Apple just jumped on the auto-play bandwagon with their revamped App Store in iOS 11. Now, when you visit an app or game page that has a video trailer, it will automatically play. This can not only get pretty annoying, but it can eat up your precious data. Luckily, there's a way to restrict these auto-playing videos to Wi-Fi only — or disable them altogether.

TrueCaller is sharing your phone activity by revealing the last time your phone was used to contacts. The application used to identify unknown callers launched in 2009 and has faced a wealth of privacy concerns before.

Facebook released a new app in November 2016 that aimed to compete directly with Snapchat, but it was only officially available in Brazil—and still is. The app, called "Flash," is so much like Snapchat that it's not even the slightest bit of a stretch to call it a clone.

To help keep sleepy binge-watchers from sleep-"watching," Netflix asks if you're still watching after a semi-short period of time. This means that it could be anywhere from 1 to 5 episodes that you slept through, which is better than 2 seasons, I guess—but it doesn't make it any easier to find out where you left off.

Most smartphone games are clichéd and mundane, but every now and then a mobile game will appear with a new concept or idea that sets it apart from all the rest. While other developers continue to regurgitate the same old "winning" formulas, developer Sebastian Goszyla is changing how we play.
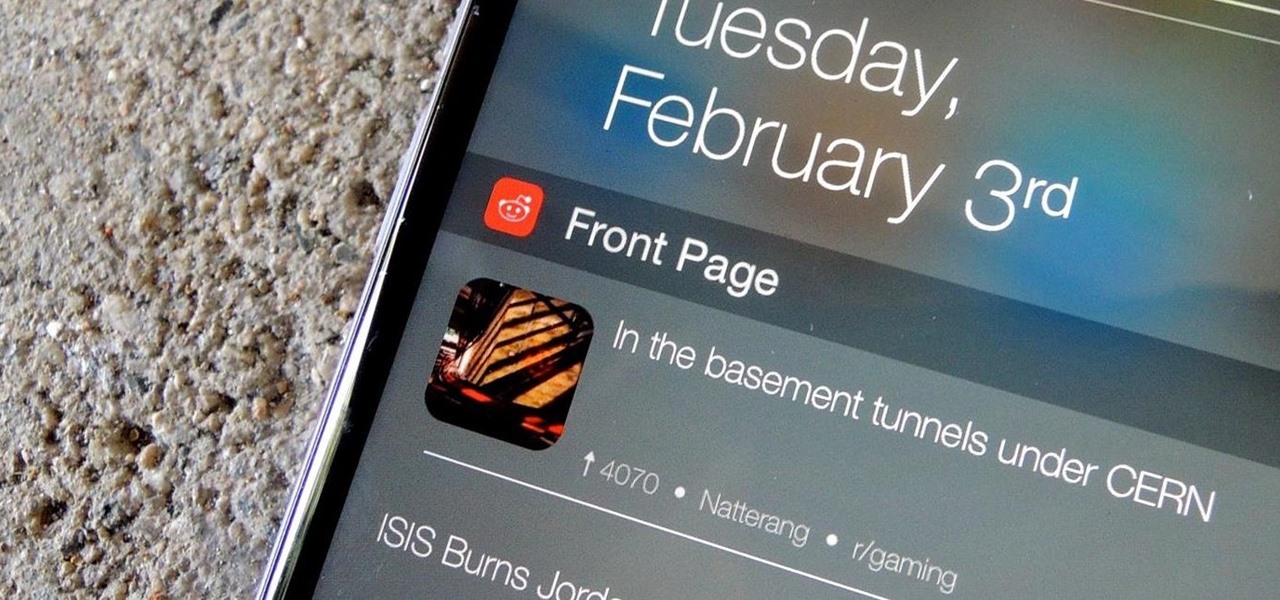
Reddit is a force to be reckoned with. What started out as link aggregator has become one of the world's most popular websites, with over 170 million unique visitors and 6 billion monthly pageviews. Whether you're into cute animals, crazy conspiracy theories, sports, or Taylor Swift's armpit, Reddit definitely has something for every taste, interest, and morbid curiosity.

Like most iPhone users, I place my most essential apps in my dock as it allows for easier access to them from the home screen. Unfortunately, iOS restricts the dock to just four measly apps, but there may be five or six that I really want to place in it.

As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

We don't typically cover games here on softModder, unless they have some special feature to offer like unlocking your device, but sometimes you've just gotta game. When you've only got a few minutes to do so, you've gotta choose the right game, and I've got just the thing for you.

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

Ways to Blocking a Website on a PC Open the “Control Panel” by click “My Computer” on your PC

When it comes to multitasking, the Samsung Galaxy Note 2 is the master of all smartphones, thanks to its huge screen size and many features. The phablet's display compliments its multi-window mode, which lets you run two apps simultaneously side by side Another cool feature is floating apps, which makes multitasking even better. So, with all of these cool features, what else could possibly be added to the Note 2's arsenal that it doesn't already have?

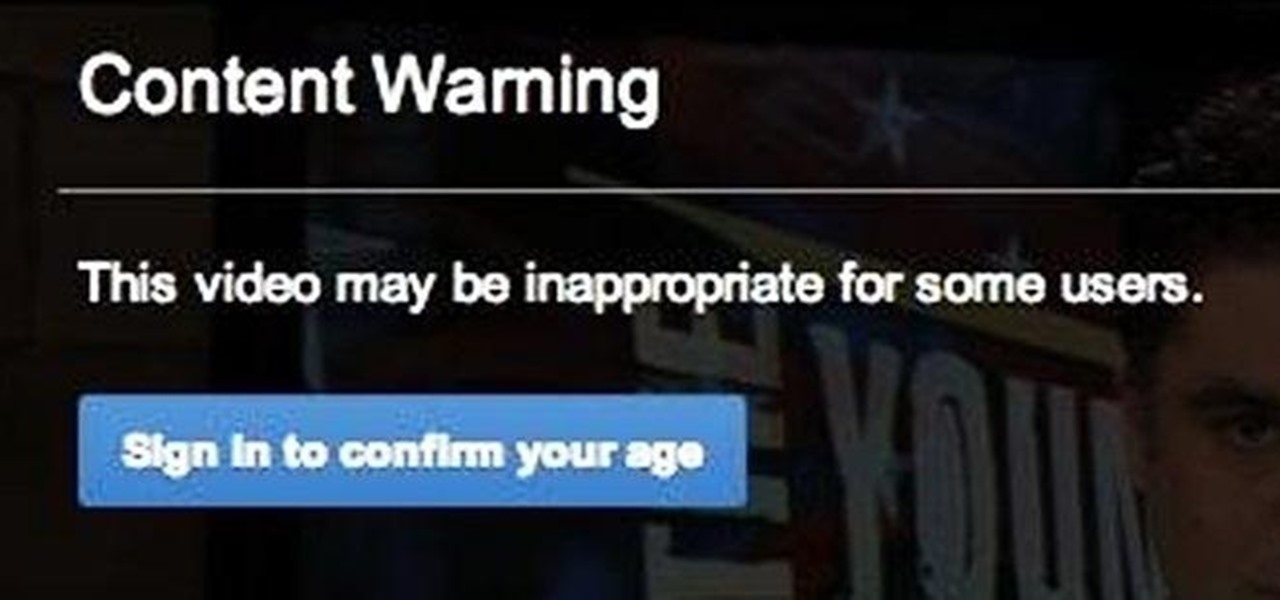
YouTube is the first place I go to watch funny videos online—me and about a billion other people. But one thing that always annoys me is having to sign in time after time to view age-restricted videos.

Yesterday, Bryan Clark pointed out a new option on Verizon's privacy settings that gives new customers 30 days to opt out of a data sharing program that gives advertisers information on basically everything you're doing on your new iPhone (or any other smartphone).

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

By now you're probably already an expert at creating cover images for your Facebook Timeline, especially if you've taken advantage of those free Facebook cards that were (and still are) being offered. But just in case you need some help making eye-grabbing cover images, there's a few tools you can try out to streamline the process.

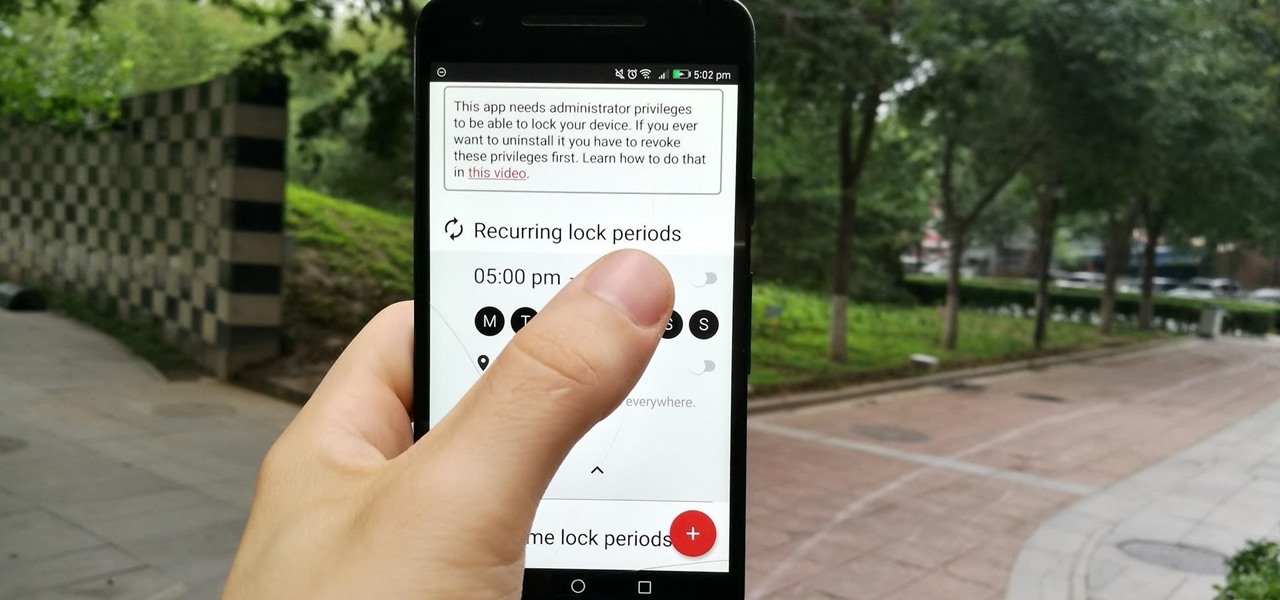
The OnePlus 7 Pro comes with a new Zen Mode feature to help increase your concentration and reduce distractions. It takes things a step further than Google's Digital Wellbeing by disabling your device and stopping sounds. But even if you don't have a OnePlus, you can now get this distraction-free feature on any phone.

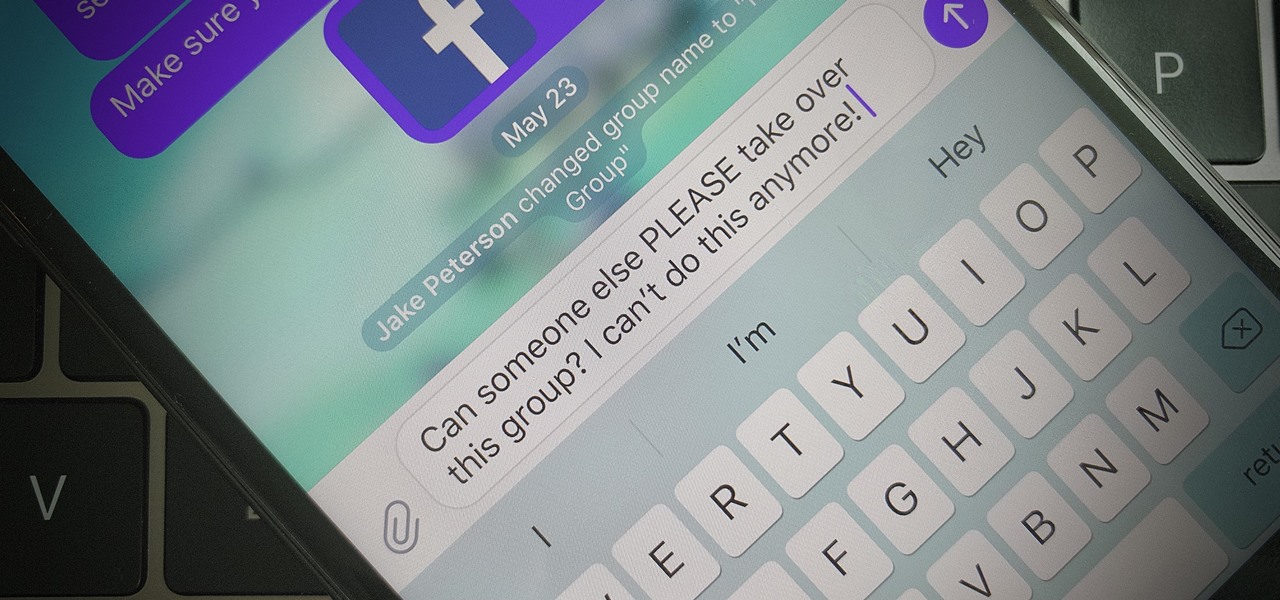
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

In the first guide, we laid the groundwork for our ultimate goal of uploading and running the unix-privesc-check script on our target. We identified an input field vulnerable to SQL injection and utilized Sqlmap to set up a file stager on the server. Now, we're ready to upload files and execute the script, so we can identify any misconfigurations that could lead to privilege escalation.

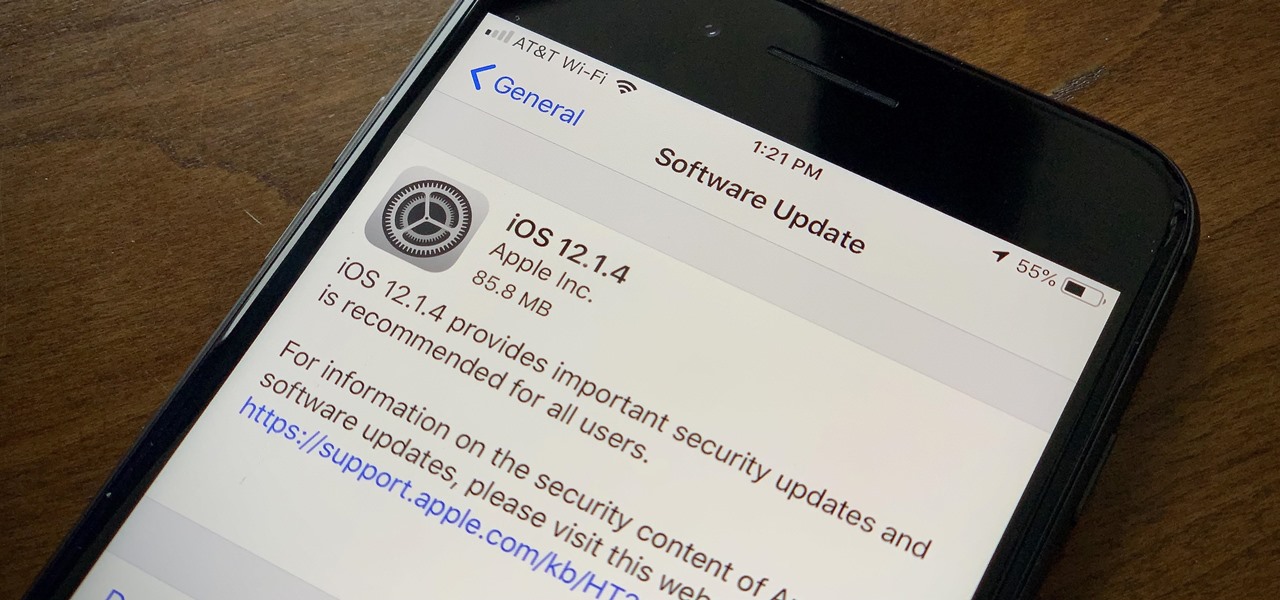
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

Although next week will mark the late David Bowie's 72nd birthday, his fans and admirers are the ones receiving a gift in the form of an augmented reality app that explores the artist's career

A few long-awaited iOS 11 features that Apple had promised way back in June 2017 have finally made their way to iPhones with the iOS 11.4 update. Aside from finally delivering on those, there's not a whole lot new in iOS 11.4 as a whole, though, there are a few things you'll definitely want to know about.

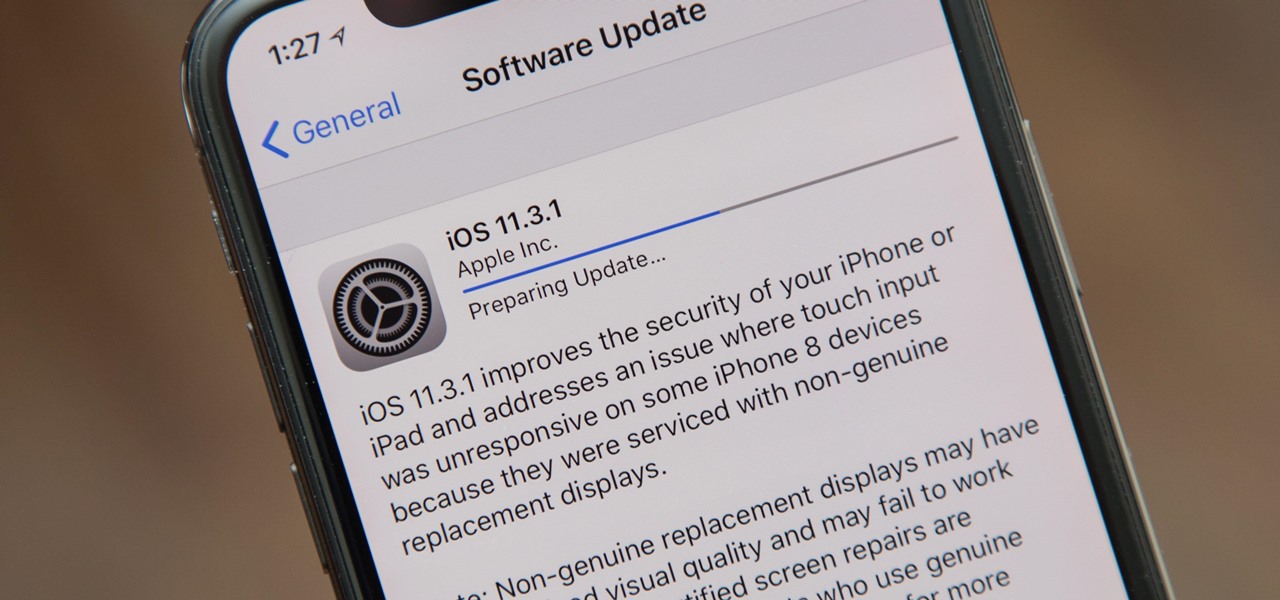
Apple released the iOS 11.3.1 update for iPhones on Tuesday, April 24, 26 days after the official release of iOS 11.3 and eight days after the iOS 11.4 beta 2 update. It is the first minor update to iOS 11.3, and the biggest thing in it is a fix that lets displays fixed by third parties work again.

It finally happened. Magic Leap has given the world its first glimpse at its debut device, the Magic Leap One Creator Edition.

It's long past time to face the facts: farts are funny. The first fart joke dates back nearly 4,000 years to the ancient Sumerian people. References to flatulence were also found in ancient Greece within the works of Aristophanes. (More like Aristo-fannies, am I right?) A standard in practical jokes, the whoopie cushion debuted way back during the time of the Roman Empire.

It looks like there is a fatal flaw in the current macOS High Sierra 10.13.1, even straight from the login menu when you first start up the computer. This severe vulnerability lets hackers — or anyone with malicious intentions — do anything they want as root users as long as they have physical access to the computer.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

As it turns out, your Android apps are pairing together to share your data without asking for your permission first. Researchers from Virginia Tech developed a tool called DIALDroid to monitor exchanges of data between Android apps over the last three years, and what they've found is quite alarming.

Google's Pixel phones have a feature that lets you swipe down on the fingerprint scanner to open your notification shade and Quick Settings panel. It's one of those features that make you wonder why it wasn't there in the first place, since it gives you another way to interact with your device, and your fingerprint scanner isn't being used while you're screen is on anyway.

Android device manufacturers may see the new Pixel "Phone By Google" devices as just another competitor, one that likely won't upset their entry-level margins. But that would be a mistake. Pixel is Google's call to action. With Google now offering as near to perfect an Android experience as we've had so far, OEMs that want to keep selling smartphones in a world flooded with them will need to start working for the privilege.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

Hello fellow Nullbytiens, I'm Washu, a long time commenter but first time poster. Today we'll be making an IRC bot, if you haven't seen OTW's post about the new IRC channel I would encourage you to go check it out. He does a good job at explaining what IRC is and how to get set up.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

When you finally turn the privileged age of 21 in the U.S. (or 18 in most other countries), the first thing you'll probably do is sprint to the nearest pub, order a drink, and revel in your new freedom. Congratulations, you've survived two decades on Earth, you've earned that drink.

While a mobile game developer may have built something unique, they still have to go through an arduous process of fixing bugs, smoothing out gameplay, making sure it works on different screen sizes, and following Apple's rules before they can submit their game to the iOS App Store.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

As technology continues to advance, we as consumers are privileged enough to be able to take higher quality photos and videos and listen to clearer and better-sounding music on our mobile devices. But sometimes we forget that there's a price to pay for that awesome content—enormous file sizes.

Widget toggles, or "power toggles" as they're often called, have been around for quite a while. They serve their purpose nicely as an easy way to add switches to your home screen or notification area for functions that don't come with the stock software on your device.