There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

Because of its ability to place digital content into the real world, augmented reality lends itself well to artists and creatives.

It is a great time to be a mobile gamer. Not only are there millions of mobile games on the Play Store and App Store, but thanks to some recent developments, we can also even play PC games. AMD recently released an app, which, among other things, lets you play your favorite PC games on your phone.
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

Already a powerhouse for its graphic design tools, Adobe is making a run at the 3D content creation realm dominated by Unity and Epic Games by acquiring software maker Allegorithmic.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

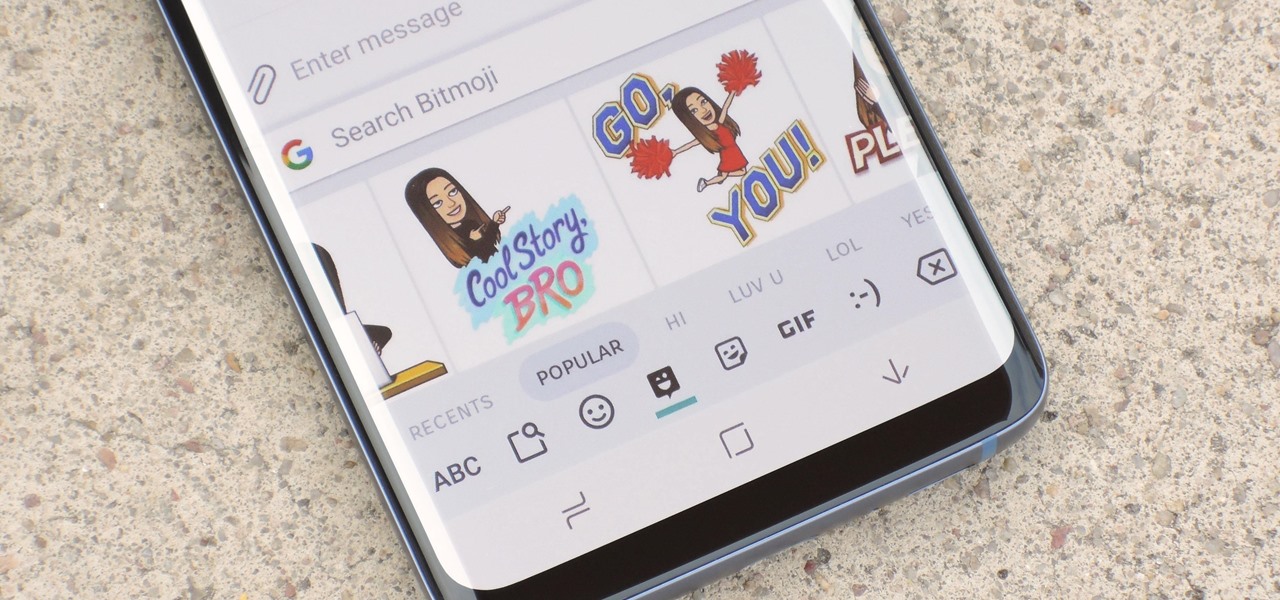
Bitmoji are personalized emoji that look like you and can be used to make funny memes or snappy replies. Normally, you have to find one of these reaction emojis in the Bitmoji app, then use Android's share menu to send it to the app where you ultimately want to post it, but there's a much better way.

On Monday, with just days left before Christmas, Lowe's dropped a surprise augmented reality treat in everyone's lap: a brand new Magic Leap One app.

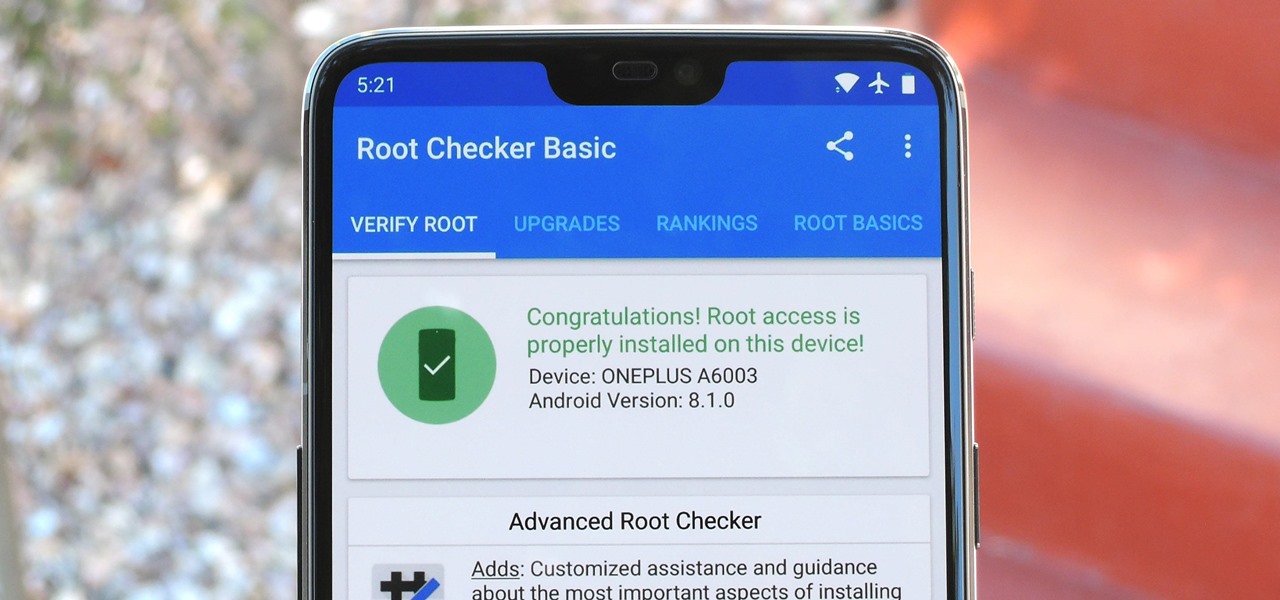
It's the icing on top of your cake (or whipped cream on top of your Android Pie) of despair. You may have not had the easiest time rooting your device, but you feel like you overcame all of the obstacles. Only now to discover that those very apps and mods you were rooting for still won't work — and the signs point to a lack of root access. Don't lose hope, because we have some tricks up our sleeve.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Perhaps you've thought about rooting your OnePlus 5, but thought again when you heard SafetyNet would prevent you from using apps like Google Pay, Pokémon GO, or Netflix. Those are valid struggles when you root using traditional methods. There are no such worries when using Magisk, as it masks the fact that your device has been modified.

Do price tags on mobile games give you pause? We get it. With so many freemium games out there, it's tough to justify spending three or four dollars on a game for your iPhone or Android device. That's why you wait for moments like this one, as both "Reigns" and "Reigns: Her Majesty" are aggressively on sale.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

Among iOS 11's many criticisms, one of the more surprising complaints came from parents worried that Apple wasn't doing enough to monitor and control their children's iPhone usage. Apple seems to have taken these issues to heart, as iOS 12 introduces new and improved parental controls to help encourage healthier mobile habits for kids.

Uber as a service is great, but using it requires you to hand over your location data to the company. What's worse is that you may be giving them precious access to your GPS even when don't have the Uber app open. This is both a major privacy issue and a drain on your battery. Fortunately, some of you can fix this.

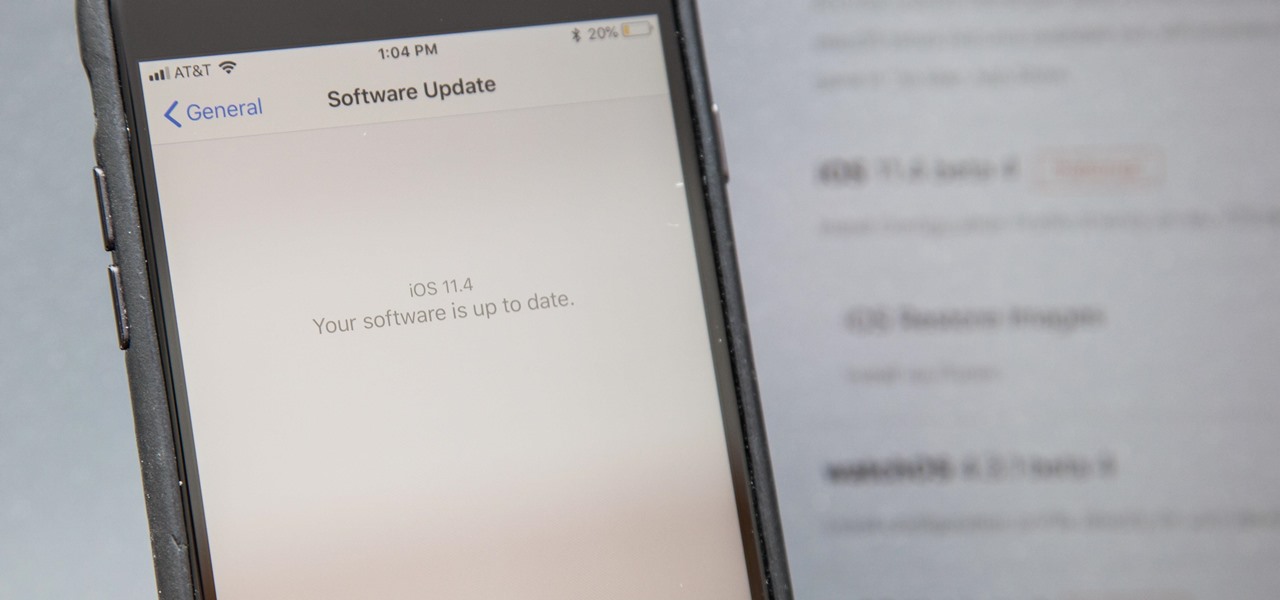
Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

You're at the bar, but your friend can't find you. You could call them, but that wouldn't feel very 2018. Instead, let your iPhone do the talking. Right in the Messages app, you can easily send your friend your current location — all without interrupting the friends you're hanging out with.

For the longest time, the only clickable link you could throw up on Instagram was in your profile's bio, and that's still true for a lot of users. The only way to add a clickable link aside from the aforementioned one is in an Instagram story, where users checking out your story would swipe up to load the webpage before going back to finish your story.

Just days after Bose did its best to frame a pair of glasses frames with spatial audio as "augmented reality," a patent application from Magic Leap, surfaced on Thursday, March 15, offers a similar idea, but with real AR included.

Not all microwaves are created equal, so when you use the recommended cooking time on any microwaveable meal, chances are you're actually cooking the food too much or not enough. And unless you're really good at mental math or have a virtual assistant that's smarter than Siri and Google, you have to do things the long way — but not with these helpful apps for iOS and Android.

In January, ZTE announced they would be conducting an Oreo beta program for Axon 7 users to test Android 8.0 before the masses. Since then, no additional information was released — until today, when ZTE finally opened up the Oreo beta to US customers.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

Some phones have a feature that turns your screen white for a second when you're taking a selfie in dim lighting. This does a great job of illuminating your face in a pinch, but there are two problems with it: First, not all phones have the feature, and second, it doesn't work in third-party camera apps like Snapchat and Instagram.

It has not been a good year for Apple, as far as software scandals are concerned. From autocorrect nuisances to secret slowdowns of aging iPhones, Apple has had a lot to answer for. iOS users now have another issue to worry about — it's being called "chaiOS," and it's wrecking havoc on iPhones with just a simple URL.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

The Pixel 2 and Pixel 2 XL were built by different manufacturers. This is pretty common knowledge among Android fans at this point — Google's smaller Pixel 2 was built by HTC, while the larger Pixel 2 XL was built by LG. What would the Pixel 2 XL look like if HTC had followed through and delivered on the larger phone for Google? Today we have some answers.

Here are a couple of quick bits, and also a little bit of a teaser. If you know of my old YouTube channel and are a developer, you may be aware of the "Scale and Rotation System" tutorial series I did. I then started working for Next Reality and never finished it.

The Xposed Framework is still alive and kicking despite the fact that development has slowed down a bit lately. Rovo89 is the only true developer behind Xposed, so it's really a one-man show. This means the popular root mod doesn't typically support the latest Android version, but it's usually only one version number behind.

Zently — the mobile app for renters — is taking on Venmo with its newest feature. Traditionally used to automate rent payments, deliver rent checks for free, and communicate with your landlord, it now allows you to connect to your bank account and split bills with housemates. Following the addition of Zelle to several major banks apps — to allow users to transfer money to their contacts — the battle of the mobile payment apps is getting increasingly fierce. With this new update, Zently is als...

Anchor has been called the audio equivalent of Snapchat. The app lets you record audio and broadcast it to whomever you follow. If you haven't heard of the app, get familiar with it because it has announced an easy way for you to record and publish podcasts from your smartphone.

For $0.25 per transaction, PayPal will soon be allowing you to transfer money through their app that will get delivered within seconds rather than days.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.