Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Google collects an enormous amount of personal data. While some of this data is used for targeted ads, others tidbits of info such as our location are used to improve our mobile experience. While it is natural for us to distrust Google's intentions, by allowing their data collection, we can add new functionality to our favorite apps.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.
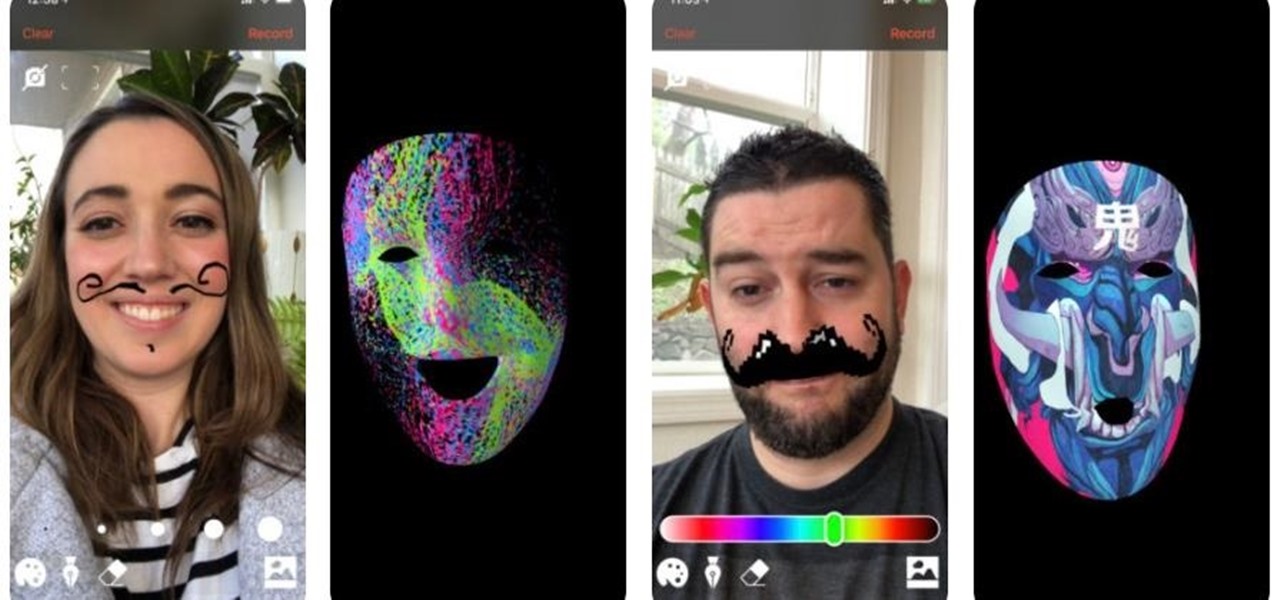
Thanks to Face Maker, a new app for the iPhone X, children everywhere can now avoid the trauma of face painting.

Google just unveiled it's biggest search product in recent memory, except this time the search giant is looking to take over the world of virtual objects.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

In the ongoing search to find better ways to use antibiotics, an extract made from maple syrup has some surprisingly important medical benefits.

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.

Google's personal messaging service Allo could reveal your search history and other private information to friends if the Google Assistant bot is called upon in chats, according to a story from Re/code.

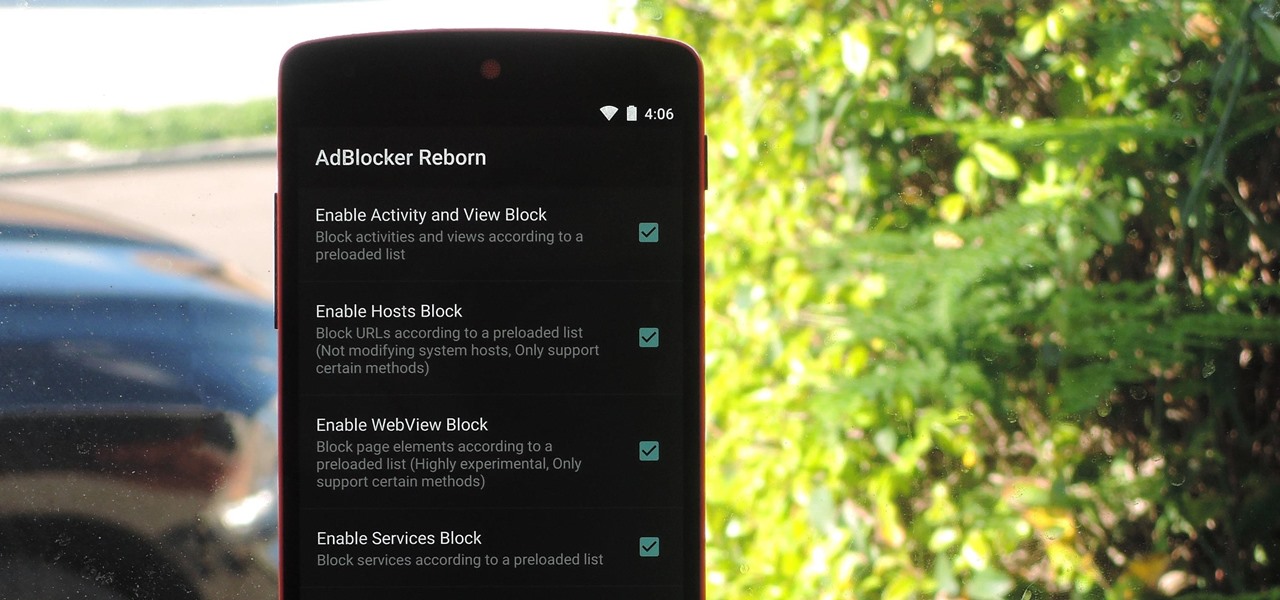
When it comes to ad blocking on Android, there's no better app than AdAway. The popular root mod filters out ads at the hosts file level, so no extra processing power is used, and your phone is literally incapable of loading most ads.

The Note7 fireworks bonanza was unprecedented in scope. A recent report suggests that Samsung could lose upwards of $20 billion in lost profit due to this fiasco.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

Autodesk offers some of the most popular software for computer-aided design (CAD) projects, which involve all sorts of 3D rendering. Their tools are clearly suited for use with the Microsoft HoloLens, but so far very little supports HoloLens development outside of Unity. Why is that?

Over the years, YouTube ads have become more and more integrated with the videos themselves, which means traditional Android ad blockers can no longer block the ads without blocking the videos. It's gotten to the point where the only ways to get rid of the ads are to either subscribe to Google Play Music and YouTube Red, or go through the complicated process of installing the Xposed Framework.

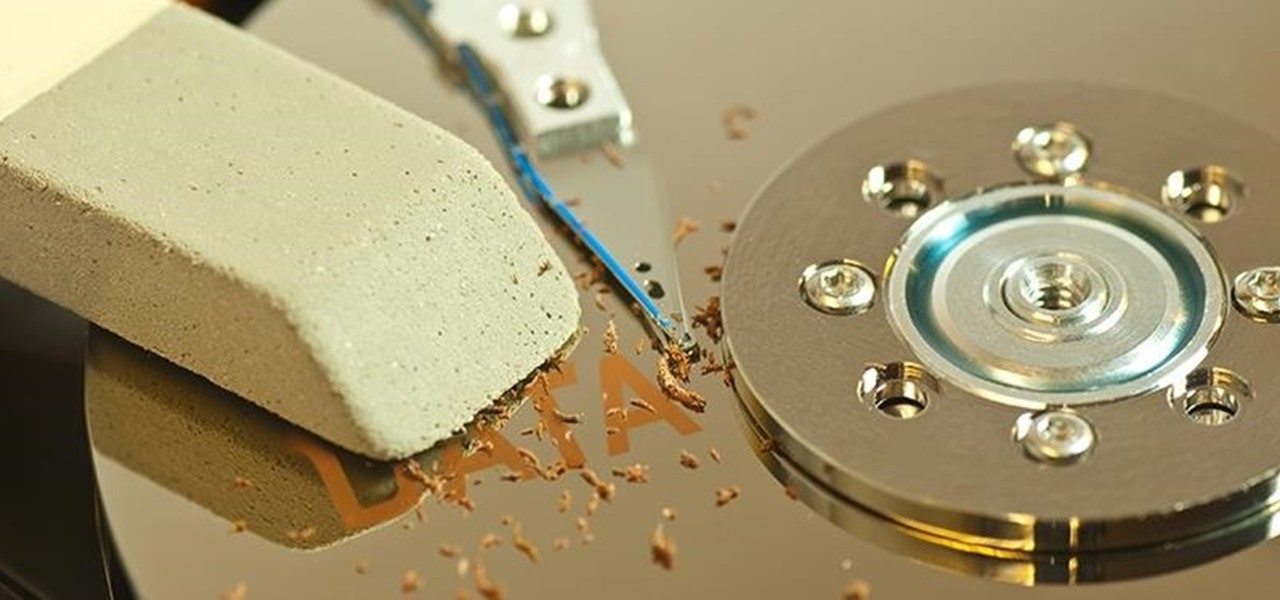
When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

Welcome back everyone. As many of you know, reconnaissance is extremely important in any successful hack. Without proper reconnaissance, we won't know what we're about to get into, literally.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

Your average Android phone or tablet comes with quite a few apps already installed—even before you turn the device on for the first time. These pre-installed apps are certainly helpful when it comes to getting your feet wet with Android, but in many cases, they're not always the best apps available for accomplishing the tasks that they perform. Additionally, many third-party apps can add lots of cool functionality to your device, so you might say that sticking with only the pre-installed apps...

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

SoundHound, the Shazam-like song-matching service, recently announced a new mobile app called Hound, which wants to be your one and only intelligent personal assistant.

Apple's latest round of devices—including the MacBook Pro, Apple Watch, and the iPhone 6S—use a new touch input method that can detect when you've applied a bit more force than usual. Dubbed "Force Touch" ("3D Touch" on the new iPhones), this gesture simulates a long-press or right-click, but it usually requires special hardware to detect the amount of pressure you've applied.

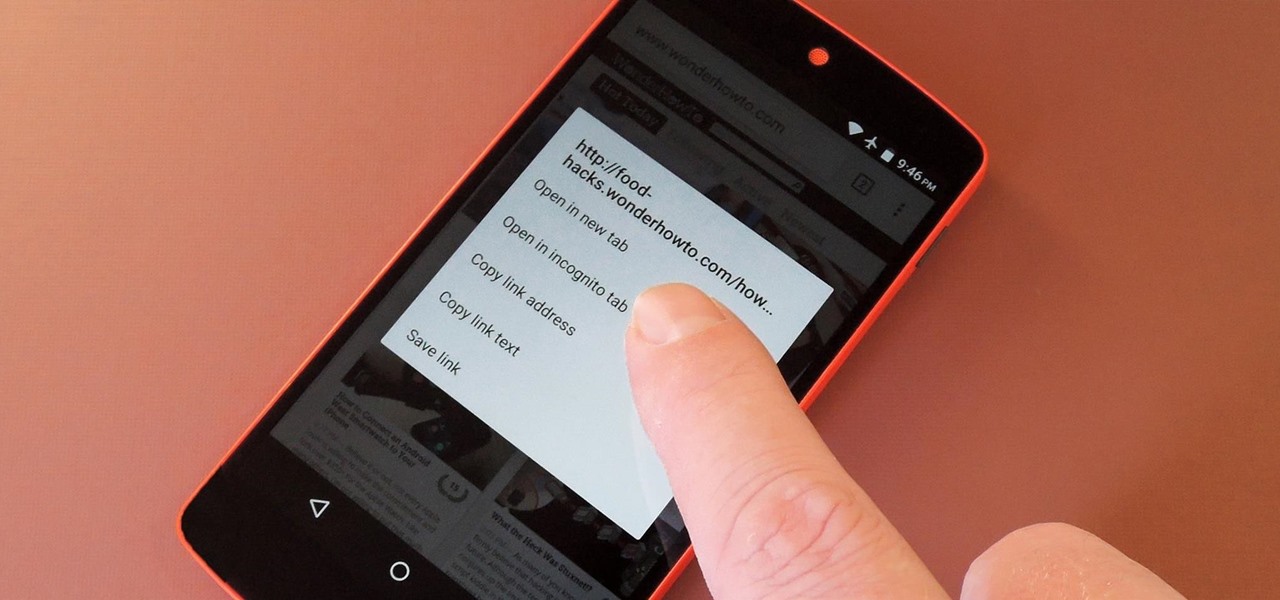
With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

We've all heard the cliches: always look at the glass as half full; a smile can change your entire day; and there's always a silver lining.

Google continues to be the most commonly-used search engine for a reason. While continuing to stay ahead of the pack with advanced semantic search functions, Google even introduced Knowledge Graph results that offer key information without ever having to click a search result.

The interwebs is a great source of information, but sometimes said information is not always legit. That can be frustrating when it comes to making fun food, costumes, and arts and crafts for Halloween, like this bowl of "bloody" gummy worms.

"Bullshit, bullshit, bullshit" was one of my favorite lines from the movie Forgetting Sarah Marshall, but it's also exactly what you have to wade through to find a good movie to watch.

At the core of your Galaxy S5's hardware lies the central processing unit, or CPU for short. Practically every piece of data, every binary bit, has to pass through your CPU before it can be used to display a video or execute a game command.

The Galaxy S5's screen is truly a feat of modern technology. It uses what is known as an AMOLED display—an acronym for Active-Matrix Organic Light-Emmitting Diode. In short, this technology means that every individual pixel on your phone's screen emits its own light. This is a break from the traditional LCD technology that requires a backlight for any pixels to be visible.

Let's be real, browser histories are virtually useless. Trying to find something you passed up a week ago is like, pardon the cliché, finding a needle in a haystack.

Merely fidgeting and shivering can burn calories, but now you can add trembling in fear to the list too. Just pop in a good horror movie and turn down the lights to burn off up to 200 calories. What would you rather do? Walk for over 30 minutes or watch a 90-minute scarefest?

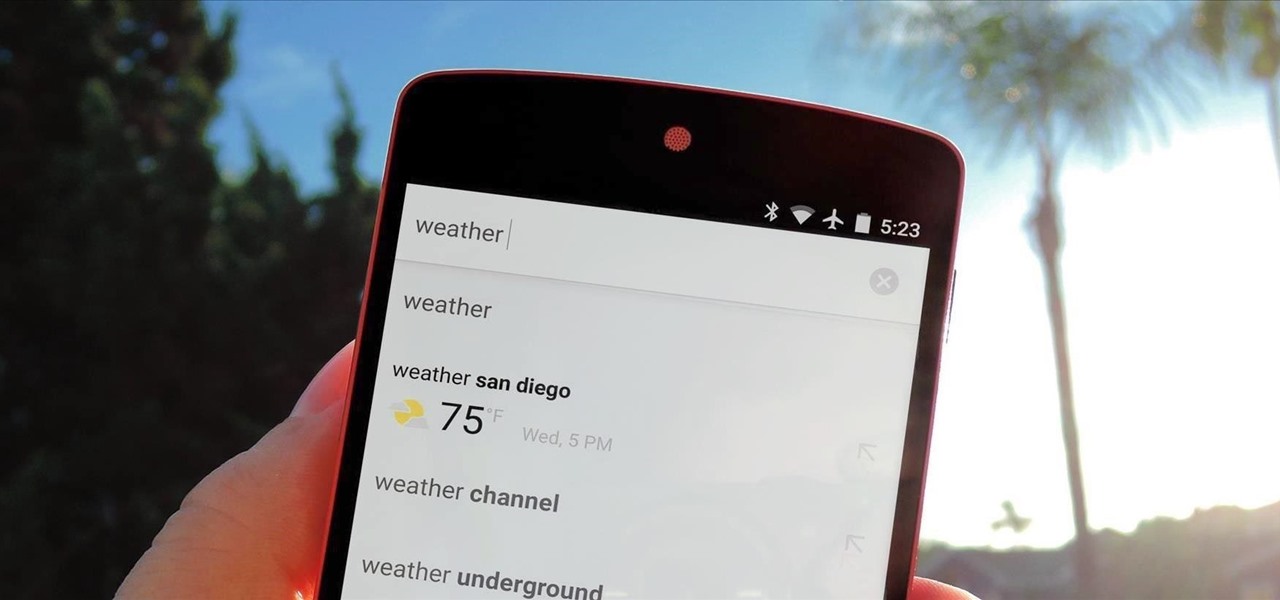
Prior to the release of Android 4.0, most devices had a dedicated search button. This functionality allowed you to search Google from your home screen and app-specific content from within any app. Eventually, though, this dedicated search button was ditched in favor of an icon in the action bar of apps, and a search bar on the home screen.

The new iOS 8 was just unveiled, and it looks pretty awesome. Apple showed off some of the enhancements and new features we can expect to receive in the fall at WWDC, and while not the huge facelift we saw with iOS 7, it does showcase what Apple does best—refinement. Continuity

Remember those horrible, soul-crushing studies from a few years back linking grilled meats with cancer? Unfortunately, they're still true, but scientists have recently found that an unexpected ingredient can curb some of the harmful effects of high-temperature cooking.

The recently released HTC One M8 and the upcoming Samsung Galaxy S5 are both boasting selective focus features for their camera apps, but with a 13 megapixel camera, the GS4 can take some pretty stellar pictures, too.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

There is nothing more refreshing than an ice cream in a hot summer day. And even though, here in Australia, summer is "just" a couple of months away, I still like to have a scoop or two every now and then. However, I like to make the ice cream on my own. In this way, you can make whatever flavour you want, plus you know what type of products you have used and it usually tastes better than a commercial one.

Give me a paintbrush and easel and you'll be sorely disappointed, but give me a Samsung Galaxy S3 and a new app called Let's 8-Bit Art and you might call me the next Picasso.