Your Android phone could be listening to ultrasonic ad beacons behind your back. The unwelcome news comes year after app developer SilverPush promised to quit using its (creepy!) eavesdropping software.

It's no secret that Samsung had a lot of bad press this year. Despite this, we've reported how, even with the massive negativity in the media, Samsung has been expected to have an excellent Q1. Not only have those expectations been confirmed today, but Samsung has announced they are also working on a new flagship smartphone. One that some say could be the Note 8.
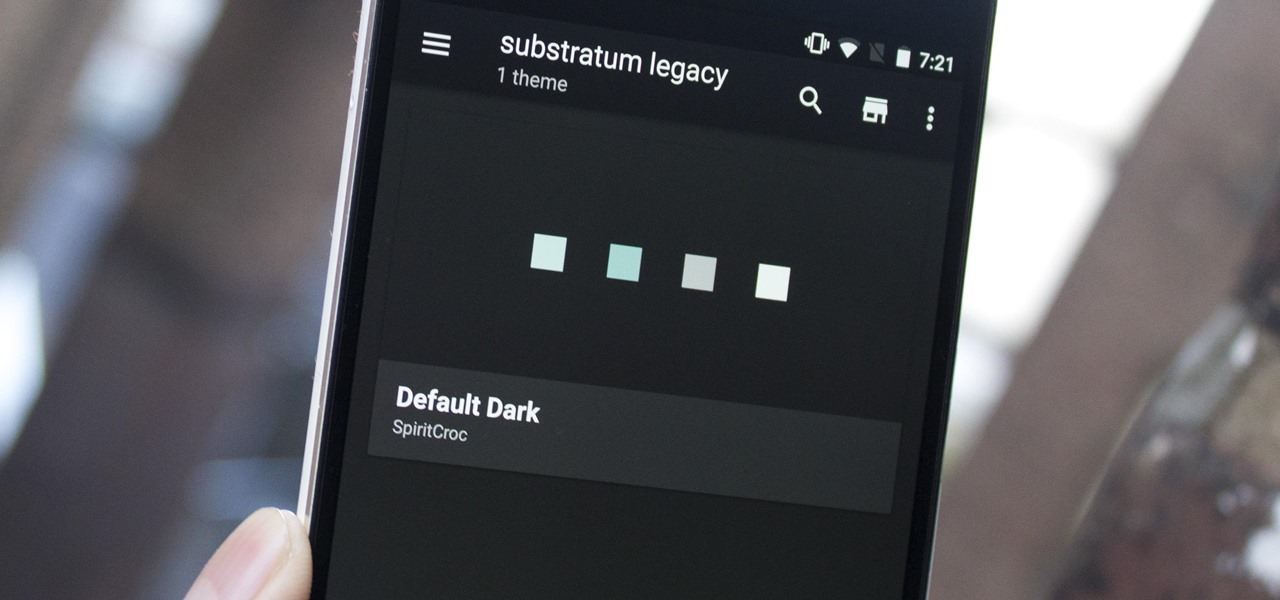
Perhaps one of CyanogenMod's greatest features was its built-in theme engine. It wasn't perfect, but it got the job done and gave users a unique look. Now that CyangenMod is defunct, and the developers behind its successor, LineageOS, have confirmed they won't be continuing the theme engine, users have to find another way to theme their devices. No need to fear, though, Substratum is here.
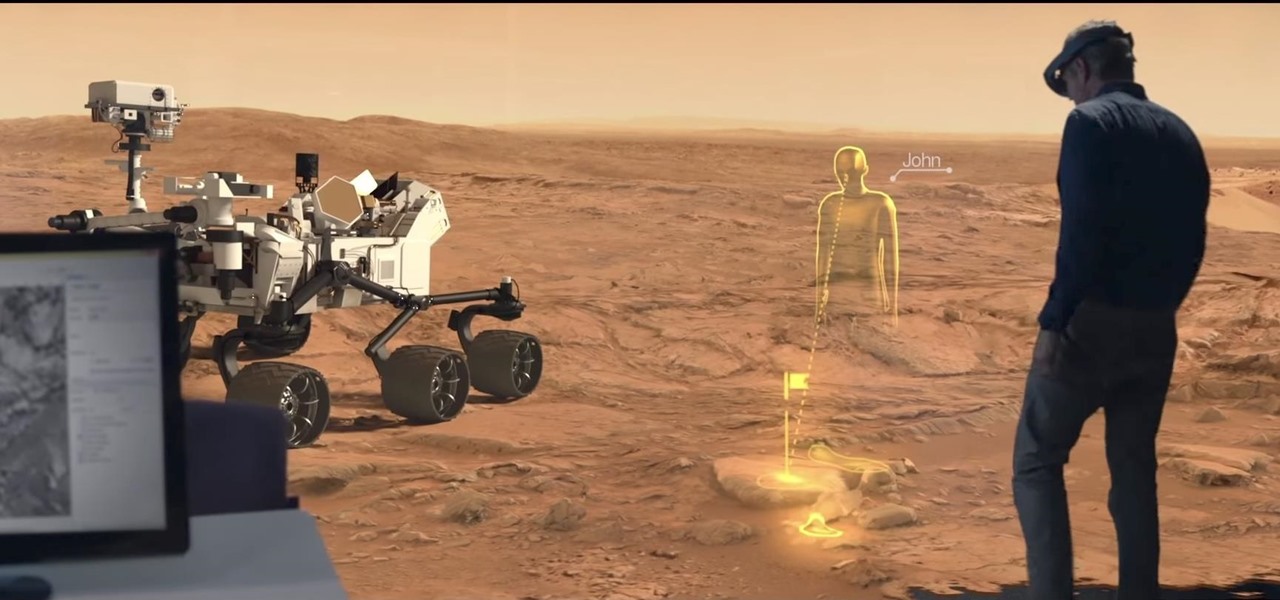
Apple likes to play their cards close to the vest, don't they? The iconic company doesn't usually reveal much about their projects until it's time for an official announcement. But sometimes ... They can't stop a leak of information from happening, or they just leak the news themselves like Steve Jobs used to. That brings us to today's news. It appears the tech giant has hired an augmented reality specialist from NASA to join their AR team.

A federal judge wants answers after an Uber engineer accused of data theft pleaded the Fifth in the ongoing Waymo versus Uber battle. This privilege would protect the accused, Anthony Levandowski, of self-incrimination and handing over specific documents demanded in a previous subpoena and forthcoming deposition.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

As someone who grew up adamantly complaining every time my parents dared to turn on talk radio in the car, I can admit it's a bit weird that I have a love affair with podcasts. I can't help it! Even though podcasts are essentially the modern-day customizable talk radio, I choose to defend my all-out obsession with pointing out how popular they are (I mean, SNL even picked up on the trend).

Rumor has it that a gang of hackers—or possibly, one lonesome individual—holds the power to remotely wipe millions of iPhones and iCloud accounts, unless Apple coughs up some ransom money by April 7.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

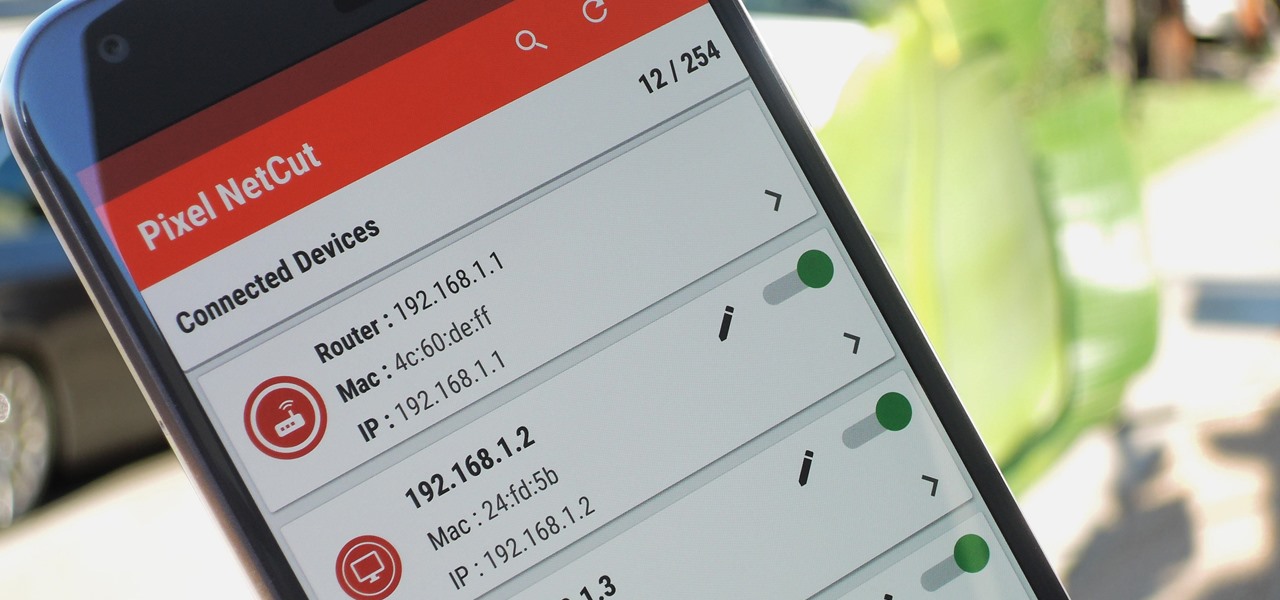
Let's say you gave your Wi-Fi password to your neighbor a while back, under the assumption that they'd only use it while they were at your house sharing stuff via Chromecast. But now, your connection is slower than it normally should be, and you have this sneaking suspicion that the dude in apartment 3C is flat-out piggybacking off of your home network.

There's no question about it—Skype is one useful program, but has always been lacking in the mobile department. On your desktop, Skype works just fine and all of its options are available for usage. However, the same cannot be said for Android. On Android, you can't even change your status to "Away" or "Invisible."

No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

Designing for mixed reality, especially for the HoloLens, can present unique challenges. Dong Yoon Park, a Principal UX Designer at Microsoft with a passion for typography, recently gave a talk to the Windows Holographic Users Group Redmond (WinHUGR) about the pitfalls he ran into trying to convert what started out as a 2D iOS app 5 years ago to the newer 3D Holographic frontier with Unity.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

If you're an Android fan, you're probably familiar with Qualcomm's Quick Charge technology or, at the very least, what it can do. Quick Charge 3.0, the third generation of Qualcomm's fast-charging technology, is built into most Snapdragon SoCs and it's what lets you charge your phone's battery up to 70% power in just 30 minutes. What's not to like?

Google's Pixel phones have a feature that lets you swipe down on the fingerprint scanner to open your notification shade and Quick Settings panel. It's one of those features that make you wonder why it wasn't there in the first place, since it gives you another way to interact with your device, and your fingerprint scanner isn't being used while you're screen is on anyway.

Starting with Marshmallow, Android added a built-in theme engine called "Runtime Resource Overlay," or RRO. This theme engine was intended to be used only by smartphone manufacturers, not end-users, so unlike Cyanogen's CM Theme Engine, owners can't use it to change the look and feel of their phones.

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

When you're driving, the last thing you need to be doing is messing around with your phone. But these days, people expect you to be available at all times, so the text messages continue to flow in while you're on the road. It's a terrible distraction, and one that is responsible for 25% of all car wrecks in the United States.

With Touch ID enabled, your iPhone needs to scan your fingerprint before you can access your home screen or last app used. Before it unlocks, your iPhone might request that you press the Home button, adding an unnecessary step between you and your data. However, you can turn the feature off so that you don't need to click any buttons to unlock your device.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

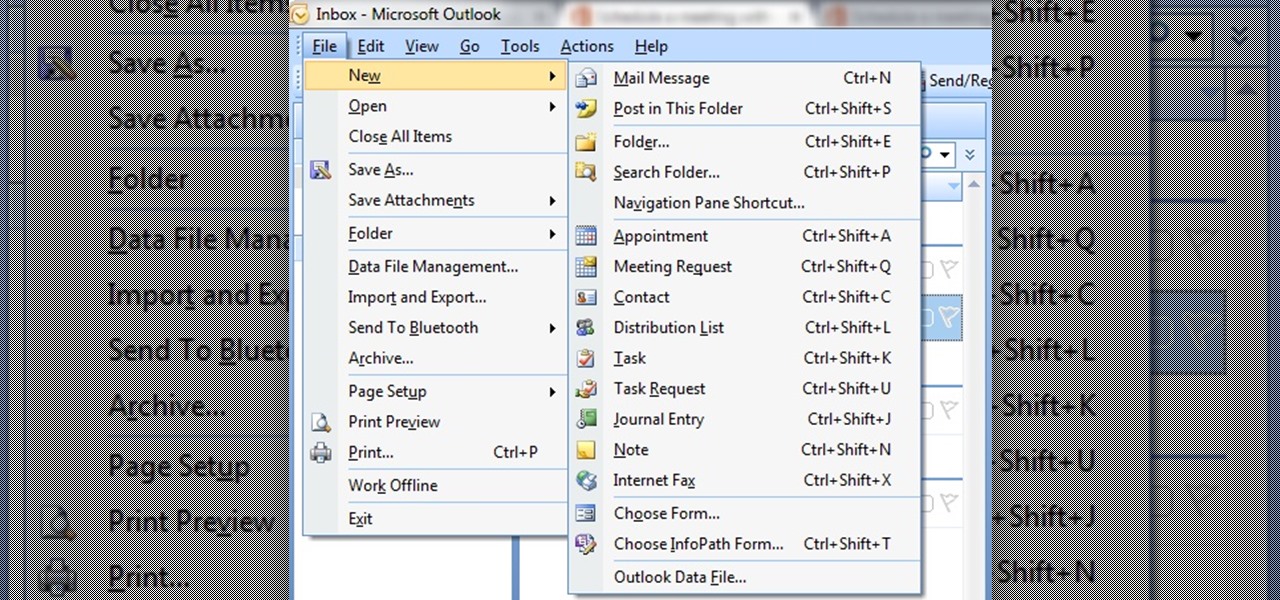
In this tutorial First, we will discuss what a meeting is, How can we schedule it in Outlook. A meeting can be defined as a mass of two or more people have a common motive. All the people present in a meeting can share their ideas and exchange information, to carry out the actions to achieve their goal. This tutorial helps those people who are looking for the steps to Schedule a Meeting in MS Outlook.

If you're looking to customize your Android beyond its stock options, things can get confusing quickly. One of the best places to get into developer mode is the XDA forums.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

Hey everyone, this guide will show the process of stealing your victims Facebook credentials. This is a followup to my previous post.

An accelerometer/gyro goes onto an Arduino board and transmits the angular motion of the skateboard via Bluetooth to a virtual reality game I made for Android phones and Google Cardboard.

No doubt you internet-savvy folks have seen the incredibly beautiful rainbow bagel going viral all over the country—and if not, let me educate you on its multicolored brilliance. Crafted by the brilliant bakers at The Bagel Store in Brooklyn, this cheery creation has actually been around for 20 years now. Watch the video below to see how the colorful roll is created.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

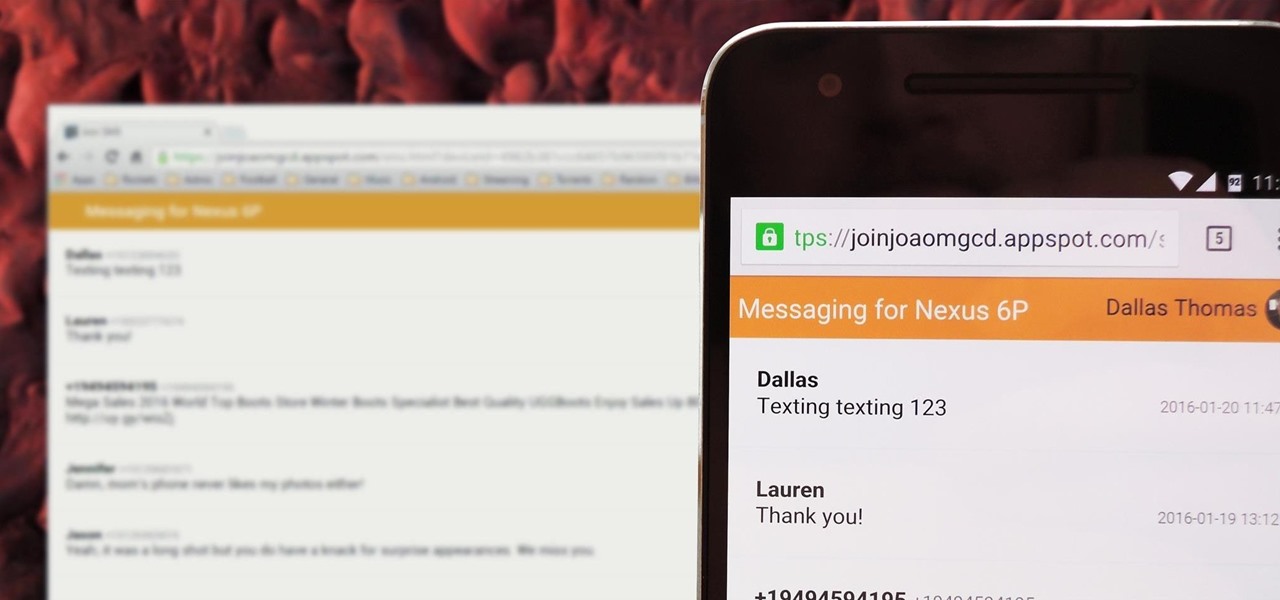
There's no iMessage app on Android, so unlike the folks who own both an iPhone and a Mac, we have to rely on third-party solutions to send and receive SMS messages from our computers. But on the bright side, this means we don't have to buy an exorbitantly expensive desktop or laptop to respond to texts when our phones are out of reach, because Android is all about cross-platform compatibility instead of chaining you to an ecosystem.

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

Some of the best images I've seen were shared via Snapchat, but once they're expired, they're gone forever, with no way to view them again unless I want to take a screenshot. But that will, of course, alert the sender.

hello hackers,newbies and followers of this great community, after some research here in our community, I noticed that there is not even one tutorial that teach Web Development. We have a lot of tutorials on how to hack web site but many do not know exactly how a web site is composed, then I decided, meeting the community's needs, begin to teach people how to develop web sites.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Video: . Being one of the most popular DIY/maker projects around, Musical Floppy Drives are nothing new. However, myFloppyDriveOrchestra includes a few unique features, which separate it from the crowd.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.