Before you figure out how to strip the paint on your car to bare metal, you should should first ask the question, should I strip all of the paint off. Depending on the type of job you're doing, it may actually be better not to strip all of the paint off.

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.

Garlic is a key ingredient in many delicious meals, and if you've been a fan of our site for even a short while, it's no secret that we love to share tricks and tips to make cooking with garlic even easier than you first assumed.

The Galaxy S7 edge comes with a feature called Edge Apps that lets you quickly launch your favorite apps by swiping in from the edge of your screen. It's a natural and intuitive gesture, and as a result, we've seen a recent influx of apps that look to emulate this feature.

Apple's MacBook line of laptops is quite famous for their extensive battery life, thanks to various technologies that Apple has utilized. However, all things must pass, and over time your MacBook's battery will degrade. Certain use scenarios can accelerate the degradation of the battery—from excessive usage to high temperatures to overloading the system—and this can all lead to the untimely obliteration of your battery.

Let's set the scene: you're at home, it's late in the evening, and you have a hankering for those deliciously decadent chocolate-wrapped squares of ice cream goodness. You could drive to the store and pick up the usual pack of Klondike Bars in the ice cream aisle... or, you can easily make these babies in the comfort of your own home with only three ingredients for a fraction of the cost—in any flavor you want! The choice is obvious. So, without further ado... Ready, set, Klondike!

Remember that feeling when you first took your smartphone out of the box, powered it on, then proceeded to futz around with it for the rest of the day non-stop? If you've owned your device for more than a year, chances are, that scenario is a distant memory by this point.

The Oculus Rift is finally shipping to customers in more than 20 countries, and we're getting a good idea of how the device holds up from the initial reviews. You'll see some common threads throughout: along with an impressive virtual reality experience, the device is very comfortable with a solid design.

On the list of problems with Android, manufacturer tinkering ranks near the top. Slow or nonexistent updates, poor performance, excessive bloatware apps—all of these things can be attributed to manufacturer skins like TouchWiz or Sense, and none of them are issues with unmodified, Vanilla Android devices like the Nexus series.

Using a technology we like to call "Hive Computing," several Android apps allow you to contribute idle processing power to help further scientific research. This basically means that when you're not using your phone or tablet, it can join forces with other idle devices to form a supercomputer that scientists can use to potentially make a world-changing breakthrough.

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

After months of speculation and sifting through rumors, Samsung finally unveiled its Galaxy S7 and S7 edge flagships, and they're pretty much what we had been anticipating. But just because there weren't any major surprises doesn't mean that it's not still exciting. Let's have a look.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

Hello, Null Byte! Mkilic here. I doubt anyone knows I even exist on Null Byte, so hopefully this post will allow me to become more involved in the community and also help me learn even more.

The first written account of "stock" as a culinary staple goes back to 1653, when La Varenne's Cookery described boiling mushroom stems and table scraps with other ingredients (such as herbs and basic vegetables) in water to use for sauces. But really, the concept of stock has probably been around for as long as people have been using water to boil food.

I recently had a small gathering of friends over for a quick cookout consisting of mostly burgers on the grill. One of my friends informed me beforehand that she didn't eat red meat, but that she would be perfectly okay with eating a turkey burger.

One of the best things about cold weather is soup, and there's nothing more comforting than a great chicken noodle soup. But I've often grabbed a can from the grocery store and found the chicken dried out and over-processed... and the noodles soggy and tasteless. What's worse: there's never enough of the stuff you like (such as the vegetables) and too much of what you don't (the nasty stuff I mentioned above).

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Here's a not-so-well-kept secret about the food industry: retailers love to take your money. And one of the ways they do that is by dividing food into smaller sizes and charging more. Have you ever noticed that a container of precut, washed broccoli costs more than a head of broccoli with the same amount of florets and stems?

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

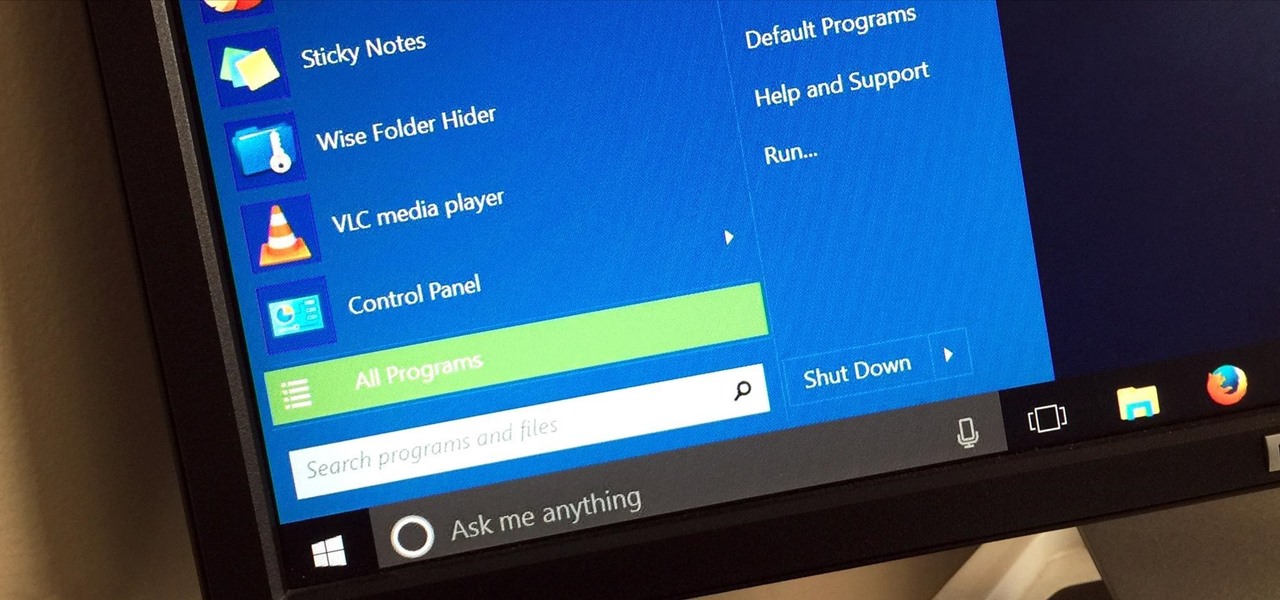
Windows 95, which introduced the Start menu to the world, recently celebrated its 20th birthday! The feature was an instant hit, becoming a core component of Windows operating systems. Well, it was removed in the mistake that was Windows 8, but you should know by now that the Start menu has been reincarnated for Windows 10.

In my opinion, spices are the key to a successful kitchen. With a healthy array of spices and spice mixes, you have the foundation for nearly any dish that you want to make; the culinary world is your oyster. With a depleted cupboard of spices, however, nearly every recipe looks intimidating and unattainable.

One of my favorite things to do when I visit my parents is cook. Aside from the fact that I adore cooking with my mom, there's something comforting about returning to the kitchen that I first started playing in 20 years ago. Nearly all of the tools and appliances are the same ones that I used as a kid, and the familiarity is palpable.

Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs.

When I first heard about the Thermomix, an all-in-one kitchen appliance from Australia, it sounded like an old SNL commercial parody: It slices! It dices! It heats! It kneads! Is there ANYTHING this machine CAN'T do?

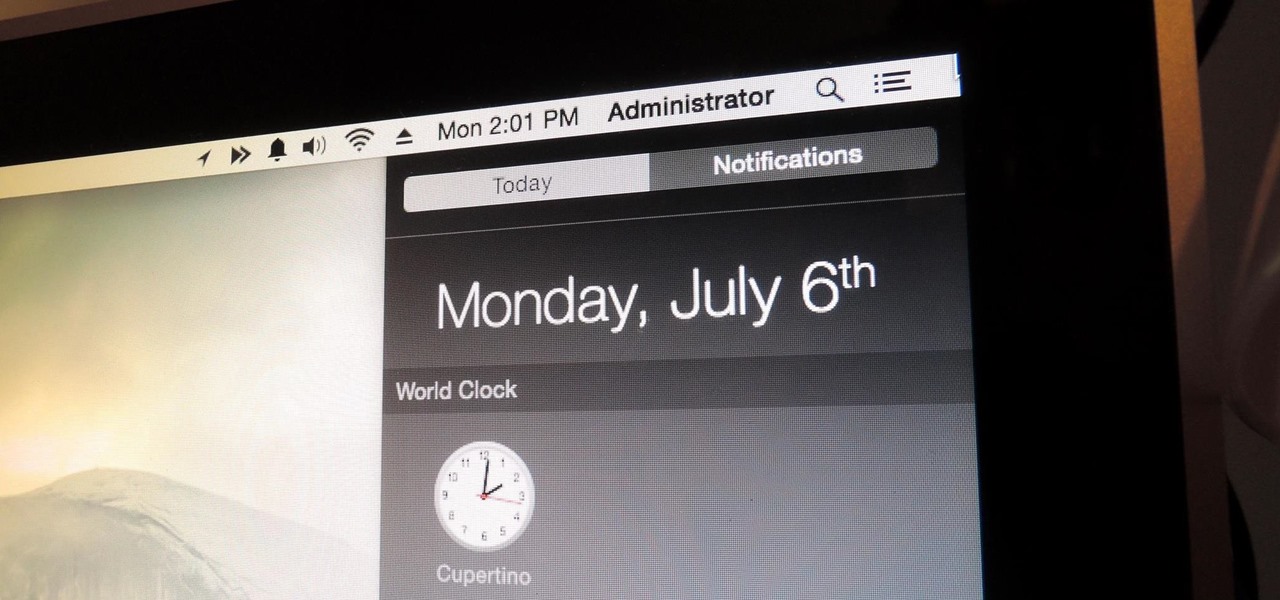
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

No offense to water, but if I could survive on coffee alone, I would. I swear I'm not addicted... I just really, really, really love the taste of a cuppa joe, whether it's hot, cold, frothed, milked, flavored, plain, whatever! And while my favorite thing to do with coffee will always be to drink it, recently I've become crazy about using coffee in cooking.

I've never met a person who doesn't love French fries. And, to be frank, I have no desire to meet such a person.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

Apple's latest update to Mac OS X, 10.11 El Capitan, is currently available in the Mac App Store for everyone to download and install at no cost. The new OS features Split View mode for better multitasking, a cleaner Mission Control, smarter Spotlight, a way to mute Safari tabs playing audio, enhanced Mail and Notes apps, and more.

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

For foods that encompass both tastiness and convenience, it's hard to beat boxed mac and cheese. Mac and cheese in a box takes 15 minutes to make, dirties only one dish, requires no skill, costs only two bucks, and is, despite all of the above, wildly delicious. Yet it can get even more delicious just by adding a few more ingredients.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Hi there, Elites Welcome to my 6th post, This tutorial will explain how to hack windows, using a program (No-IP)

Confession: I love bagels. I love to make them, but above all, I love to eat them. In college I ran a mini-bagel business from my kitchen, and on bagel-making day, it wasn't uncommon for me to eat the circular goodies for breakfast, lunch, and dinner. Yet even with my obsession I can't always eat bagels fast enough to keep them from going stale. That's why I started learning ways to use bagels even when they're a day or three past their prime. As it turns out, there are a million and one thin...

Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time.

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.