If you're butting heads with one of your employee's at work, or are having trouble resolving conflicts between other employee's, as a manager, supervisor, or someone else in a position of leadership, this can be a stressful situation. In this video you will learn a helpful exercise that you can use to work your way through a way to resolve the conflict itself.
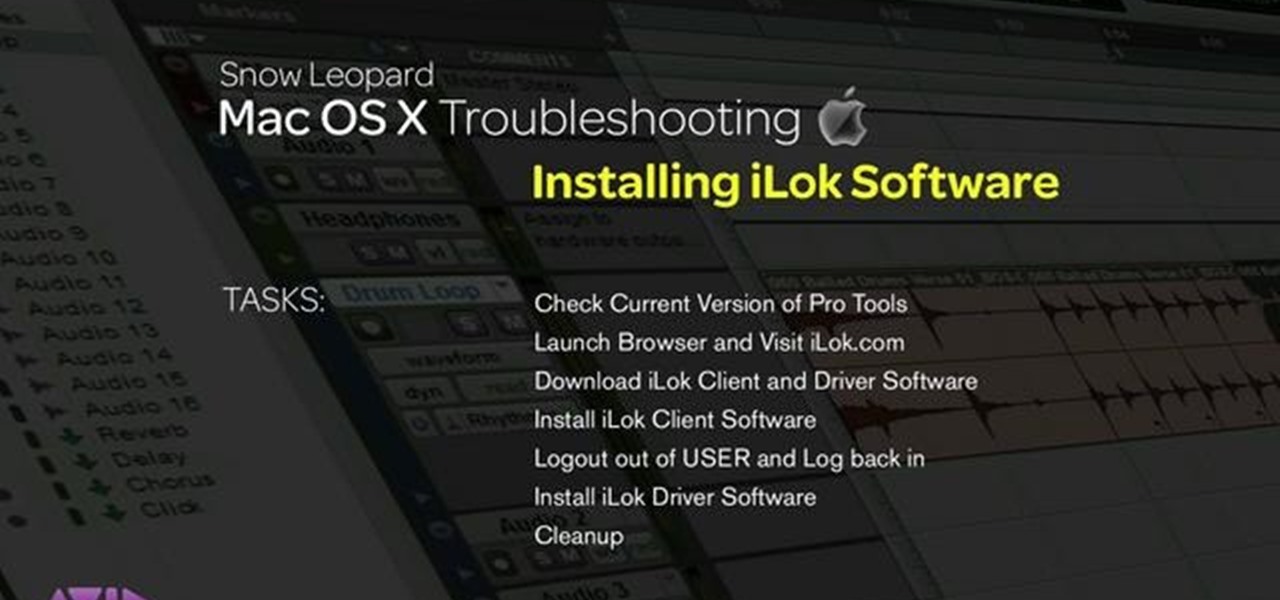
This video explains how installing/re-installing iLok Client, and Driver software, can sometimes be a great troubleshoot for resolving issues with Pro Tools, and the Mac Platform. Whether you're new to Digidesign's Pro Tools 8 or simply looking to pick up a few new tips and tricks, you are certain to benefit from this free software video tutorial. For complete instructions, takea look.
This video series is all about alphas in Zbrush! Step away from learning how to sculpt in Zbrush, and learn how to work, in-depth, with alpha mattes. If you don't know what an alpha is, this is a GREAT place to start.

In this automotive repair guide, we learn how to troubleshoot and repair a "no heat" problem on a Nissan Altima car. For all of the gritty details, including step-by-step instructions, and to get started resolving your own Altima's no-heat trouble, watch this video tutorial.

In this clip, you'll learn methods for troubleshooting and resolving the most commonly encountered WiFi wireless network problems. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.
In this tutorial, you'll learn a few standard methods for resolving less common and more complicated wireless network problems. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

A suspended chord (or a chord suspension) is usually made by holding one of the tones of a chord a tone higher, then resolving it to its resting place. This video explains what a suspended chord is and how to play them on the piano.

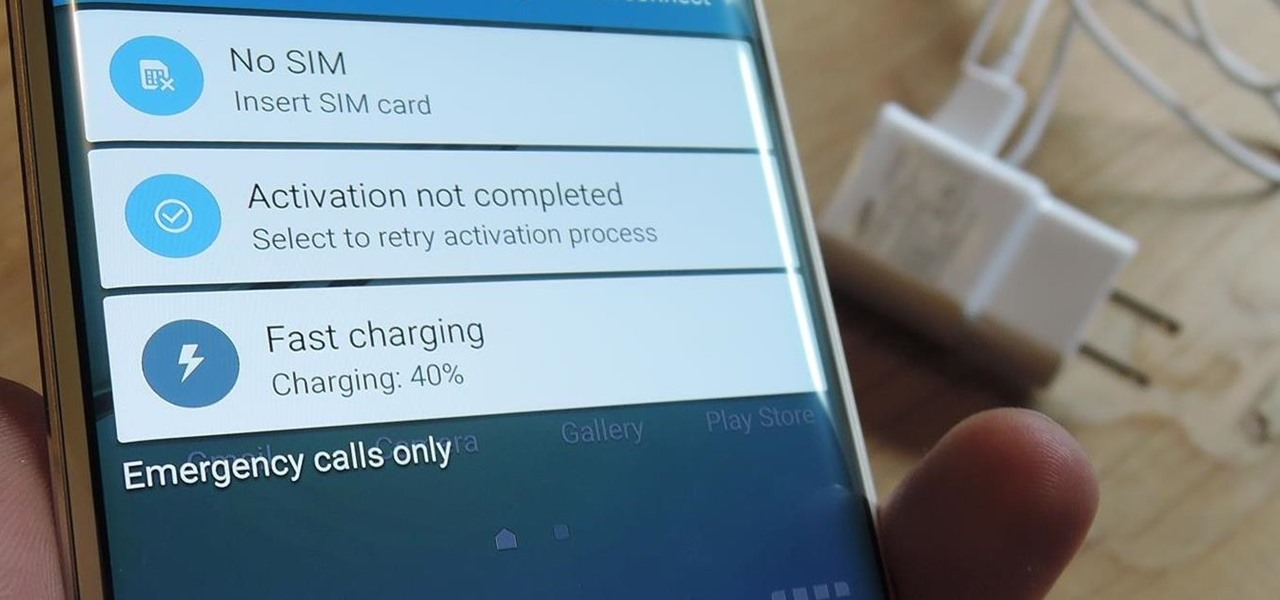
Faced with a missing log-on screen startup problem? This clip offers some advice for resolving it. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

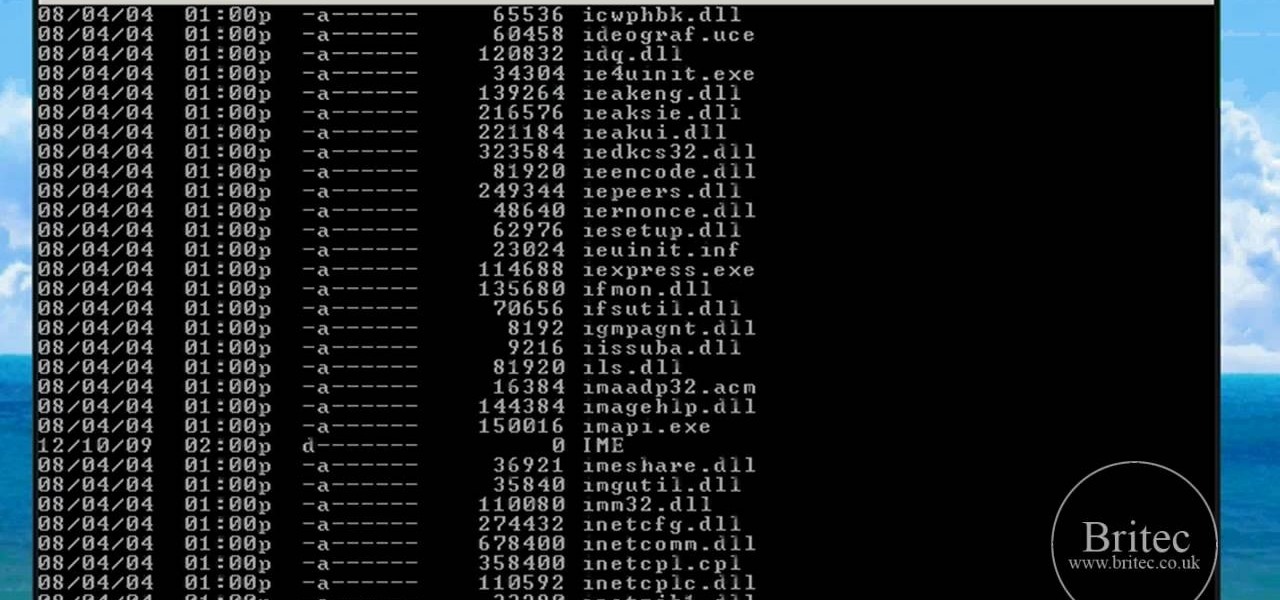
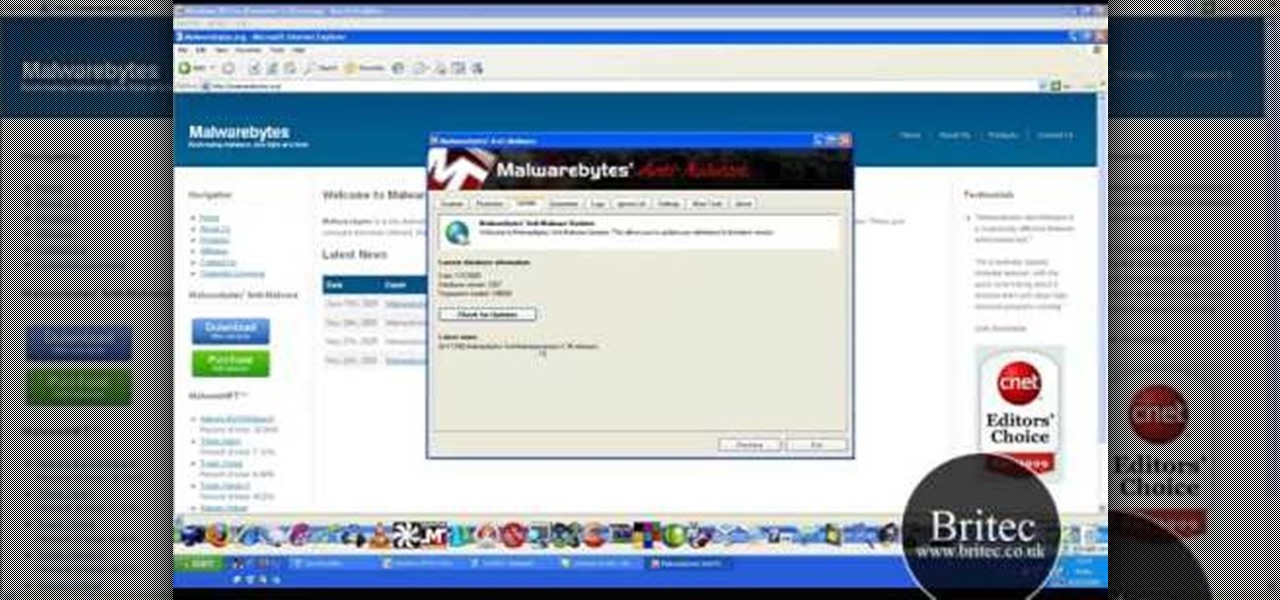
Need help resolving a disabled task manager or registry editor problem (as caused by a virus or malware) on a Microsoft Windows XP? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just under ten minutes. For more information, including step-by-step instructions, take a look.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

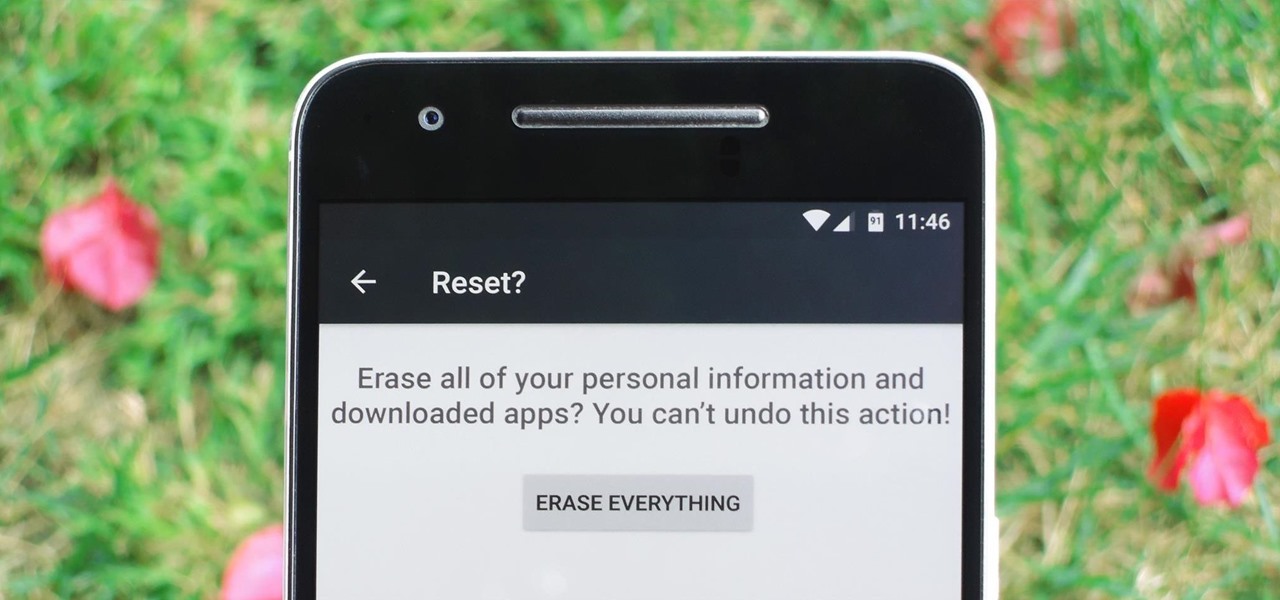
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

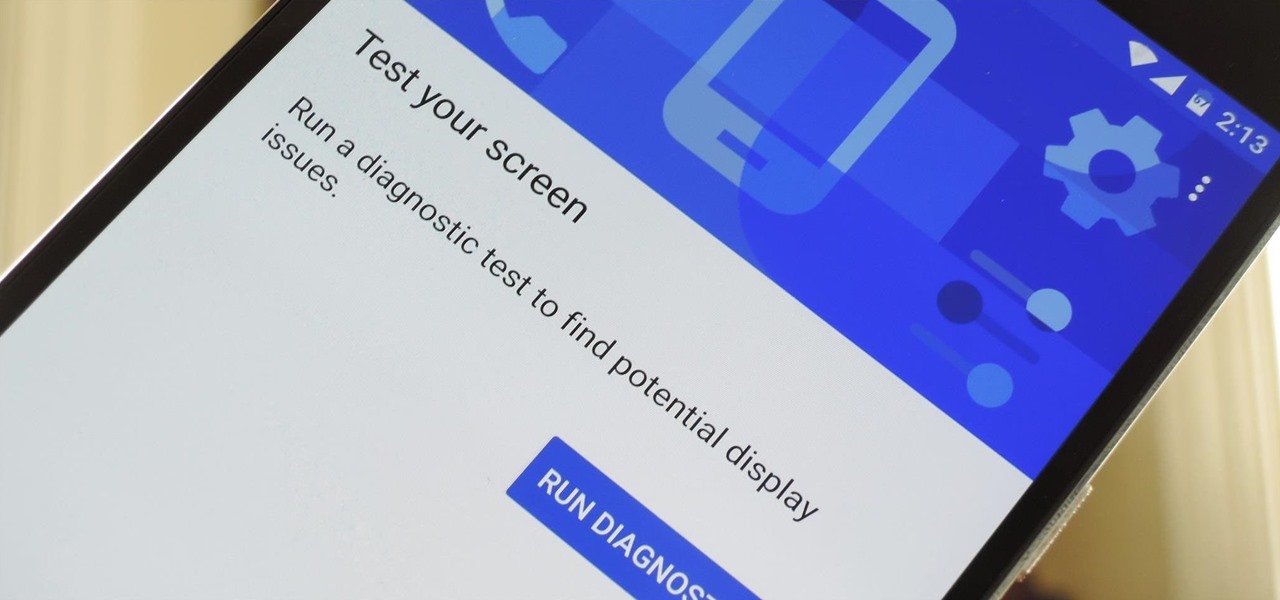
Google has a lesser-known Android app called Device Assist that might just be one of the most useful programs the company has ever published. It offers interactive guides and general tech support for Android, plus it can diagnose your device and help you fix any issues it finds.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

I picked up my Galaxy S6 Edge on release day and have loved it ever since. Did I spend an extra hundred bucks for the mostly-aesthetic Edge display? Yup! Did I have buyer's remorse about my frivolous spending? Not even a little.

Android has a single text file named build.prop that determines tons of various system-wide settings on your device. You need root access to edit this file, since it's stored on the system partition—but the various lines of codes it contains are actually fairly easy to interpret and modify.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

Hackers rely on good data to be able to pull off an attack, and reconnaissance is the stage of the hack in which they must learn as much as they can to devise a plan of action. Technical details are a critical component of this picture, and with OSINT tools like Maltego, a single domain name is everything you need to fingerprint the tech details of an organization from IP address to AS number.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

Many of you who tried to wake up to your iPhone's alarm clock this morning didn't. Reports say that after the stroke of midnight last night, the alarm clock application on all iOS 4 devices simply didn't work— unless you set a recurring alarm.

There was a huge ban wave recently on Xbox Live. In the unfortunate event that you decided to do something against Microsoft policy, and have consequently gotten yourself banned from Xbox Live, you may have come to the realization that doing whatever got you banned from Xbox Live in the first place was not worth the risk.

Last week, we discussed whether Google should require you to use your real name for Google+ profiles. Google is working on eliminating fake profiles, and in the process, they've booted some real people, including actor +William Shatner. If you find out that your Google+ account has been suspended, you can appeal the suspension and get your profile reinstated.