
How To: Make Music with Floppy Drives & LabVIEW
Video: . Project Overview


Video: . Project Overview

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Fish is delicious, and as the Harvard School of Public Health points out, incredibly good for you. There are many studies that show regularly consuming a couple of servings of fish per week can help prevent heart disease and may well reduce your chances of stroke, depression, and getting Alzheimer's. After all, there's a reason why fish is called "brain food."

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

Welcome back, my greenhorn hackers! Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!

When you come home from the grocery store, you probably put away every single fruit and vegetable in the bins and drawers in your refrigerator. Any fifth grader knows that fridges work to preserve food, thus everything should go in there, right? Nope!

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

Everyone hates to feel like they've been taken advantage of, especially when buying a used vehicle. The thought comes across every car buyer's mind... "Did I just get taken by that smooth-talking salesman?" When it comes to cars, how do you know if you're really getting a good deal, or if you're being offered a fair price for your car? After all, cars are most peoples second largest investment, so we need to make this decision wisely.

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

In one of my previous articles, I showed off how to make water freeze into ice instantaneously. In this article, I'd like to elaborate on this, and show how a glass of water can turn to ice instantly on command. What exactly is this supernatural power? Discover the secrets to ice-bending—in real life.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Stand out from the high street fashion clones with stuff you’ve fashioned yourself. It’s easy to take old pieces of electronic junk and transform them into all sorts of fun ‘n’ funky geeky accessories. Like a totally useful tote bag, a what-on-earth-is-that wallet and a bedazzling belt. It’s terribly geeky but chicy too. Here’s how…

A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

It's all fun and games until the technology is actually put into use and you realize augmented reality is now part of Death Star.

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

If there's anything we've learned during 2020, it's that working and learning from home is going to shift the way we do business. With Microsoft announcing that its staff will be allowed to permanently work from home, expect more businesses to follow suit.

The amount of information we see on a daily basis is overwhelming. Then there's all the data we never even see. If your career depends on making sense of all of this information, you need to understand the programs that do the heavy lifting.

Thanks to a growing demand for talented and trained leaders who can inspire teams and innovate new products and services, there's never been a better time to work as a project manager. Whether you're interested in joining the ranks of a Fortune 500 company or working independently, project managers command high salaries and enjoy unparalleled opportunities for advancement.

It looks as though the novel coronavirus and social distancing guidelines are here to stay for a while. So companies of all sizes and industries are scrambling to adapt to a new reality in which everything from morning meetings to large-scale presentations are done entirely online. It looks like this is going to be the new normal for the foreseeable future.

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

We're living in a world that runs on Big Data. As the driving force behind everything from self-driving cars and Google algorithms to the latest medical technology and financial platforms, massive sets of increasingly complex data lie at the heart of today's most exciting and important innovations.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

We're glued to the news now more than ever, but our "free press" isn't necessarily free of charge. Cable news outlets like CNN and MSNBC are locked behind expensive cable TV packages and cord-cutting streaming subscriptions such as Sling TV and Hulu + Live TV. Luckily, there are plenty of alternatives to get your TV news fix, free of any payment, account, or commitment.

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

We've been so worried about volumetric scans possibly robbing celebrities and performers of their agency and right to control their image that, somewhere along the way, we forgot that scans may not always be necessary to produce passable holographic performances.
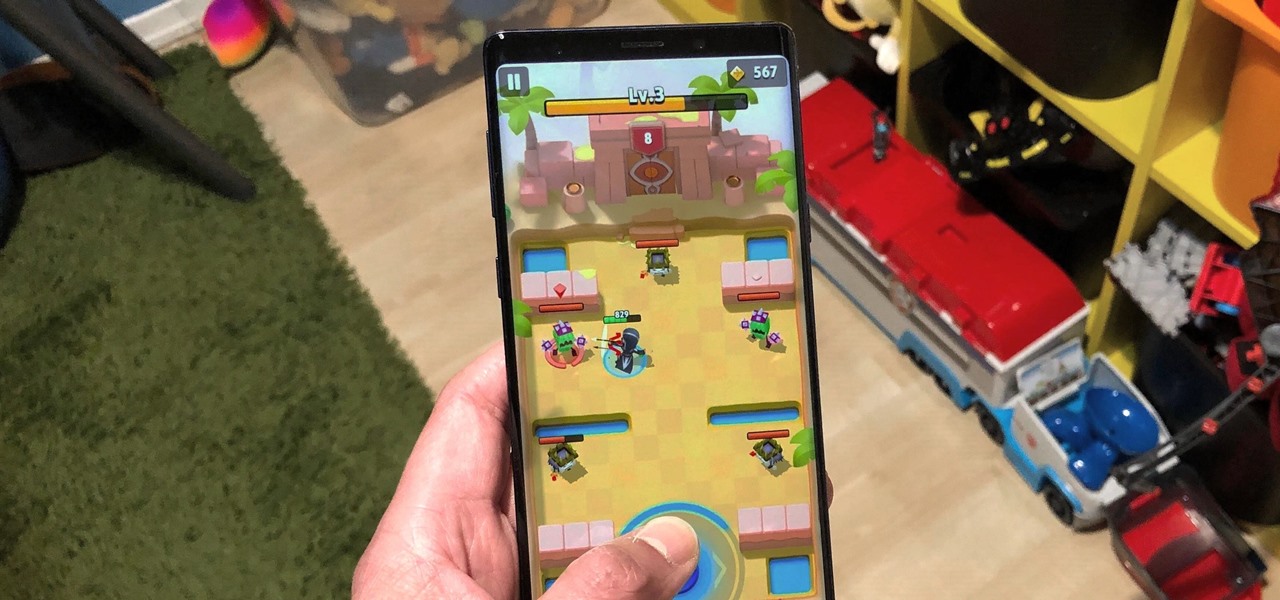
When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

The last time we heard from Meta, the makers of the Meta 2 augmented reality headset, things looked pretty bleak. Now, as several new facts have come to light, we have confirmation regarding the beleaguered company's fate: Meta is done.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

While the iPhone XS and XS Max come equipped with 4 GB of random access memory, and the iPhone XR with 3 GB of RAM, Apple's latest flagships are still susceptible to occasional slowdowns in performance in iOS 12. This can be fixed by clearing RAM, but the process is now a little trickier compared to iPhones with Home buttons.