Last Friday's mission was to accomplish solving HackThisSite, realistic 2. This second mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend take down a racist hate-group website.

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

I can't believe it, but I've actually read about dozens of people getting their iTouch, iPhone, or iPad stuck in a bricked recovery loop and then going out to buy a new one. This is overly unnecessary. When it gets stuck in the recovery loop, some people mistake themselves by thinking that it is impossible to get the device back into DFU (Device Firmware Upgrade) mode. Getting the device back into DFU mode would at least allow us to jailbreak the device, essentially bringing it back from its ...

There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and advanced alarms, obviously, but not for the reasons people normally think.

Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen.

Welcome to part two in a series about steganography, the art of hiding things in plain sight. We are practicing steganography because it can be a useful skill if you don't have access to encryption software, or need a quick solution to make sure the sender and recipient are the only ones who are able to read your message.

Since its inception, Google+ users have been a loud, vocal bunch, and they've made their displeasure known about many issues, especially on the lack of support for pseudonyms, Google Apps, and brand pages. It's been especially galling for many Google loyalists, who found their Google+ profiles suspended, when they ended up violating the Google+ "common name" policy.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

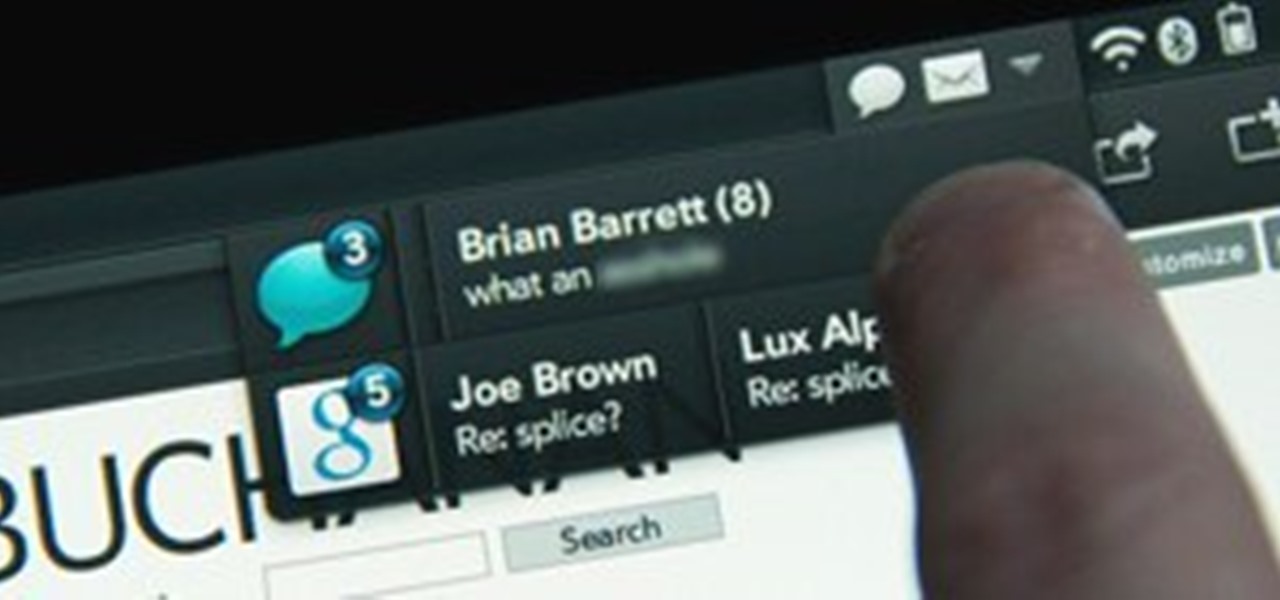
This week, we saw the implementation of collapsed comments, Google+ games were rolled out to everyone, and yesterday, there were several more announcements of enhanced features and tweaks.

These are the KGB Agent Guidelines as taken from 542542.com/guidelines. kgb Guidelines
On Thursday, March 9, there was a news story on the evening news about Khan Academy (NBC News). The story began when Sal Khan started tutoring his cousin in 2004. Since he was in Boston and she was in a different city, he decided to make and post videos on YouTube so anyone could watch the videos. Later he added videos for her brothers and for people that contacted him with requests for other videos. During this time Sal had a job that he later replaced with another job. Today Sal has 2010 vi...

The Clock Bloggers love Angry Birds so much, they decided to transform into... Angry Birds. With a little advice from our jolly bloggers, you too can jump into the video game fantasy vortex.

I confess, I’ve always wanted to put on an awesome holiday dinner in a big house that’s mine where I cook everything and it is AWESOME. Since I don’t yet have a house, I’ve only entertained in small ways (college parties notwithstanding, ahem), but watching Mom the Homemaker utterly tame Easter dinner this year gave me some great ideas for holiday entertaining. Check out the helpful tips I learned from watching her!

Blogs are a gold mine Some of the best sentences you will ever get when building your vocabulary can definitely come from blogs. The language and vocabulary usage in blogs is always changing to reflect how people talk in this day and age, and therefore are the perfect research tool for vocabulary sentence building.

This past Sunday, a group called Gnosis launched a massive hacker attack on Gawker media, one of the web's most popular blog networks (Lifehacker, Gizmodo, Jezebel, io9, Jalopnik, Kotaku, Deadspin and Fleshbot). 1.3 million registered users' passwords were compromised, and 188,279 of them were decoded and made public. The biggest takeaway? Many Gawker denizens use downright dumb passwords. (Guess they didn't see their own Lifehacker's story on avoiding such a thing.)

So you know what language you want to learn You've got your language picked out and you're ready to dive in, so let's move on to the first step in building a language foundation:

I've been on the inside of my box reflecting to what is on the outside. I live my life outside the box but occassionally have to get back intot the box to see what's going on... I have been on a 4 - 5 week non creative mode... Through this time frame... great people on Mikeyssmail have been still continuing to exercise their creativity... I'm so pleased to see that! Though many ideas come daily on what I could do next... I'm not motivated by just a simple request... I've allowed this same tim...

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

The motivation for the Add Shadow command, according to sources at Macromedia, was in response to a popular enhancement request to add "perspective shadow-like" capability to Fireworks. In this Fireworks 8 video tutorial you will learn how to use distort to add perspective shadows to your objects. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Add perspective shadows in Fireworks 8.

Today I was the only admin online at like 2:30 to 3:45. I had to deal with 27 people....asking me to World Edit all of their builds, and I explained how to apply online 3 different ways to 1 person...it was horrible. The other people who were online with me were getting super upset at this Guests. They were rude, and not able to understand super simple things.

What happened to please and thank you? When did asking someone to come look at your build degenerate into COME NOW or FOLLOW or sending out teleport requests to any and all currently on the server without asking?

In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time.

As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I am transitioning from C#.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. So you have a deep mine, an epic home, a bountiful farm, and mob traps galore, but have you ever considered linking them together into one cohesive unit? With the use of a minecart train station you can turn your disjointed Minecraft manor into a well oiled machine and cut travel times in half.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server.

Google+ is taking over more and more of Google's core properties. This week, we've seen several announcements from Google blogs about new products, new features, new looks, new integrations. If you're like me, you actually want to know where to go for all the latest information on Google products.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

For more than a decade, Interplay was arguably the best video game publisher in America. Their list of games is a who's-who of the most creative and forward thinking games of the '90s, including everything fromOut of This World to Alone in the Dark to Earthworm Jim to Descent. They've been around since 1983, but have fallen on hard times since 1997, when they became a public company. They were acquired by a French publisher who then went bankrupt. They were forced to close their internal deve...

This Null Byte is a doozey.

In a recent announcement, Hewlett-Packard announced that they're considering spinning off their PC hardware business, but even more recent was the decision to completely off webOS devices. Though they aren't eradicating the once popular Palm platform altogether, they are liquidating all of their HP branded smartphones and tablets in a fire sale, including the Pixi, Pre and Veer phones and TouchPad tablet, which is less than two months old.

We're ending the week with a lot of big announcements and updates. To date, Google+ has updated its name policy, but is still forbidding pseudonyms. Blocking people on Google+ became even easier, and yesterday, games on Google+ launched.

It's only been a few weeks, and already there are a lot of misconceptions and myths floating around Google+. Let's take a deep breath, and tackle some of the more prominent ones.

+Tom Anderson of MySpace has been very active on Google+ over the first week, and he's not shy with his thoughts on the evolution of the industry he once owned. Here's his take on this morning's Facebook announcement and Mark Zuckerberg's response when asked about Google+.

You've had a hard day at work and need to get out of the house, have a few drinks, but you don't want to go just anywhere—you want the right crowd and the right bar. For those nights, barhopping just isn't the answer, it's SceneTap.

Minecraft is the most basic and barren open sandbox building game. There are a limited number of materials and recipes to craft. But with these few building blocks, people have been able to creatively build some amazing structures and cities. There is a physical limitation, but the beauty of the game is turning that limitation into a strength.

http://www.thecolorawards.com/img/index/logo-index.jpg Type: Traditional print and digital, color only