Frustrated with a bedroom closet that doesn’t work for you? You’re not alone, and you don’t have to live with it the way it is! In this episode, a renter’s closet gets a makeover so she can have easy access to everything and have more hanging space. Taking the sliding doors off and getting rid of the shelf above the rod opens up all sorts of possibilities, including adding a double hanging rod. You’ll see how easy it is to organize your bedroom closet to maximize the space, all on a budget.

In this episode, see how to decorate a small balcony to add livable square footage to your apartment by installing a reed fence, and making a bench out of a few plastic storage containers and plywood. There’s even room to include a balcony garden with a raised planter. These balcony decorating ideas can also be used for small patios and decks and will inspire you to create your very own outdoor oasis.

Do you like everything about your apartment, except for that unsightly ceiling light fixture? No need to replace it, just cover it up with a DIY drum shade – it will instantly give your room a more sophisticated and personalized look. See how easy it is to make a customized drum shade that will fit any décor, all with inexpensive and easily sourced materials. This is do it yourself lighting on a budget that’s perfect for renters and anyone looking for a quick upgrade to their lighting fixtures.

Whether you own or rent, it’s not always easy to decorate a studio apartment to keep the bed out of sight. In this episode, you’ll see how to divide a studio apartment with an IKEA KVARTAL system. Panels, curtains and art hanging from the ceiling tracks give the illusion of a wall, creating a separate living room that’s easy to open up anytime. All it takes is a few simple tricks and you’ll see what an easy project this is for decorating a studio apartment or any space that could use a room d...

Hackers are always seeking zero-day exploits that can successfully bypass Windows 10's security features. There has been extensive research into creating undetectable malware and entire GitHub projects dedicated to automating the creation of undetectable payloads such as WinPayloads, Veil v3, and TheFatRat.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

As the fish farming industry struggles to become more environmentally friendly, it just gained another problem. Fish food loaded with antibiotic-resistant genes.

In the perpetual search for a renewable and convenient energy source, our bacterial friends have once again stolen the limelight.

If you use Google Chrome as your default desktop/laptop browser, then Chrome OS will be pretty easy to get up and running if transitioning from Windows or macOS. Google has created an operating system that is fast, lightweight, and versatile enough to be adopted by pros and novices alike.

Remember the feeling you had the moment you removed your shiny new Nexus device from its packaging and booted it up for the first time? You swiped through the app drawer at lightning speed and thought to yourself, "This is the last Android phone I will ever need, they just aren't going to get any better than this."

It's no secret that the vast majority of Null Byte readers range from beginner to seasoned coding pros and developers. Regardless of whether you're interested primarily in building websites or creating best-selling apps and games, working with a wide variety of programming languages remains one of the best ways to make serious money in an increasingly app-driven world.

If you're trying to learn a new skill, you wouldn't want to waste your time learning from someone with sub-par experience. No, you'd want to learn from the very best of the best to ensure you're getting a quality education.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.

For Apple Pay users, the iPhone X, XS, XS Max, or XR will be an adjustment. Gone are the days where you could rest your finger on the Home button and hold your device within range of a contactless reader. Without Touch ID on the iPhone X, this isn't possible. But have no fear, Face ID is here.

Aura, a highly rated app for mindfulness and mental health, just became available on Android and is currently on sale.

In an effort to make its services more accessible to users who live in developing countries, Facebook has released a streamlined version of its messenger app. Messenger Lite, at less than 5 MB, is much smaller than its regular 25 MB counterpart and was developed for use on older and lower-end phones. Finally, the app is now available for download in the US.

If you want to quickly understand EtherWars, imagine a game like StarCraft where you build out your base on your living room floor instead of on a computer screen. Before we had computer games to help us imagine what space wars might feel like, we played with toy ships and used our imaginations. EtherWars combines those two elements by replacing toys with holograms that actually react to your choices.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

If you watched a YouTube video on your Android device today, you may may noticed something just a little different. If you haven't, go check out the app in your drawer or homepage. Google today pushed out an update to their YouTube app, but by all accounts, it was never meant to hit the public. This is labeled a dogfood build, which is a term used to describe products going through in-house testing, in effect "eating their own dogfood".

Via Twitter, HTC, the Taiwanese device manufacturer, announced today that their barely 18 month old flagship phones will not see official updates for anything past Jellybean. HTC went on to elaborate, saying:

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

We've already highlighted the importance of learning Microsoft Excel from a hacker's standpoint, but it's also just a good skill to have as you'll likely come across the number-crunching powerhouse at school and work, as well as in other areas of your life, such as budgeting.

Over half of all Americans have listened to at least one podcast, and that number is growing every year. With over one million podcasts and 30 million episodes in existence, there's no end to discovering new voices expounding on a range of topics.

You've spent untold hours playing your favorite games. You know what you love. More importantly, you know what can be improved upon. The distance between vision and reality is not as far as you think. You just need a bit of training.

If there's any silver lining to being stuck at home right now, it's the fact that many of us have way more time to take care of those things that have been sitting on our back burner for ages, like beefing up our resumes.

One could argue that, at least for the moment, software development is more important to the augmented reality experience than hardware. Since a viable augmented reality headset has yet to emerge for the broader, mainstream consumer market, currently, the same devices that make texting and selfies possible are leading the charge to enable easy-to-use AR experiences.

Reddit user Mr. Squishy recreated the entire Game Boy Pokémon Red Version game in Vanilla Minecraft, i.e., a Minecraft server without gameplay modifications. Instead of using mods, he used 357,000 commands blocks—blocks that execute commands in the popular sandbox game. How long did it take him? Almost two years.

A new app called Roadie now makes life a little easier by connecting users to people who can transport their stuff. The app allows users to transport anything from dogs to getting rid of your ex's things. Furthermore, anyone can register as a sender, or become a driver to make an extra buck. The app is very easy to use: simply download (the app is available on both iOS and Android) and register using an email address or with Facebook. Using the profile you've created, users then select whethe...

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

You didn't have to attend this year's CES to have gadget envy. There are so many great smartphones, computers, laptops, and other gadgets available in the market that the real challenge becomes choosing the right one to fit your needs and your budget.

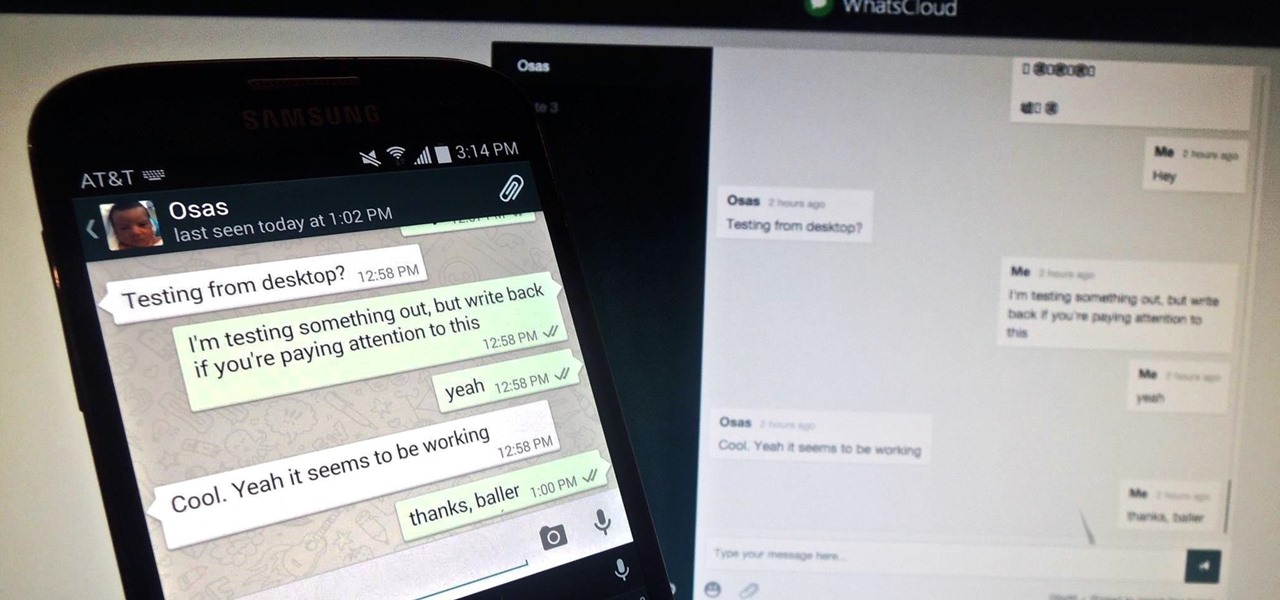
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

Brought to you by Tomcat. Falling snow, warm fireplace, delicious hot cocoa, quiet reading time, mouse. Quick quiz - which one is not like the other? Nothing can ruin a perfectly cozy afternoon in your home like a pest on the loose. With dropping temperatures, you may have some unwelcome residents, like mice, looking for shelter from the cold.

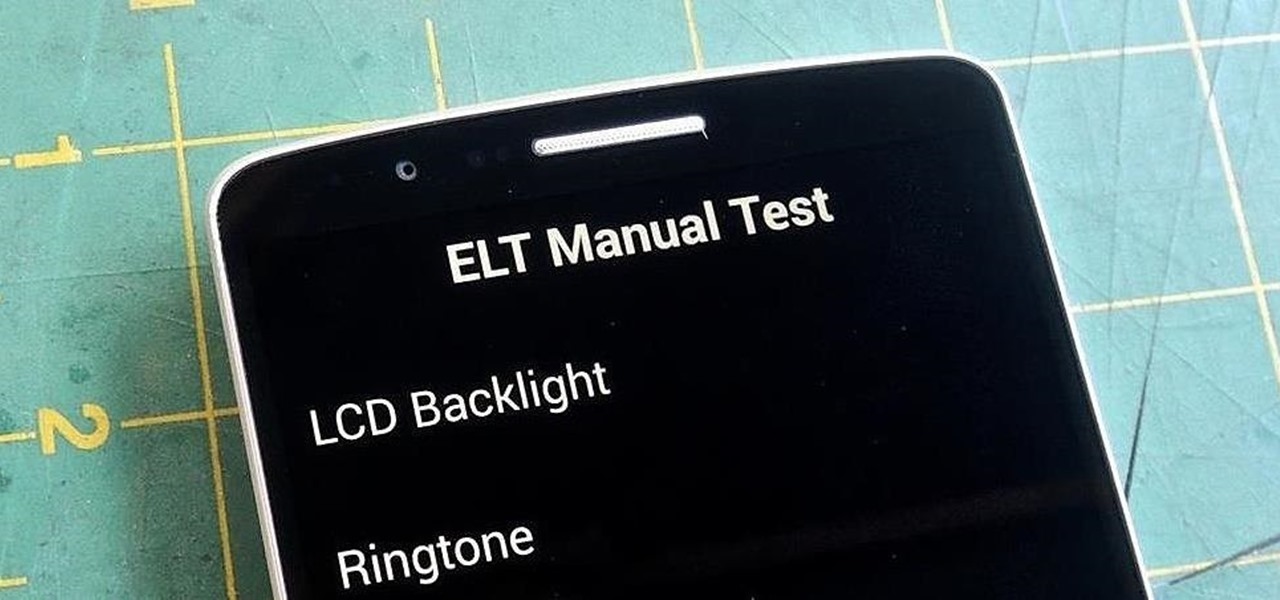
If you notice any issues with your LG G3, pinpointing the culprit can be an arduous task. It could be a hardware issue, a resource-heavy app, or a bloatware-infested operating system.

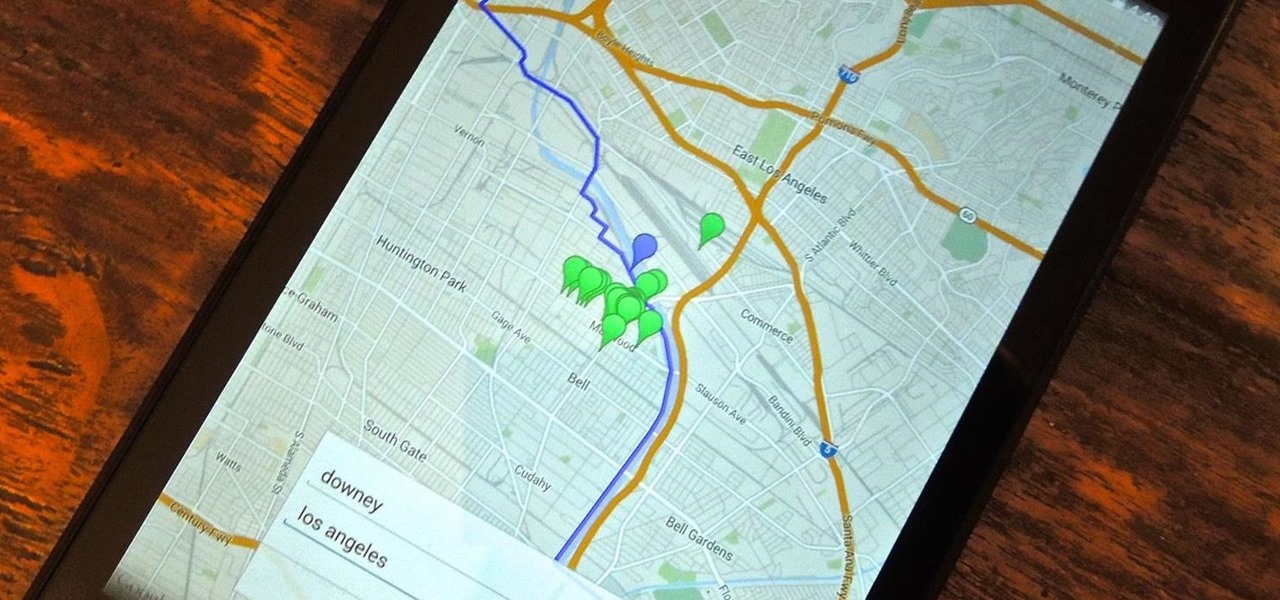
Back in college, there were many instances where I'd have to meet up with a partner that I was randomly paired with in order to work on a project or to study for an exam. Besides the awkward interactions, the most difficult part was always figuring out where we would meet off-campus. I live here and they live there, so what's reasonably halfway?

We've all had to write an essay or research paper at some point, and undoubtedly the hardest part about it is always the citation, right? If you ask me, it's a huge pain in the arse. Even more so if you're gathering your facts from a huge variety of sources.