Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.
You may have noticed your Note 10 came with quite a bit of bloatware. Even the unlocked version of the phone comes with Facebook preinstalled, and if you bought it from a carrier, it's much worse. Luckily, there's a way to remove any apps you don't want, and you don't need root or a paid app to do it.

Long before the HoloLens or the Magic Leap One, a California-based team of independent filmmakers envisioned what the future of augmented reality might look like.

When it comes to augmented reality (AR) on Android, you might be wondering how you can get those cool new games and apps on your unsupported phone. Google has an officially supported device list for its ARCore platform, which usually consists of the more modern devices. You won't find very many older devices on the list for a reason, but that doesn't mean your "old" phone can't use ARCore still.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

This week, the recurring theme in augmented reality can be summed up fairly succinctly: content is king.

Augmented reality startup Nreal was a hit at this month's CES event, with some even calling the device a worthy challenger to the Magic Leap One.

The saga of augmented reality startup Meta appeared to be at end, but there are new developments unfolding in real time that may either sink Meta deeper into trouble, or provide a tenuous lifeline for the beleaguered augmented reality company.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.

With the new iPhones coming out, many see the current mobile market as just another epic battle between Samsung and Apple. But let's not forget there are many other phones that run Android. And when you start to sift through the specs, one stands out as a competitive alternative to the iPhone XR, the LG G7 ThinQ.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

You can never replace the skills and expertise of a professional graphic designer, but Canva comes pretty damn close. It's ridiculously easy to use the drag-and-drop design tool for both professionals and people like me who don't have the need (or knowledge required) to use more advanced graphic design software.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

As manufacturers try to differentiate their smartphones from the sea of Android devices, a new genre of smartphone has emerged: gaming phones. Razer Phone was the first to gain traction, but the likes of Xiaomi, Asus, and ZTE have all announced gaming-first phones coming soon. Still, you don't really need to buy a "gaming phone" to play games like a pro on your smartphone.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

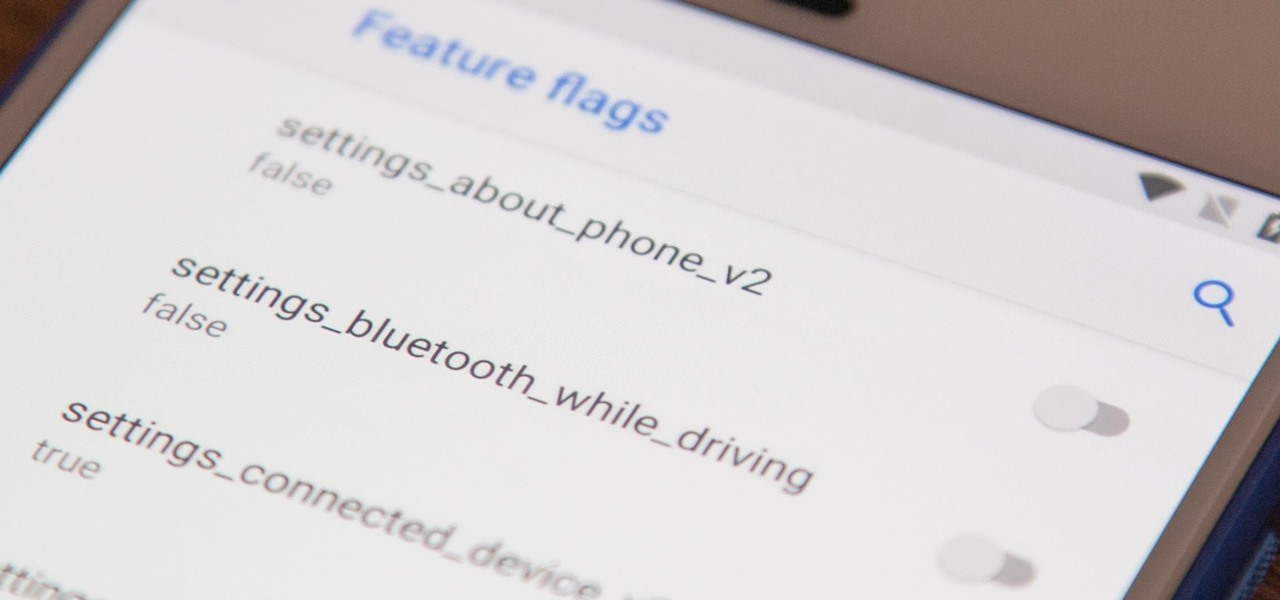
There's a new secret settings menu hiding in Android 9.0 Pie that offers Chrome-style "flags" to the overall operating system. Since it's currently the first Developer Preview and Public Beta versions, it's possible that this menu could disappear entirely when the stable version finally gets released, but it could also persist in its current hidden state where you have to unlock it.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

One unique feature of Firefox Mobile is extensions. Extensions allow users to add in features that didn't originally come with the browser. These add-ons provide an array of features, including improvement to privacy and security.

As the calendar year (and, for many companies, the fiscal year) comes to a close, it appears 2017 may stand as the new high-water mark for investment in augmented and virtual reality technology.

Market boxes are an integral part of the player experience in Animal Crossing: Pocket Camp, but using them effectively can be a tricky task. The item-trading tool between human friends is the locale for both junk and diamond-in-the-rough deals, and it can greatly increase the number of bells you earn if you play your cards right.

Introduced along with the iPhone X, Animoji are animated characters, mostly animals, that are rendered from the user's facial expressions using the device's TrueDepth camera system to track the user's facial movements.

There was a time when building a website required coding knowledge. Eventually, software came along that made the process easier, and then services like Squarespace made it dead simple for even a technical novice to design a website.

Update 10/23: The hits just keep on coming. We're now seeing reports of a "smearing" effect when scrolling through apps on the Pixel XL 2. We'll expand on that at the bottom of this article, but it's still worth reading the background information on issues with LG's new POLED displays.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

A recent initiative by the Cherokee Nation American Indian Tribe delivers a success story for knocking out a silent killer — Hepatitis C.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.

Cancer cells do a pretty good job of flying under the radar of our immune system. They don't raise the alarm bells signaling they are a foreign invader the way viruses do. That might be something scientists can change, though.

Augmented and virtual reality continues to be a hot commodity among tech investors, with more than $800 million invested in AR/VR companies in the second quarter alone and global tech leaders like Samsung focusing their investment strategies on the emerging field.

There's nothing more fun than unlocking a hidden Snapchat filter or lens and beating everyone to that perfect first selfie. So when a new filter or lens comes out, like the current Uganda Knuckles one, it's always interesting to see how things will turn out.

As summer heats up, new maps from the Centers for Disease Control and Prevention (CDC) gives us our best guess at where Zika-carrying mosquitoes could be hanging out this year in the US.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Zika is a threat to unborn babies — the virus can cause neurological damage if it infects a mother during pregnancy. But as with many things, our solutions to the problem aren't always all that much better than the problem itself.

On October 17, 1943, a story in the New York Herald Tribune read "Many laymen — husbands, wives, parents, brothers, sisters, friends — beg Dr. Keefer for penicillin," according to the American Chemical Society. Dr. Chester Keefer of Boston was responsible for rationing the new miracle drug, penicillin.

The Autobots and Decepticons are back as Transformers: Forged to Fight has soft-launched for both iOS and Android. Help Optimus Prime fight corrupted Transformers one on one to save them from their ruthless overlords, and have them join your cause, regardless of which side they're on. Collect, control, and level up unique robots from the entire Transformers universe, including the classic TV animated series, movies, comics, and toys.