A few weeks ago, Twitter announced that they would be creating an archive feature for its members, which they've been slowly rolling out to select users. After signing in today, I noticed the feature was finally available for my account, so I went to test it out.
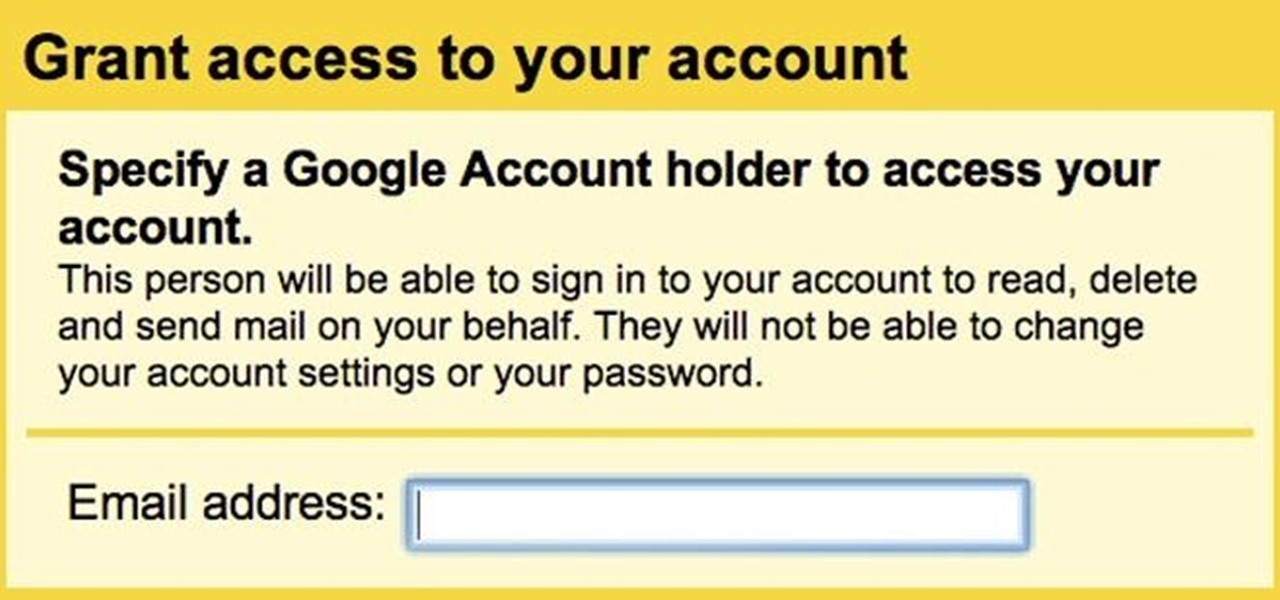
Whether it's because you have no access to the internet or because you're simply on vacation, having someone else check your emails may be a possibility. You can give them your password and screen name, but that's never a good thing. Giving out your password to anyone, even someone you trust, is not something that I would ever suggest for two reasons:

As enjoyable as Facebook can be at times, it can also be a great distraction and even better deterrent of getting work done. A quick "Oh, let me check my notifications" can turn into hours and hours of Facebooking, and before you know it, you're already on your 7th Wikipedia page, all thanks to that status your friend posted. The reason I mention this is because Firefox's new 17.0 update includes many features, but the one that's been making the rounds online is the integration of Facebook Me...

Yesterday, Bryan Clark pointed out a new option on Verizon's privacy settings that gives new customers 30 days to opt out of a data sharing program that gives advertisers information on basically everything you're doing on your new iPhone (or any other smartphone).

There's a lot of firsts that President Barack Obama can claim, like being the first POTUS from Hawaii, the first to publicly support same-sex marriage, and of course, the first African American to hold office. One of his coolest firsts, though, is that he's the first American president to ever brew his own beer in the White House. And thanks to a Redditor who filed a Freedom of Information Act request, two recipes have been released so that home brewers everywhere can give them a try.

You can take some absolutely gorgeous photos using the natural reflection that appears in people's and animals' eyes. With the right angle and lighting, you can even see a detailed picture of what the subject was looking at when the photo was taken. Photo by Martin Cathrae

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

Watch this video to put your Eee PC in advanced mode, which makes it look like XP. The steps are as follows

For years, you could only make purchases with your Apple Cash balance on your iPhone using Apple Pay, but a new update gives you the power to set up a virtual card number you can use just like a debit or credit card.

The art of fuzzing is a vital skill for any penetration tester or hacker to possess. The faster you fuzz, and the more efficiently you are at doing it, the closer you come to achieving your goal, whether that means finding a valid bug or discovering an initial attack vector. A tool called ffuf comes in handy to help speed things along and fuzz for parameters, directors, and more.

The Pi-hole project is a popular DNS-level ad blocker, but it can be much more than that. Its DNS-level filtering can also be used as a firewall of sorts to prevent malicious websites from resolving, as well as to keep privacy-killing trackers such as Google Analytics from ever loading in the browser. Let's take a look at setting a Pi-hole up and customizing a blacklist to suit your needs.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

The biggest new feature in Android 10 is the system-wide dark mode. Both Samsung and Google phones have it, so third-party support is everywhere. The only problem is OnePlus forgot to include a way to quickly toggle dark mode on and off.

After the lackluster update that was iOS 13.3.1, we beta testers were in need of some excitement. Thankfully, Apple delivered the goods with iOS 13.4 developer beta 1, introducing fun new features like fresh Memoji stickers and a new Mail toolbar. Of course, that update was for developers only, so we public testers are thrilled that Apple just released the first public beta today.

We might never truly know all of the colors behind old and classic black-and-white photos, but thanks to technology, we can get a pretty accurate colorization. Although Photoshop is a popular way to colorize these images, you can now use your iPhone, along with a nifty shortcut, to transform and give new life to vintage photos.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

The iPhone X, iPhone 8, and iPhone 8 Plus may be some of the fastest phones of 2o17. However, the equally new iOS 11 isn't quite as impressive. That being said, Apple is continuing updates to the developer beta for iOS 11.1, as it releases the 5th version of the beta today.

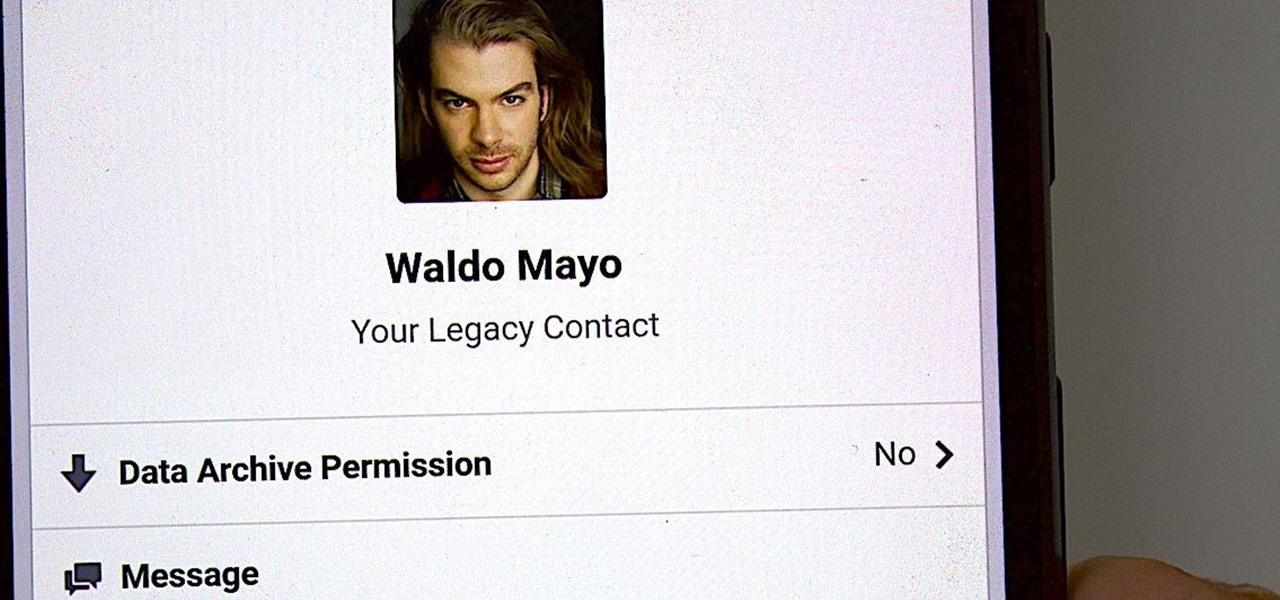
It's time to set your Facebook "Last Will and Testament" straight. Do you want to assign a contact to look over your account, or would you prefer to have all your online memories fade away the minute you die? It's a tough decision, but with a little time, you can set up at least one of these options to ensure that your account isn't left to sit pretty without you for the rest of time.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Sometimes it's impossible to concentrate — let alone direct your personal assistant Siri — when someone is blasting music on their phone or talking to thin air. I mean I'm loud, but not that loud.

Rumors that Apple is honing its automated car technology have skyrocketed. Thanks, now, in no small part to some enterprising members of the media who leaked the names of Apple's self-driving car team to the public.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

Months before London-based Jonathan Moon would turn 30, he started musing over how to celebrate. While he had rung in past birthdays at home, he wanted to do something out of the ordinary as a farewell kiss to his twenties. A short ski vacation with friends felt like the perfect idea.

One of the only downsides to the Pixel XL is that Google's flagship phone does not have stereo speakers. But if Android's awesome development community has taught us anything over the years, it's that limitations like these can be bypassed with some creative software tinkering.

With the release of the Mirai source code, botnets are back in a big way. In the early days of botnets, zombies (infected hosts) would report to IRC (Internet Relay Chat) channels for CNC (command and control) instructions. Modern botnets have evolved, but they continue to use the same concepts as their predecessors.

The decadent, chewy, fresh-from-the-oven brownie is a classic American dessert. US History Scene states that the first brownies ever made were a result of socialite Bertha Potter Palmer's request of her chef at Chicago's Palmer House Hotel in 1893 "to create a dessert that could be tucked into a box lunch for ladies to eat while attending the Columbian Exposition."

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Greetings my fellow hackers.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.