The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Your best chance of getting to a destination on time during rush hour is to drive through relatively empty HOV lanes. Thankfully, if you're using Waze to navigate through traffic, you can easily locate HOV or HOT routes to optimize travel times by adding your toll passes in the app's settings.

While millions eagerly await the stable Android 8.0 release for the Galaxy S8, the beta is already in the wild and readily available. Notable improvements include notification channels and the revamped Samsung keyboard. One aspect often overlooked are new customization options, a huge part of Android. Let's take a look at what's new for customization on the S8's home screen in Oreo.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

After installing the new iOS 11 update on one of our iPads, we noticed something peculiar — AirDrop simply stopped working. The button was still there in the revamped Control Center, but it was almost imperceptibly grayed out. Tapping it did nothing, nor did long-pressing or 3D Touching. Even more perplexing, AirDrop was just working flawlessly before the update.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

With the US Department of Homeland Security (DHS) banning laptops and tablets on flights originating from 10 international airports, and the United Kingdom taking similar precautions, international travelers are faced with hours of non-productive — or far less entertaining — flight time.

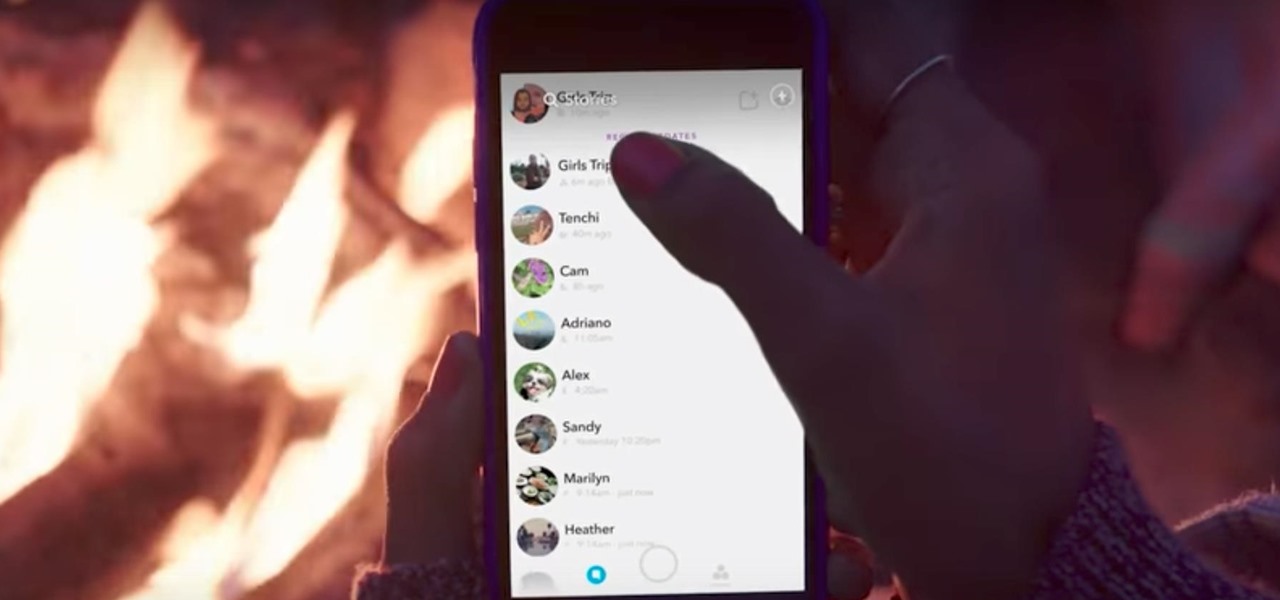
Snapchat hit back at its arch-rival Facebook this week with a number of new Group features, including custom stories. Facebook and Instagram both rolled out clone Story options this year, but Snapchat is obviously trying to up the ante in this arena.

Uber's chance at driverless domination may be ripped away as its legal battle with Waymo escalates. The company's self-driving program is now under threat of closure if the allegations of premeditated theft are proven

Stop me if you've heard this one before. You plop a marshmallow down in front of a kid and propose the following: You can eat this marshmallow now, or you can wait twenty minutes and eat two marshmallows. What do you think the kid is going to do? Better still, what do you think you would do? Personally, I'd eat the first marshmallow without hesitation. But now we're getting off track ...

A baby with severe Zika-related birth defects was born in San Diego County this week, prompting officials to urge pregnant women to avoid disease hotspots.

As you get barbecuing this summer, you're likely to encounter a few grills that aren't exactly the cleanest. At parks or campgrounds and even on your friends' grills (or, um, your own), no one wants to place food on gunked-up grill grates.

Since its purchase by Microsoft in 2014, Minecraft has regularly been pushed to new platforms such as Windows 10, Wii U, and Fire TV. In that spirit, Microsoft-owned Mojang has been developing virtual- and augmented-reality versions of the blocky sandbox game.

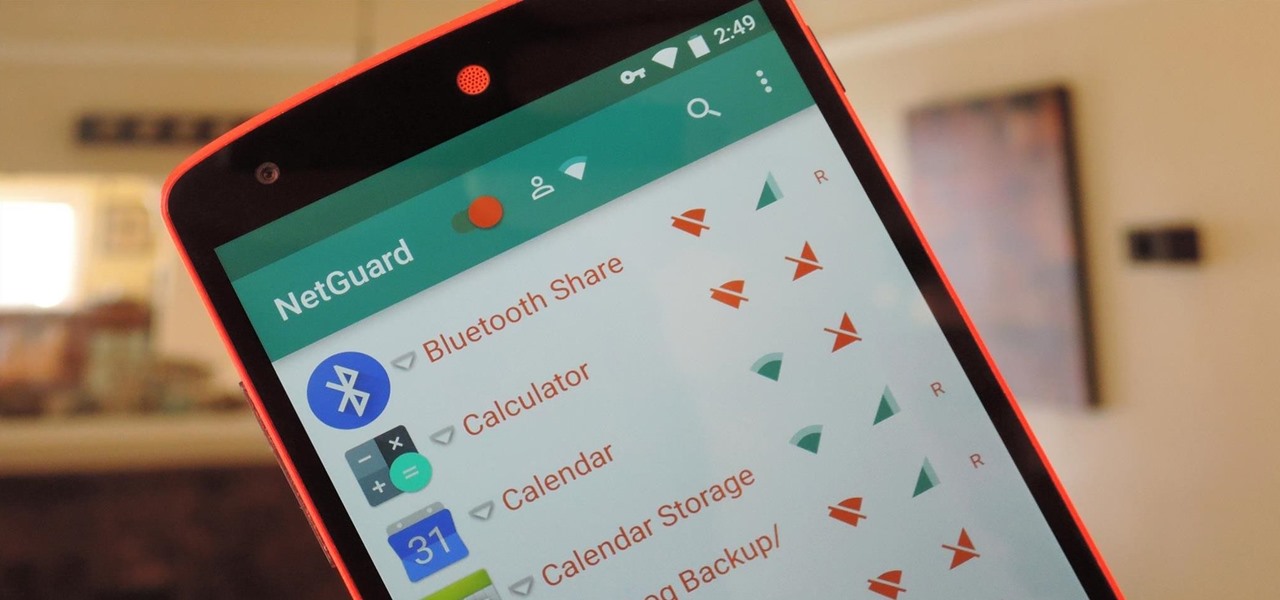
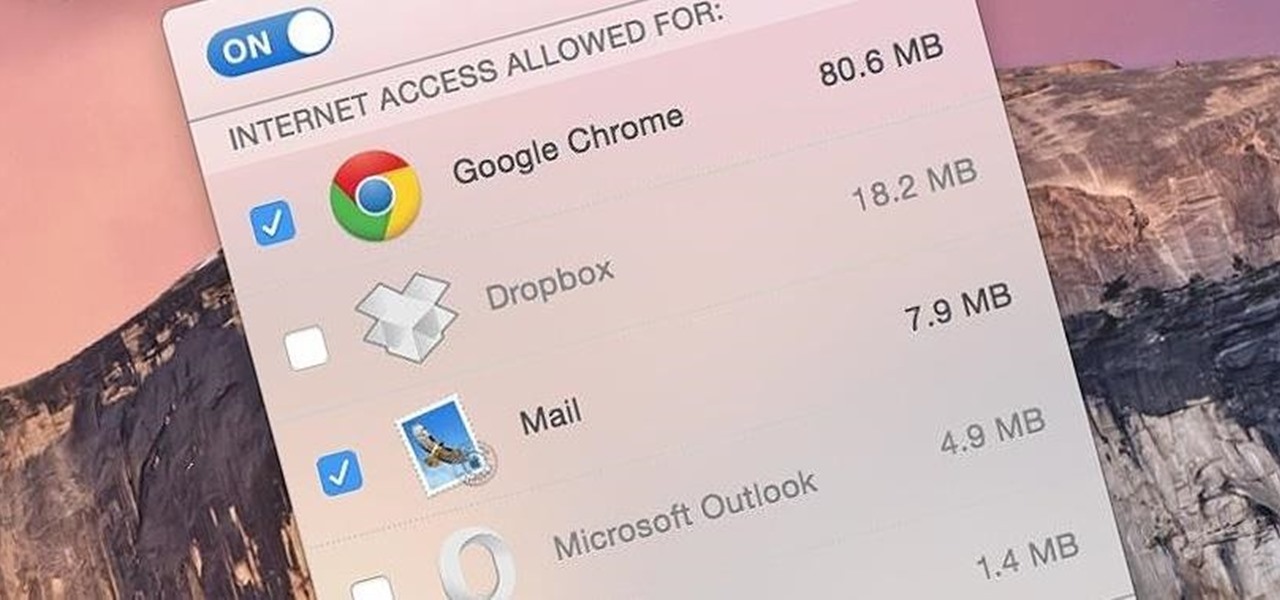
If you exceed your monthly mobile data limit, your cell phone bill can skyrocket pretty quickly. This is why a lot of people vigilantly monitor internet usage and even uninstall apps that use too much background data.

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

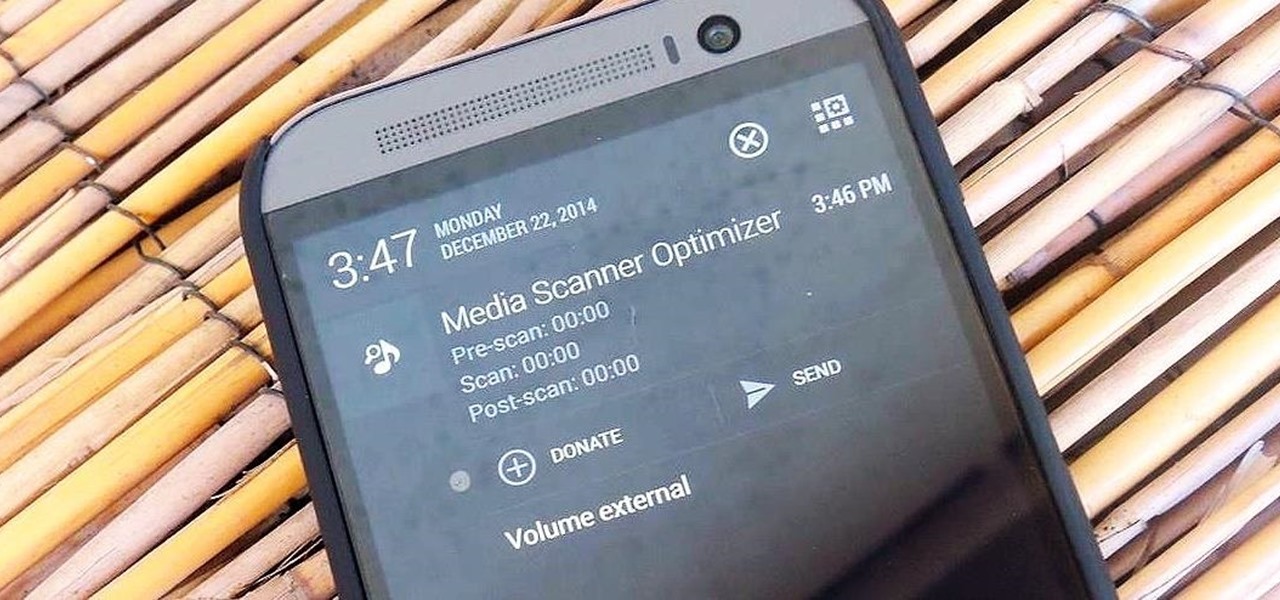
Battery life is extremely unpredictable on an Android. Finding the right ROM and kernel combo can make or break having the kind of battery that will last you all day long. Even if you do find the perfect pair, you then have to worry about apps, widgets, and other processes constantly waking your phone and draining your juice. While your media scanner isn't the biggest battery hog out there, it can definitely take a chunk out of it.

Most diehard Mac users have used TinkerTool at some time or another, and if you haven't, it's time to start. Whether it's to change your system's font or to disable UI animations, it seems like anything you could ever think about tweaking in Mac OS X is doable through TinkerTool. And now, developer Marcel Bresink has updated his app to work with Yosemite, so let's see what it can do now.

Whether if it's to play games or watch Netflix or YouTube, children love using our smartphones and tablets. As an uncle of many, I don't mind my nieces and nephews using my gear, but I do mind them opening apps they have no business being in, like my photo gallery or messaging app.

With all of the top-notch specs that the Galaxy S5 sports, the only minor quibble users have had with its hardware is the speaker situation. A front-facing earpiece is used for phone calls, but all other media is restricted to a single rear-firing speaker.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

There are over one million apps in the Google Play Store, and many of them are restricted to certain device types, brands, and Android systems.

As great as Google's own Play Music app is, your MP3 library is restricted to Google's own app. There are much better music players that give Google Play Music a run for its money, but duplicating music files on your device for this reason alone is a waste of storage space.

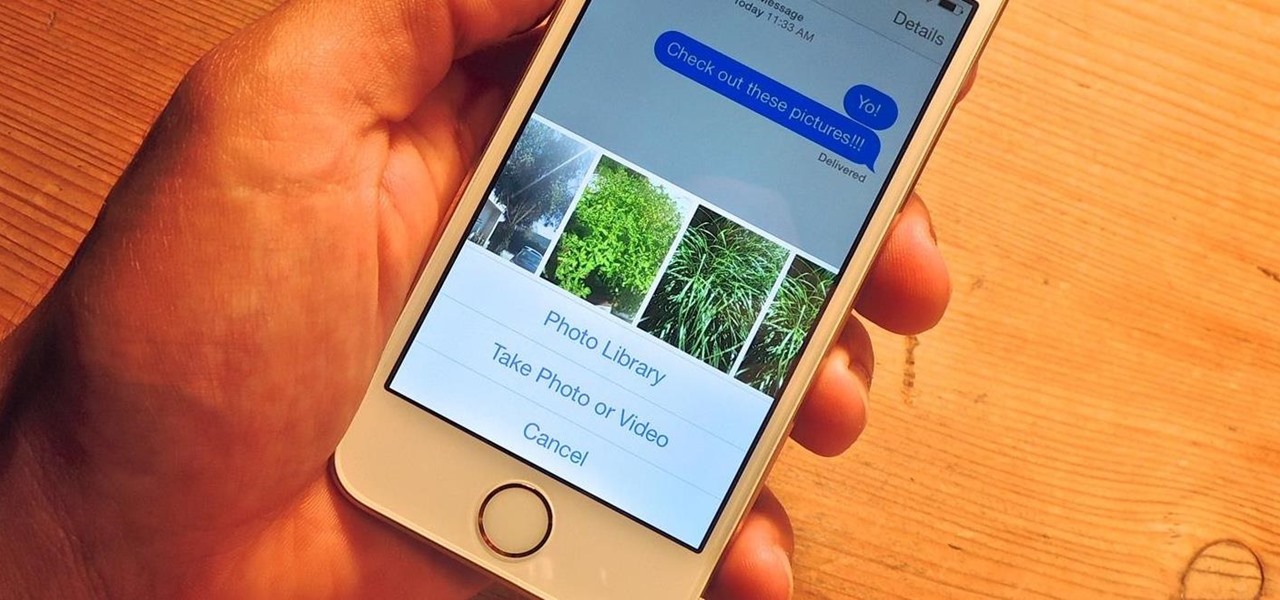
As it is right now, you can only send 5 images by email at the same time from your Camera Roll in iOS 7. There are some workarounds to increase that number, but a new feature in iOS 8 is finally making them unnecessary.

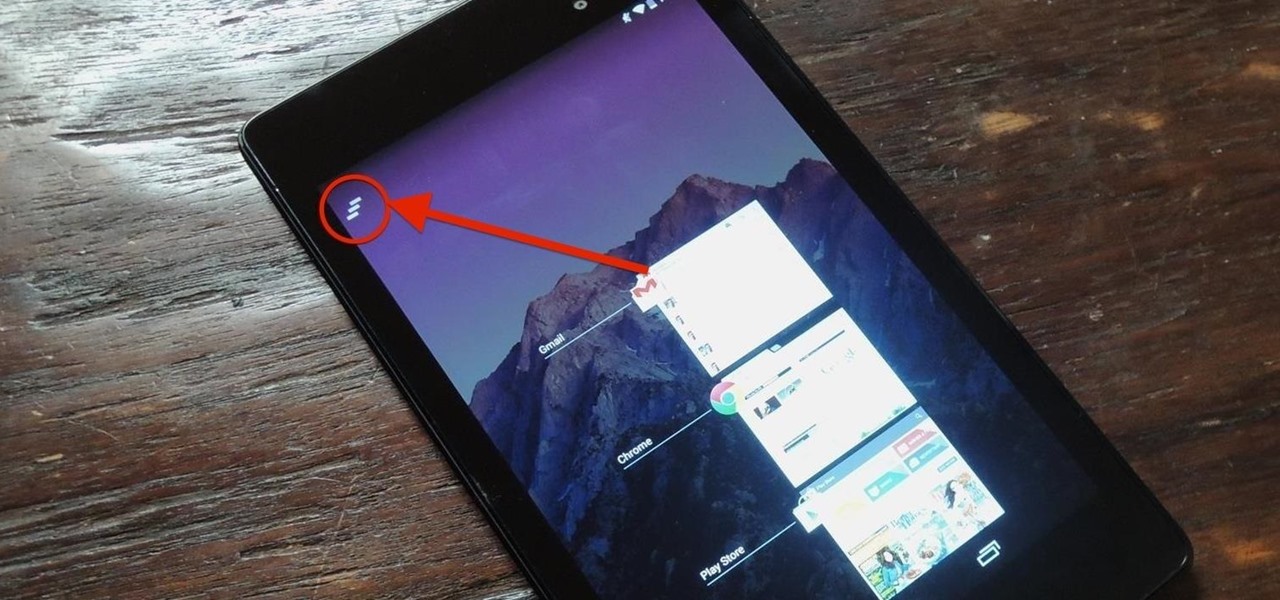
Unlike the Galaxy S4 and other Samsung devices, the Nexus 7 doesn't have a Clear All option in the recent apps menu. It's a highly requested feature, as it cuts down the time required to go one-by-one swiping each individual app (you can't swipe away multiple ones at the same time).

With the Galaxy S5's root bounty over $18,000 and climbing, there's still no Superuser in sight. That doesn't mean we can't tweak and personalize our shiny new toys, though. Several customization options are available just by virtue of the S5's Android base, and installing a custom launcher is one of the fastest ways to get a fresh look.

Video games have come a long way over the last 30 years. In the late-'80s, Atari, Nintendo, and Sega were taking gaming from arcades to living rooms. Back in 1994, the Super Nintendo and Sega Genesis were in bedrooms everywhere, and over the next couple of years, were slowly being replaced by Sega Saturn, Nintendo 64, and the first ever Sony PlayStation.

Apple has acknowledged a problem with the sleep/wake key, better known as the power button, on a certain number of iPhone 5's manufactured through March 2013. As a result, the company has announced the iPhone 5 Sleep/Wake Button Replacement Program, which will replace the power button mechanism, free of charge, for certain iPhone 5 models.

If you have a limited or restricted data plan, monitoring your usage can be the difference between escaping the month without overage fees or emptying out your wallet.

There wasn't really anything too special about the S Pen on the Samsung Galaxy Note 2, with its limited capabilities and finicky sensitivity. Luckily, the S Pen was greatly improved on the Note 3, the biggest enhancement being Air Command, a floating menu that appears when the S Pen is removed that gives quick access to all the new features.

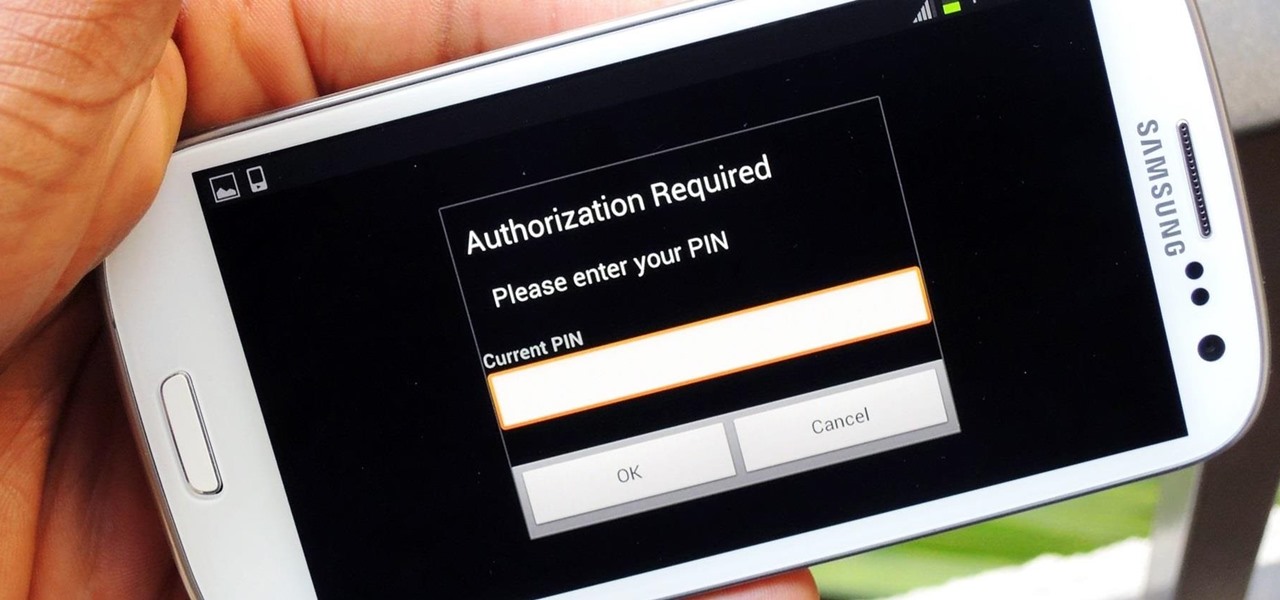
Normally, "restricted access" is something you despise. No one likes to be told they can't do something, especially when it comes to the Internet. Unfortunately, having web access at all times can not only eat away at your wallet, but make your day less productive overall, so some sort of moderation is needed.

This is my first contribution in an ongoing series on detailing the best free, open source hacking and penetration tools available. My goal is to show you some of the quality tools that IT security experts are using every day in their jobs as network security and pen-testing professionals. There are hundreds of tools out there, but I will focus and those that meet four key criteria:

Apple's latest iPhone and iPad software, iOS 15.5 and iPadOS 15.5, became available on May 16, so you can download and install it right now if you haven't already. While there aren't as many new features as iOS 15.4 and iPadOS 15.4 had, there are a few big ones in the U.S. you'll want to know beyond Apple's minuscule "About this Update" information in the "Software Update" menu.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

OnePlus phones are easy to root, but that also means they're easy to brick if you get trigger happy with your superuser privileges. If you find yourself in this situation, you'll quickly realize the OnePlus firmware download page doesn't provide files you can flash in Fastboot mode.

With the Galaxy S20, Samsung has officially removed the Bixby button from its flagships. While it was a controversial key, in its later days, it did give us the ability to launch an app or custom action at the press of a button. There's still a way to do something like that, but now, you'll have to use the power button instead.

One vital part of Android 10's new navigation system is the "QuickStep" gesture. Swipe up from the bottom of your screen, then pause. You'll see your recent apps along with a dock containing a handful of icons for quick access. This dock is provided by the phone's launcher, which means your home screen is now integrated into the multitasking UI. So what happens if you change your home screen app?

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.