
How To: Bypass UAC Using DLL Hijacking
This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.


This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Welcome back, my neophyte hackers! Metasploit is such a powerful tool that I can only scratch the surface of its capabilities here. As it has developed over the years, it is now possible to use Metasploit for nearly everything from recon to post exploitation to covering your tracks. Given its versatility, every aspiring hacker should have at least a tentative grasp of Metasploit.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

Welcome back, my rookie hackers! A short while back, I began a new series on database hacking, and now it's time to continue and extend your education in that field. As you know, the database contains all of the most valuable info for the hacker, including personally identifiable information, credit card numbers, intellectual property, etc. So, it's the ultimate goal of cybercrime and the APT hacker.
Keeping your Samsung Galaxy Note 2 clean and neat can become a hassle, especially if you're an app whore. As the amount of applications on your device goes up, so do your notifications, which will clog up your Status bar with icons alerting of recent news and tasks.

Posture plays a huge role in your entire respiratory system. Enabling your body to have good psture can increase breathing and really help expand your lungs. This video will demonstrate exactly how to improve lung capacity with a posture breath excersise.

Nexus is a pre-approved trusted traveler program that allows approved people expedited travel between Canada and the US. The card is available to US and Canadian citizens or permanent residents who travel by air or land between the two countries. Anyone traveling between the two countries must have their own Nexus card including babies. The Nexus card is considered a privilege by both the US and Canadian governments. You must have a clean record with both the Canadian Border Services and The ...

Need to leave town earlier or later than planned? Flying stand-by is not as simple as it used to be. Learn how to fly stand by - you never know when it may be necessary.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.
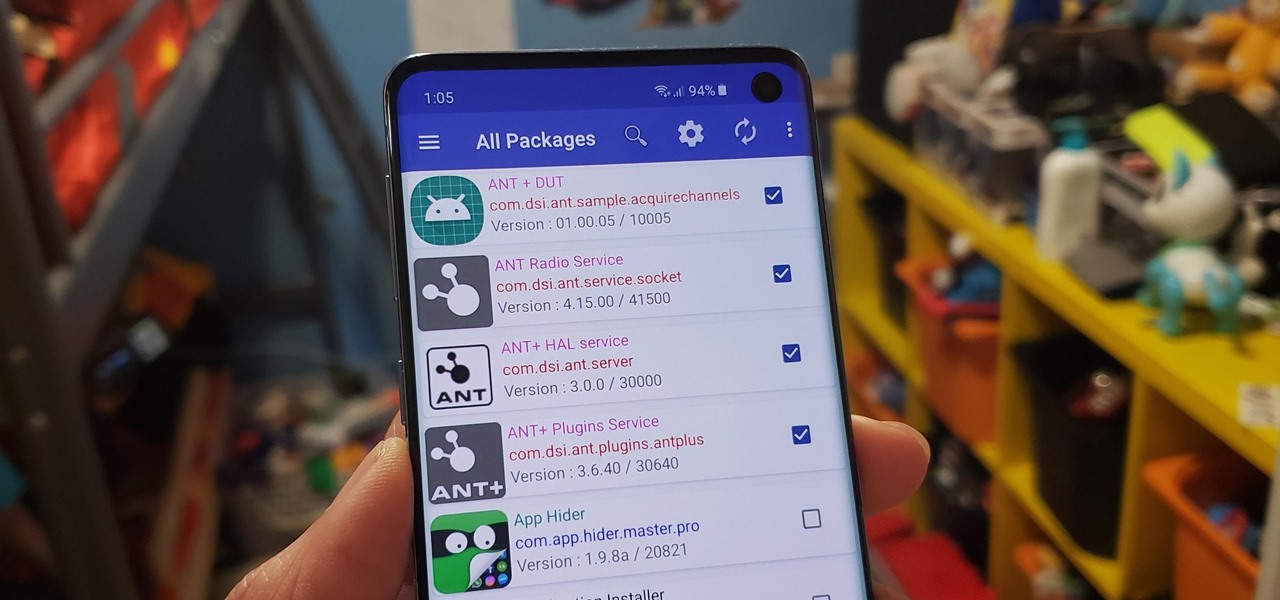
Bloatware remains one of the biggest problems with Android, especially when tied to a carrier. Removing bloatware usually requires you to take extreme measures like rooting. Unfortunately, the Galaxy S10 falls under this annoying umbrella, but there's an easy workaround.
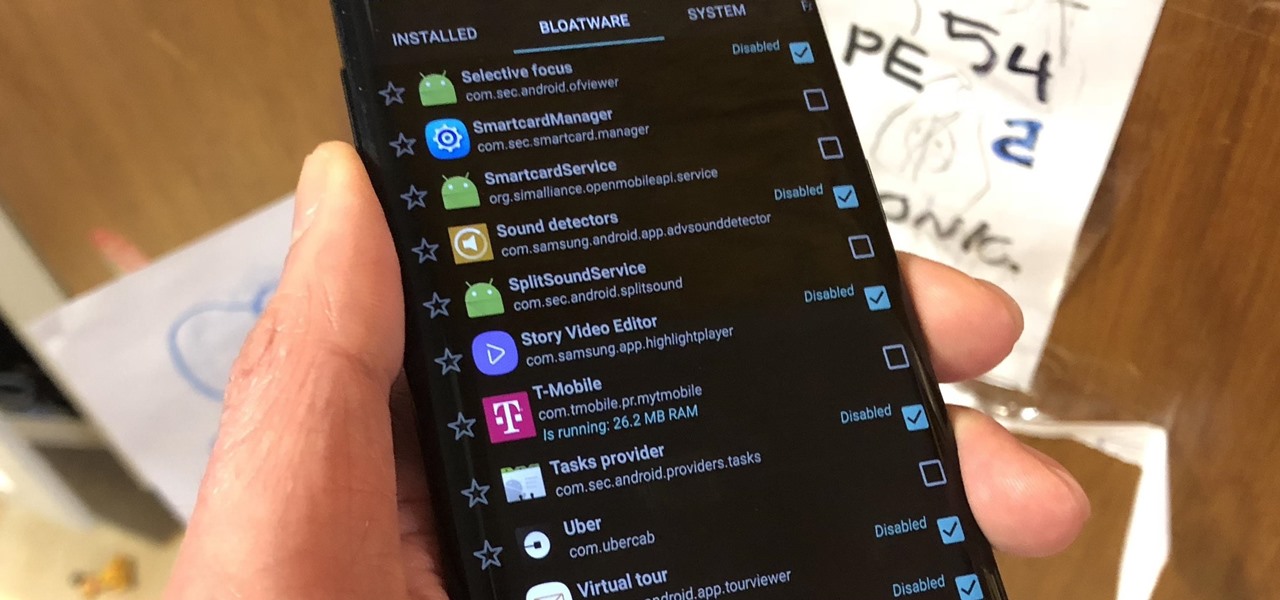
Carrier-branded Galaxy S9 models come with a ton of bloatware that you usually can't get rid of without rooting. With a little digital elbow grease, however, there is a way to disable bloatware on your S9 or S9+, and it's a lot safer that attempting to root and modify you precious device.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.

One of the main reasons for installing a custom ROM on an Android device is all of the added features. For instance, OmniROM offers a souped-up multitasking mod called OmniSwitch, so instead of the regular app switcher, you get an interface that lets you pin your favorite apps, access settings, view memory usage, and more.

It's really amazing how much you can do with root access on an Android device. From various themes to porting exclusive funtionality from other devices, the power of Superuser privileges is truly awesome.

Your new HTC One M8 has a ton of really cool features, some of which relate to waking the device up. A swipe up to unlock to your last active screen, a swipe down to access the voice dialer, and a double-tap (or knock) to wake the device and bypass the lock screen.
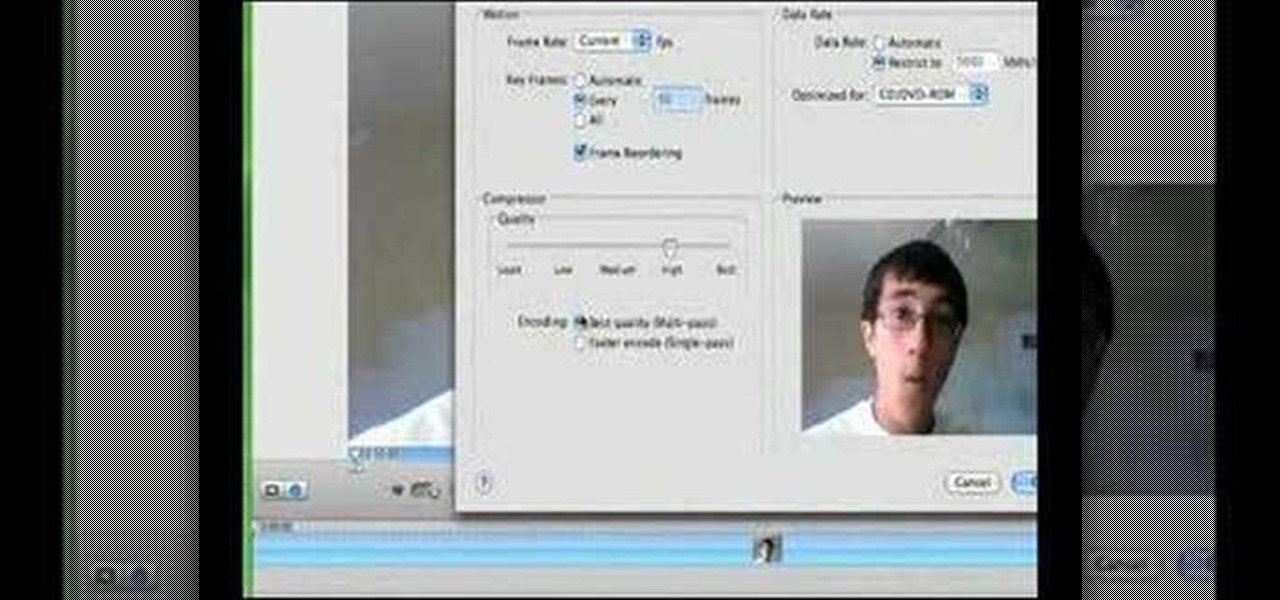
In this how-to video, you will learn how to compress iMovie files into QuickTime files to make them look really good on YouTube. First, open iMovie. Click Share and click Share again. Go to Expert Settings and click on Share. Click on Options and go to Settings. Change it to h264, current frames per second, and every. Restrict should be set at 5000. Optimize it for DVD and change encoding to best quality. Change the size to NTSC 720X486. Check de-interlace video and hit okay. Change the sound...
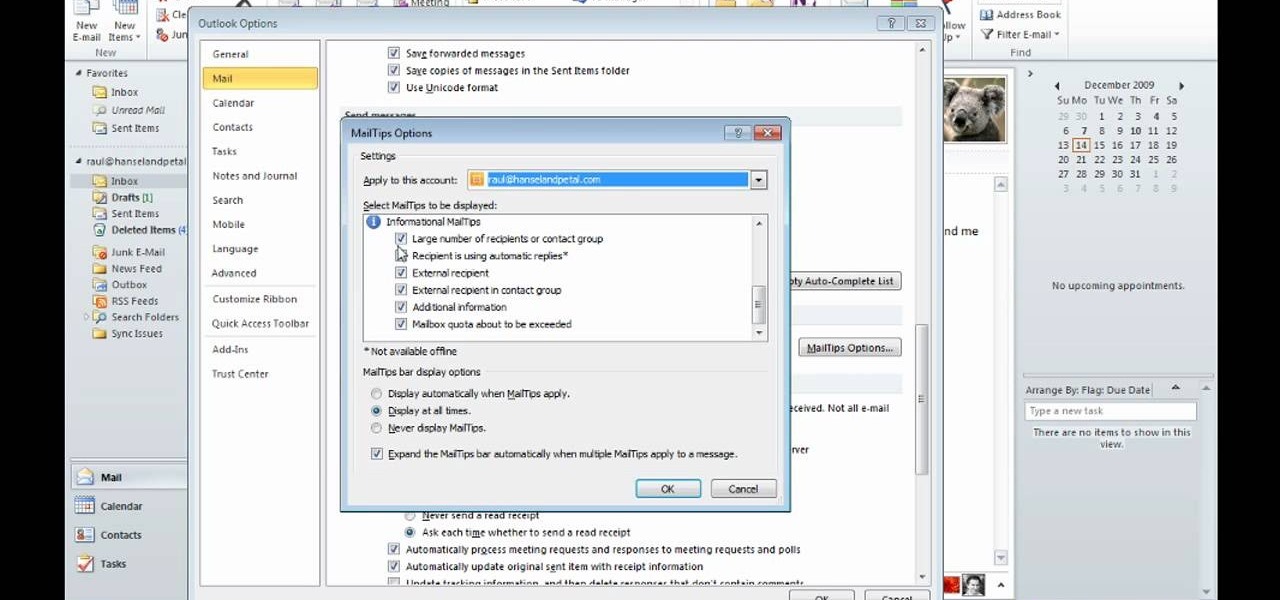
David Rivers is back to give us some more tricks on using MS Outlook 2010. In this video he tells us how you can avoid sending email to the wrong person by setting up some email preferences in MailTips. MailTips actually has the ability to alert you when you are about to send an email under certain conditions. Don't worry about sending an email to your boss that was meant for your co-worker. Your MailTips folder contains many options that you can use to restrict some of your outgoing mail and...
In this video tutorial, viewers learn how to turn off the system firewall without admin privileges. Begin by clicking on the Start menu and open he Run program. Type in "system.msc" and click OK. Scroll down the Services list and look for Windows Firewall. Double-click on it and under the General tab, click on Stop. Then click Apply and OK. This video will benefit those viewers who use a Windows computer and would like to turn off the firewall, even if they are not running the administrator a...

In this video, we learn how to tune an RC nitro engine. First, you will need to adjust your needles. Make sure you know which way to go as you are adjusting them. After this, you need to find your high speed needle and find where you will hook up your fuel line. Lean the motor by turning a screwdriver into the barrel. This will screw your needle in and make the engine restricted to fuel flow. Now you will want to test out your engine to see how much lean you are getting. Make sure it's oiled ...
In this video, learn how to convert iTunes m4a files into mp3's so that you can share and listen to them anywhere. This tutorial will also show you how to bypass the restrictions on the program and convert as many files as you like for absolutely free.
Using ASP.NET Secure Services and Applications Services

It is a demonstration of a cream blush with a # 130. We will be using a steela convertible collar and a color called camellia which is #1 and is used mostly as a blush which nice and bronzy. You firstly stamp the brush onto the blush and then lightly tap the brush onto your hand first so as to ensure you won't have too much of blush on your face.

Compression pants, or compression shorts, are good for managing hamstring injuries without restricting motion. There are many styles of compression pants, which are also known as compression pants. Learn how to use compression pants and stay fit in this sports medicine how-to video.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.
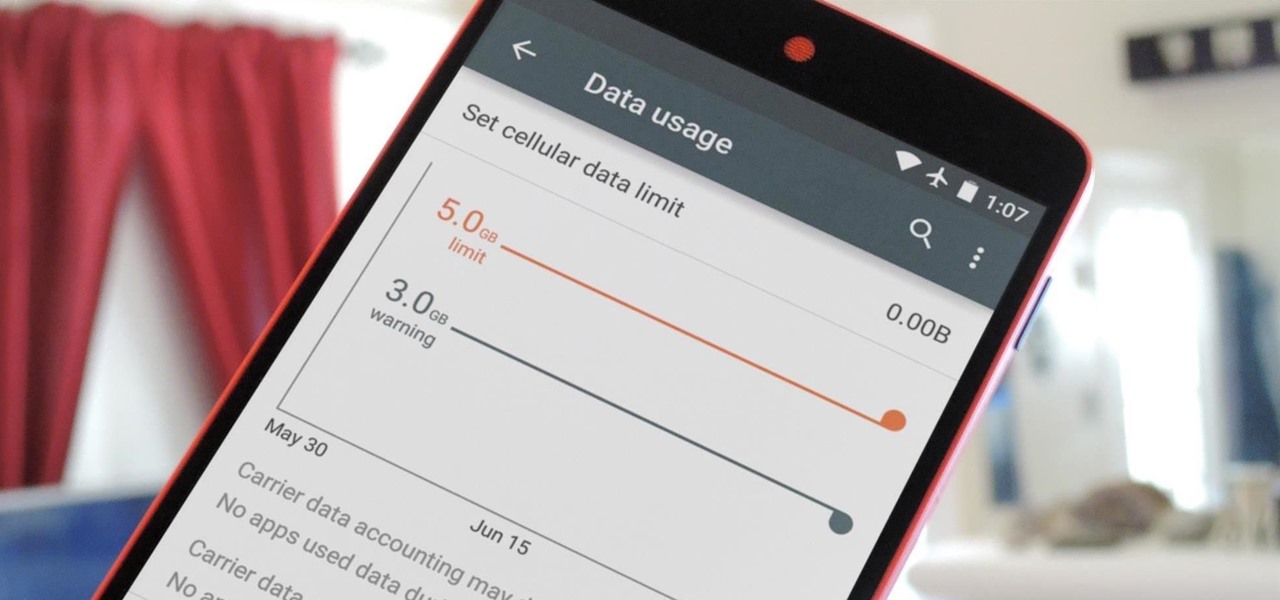
Ever watched Netflix on your phone only to realize an hour later that you forgot to turn Wi-Fi on? That's a whole lot of data used.
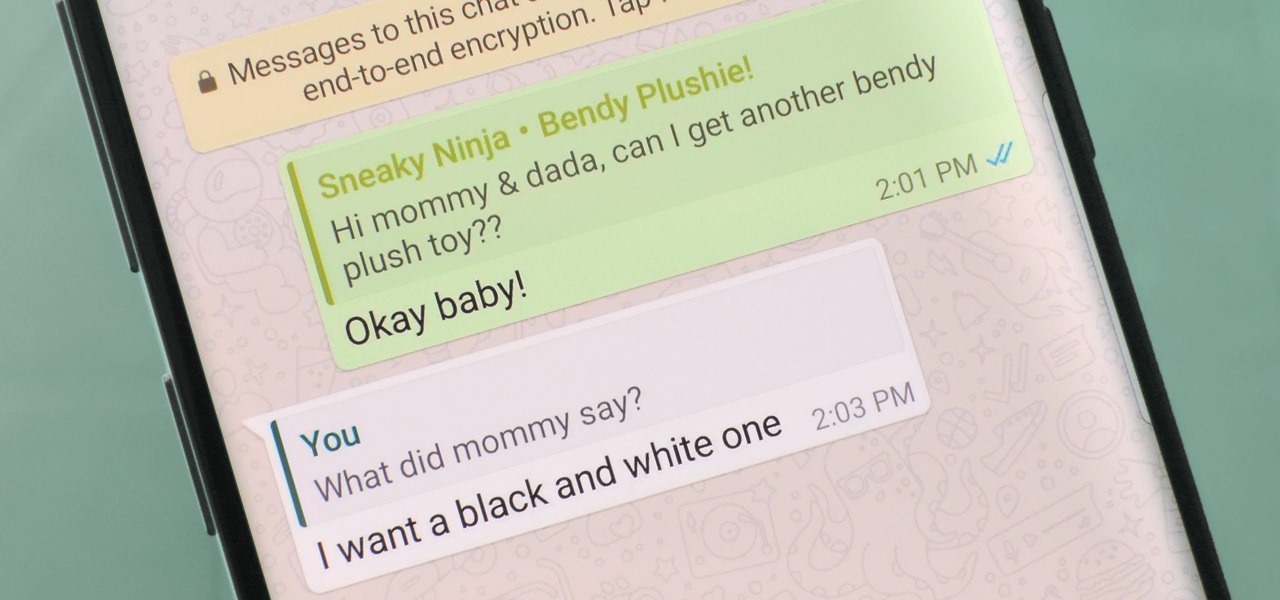
Group chats in WhatsApp are great for communicating with multiple people at once, but that can be a blessing and a curse — any message you send will be seen by everyone, and that's not always ideal. Thankfully, there's a new feature that lets you respond to group messages privately.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

Welcome hackers. Hackacademic.RTB1 is vulnerable machine for training our skills.This machine can be download from free from here. There is many tutorial how to hack these machine but i did always be my self.
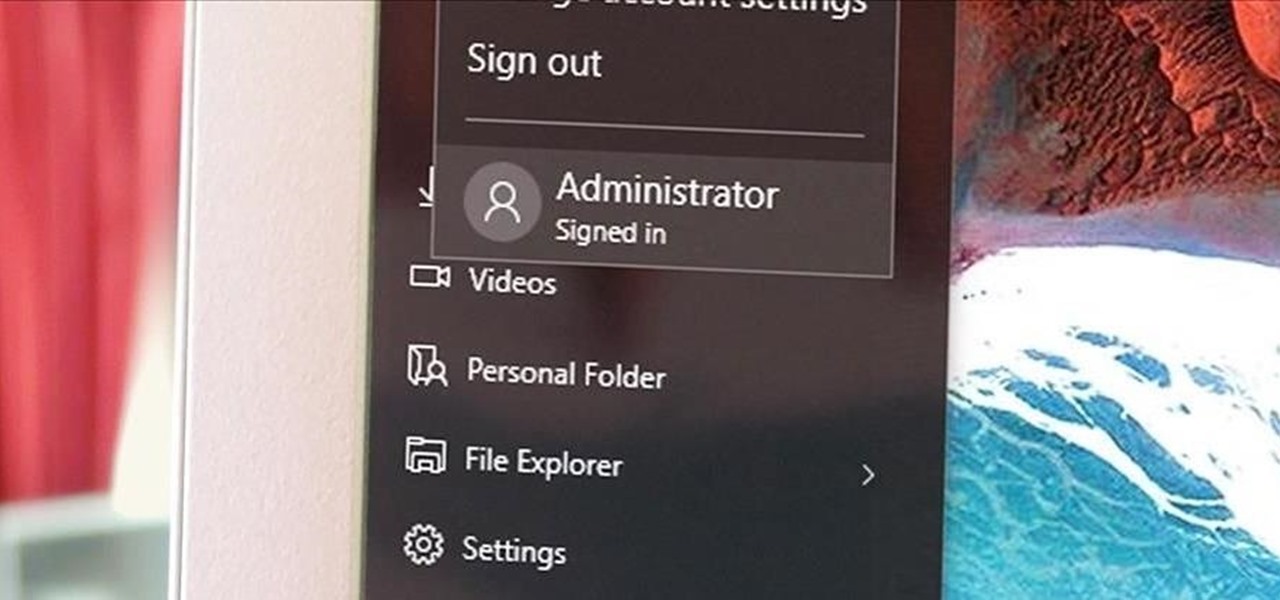
Windows has always had an "Administrator" account that allowed you to install programs and manage system files with elevated privileges. The difference between this account and a regular user account with administrator access was that you never got bothered by annoying User Account Control popups when you were logged in as Administrator.
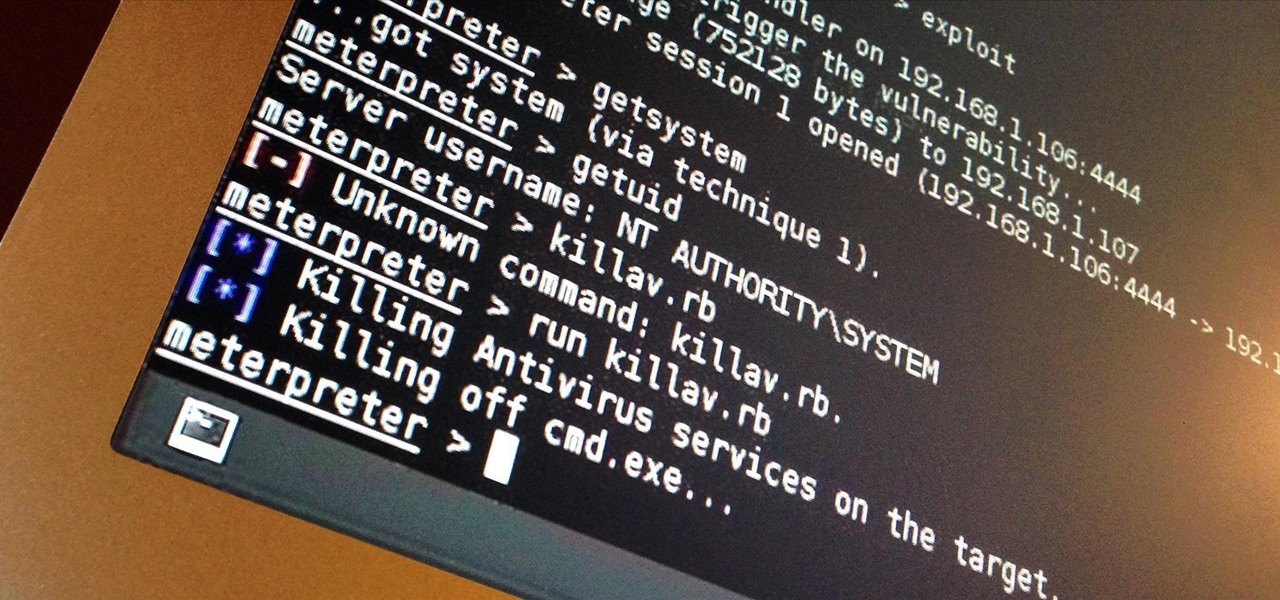
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

'Tis the season... for cheap (and free!) video games. THQ's Humble Bundle lets you get 7 games for any price you want, and now they're making it even better by offering fans a free Steam copy of Metro 2033 just for liking Metro on Facebook, which is gearing up for the latest Metro: Last Night release.

This video shows how to make a "Dreadhawk," which is a mohawk made of dreadlocks. This is a unique hairstyle that provides a very different look. The instructor begins by separating his front section of hair from the rest, and making a ponytail with it using a rubber band. He continues in this manner, making five more ponytails with sections of hair. You can then tie ponytails together, restricting their movement and keeping the Dreadhawk more intact. This hairstyle can also be done with regu...

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

Among iOS 11's many criticisms, one of the more surprising complaints came from parents worried that Apple wasn't doing enough to monitor and control their children's iPhone usage. Apple seems to have taken these issues to heart, as iOS 12 introduces new and improved parental controls to help encourage healthier mobile habits for kids.
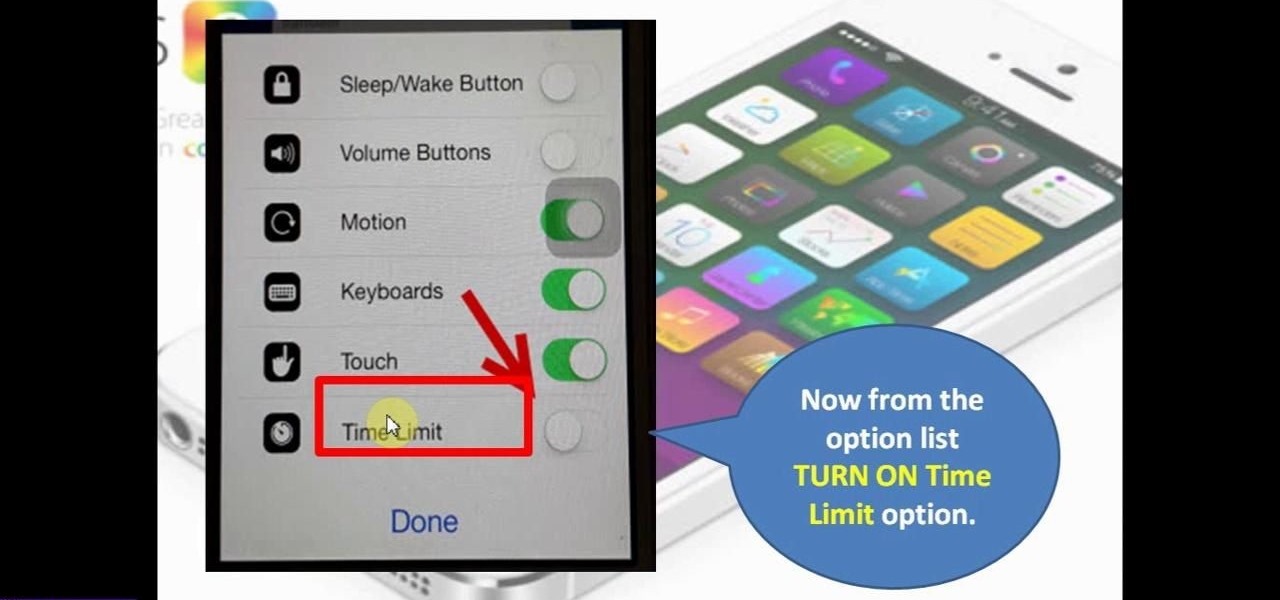
This video will show you how to set time limit for your children games in your iPhone or iPad. This will restrict children from excessive use of your iPhone or iPad. When this time limit is over, the game your child is playing will be stopped automatically. They will not be able to continue playing games until you start a new session for them. So please watch the video and employ it in your phone.

The moment arrives when you finally pop a shell on the web server you've been working on, only you find yourself in a strange environment with limited functionality. Restricted shells are often used as an additional line of defense and can be frustrating for an attacker to stumble upon. But with enough patience and persistence, it is possible to escape these restricted environments.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.