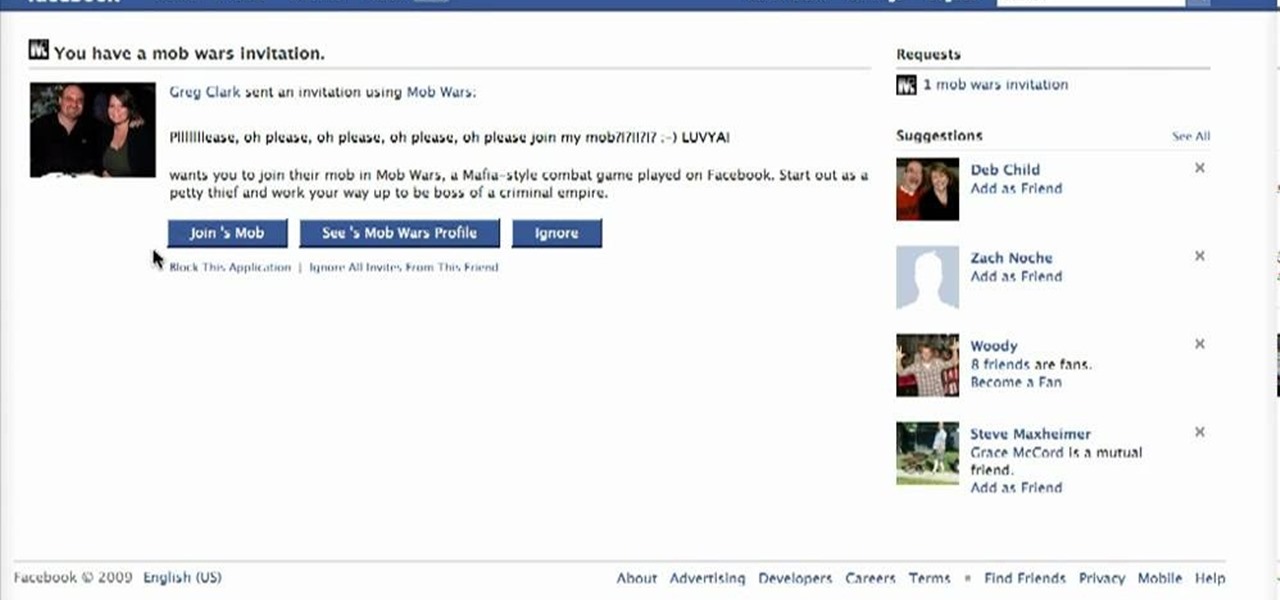
In this how-to video, you will learn how to block third party applications on Facebook. On your main page, you will see requests on the right. Click on the request to check the invitation. You will be presented with a few choices. If you are never planning on accepting an invitation to the application, you can click on the Block Application at the bottom. You can also ignore all invitations from a person by clicking the link with the same name in the same page. This will make using Facebook m...
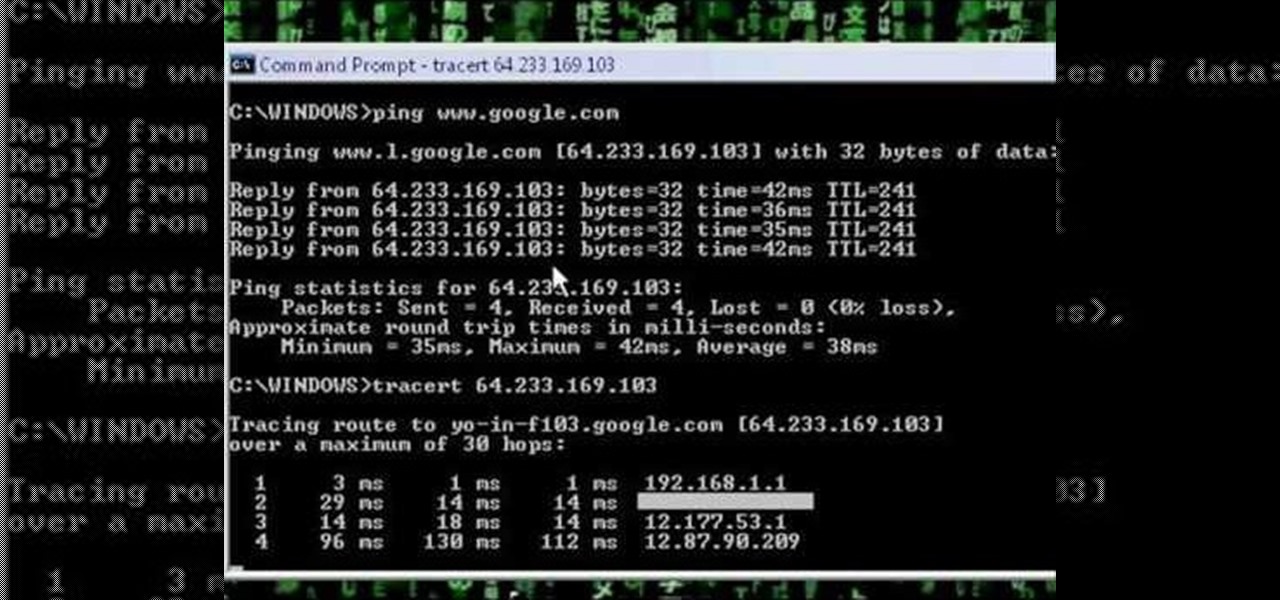
A network security tutorial on using ping and tracert to show th IP of a webserver, your own IP, your ISP's IP, who they connect to, and what computers your request goes through before reaching a destination.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.
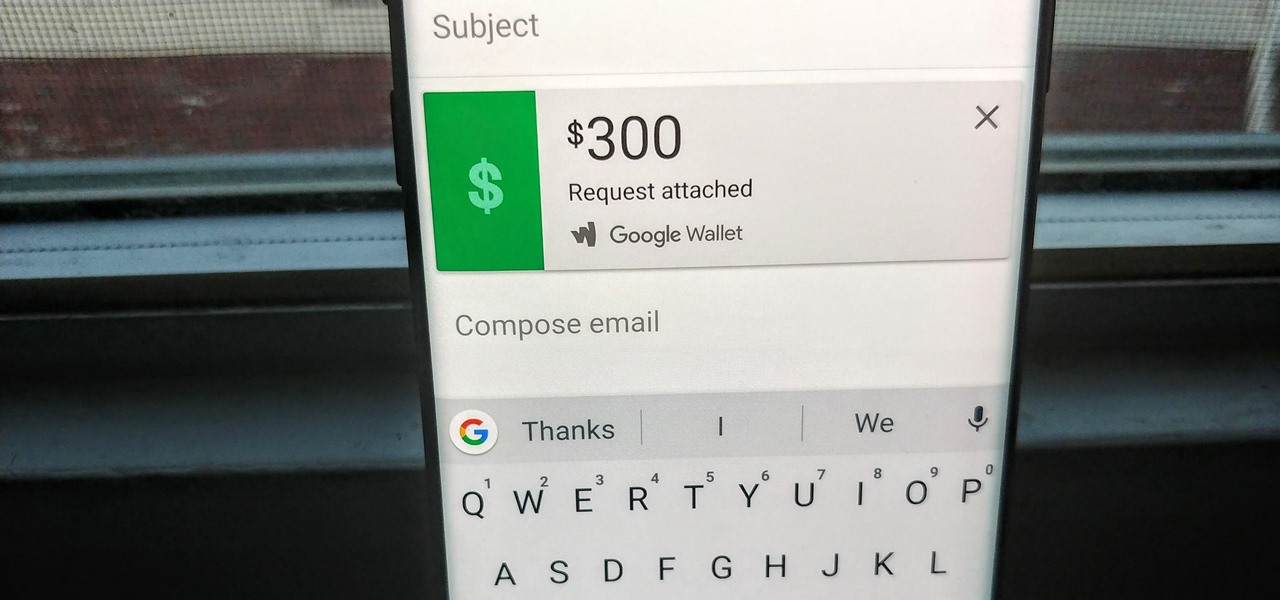
Since its debut in 2004, Gmail has become the go-to email service for the internet at large. Over 1.2 billion people use it, so Google has wisely continued to add features that address the needs and wants of its diverse user base. For US and UK users, one of these new features is the ability to transfer money.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

There are a number of reasons why you might want to trick a web server into thinking you're on a different operating system (OS) or web browser. One might be that you want to test the mobile version of your website from your computer. Or perhaps for some reason a website is restricted to a certain OS or browser and you wish to circumnavigate that barrier. Today's guide shows you how to do just that!

Military service records can teach you a lot about a person. If you want to see the service records of a friend or family member to prove their service or simply research your past, watch this video to learn how you can.

In this clip, you'll learn how to make a call to an external website from within a Silverlight app. Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

If you want to look like the sexy bombshell Megan Fox, then pull out your bag of tricks (makeup bag, that is) and follow along to this makeup tutorial to see how to mimic Megan Fox's super sexy looks. She's definitely one of the hottest actresses in the film industry today, and her makeup looks are in constant request.

Ditch those wimpy flat strands in favor of touchable volume this summer by watching this hair tutorial by MakeupByTiffanyD. After all, there is a reason that "Victoria's Secret hair" is the most requested hairstyle year-round by beauty-saavy gals all over.

This video by Wizard demonstrates how to draw a graffiti design that he specifically describes as easy. For the novice tagging artists out there, this video is a great place to start improving your design and drawing skills in pen. Get to practicing!

Hard-working, request-taking graffiti artist Wizard spits his game all over this design, a script tag of the name of viewer Serk. It bears all the earmarks of Wizards clean, traditional style, and as with all of his work would make a very rewarding exercise for any aspiring graffiti artist.

The master of online graffiti design videos Wizard is working his magic on another user-requested design, this one of some very elaborate script. He does work with a pencil underdrawing this time, but this does little to downplay the sheer skill necessary to draw something like this so quickly.

For those among you looking to improve you small-scale pencil-and ink graffiti skills, you could not ask for a better silent teacher than Wizard. His viewer-requested drawings always demonstrate a high degree of skill while being simple and slowly-done enough to allow his fan to emulate him and improve their own art. His trademark well-chosen electrofunk soundtracks are perfect background music for the graffiti creation process.

Talented graffiti-artist-for-hire Wizard here demonstrates a user-requested drawing of a cholo figure and some very elaborate script. As will most of his demonstrations, he works in pencil and black ink on grid paper, creating small and somewhat austere designs with undeniable virtuosity and charm. His demonstration services are quite a bargain at only $5!

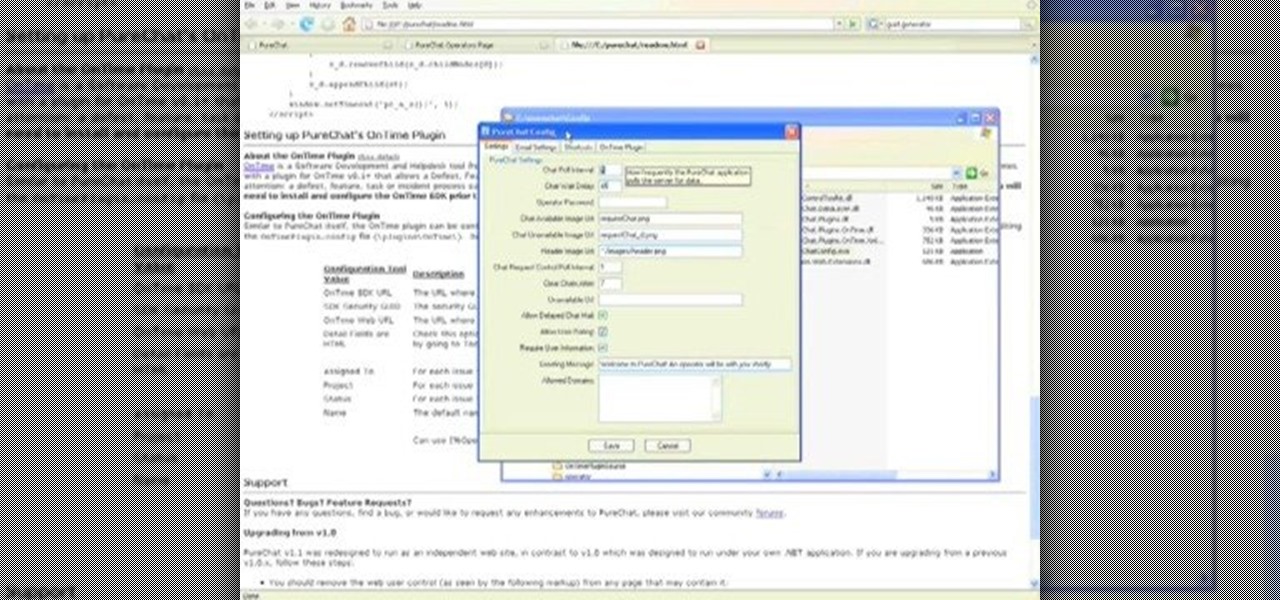
PureChat 2008 ships with an OnTime plug-in that allows you to quickly turn live web chat conversations into defects, feature requests, incidents or tasks in OnTime -- with just a few mouse clicks!

This is the second version of 'How to build a Custom Built Model Rocket' with requested corrections. This guidelines provide you with both written and demonstrative instructions. Enjoy building your very own Custom Model Rocket from scratch and have fun with model rocketing.

In this video tutorial, Scott Golightly shows how to implement a simple HttpModule that uses the BeginRequest and EndRequest events to store some data about the request and later display that data to the user. Scott also shows how to register the module in the Web.config file.

In this video tutorial, Scott Golightly shows how to create an ASP.NET HttpModule to “rewrite” the URL when a request for a web page comes in. You may want to rewrite URLs to create friendly URLs or to direct an old URL to a new URL. We will look at the code needed to implement URL rewriting and also how to handle page post back events.

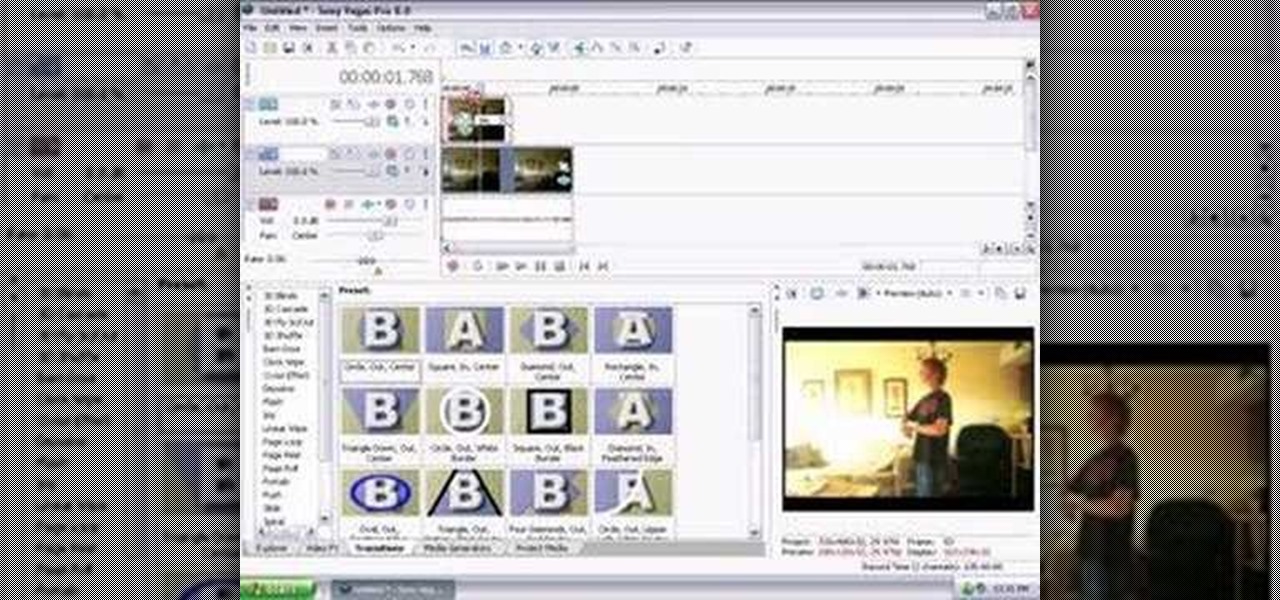
This tutorial teaches you how to teleport you or any object, out of a scene, but still leave the scene behind using Sony Vegas.

After numerous requests for help, I've made a "how to" for the pencil trick. -Eric

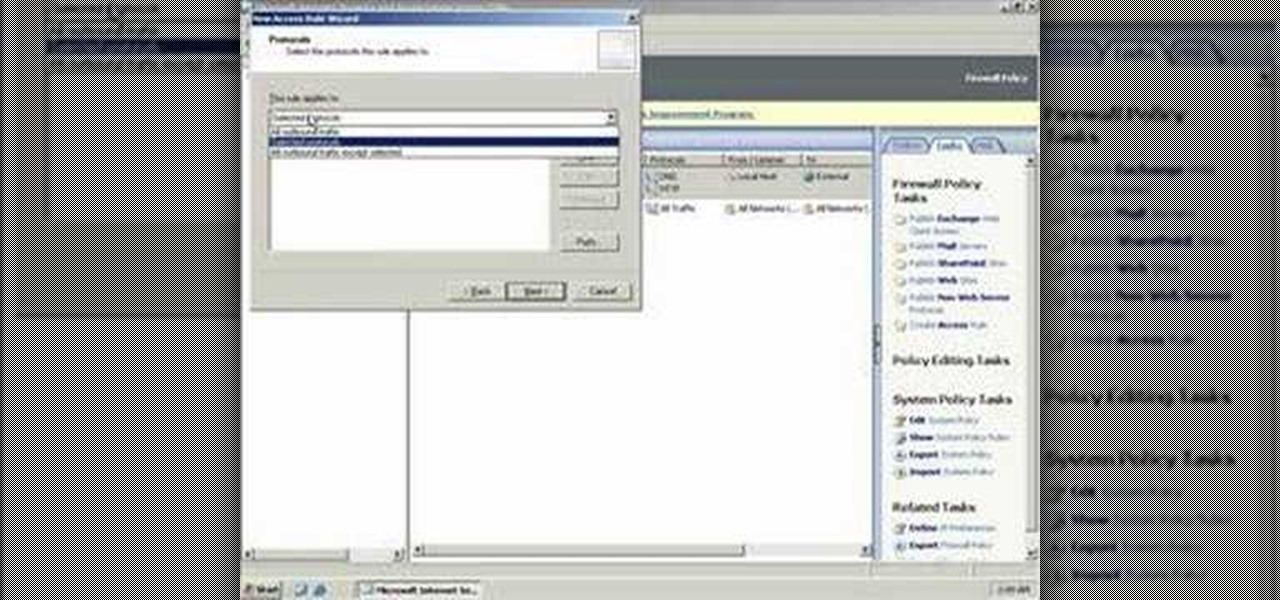
One of the uses of an ISA Server is to act as a proxy server. A proxy server allows your Windows XP and other desktop computers to make requests to the ISA Server and the ISA Server will then go and fetch the results from the internet or, if the ISA Server has cached the page(s), it can serve the pages from cache thus speeding up client browsing.

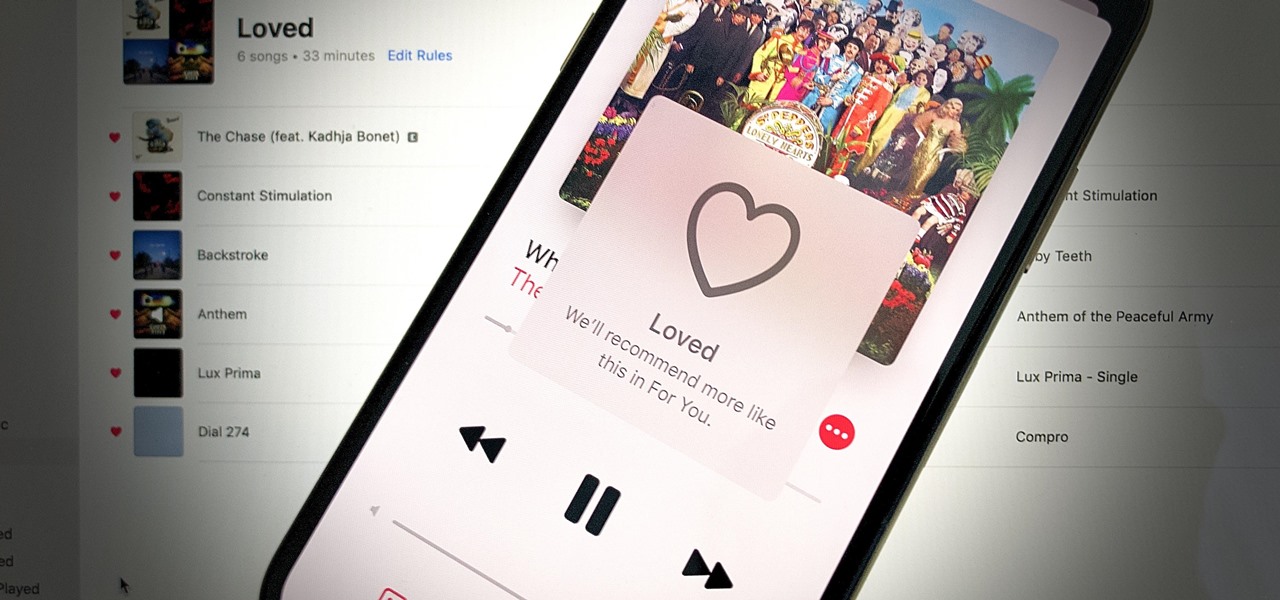
In Apple Music, loving and disliking songs is a great way to teach Apple's subscription service what type of tunes you like and which you don't. While it also seems like it should be an excellent way to keep track of songs you enjoy in the wild, there's no clear way to view all of your loved tracks in one convenient list. There is a way, however, but easy it is not.

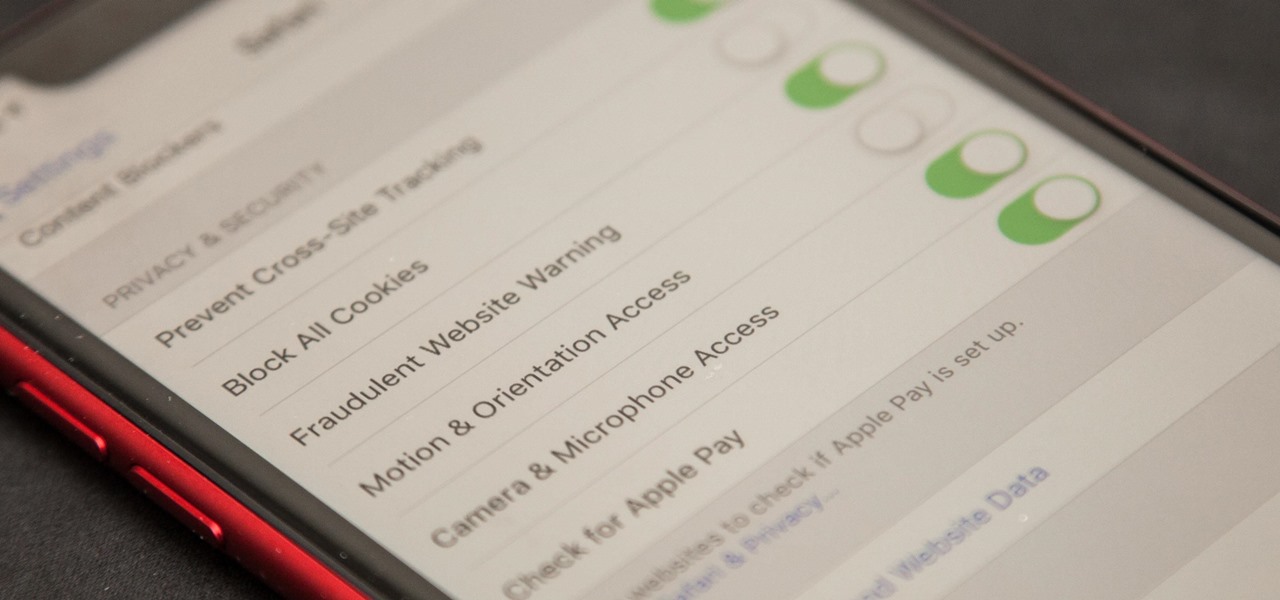
Apple first added the "Do Not Track" option to Safari in iOS 7, which sent a request to site owners and advertisers to not track your browsing activity. By tracking your activity, those third-parties could tailor content to you that you're more likely to interact with. While the feature was always opt-in, it's no longer a feature at all in iOS 12.2 on your iPhone.

Cross-site scripting is one of the most common vulnerabilities found on the web today, with repercussions of this type of flaw ranging from harmless defacement to sensitive data exposure. Probing for XSS can be tedious and time-consuming for an attacker, but luckily there are tools available to make things a little easier, including Burp Suite, Wfuzz, and XSStrike.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

In the changes to the App Store Review Guidelines for iOS 11, Apple has announced that developers must use the App Store rating API. The API was introduced in the iOS 10.3 beta period as something that would eventually become mandatory. Now, Apple has followed through on that promise.

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Graffiti maestro Wizard performs one of his trademark user-requested graffiti demonstrations. In this video creates an even more compact design than usual, creating the word UZI in fairly standard graffiti-script and elaborating it with some splatter patterns and a hatted figure popping out from the corner. His speed and technique, especially working without a pre-drawing, are simply remarkable.

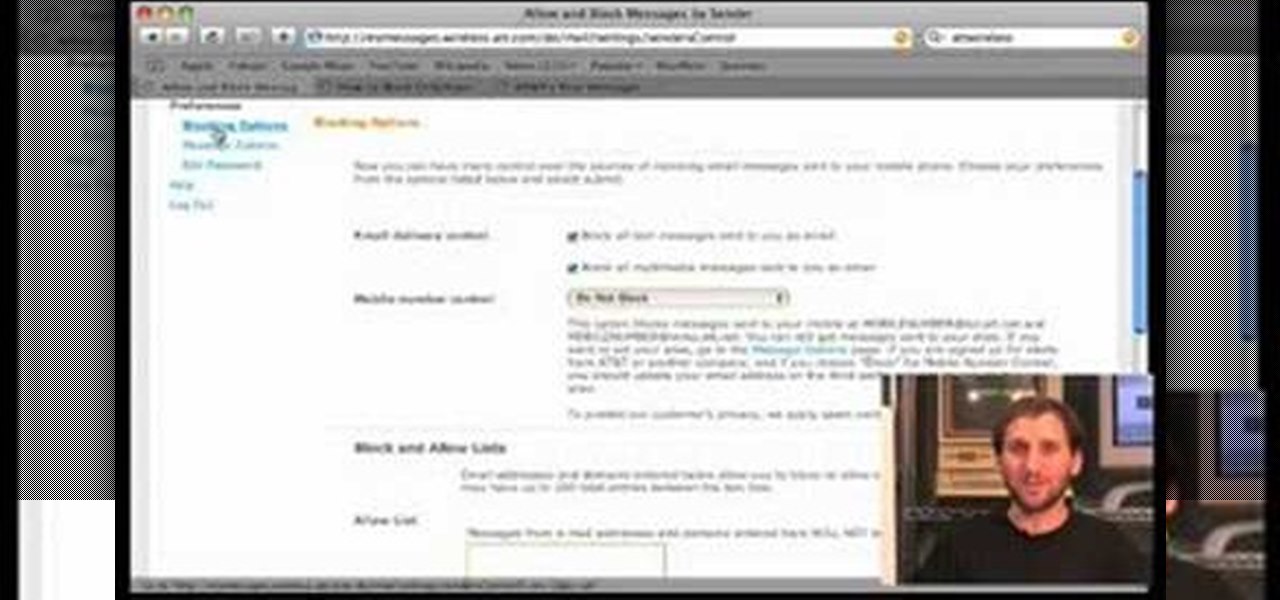
If you're among the throng of Apple iPhone users to refuse to pay $5 for a monthly SMS allowance, then each text message you receive, whether you like it or not, will run you $0.20. In this how-to, Gary Rosenzweig shows you how to prevent unwanted text messages by turning off the ability for someone to send you a text message via email. Learn also how to request that text messaging be turned off completely in this video.

Rob "Riki Tiki" Roy takes a vague request and brings about a classic. All you need is whiskey, sweet and sour mix, and a cherry for garnish. Sweet and sour mix can be added to any liquor to create a something sour cocktail. It's so easy.

This video will show you how to tether an iPhone 3G in Windows Vista so that you can use its internet connection on your own computer!

As requested by a few of you guys, here is a video you can follow to learn how to play the batman theme on your guitar. Hopefully, this will cover all that is needed. This is ideal for beginners, provided you can play power chords and have a little bit of musical and batman knowledge. Enjoy!

This tutorial video will show you how you can use various makeup products to make the MAC eyebrows. With these makeup tips, you can define your eyebrows and have them looking better in no time.

This week on Threadheads, the ladies of Compai are helpin' us out with a very special viewer request, plus we hang out and take a look into their popular DIY book series 99 ways. So sit back, relax, grab your sewing machine and get comfy.

This flower bracelet is very simple. It will quickly become one of your most requested items at any restaurant or party. This balloon bracelet requires two balloons.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.