
How To: Tips & Tactics to Create Your Own Compost Pile
While it is easy to create and maintain your compost pile, you can enjoy it more knowing a few basic tips.


While it is easy to create and maintain your compost pile, you can enjoy it more knowing a few basic tips.

In a race to make self-driven cars mainstream, Intel announced today that they've bought Israeli microchip technology company Mobileye for $15.3 billion, setting the stage for Intel to dominate a large portion of the driverless market.
Welcome back Hackers\Newbies!

In this video, I show you how to make a "cow furnace" that gives you leather and cooked steak without having to use up your resources.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

Baby showers are fun ways to celebrate new mommy-hood. You won't want to forget the traditions though. Check out this video before you start planning and make sure you have an nice balance of etiquette and fun.

To assist developers and researchers in their efforts to create apps and services for automobiles, Volvo Cars has launched a new Innovation Portal with useful new tools and assets.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

We're living in uncertain times. The sudden outbreak of the novel coronavirus and subsequent self-isolation of roughly half the world's population has led to a massive reorganization of the economy, countless layoffs, compromised security networks, and a variety of other significant disruptions that will forever alter the landscape of our daily lives.

As the COVID-19 virus continues to spread, counties, cities, and states are closing down businesses, events, and schools that aren't absolutely necessary. Some companies around the US are recommending or requiring employees to work from home during the coronavirus pandemic. If you're stuck at home, there are apps and services to help you make it through a lockdown.
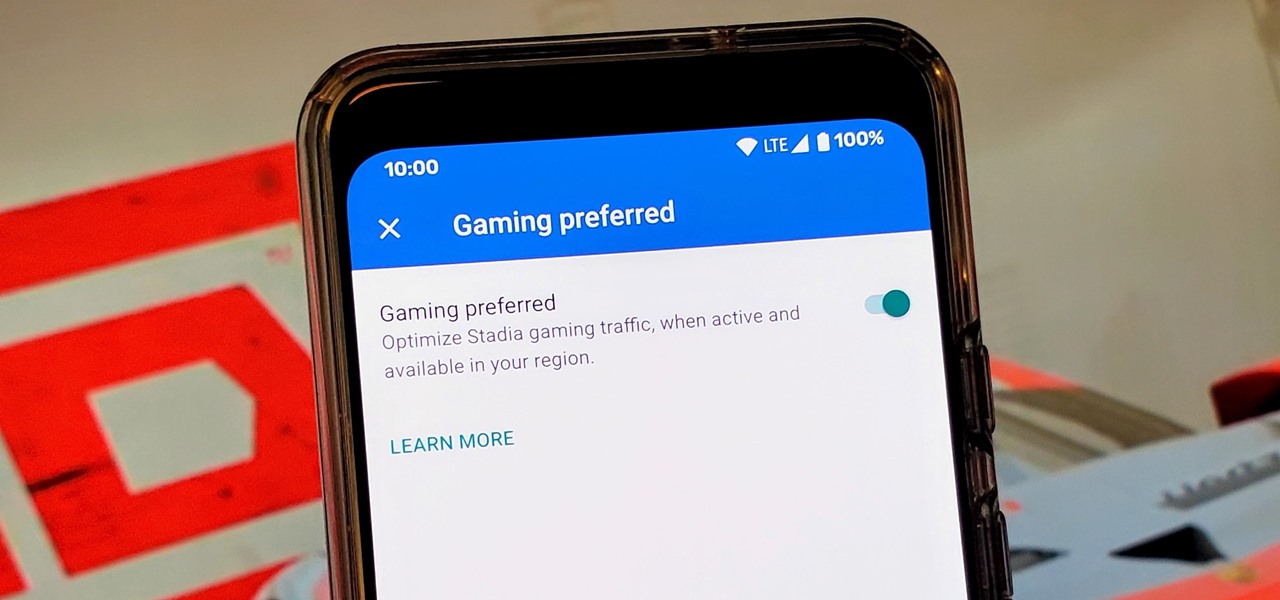
Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

With Pokémon GO as its cash cow and the forthcoming Harry Potter: Wizards Unite and Niantic Real World Platform promising future revenue streams, Niantic has convinced investors to bet on its flavor of augmented reality

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"
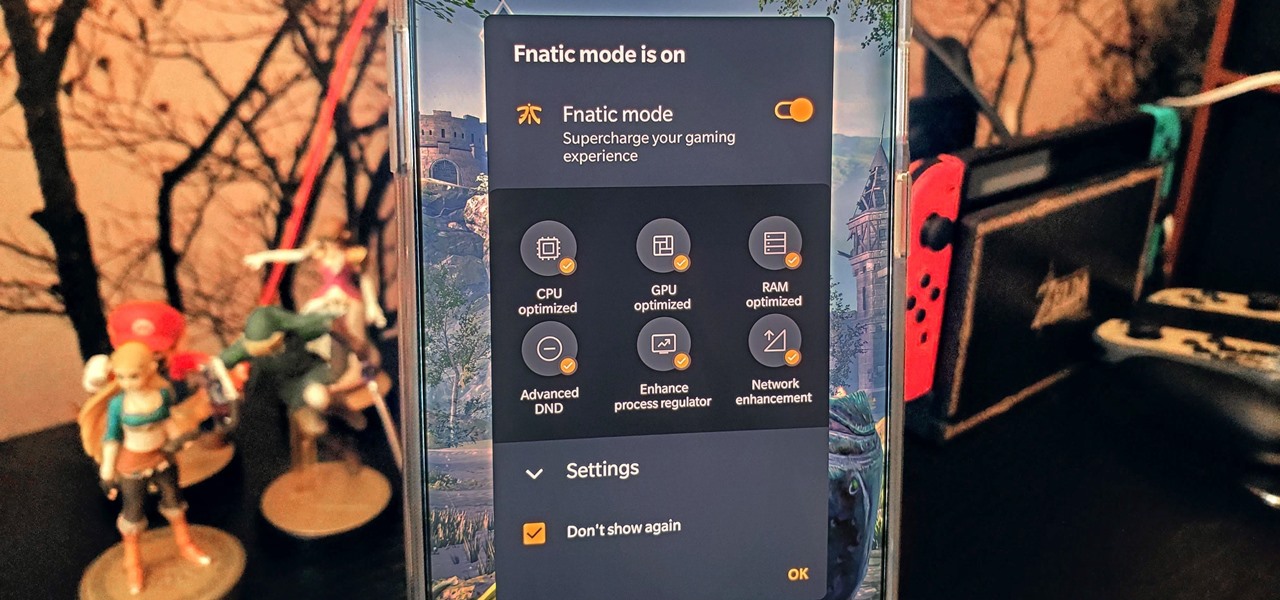
The OnePlus 7 Pro is an outright beast. From the highly rated display with minimal bezels to the 90 Hz refresh rate, there's no denying this phone is great for gaming. Although not explicitly marketed as a gaming phone, it seems OnePlus unintentionally created one by cramming in great specs and game-friendly software features like Fnatic Mode.
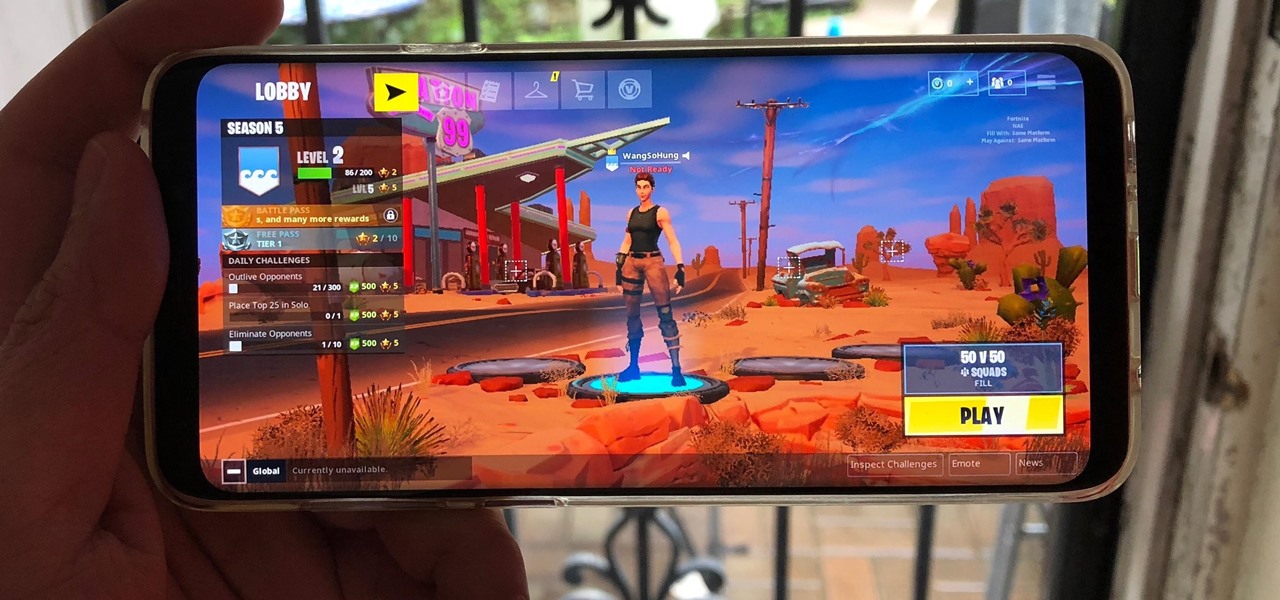
Fortnite's long awaited arrival on Android has ramped up excitement among gamers who are installing the beta version in astounding numbers. With so many midrange and budget devices running Android, however, it's important to stay on top of your device's performance to ensure smooth and uninterrupted gameplay.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.

Termite poop and biofuels — what's the connection? New research into termites' intestinal comings and goings describes a process that may speed the development and lower the cost of fuels made from plant matter.

As a fan of the HTC One series, I almost always upgrade my phone soon after the new model becomes available. I purchased the M7 when it first came out, upgraded to the M8 shortly after its launch, and then jumped on the M9. However, I stopped right there.

If you could save the world by eating a burger, would you? Two companies, Beyond Meat and Impossible Foods, are on a mission to redefine veggie burgers and eliminate all of the downsides of animal farming on our planet. With over five years of research and product testing, they've finally figured out how to make a plant-based burger look, feel, and taste just like real meat.
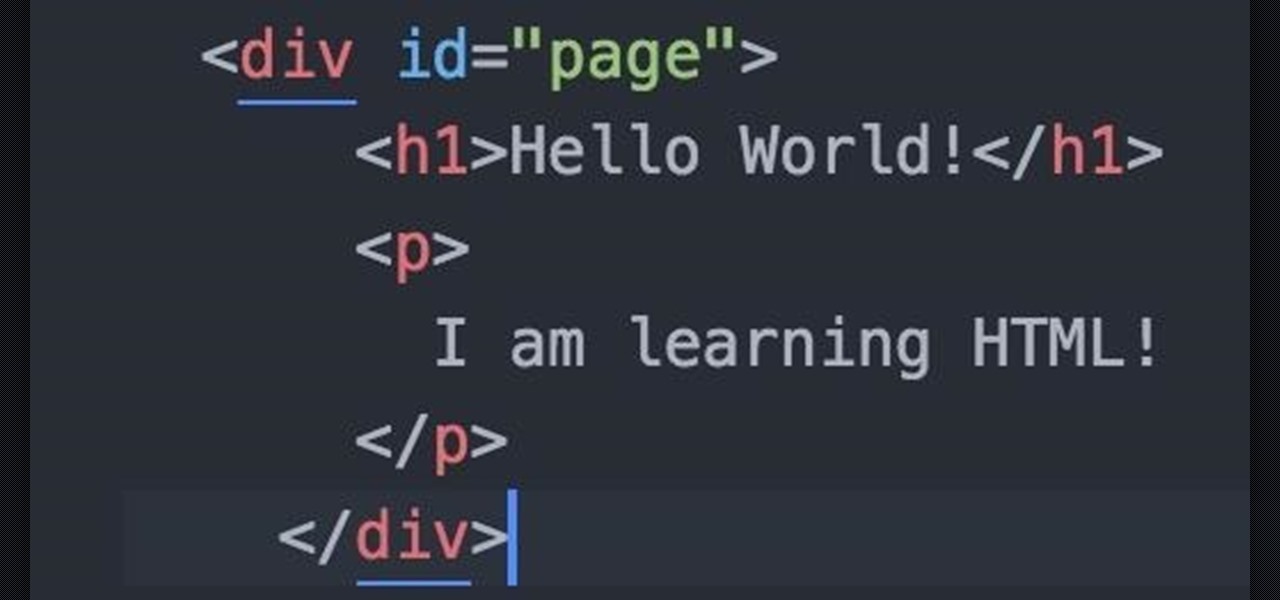
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.
There is many different types of stars in the universe. Majority of them are red dwarf stars. However, there are plenty of stars like ordinary stars (like our sun), red giants, blue stars and etc. Furthermore, when you look in the night sky, we see a lot of small and bright stars. What people don't know is that there are stars that are not even completely understood by astronomers and scientists.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.
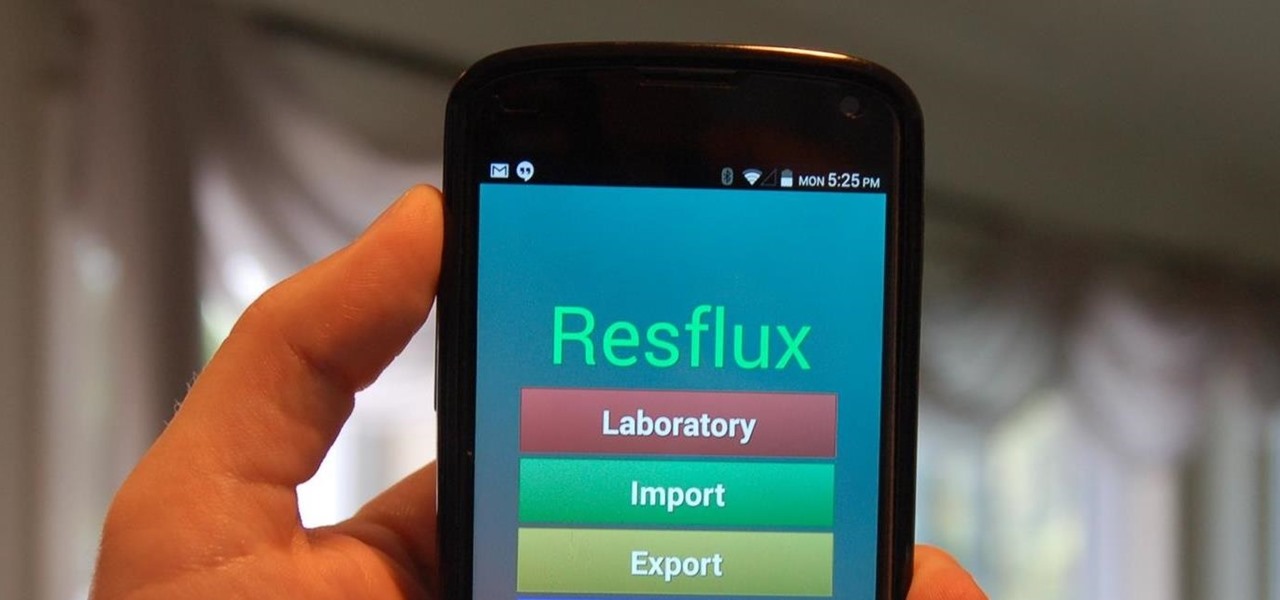
Resflux is an Xposed mod developed by Julian Paolo Dayag, aka WisdomSky, that provides users with a straightforward and functional way to customize and theme almost every aspect of the packages (apps and system components) installed on their Android device.
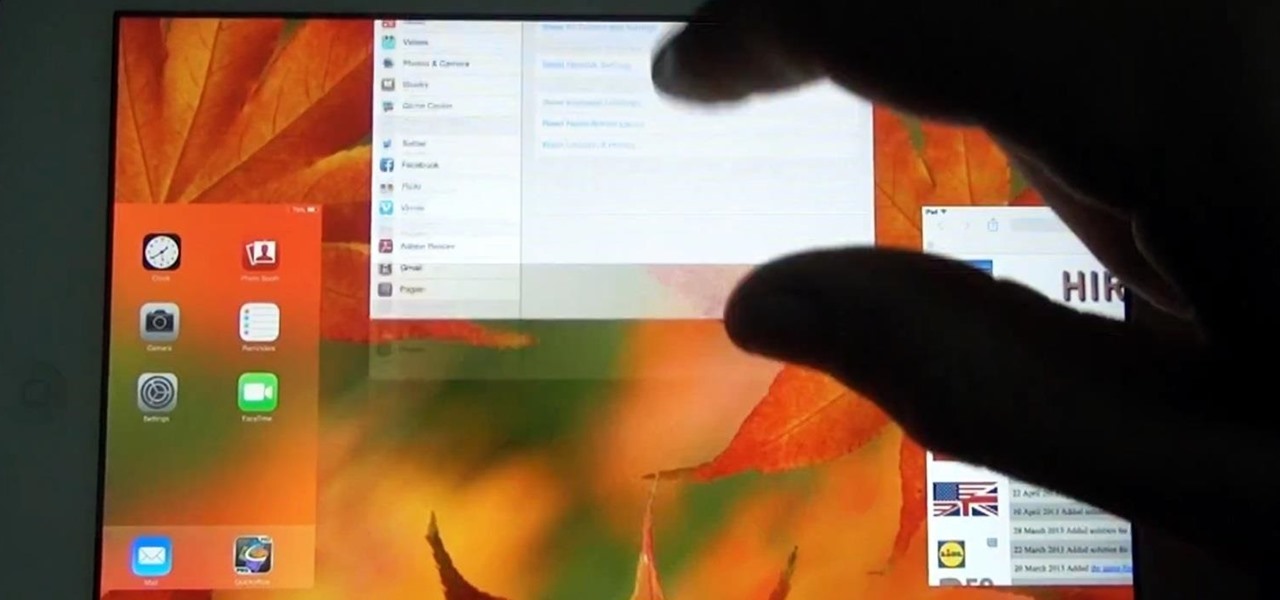
The new Apple iOS 7 is here for your iPad Mini. Closing running apps prevents them from taking up precious memory, resources and battery. Simply quitting an app by pressing the home button doesn't work; the application is still running. Watch the video below to see how to close them completely.

GTFOBins and LOLBAS are projects with the goal of documenting native binaries that can be abused and exploited by attackers on Unix and Windows systems, respectfully. These binaries are often used for "living off the land" techniques during post-exploitation. In this tutorial, we will be exploring gtfo, a tool used to search these projects for abusable binaries right from the command line.

Welcome to Minecraft World! Check out our full tutorials and make sure to post to the community forum if you have any questions or cool builds you want to share.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.