Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...
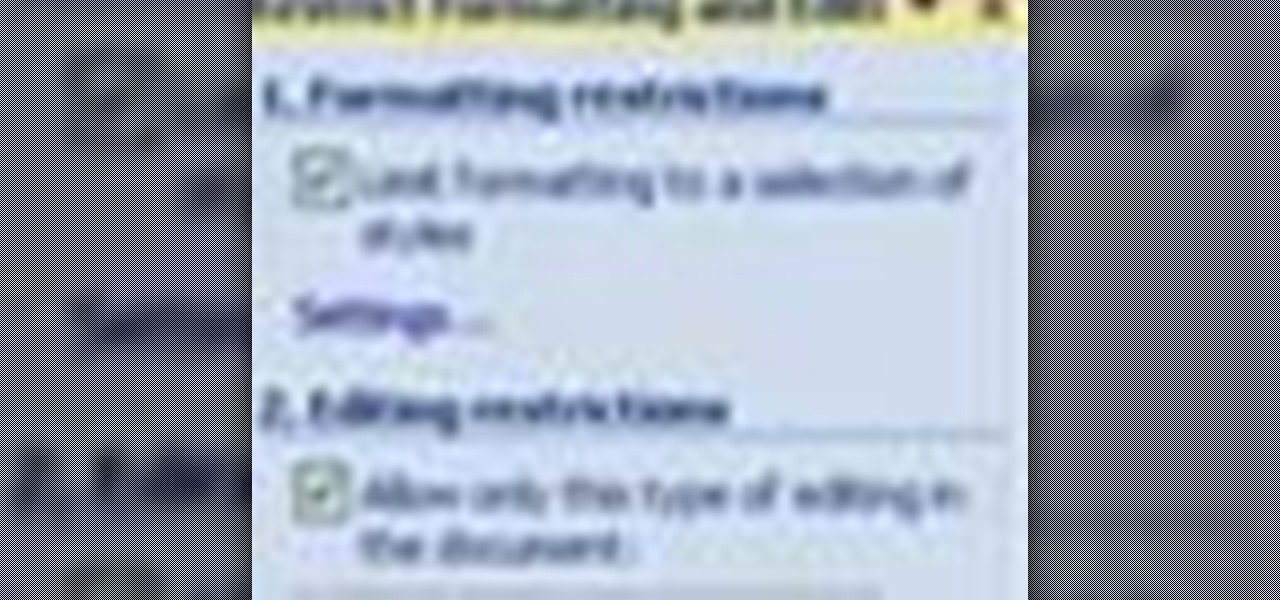
In this tutorial, we learn how to prevent edits or changed in documents in MS Word 2007. Start by going to the review tab, then click on protect documents. Then, click restrict formatting and adjust the different settings. Click on the check marks to choose what types of settings you want to restrict from being changed. This can make it impossible for anyone else to edit the pages except for the original author. You can also make an enforcing protection password so only the document creator c...
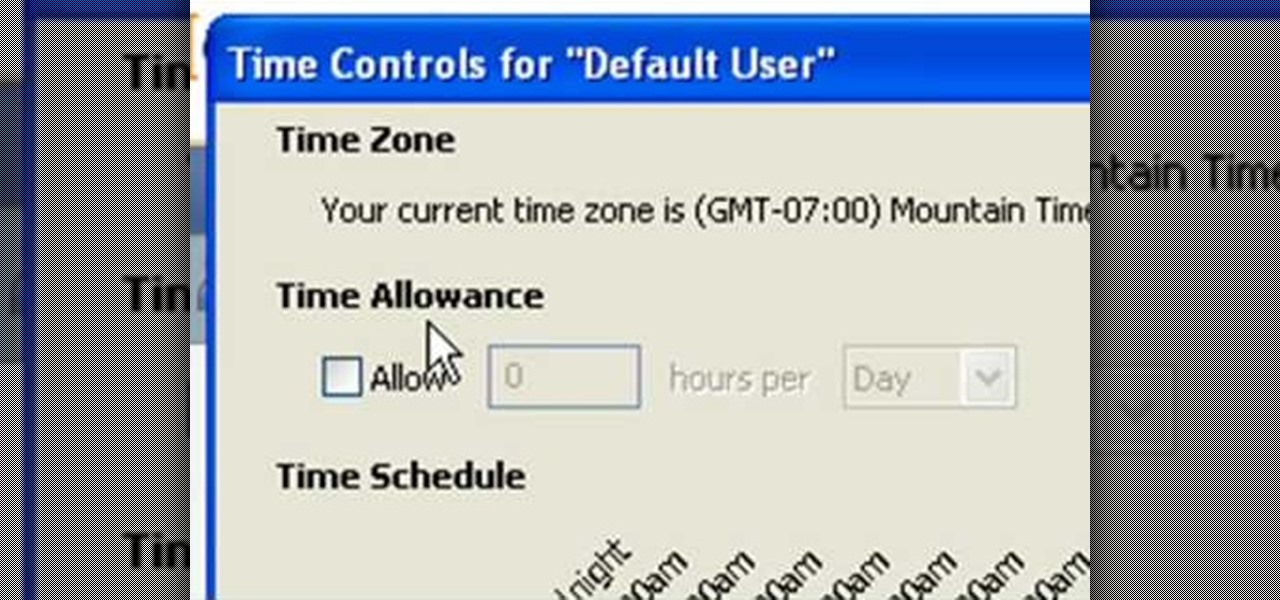
In this tutorial, Andy from TopTenReviews shows us how to restrict internet time usage with Net Nanny. First, open Net Nanny's dashboard and find where it says "time controls". You will see "internet usage", make sure you click on this. Now, a new window will pop up where you can choose time allowance, schedule times and blocks to your specific preferences. Once you pick these, click "ok" and your restrictions will be set and saved! This is a great way to control when your children and others...
If you want to set privacy rules or moderate who has access to the different content that you share on Google+, take a look at this tutorial. It will walk you through the settings and features of Google+ that allow you to restrict who can view and see the information you post to your profile.

FAST is an expedited travel program for commercial truck drivers that travel between the US and Canada. FAST cards are available to citizens or permanent residents of Canada or the US. The FAST program is viewed as a privilege by both Canada and the US. You can be denied for the FAST program if you do not have a clean driving record and a clean record with the Canadian Border Services and The US Customs and Border Protection. Things such as being caught with undeclared items and having a crim...

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

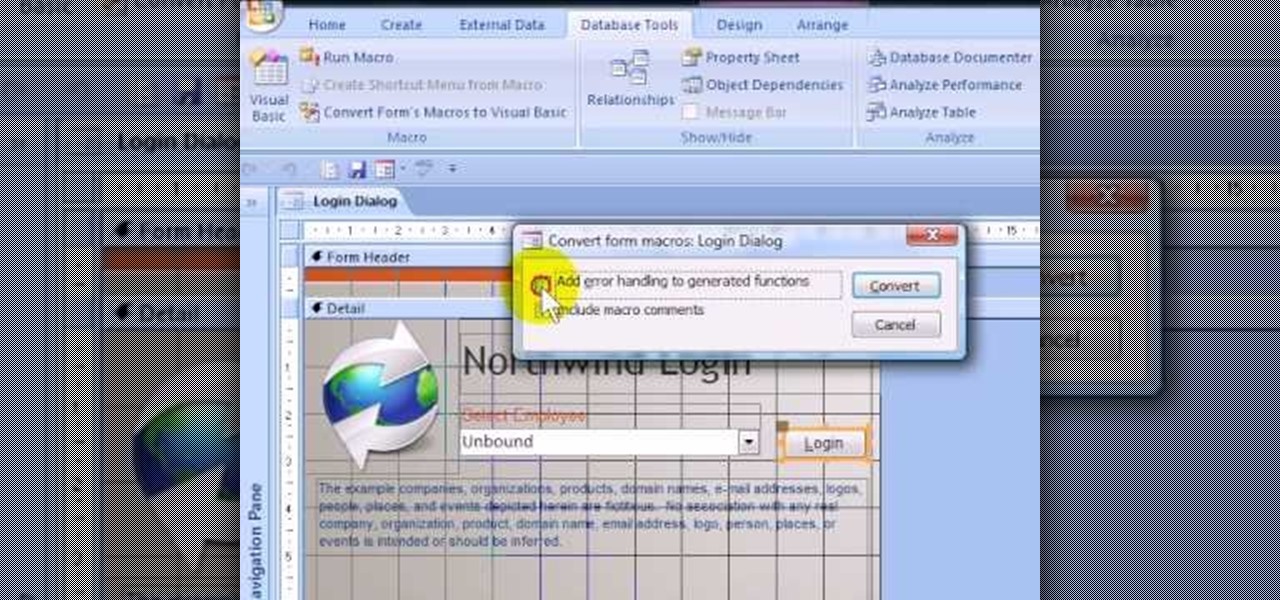
If you want to password restrict some of your data, or just want to know who is doing what in Microsoft Access 2007, you will want to set up a login form for MS Access 2007. This is an easy procedure, and you can create one yourself with just a basic understanding of the structure for MS Access. Watch this video, and Uncle Gizmo will show you how to do a login form and several other forms for MS Access.

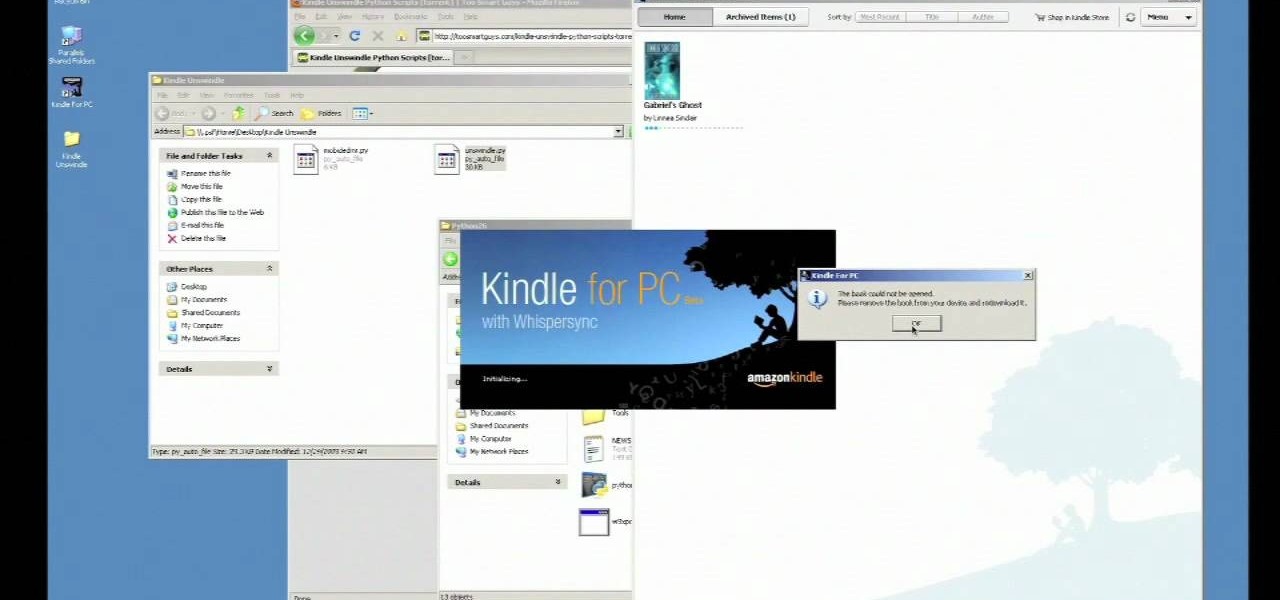
You've got a Kindle, and you've bought your first ebooks! Did you know that you don't have complete control over those books you bought? Amazon restricts your use of ebooks with DRM, or Digital Rights Management, that prevents you from transferring your purchases to other devices, or copying them. Watch this video to learn how to strip your Kindle ebooks of the DRM, and really own your content!

Kids can have fun using the iTunes music store while parents still control the credit card and content their children can access. Parents can restrict access to certain content, set up a shopping cart to review music choices before they're purchased, and give kids a monthly allowance.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

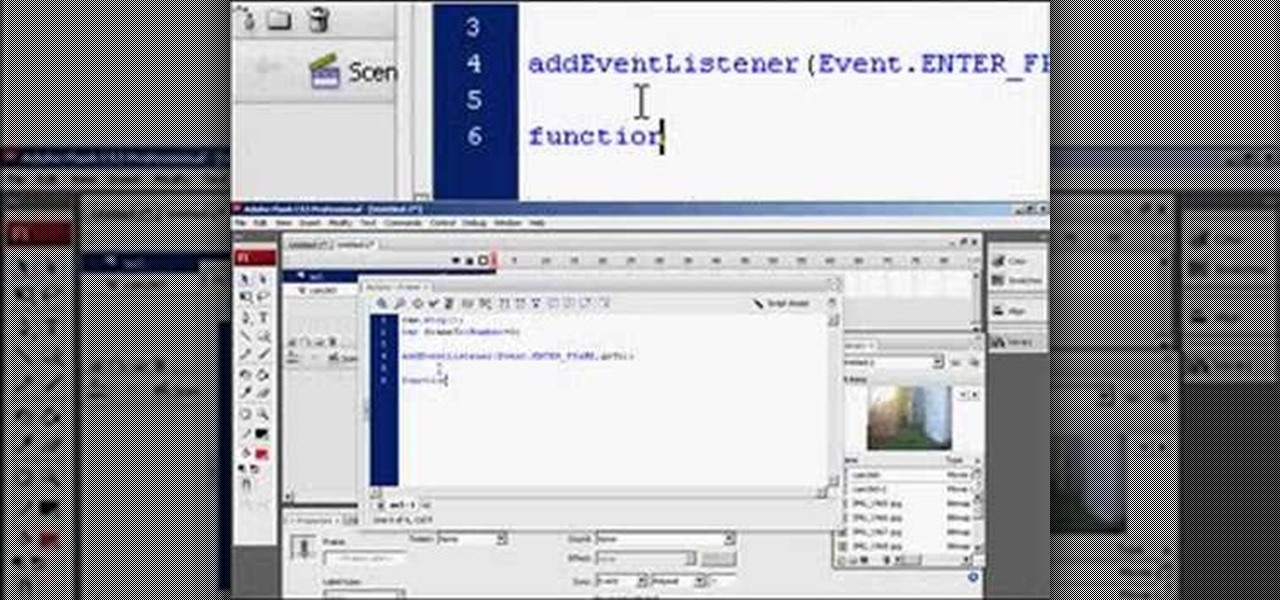
360 degree panoramic viewers are a staple of all kinds of websites from real estate to auto sales. This video will teach you how to create a a 360 degree view that will display on your website using Flash CS3 and Actionscript 3. Don't restrict your users to just one photo, let them see all of whatever you're showing them with the tools your learn in this video.

One of the great things about Myspace, is the ability to customize the layout on your homepage. It gives you the ability to be as creative as you want and show as much personality without being restricted. So in this tutorial, you'll learn how to make a custom Myspace 2.0 layout using easy to use computer programs. Good luck and enjoy!

When will the drama end? The lawsuit between Waymo and Uber is back in the news with no signs of stopping. Today the court denied yet another request from Uber to shield itself with the fifth amendemnent, securing a small victory for Waymo.

Another series I am now starting, might have to slow down on all of these series, but why tf not. What Is CMD?

Now that all variants of the Galaxy S5 have finally been rooted, we can start exploring all of the tweaks and hacks that Superuser privileges open up to us.

While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

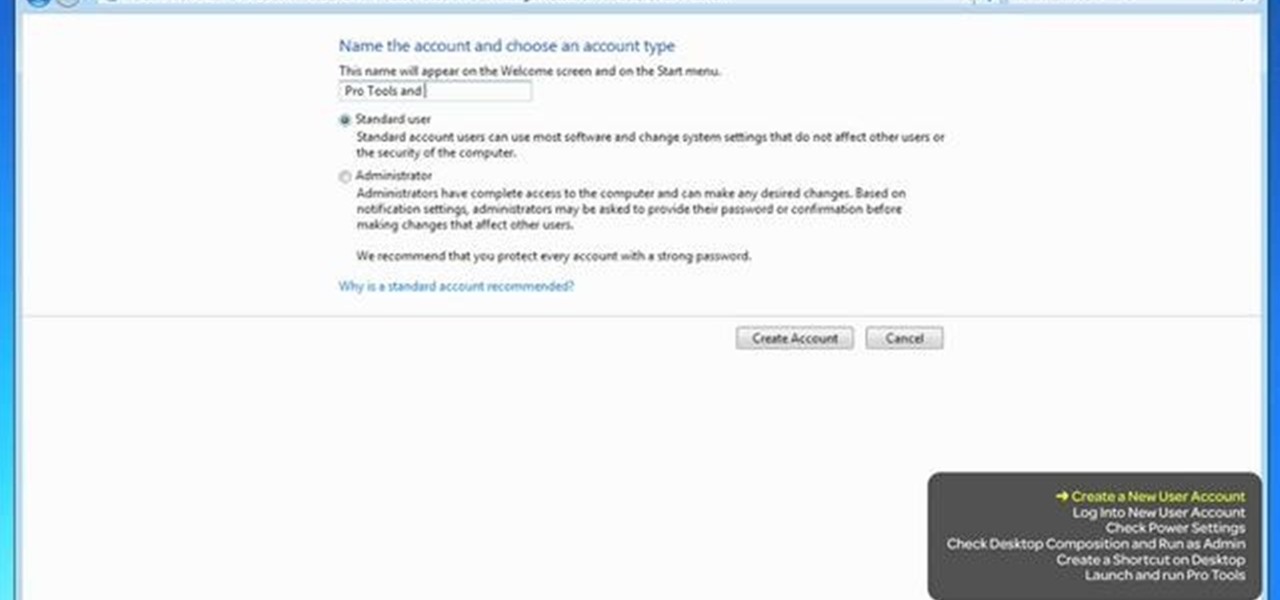
If you're trying to troubleshoot Pro Tools, one way to help is to set up a new Admin account on your computer. This will help you determine if the problem you're experiencing is global, or is just restricted to your own account.

You'll of course want to set up an admin account when you create your own website, so you can restrict access for everyone else but the admins. This tutorial shows you how to set up an admin account on your website using Dreamweaver.

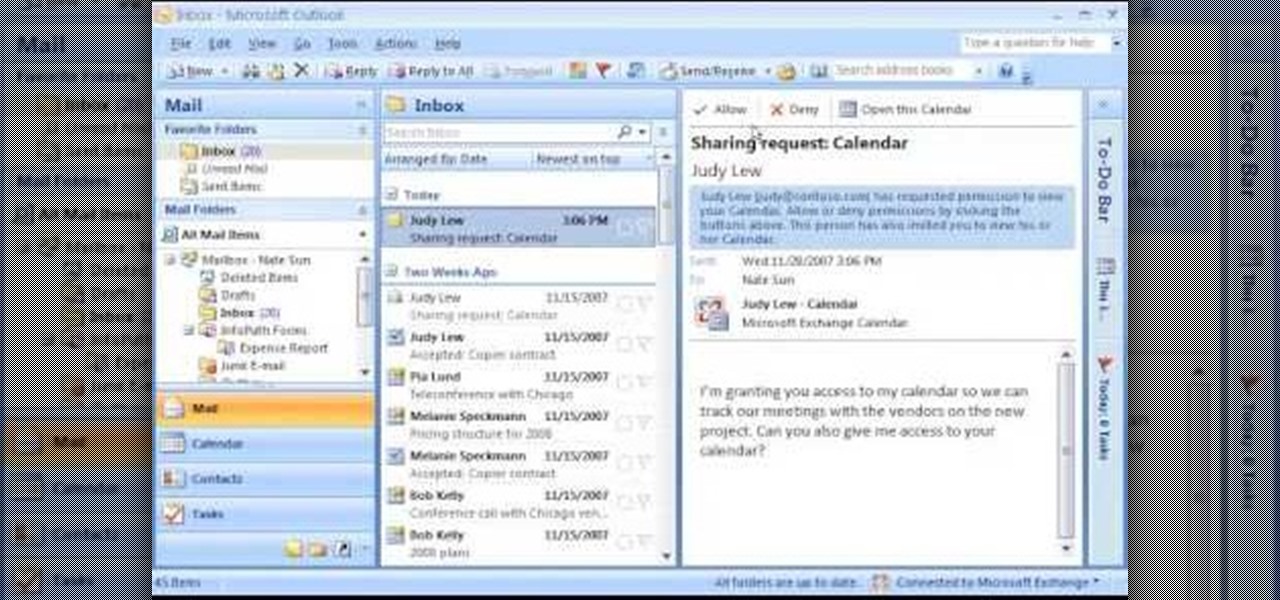
This tutorial shows you how to share your calendar three ways in Microsoft Office Outlook 2007. If your company uses Microsoft Exchange Server, you can share your calendar within the organization by using that feature. You can also send a snapshot of your calendar in e-mail to people outside your company. And you can publish your calendar on the Microsoft Office Online Web site and restrict how much detail is shown and who can access it.

Learn how to secure a web site using the new Membership and Roles features of ASP.NET 2.0. In this ASP.Net video tutorial, the topics include user registration, password recovery, and restricting access to content with roles.

How to get around your school or home's computer security to view restricted webpages.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

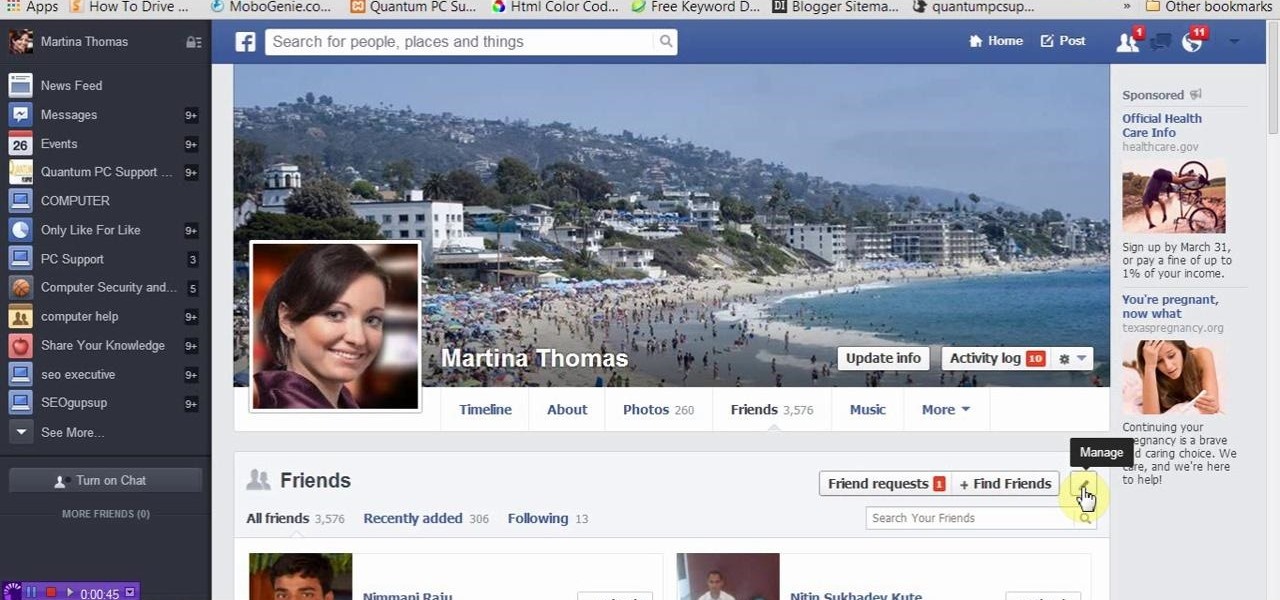
This tutorial video will show you how to hide Facebook friends list from public. With the help of this video you should restrict others from watching your Facebook friends list. Watch the video and employ the technique in your Facebook account.

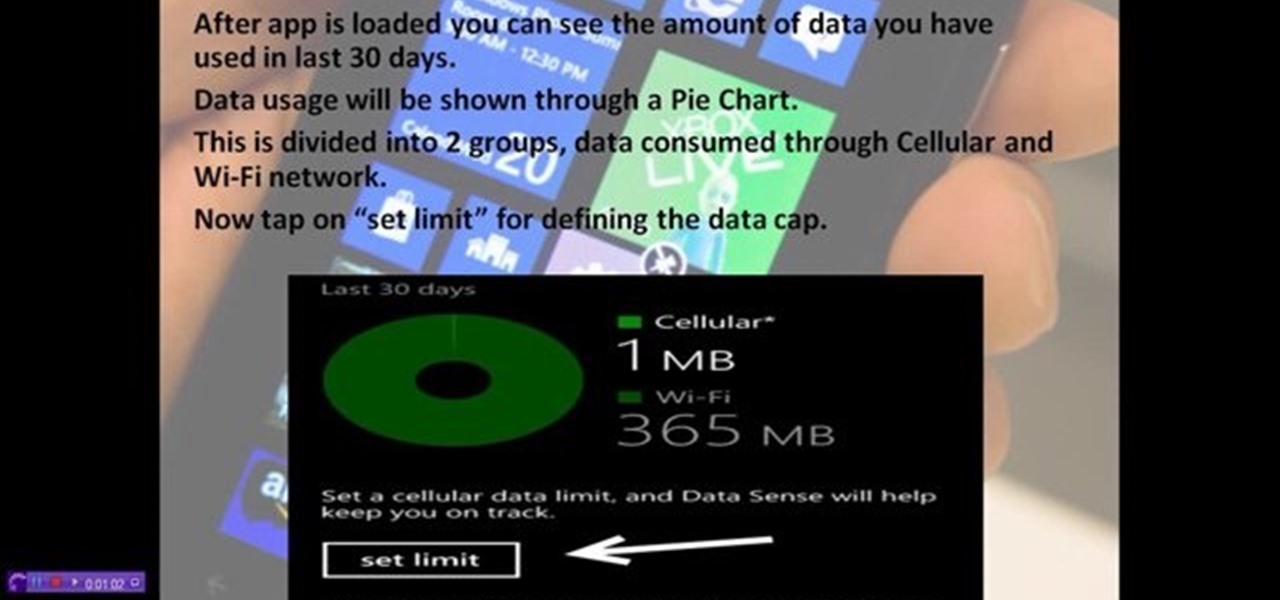
This video will show you how to control and limit data usage in your windows 8 phone. You may want to restrict your data usage and want to set limits for apps also. If you set your usage limit internet will stop automatically after reaching the limit.

Just a little tutorial I put together for those that love to text at work or school or any other place really that you spend a lot of time in. I hope you enjoy.

This video will provide an idea how to disable or enable the USB port on your PC. By disabling USB port will restrict people from copying your files into USB devices. This is a very effective trick to save your data. Watch the video and follow all the steps.

How to control and limit your internet usage in your windows 8 phone? You may want to restrict your internet usage and want to set limit for apps also. If you set your usage limit internet will stop automatically after reaching the limit. Follow the video to employ in your own phone.

Is the proper term nudists or naturalists? Doesn't seem to be too much of a difference, because when it all boils down, they're both still butt-naked on the beach. Nude beaches are fascinating places for the adventurous spirit, but unless you’re an old-time nudist, you probably have questions about the proper way to behave on a nude beach. Well, we’ve got the answers.

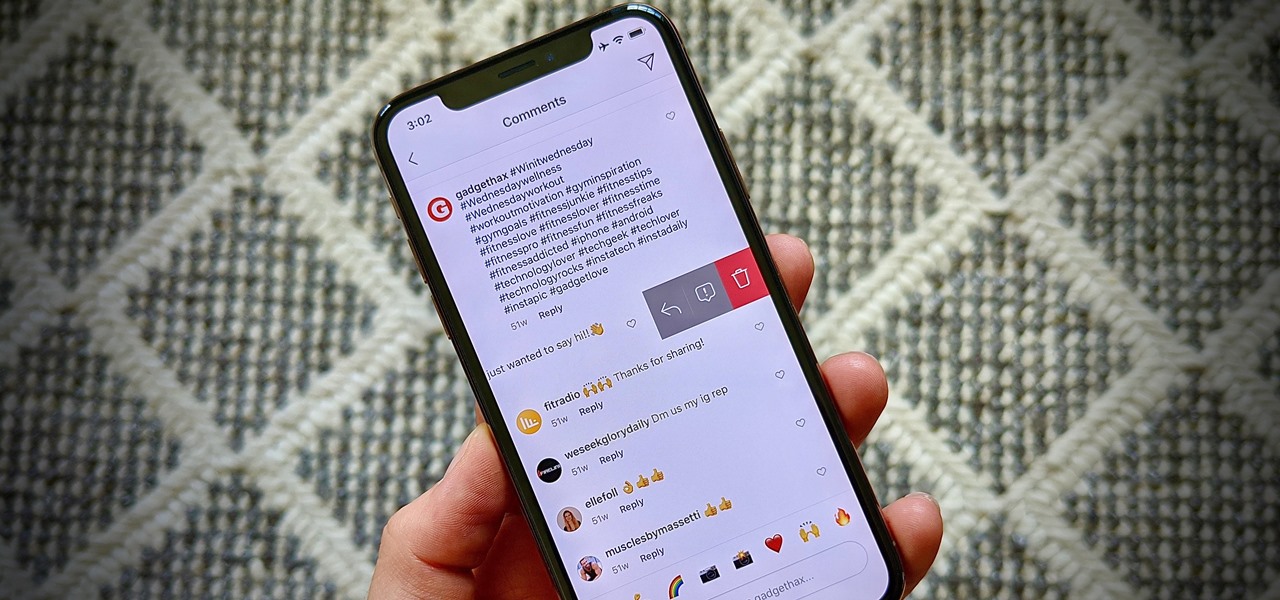
When you post a photo or video on Instagram, it's always nice to see positive comments from friends, family, and even fans. On the other hand, it's never fun to see spam or hate messages underneath your posts. Before, you'd have to delete these comments one by one, but now you can delete comments in bulk.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.