Buried deep in the code of many Google apps is a set of debugging options. These options, which are designed for developers to help test the way their apps interact with Google's own, are normally hidden from view.

One of the coolest features of the Galaxy S5 is its IP67 certification. This means that the S5 is internally impenetrable to dust and can be submerged in water for thirty minutes at a depth of one meter. It's definitely a handy feature for folks who've lost a phone to a toilet in the past.
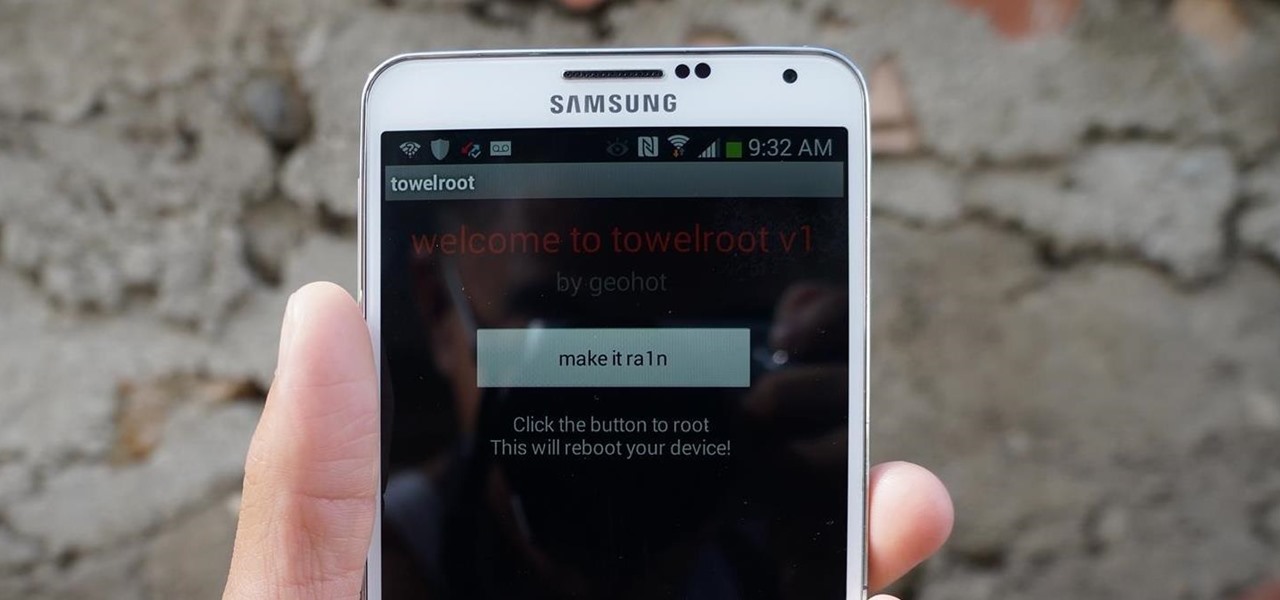
AT&T and Verizon customers, it's finally happened. After many long months of waiting, and a fairly significant bounty up for grabs, your Galaxy Note 3s can finally be rooted! Best of all, it may be the simplest method for achieving root we've ever encountered.
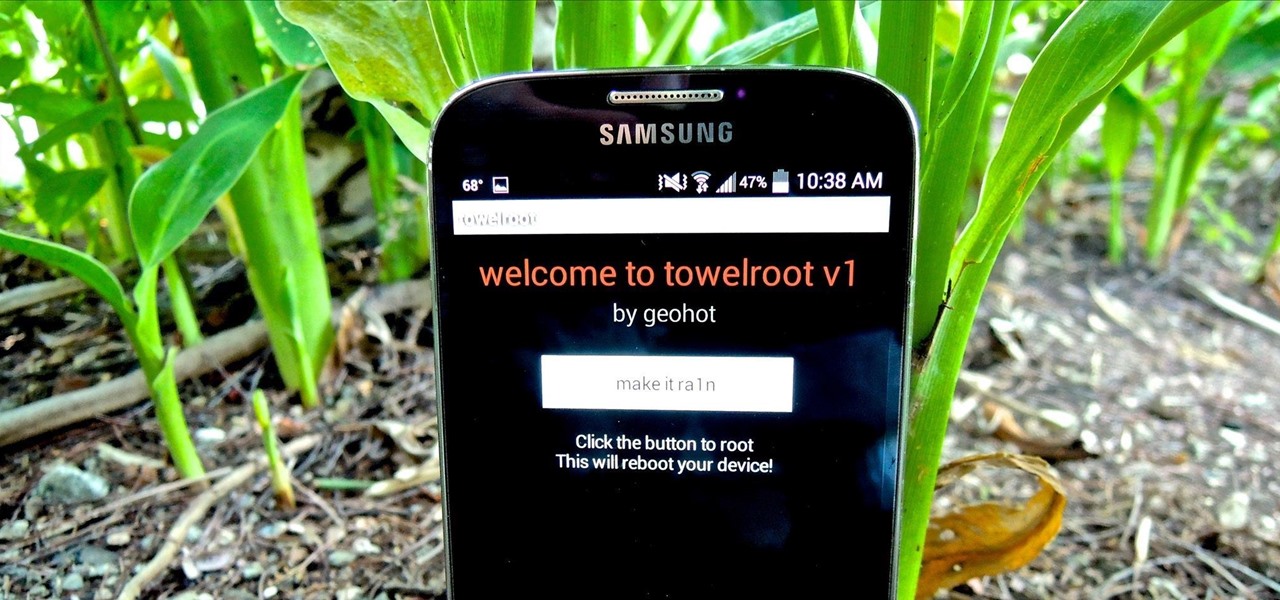
Something pretty awesome happened over the last couple of days. George Hotz, better known as Geohot, the infamous hacker known for jailbreaking iOS and exploiting the Sony Playstation 3, has brought joy to owners of just about all Android smartphones and tablets, especially those on AT&T and Verizon.

One draw that Samsung's Galaxy S line has had over the Google Nexus 4 and 5 and the HTC One (though the M8 appears to be following suit) is expandable storage. Pop a microSD card into the slot and you have extra storage for music, photos, and even apps themselves in some cases.
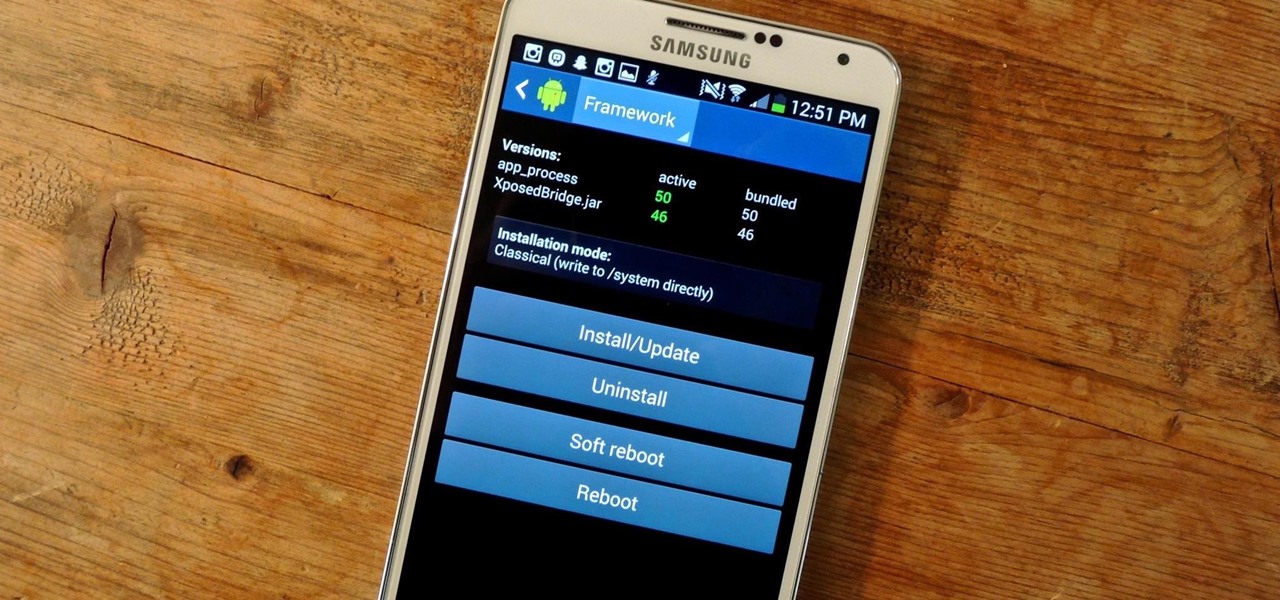
Allowing us to easily get features that would otherwise be available only through flashing mods and custom ROMs, Xposed Installer has been a godsend since its development, simplifying the sometimes tasking and potentially harmful process of changing the core components of Android's operating system.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

While the Samsung Galaxy Note 2 has an integrated LED for notifications, it only works for a few things, like charging and low battery, and it only flashes two main colors (red and blue) when the screen's off. As someone that usually has their phone on silent or vibrate, it's hard to tell when I receive important messages or notifications. Sure, I could set a specific vibration or ringtone for individual apps, but that can quickly get annoying and distracting, especially at work or school.

I rarely ever turn my desktop off. For starters, it takes a few minutes to boot up, which I hate, and secondly, putting the computer to sleep is perfectly adequate. You really only need to completely shut down your computer every once in a while.

UPDATE: A patch to fix the exploit has been released. Download it here.

These days, news papers, online editorials and magazines are filled with news on Iran and Syria. Of course, that is expected, as such sources need to stay current to stay in the game. My concern is that most of these articles talk about what to do about these situations.

Antibiotics used to prevent diseases in livestock are creating a world of hurt for humans and the soil we depend on for food. Bacterial resistance to antibiotics is a global health issue. The overuse, underuse, and poor use of these life-saving drugs is rapidly removing them as a treatment option for serious infections in humans—plus bacteria are naturally adaptive.

As researchers learn more and more about our intestinal bacteria—also called the gut microbiome—we're finding out that these microbes aren't just influencing our health and wellness, they're a useful tool for improving it, too.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

Childhood obesity is becoming a national epidemic. If we don't improve what our kids eat soon, the next generation will have a significantly shorter lifespan. Instilling good eating habits when kids are young makes it much easier for them to stay healthy as they grow older.

In this video the instructor shows how to set parental controls for a user ID account in Windows 7. To do this go to the 'Start Menu' and go to 'Control Panel'. In the Control Panel window select the 'User accounts and Family Safety' link. There is an option called 'Set up parental controls for any user'. Select that link and it opens a window where it asks you to Choose a user and set up parental controls. There you are presented with some user accounts that are currently active on that syst...

Not exactly sure how to get a hold of a death certificate? Whether you need a death certificate to trace your family history or to make a legal claim, follow these steps to get the record you need.

Caged Fighter: Make your way across town and you'll find an injured soldier on the rooftops that gives you some new information on finding Bartolomeo, who should in turn help you with Silvio. You get a large green area added to your map, but note that it's overlapped by a restricted area. Expect trouble.

This session is about page view sharing. Click collaborate, send collaborate live. It works with Acrobat. It opens a live chat session. Log in with Adobe ID. You can invite others to collaborate. Click to select name, attach a file and send an email. File can be saved on Acrobat. Access can be restricted to those who are invited. Collaborate live panel opens. You can open the invitees computer. Invitee needs to sign in. You have the ability to chat. Start page sharing. Pages are synchronized....

A big problem for many women is how to keep your tummy from showing. Well, YouTube user BeverlyLaneTV is here to help show you how by giving you examples of what you can wear. There are many ways to avoid the tummy showing but the easiest and most efficient way is simply clothes. Ruffle dresses are the first and the best way to cover your tummy and what this does is it give you a camouflaged look and it make a slender line across your mid section . Next are banded tops, which the band is at t...

Worried your canine might bite somebody? Afraid to take them on walks anymore because of what could happen if a child walks past you? Afraid of a lawsuit? These are the worries associated with overly aggressive dogs. But with proper training, an aggressive dog can be transformed into a well-behaved companion you'll love having at your side.

When it’s that time of the month and a heavy period interferes with your lifestyle, it’s time to take action.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Facebook rolled out a new feature that lets your friends ask you about your current relationship status. This is great feature if you use Facebook for finding hookups, but if you use it mostly to connect with family and friends, a bunch of questions about your dating status can get annoying real quick.

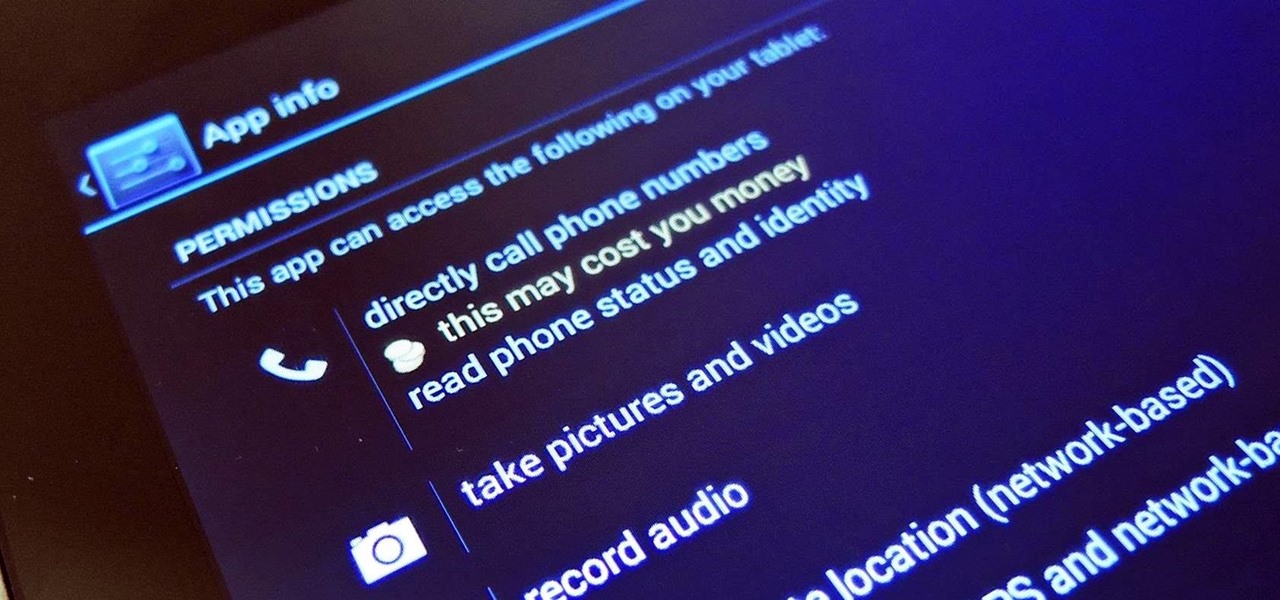
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

Android 9.0 Pie moved the status bar clock from the right corner to the left to accommodate phones with notches, but there's one major downside for Samsung users: since no Galaxy phones have a notch, all this did was take away space for the notification icons that would otherwise start from the left corner.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Recently, I ran across SecGen, a project which allows a user to create random vulnerable machines. I absolutely love vulnerable machines, since a vulnerable VM is a safe and legal way to practice hacking tactics, test out new tools, and exercise your puzzle-solving skills.