
Pet Portrait Challenge: Xena by the Pool
This is Xena, the most remarkable dog I've every had the privilege to own and love and take care of. RIP 5.18.2011. This was taken with a cheap $59.99 camera.


This is Xena, the most remarkable dog I've every had the privilege to own and love and take care of. RIP 5.18.2011. This was taken with a cheap $59.99 camera.

The Ironkey is a high security thumb drive designed to provide strong AES encryption, tamper resistance and other security services. Some of the topics covered will include: How is the drive mounted without admin privileges in Windows? How is it mounted in Linux? How does the "Self Destruct" feature work? What is Secure Sessions? How is the Ironkey better than just using Truecrypt? For answers to these questions, take a look. Use the Ironkey High Security Flash Drive.

Hello null byte!! I found a local local privilege escalation exploit on Exploit-db known as CVE-2015-5889: issetugid() + rsh + libmalloc osx local root by rebel. You can visit the link here or find the code on pastebin here.
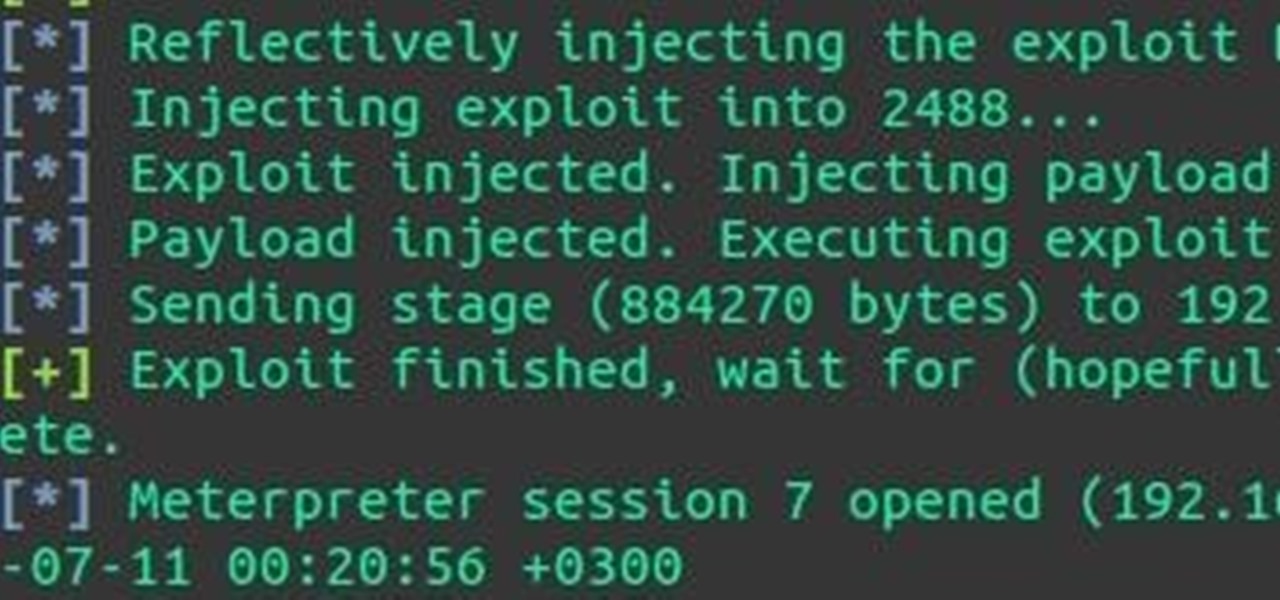
Hey everyone, I've been encountering some problems with privilege escalation when the target has an AV installed, so here's a tutorial for when the almighty "getsystem" doesn't cut it and "bypassuac" gets blocked by the AV. The machine is running Windows 7

In order to prune pine shrubs or trees, you will need the following: pruning sheers. Conifers can be pruned, whenever they aren't growing. Pruning when a plant is actively growing will retard the growth. Therefore, if you need to restrict the height of a tree or shrub, then you would prune it, when it is in active phase. New bud formation will begin at the point where you trim. Future trimming should be done where new bud growth is found.

This tutorial shows how to escalate privilege on XP and get admin or even better SYSTEM privileges. Escalate privileges in Windows XP.
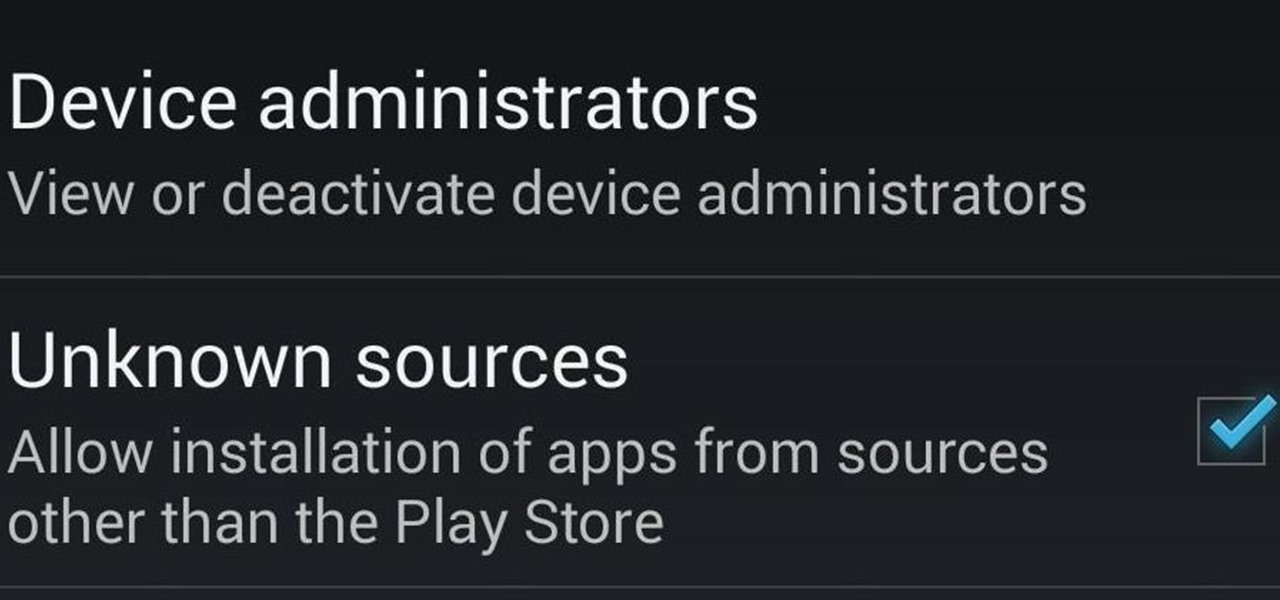
Here's one of those modding must-haves that's basic, yet easy enough to forget about. If you're going to install apps that don't live in the Google Play Store, like the Google Experience Launcher, the OnePlus One lock screen, or something that needs root privileges like the Xposed Framework, you need to turn on this setting.

Week 01 : 9/31 - 09/06 Read Chapters 1-2 of Creating Motion Graphics with After Effects

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

Anti-graffiti councilman Peter Vallone Jr. has previously helped push through laws restricting the sale of spray-paint cans and broad-tipped markers. He now seeks to get fat caps banned.

This four chapter tutorial has proven popular among our staff.

RESPECT - What It Means (in the picture above are my parents, both of whom I respect and cherish dearly)

New to eBay? Don't worry, setting up an account and buying and selling doesn't take that much effort at all. Everyone who has an Internet connection has at one point come across eBay, to find the perfect gift for their loved ones, to find the cheapest deals on plasma televisions and computers, or to get rid of their dusty, old record album collection in their web store.

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

Everyone has deleted a file or folder on accident before. Sometimes people even delete stuff on purpose, only to find out that they needed the files after all. If you're experiencing one of these mishaps, don't worry, file recovery is possible in most cases!

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.
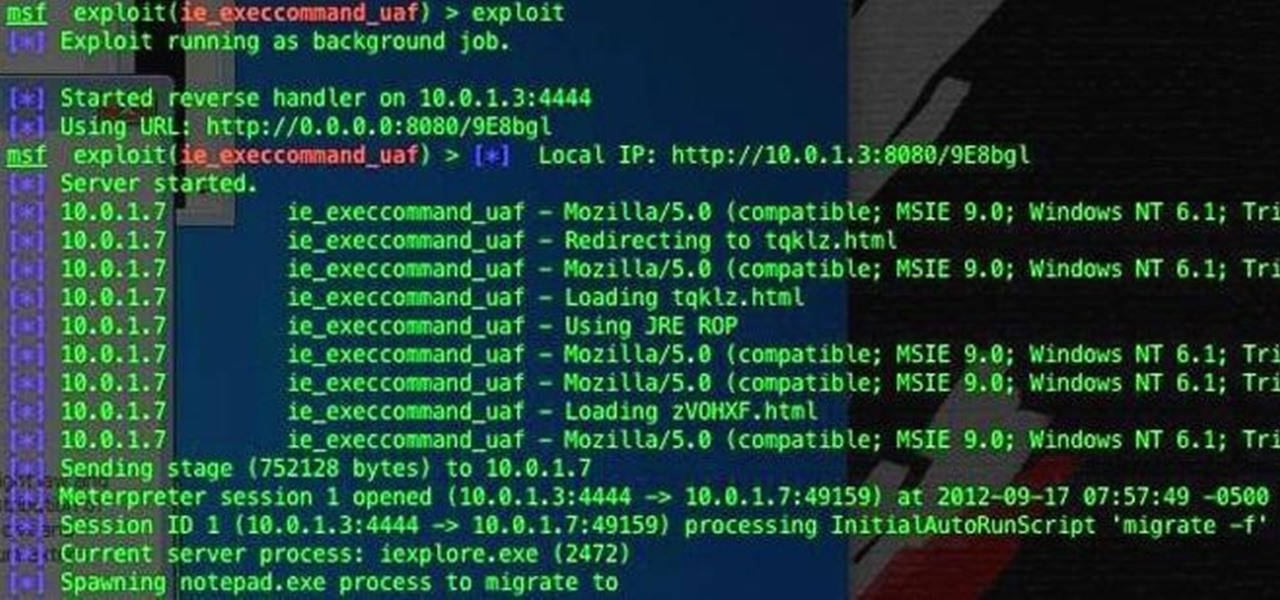
If you're one of the people who make up the nearly 24% of Internet users on Internet Explorer, now is a good time to click on 'Check for updates.' Researchers have found yet another Metasploit Zero-Day exploit that leaves IE 7, 8, and 9 vulnerable for Windows users. Brought to us by the same group as the Java 7 exploit a few weeks ago, this one uses a malicious site to install the Poison Ivy backdoor trojan while unsuspecting users browse. Once installed, it basically gives the attacker the s...
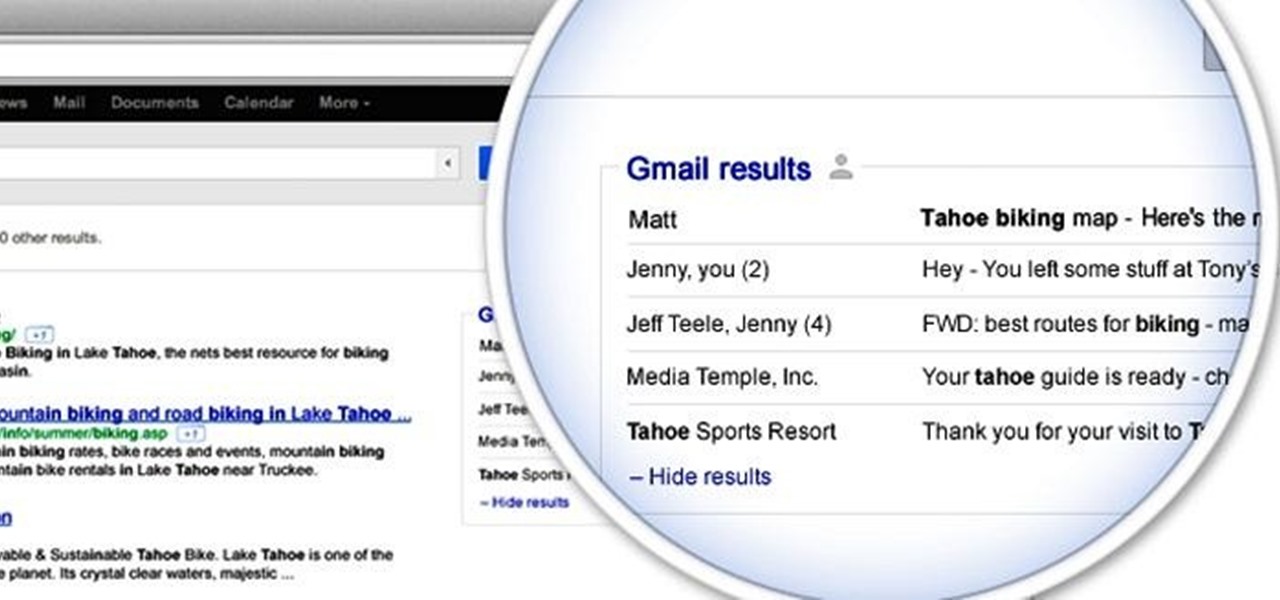
Google is rolling out a new feature that will integrate your Gmail account with Google searches. The feature will add results pulled from your email correspondences to create more "personalized" Google search results. Google is currently doing a test run of the service. To activate it for your account, head on over to this page to sign up. It's currently restricted to the English version of the site, and for those with @gmail.com email addresses (not available on Google Apps accounts). And be...

This morning, I received a message from a friend who was reading a hack log, and she had some questions about the commands used. This got me thinking, as Linux has a ton of commands and some can be archaic, yet useful. We are going to go over everything you need to know to read a hack log and hopefully implant the steps in your head for future use.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

Welcome to the second Goonight Byte! Our second coding session was kindly hosted by th3m, so props to him for letting this happen.

Our first Community Byte went well! We had around 8 people in the room coding collaboratively and watching to learn. LukeStav did the kind task of hosting it on Gobby for all of us, so big thanks to him!
Windows Live SkyDrive which is initially termed as Windows live folders is one of the parts of Microsoft Windows online service. It is a password protected service that allow users to store file and share them with others. Here the windows live id is required to access the users profile. Anyone can make his/her files private or public. Public share file are easy to access without requiring any Windows live id.Initially it was available only few states in United States. But nowadays it expande...

Learn how to train your dog leave treats and toys, and walk on a loose lead. The Head of Training at Battersea Dogs and Cat's Home, Ali Taylor, takes you through the technique. First, learn when and how to reward you dog. Rewarding your dog will encourage them to repeat the action, so make sure to reward them immediately so that they know what they are being rewarded for. Next, teach your dog self control by teaching your dog to hold back from a treat until you say "take it." More importantly...

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

Still reading? Either your kids are not in diapers anymore or you're just curious. Either way, on to the next category of scavenger hunters.

If you would like to restrict what appears on your Facebook page, here's a novel way to retain ultimate control, coined the "super-logoff" method:
From Gaming Age: An Xbox LIVE Gold Family Pack includes:

Fans of Fortnite Battle Royale were understandably ecstatic when the smash hit arrived on mobile. While at first the game was restricted to invite-only, Fornite is now available to all on iOS. If you're just starting out, you're going to want to check out these expert tips to gain an advantage over the other new players.
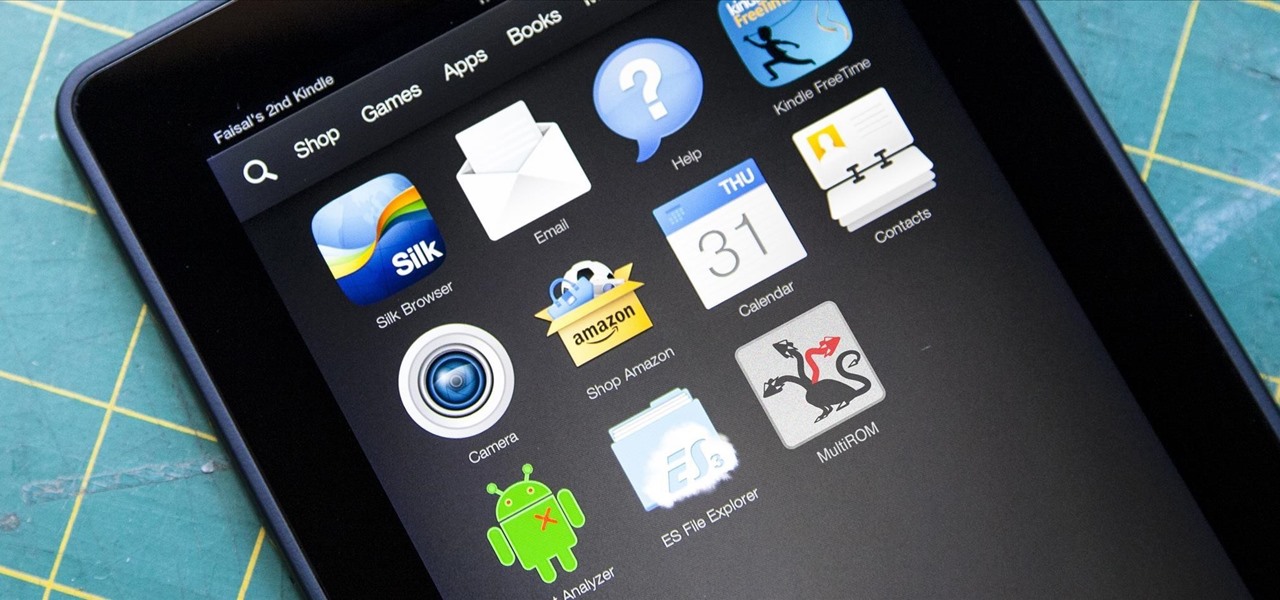
Amazon's Appstore has come a long way since it launched in 2011, with over 250,000 apps to its name. That being said, their app numbers pale in comparison to Google's Play Store, which currently boosts over 1.3 million apps.

Another week has passed on the online battlefield as the CISPA legislation continues to grind away at our freedom. Here at Null Byte, we try to keep our community informed and knowledgeable at the same time—and that means creating content for them to learn from.

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

Having a custom Linux distro can be the coolest thing ever. Most of you will probably be satisfied with any particular Linux distribution, but I know I'm not the only one out there who wants it to have custom configurations and programs preloaded while leaving the bloatware behind.

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

This Null Byte is a doozey.

As Google+ became available to more people, it started running into issues of accounts being suspended due to names that did not sound "real". According to Google+'s community standards, names that users "commonly go by" were encouraged, but not pseudonyms. Those who were using pseudonyms in their Google+ profiles quickly found themselves suspended from using Google+.

This one smells like a fish story. It is not. Tuesday April 13, Dave and I got up to surf westward at 7 in the morning. First rate waves. Headache cold water....sun blocked by the cliffs. Fast, clean, beach break. 3-4 foot sets, mostly lefts. About 15 dolphins swam by. Blase blase. We always see dolphins. But then some bigass whale with barnacles breaches. We are speechless. It is about 20 feet from us. We follow it for about thirty seconds and pinch ourselves. Have-you-ever? No...

Access blocked or restricted websites at your school by using one of the different language versions of Google. Access blocked websites through Spanish Google.