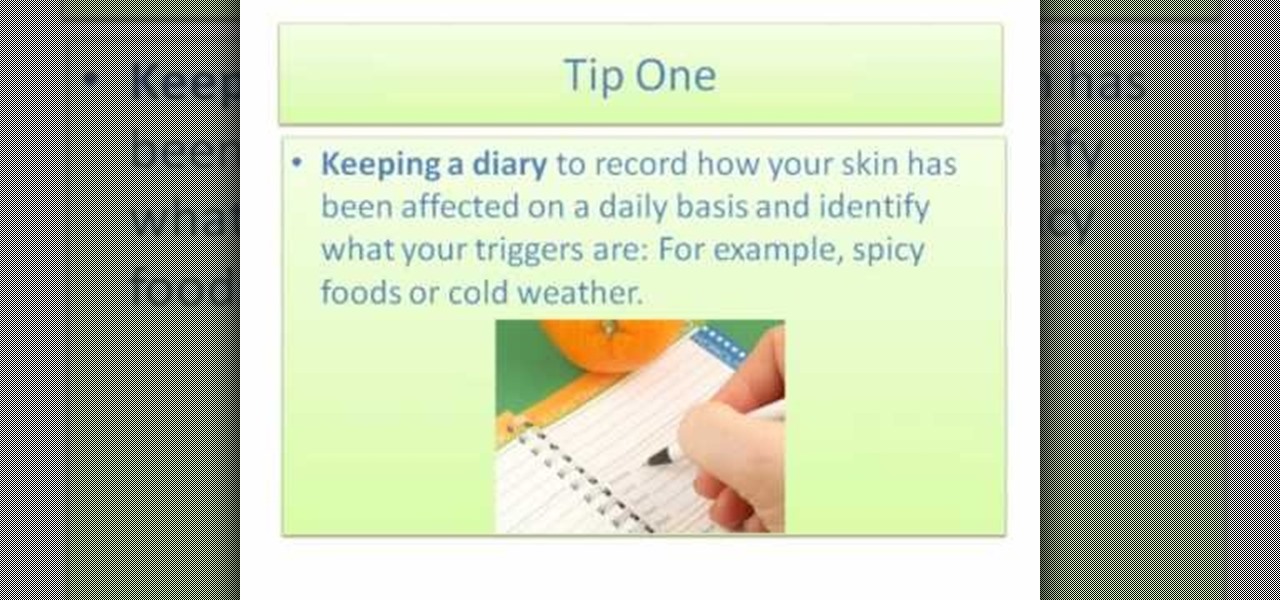
Tip 1. First of all you need to maintain a diary to record how your skin has been affected on a daily basis and identify what your triggers are: for example whether it is due to spicy foods or cold weather.

It doesn’t matter how long ago your last geometry class was, you can still impress your friends by finding a geometric mean. The geometric mean can be used to find the average of numbers with out unusually high or low results effecting the result.

In this emergency preparedness video series, learn what to do when you need to call 911, or even if you call by accident. Our expert, an experienced 911 dispatch operator, Jill Maglione, will tell you what the most important information you need to give is, why you need to give your address, why you may be asked to stay on the line, how to get to the point about what type of emergency you have, how to teach kids to use 911, how to report a car accident, and more tips you need for emergency pr...

One of the best recent outings in the Marvel universe is the animated series What If...?, which explores alternate universe takes on various superhero storylines that deliver fascinating scenarios if one single factor had been different in the story.

Snapchat parent company Snap has opened up its war chest to acquire yet another company that will play a role in its augmented reality ecosystem.

The biggest win in the race for consumer augmented reality smartglasses to date belongs not to Apple, Facebook, or Google, but Snapchat's parent company, Snap.

One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again.

Apple's iOS 14.5 overhauled the Podcasts app, combining new aesthetics with smart and efficient features. While you might find the app better at playing your favorite podcasts than past versions, you might also find something negative about the update on your iPhone: it may be eating up your storage.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.

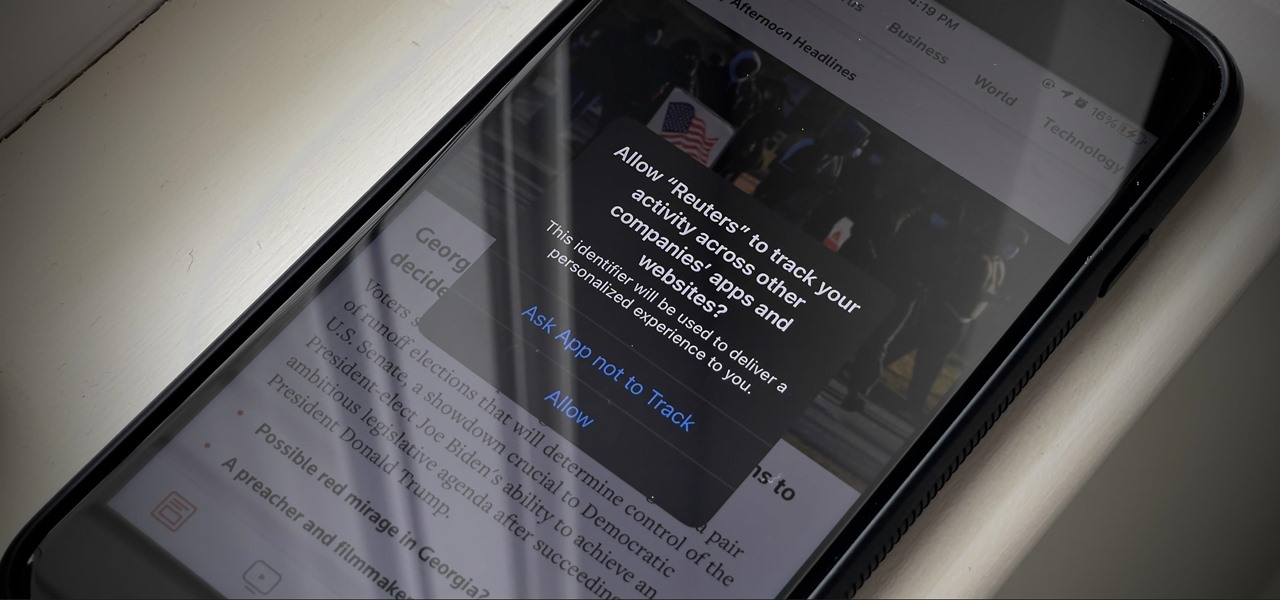
If you're like me, you're not too keen on being tracked. So when an app asks you if it can track your iPhone activity across other programs and websites for ads or data brokers, the answer is pretty much always "no." If you're tired of choosing "Ask App Not to Track" over and over again, there is a way to stop apps from even being able to ask in the first place.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

It's safe to say that we can call the annual ranking of AR investments a holiday tradition at Next Reality.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.