Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.
In iOS 13, Safari has become even more powerful, especially when it comes to privacy. The browser will warn you when you create a weak password for a new account. Your history and synced tabs in iCloud are end-to-end encrypted now. And there are per-site settings that let you choose which domains can and can't have permission to use particular device hardware or sensors.
For some reason, the Slack app on Android and iOS is a little less customizable than Slack on other platforms, so you can't adjust the sidebar theme to different colors directly inside the app. But that doesn't mean you can't customize the look of your mobile app at all. It's just a little less convenient.
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.
For parents that have an iPhone X, things are about to get a lot easier for you in iOS 11.3, which finally lets you approve app and media downloads on your child's iPhone using Face ID instead of typing in a password.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

This little demonstration was a request to show how I die cut the Anna Griffin Flip card base die that was included in the Flip Card Kit. Step 1: Now Watch the Tutorial

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

These days, you can find a digital version of almost any form of entertainment. Being able to download or stream content is convenient for a lot of reasons—you can avoid going to the store and you never have to worry about late fees on rentals.

Video: . Requested by quite some people out there.

Chef Billy Parisi from Fix My Recipe responds to a request sent by one of his viewers, to "fix" a barbecue chicken skewers meal.

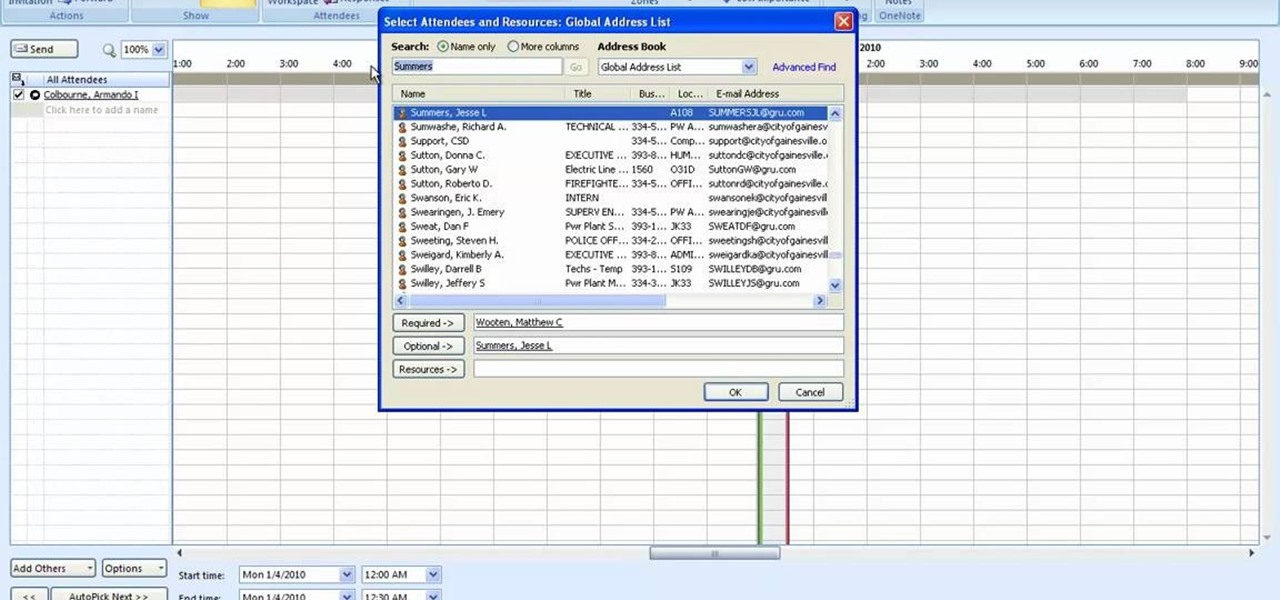
This how to video shows you how to setup a meeting using Microsoft Outlook. First, open the program. From here, click on calendar. Next, go to the upper left corner and select new. On the subject line, type in the subject of the meeting. In the body, type in what the meeting is about. Go to scheduling and go to the left and select invite attendees. From here, select the address book and search for people by their last names. Select who is optional and who is required. Click okay. You will see...

1. Open the web browser and type www.facebook.com and press enter. 2. In order to be a member you will have to first sign up as a facebook member.

When someone you love asks for money it can be very hard to turn them down; especially since you are usually put on the spot. Check out this tutorial and discover ways that you can help your friend without having to spend a dime, and make things easier for everyone.

This video shows how to change the advanced settings to make Firefox faster on Mac and PC.

Like it or not, she's one of the most important people in your spouse's life, so do what it takes to get her on your side.

What would be cooler than showing up at your prom with a famous celebrity? It's a long shot, but here's your best chance to make it a reality.

In this video from Laurie Ann Gibson, you will learn how to perform the choreography to one of Lady Gaga's most popular songs. This dance is straight out of the music video for "Poker Face" and now you can learn it on your own!

There just isn't enough space on airplanes for any one, even those on the shorter end of the spectrum. Top flight nightmares are usually being seated next to a screaming child, a person of large girth, or behind that jerk who reclines their seat for the entire flight. Most people aren't going to respond well to even polite request for courtesy, so that's when a little chair subterfuge comes in handy. Come prepared with a plastic zip tie and this simple trick. Watch this pranking tutorial and ...

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick like in response to something. But it doesn't have to be the standard Facebook thumbs-up sign — it can be any emoji you want.

The Federal Communications Commission (FCC) has cleared a path for Google to move forward with hand-tracking technology that could pose a major threat to Leap Motion.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

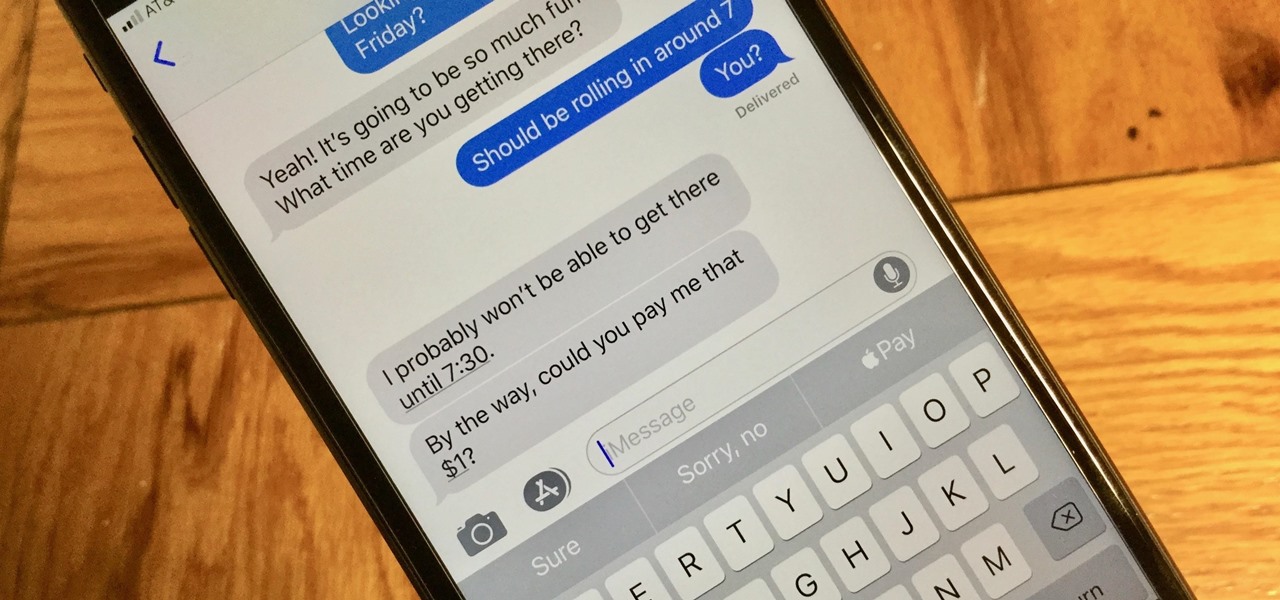
With Apple Pay Cash, you can easily and securely pay your contacts directly in your iPhone's Messages app. While you can always use the normal method of paying someone with Apple Pay Cash, there's actually a faster way, as long as your contact asks you for money in an iMessage.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

Instagram recently released their new Instagram Direct messaging feature in their Android and iOS apps, which lets users share private photos and videos directly with individuals or groups of up to 15 users. However, there are no restrictions on who you can send private photos or videos to.

What girl doesn't want Victoria's Secret hair? You know what we're talking about, ladies: Big, voluminous curls that look undone but not too messy and always goddess-like. It's the type of hair most celebrities wear on the covers of magazines and the most requested hairstyle in salons.

If you've ever been to a Marie Callender's restaurant, then you know their chicken pot pie is the most popular and most often requested dish. That's because chicken pot pies, while a rather simple concept, contain just enough bready goodness, veggies, chicken, and sauce filling to get you full and way satisfied.

As far as Chinese food goes, lo mien is the most requested complement to more savory meat and vegetable dishes. While clearly much more unhealthy than steamed rice (and maybe even friend rice), lo mien is oily, salty, and overall yummy.

Eric Mayo teaches us how to put together a resume as an ex-offender. Your resume should be a one page paper of all your skills and work experiences. If you don't have a lot of experience writing resumes, get help from friends who have experience. When you write it, add your name, address and telephone number onto it so you can be contacted. After this, you will want to list: objective, work experience, education/training, skills/strengths, and references. Remember not to list your references ...

If there is one hairstyle we all remember the late and great Farrah Fawcett by, it's her feathery, winged back '70s hair from "Charlie's Angels." The sexy style has had celebrity imitations up to this day and is frequently seen on Carmen Electra and Cameron Diaz. For some, this will always be Farrah Fawcett hair.

Celebrities look amazing in photos, on the red carpet, and really just in general, but they can attribute their awesome beauty to more than just their heavenly descent to earth.

The man was requested to solve a short, basic chemistry exercise. He starts by explaining the meaning of the terms involved in the problem: molecular mass, empirical formula and molecular formula. He also explains the way the are connected, for a better understanding of the way the exercise is solved.

In this video from Fashion Face, we are shown how to do a 1920's pink film noir makeup look that was actually requested by Courtney Love and originally created by a makeup artist for the brand Illamasqua. This is an extreme look, and there are a lot of tools and makeup involved, but it creates a really cool look, and provides some great tips.

Lady Gaga's Poker Face bow hairstyle! Lady Gaga’s hair bow was definitely a challenging request. I had to change it up to make it something more wearable for everyday. Well at least for me. I don’t think a HUGE-mongo bow on my head would work for me. A small petite one on the side is much more wearable. Watch this how to video to learn how to recreate Lady Gaga's bow hairstyle from the Lady Gaga music video Poker Face.

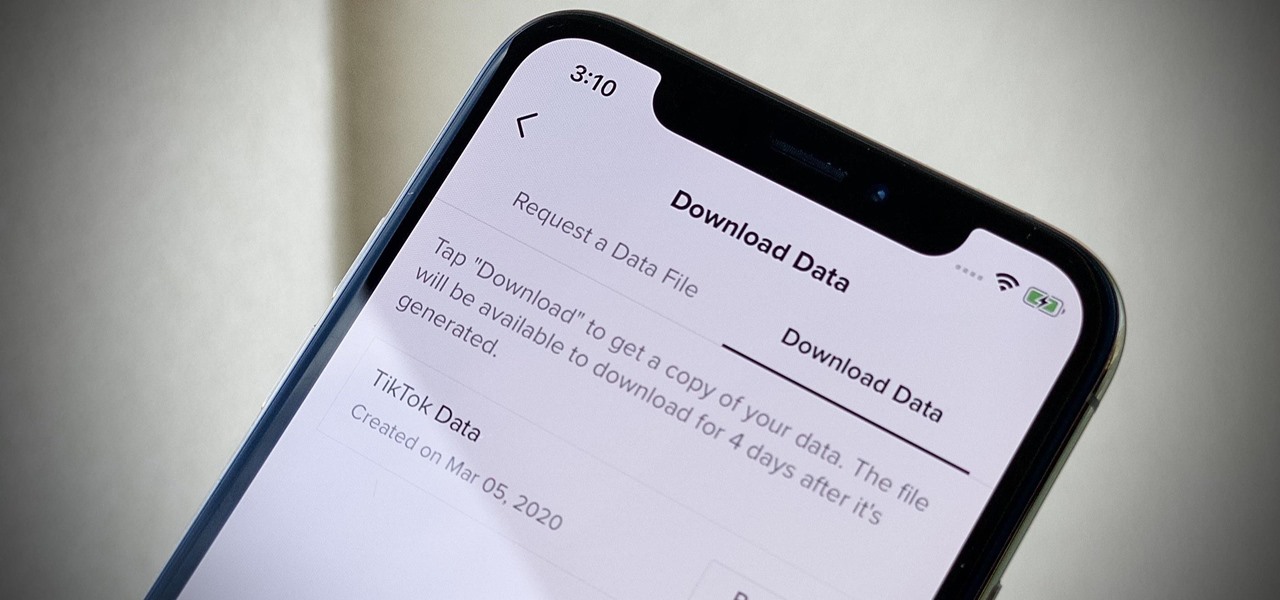
If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.